IBM Db2 Audit Tools
Introduction
IBM Db2 has been a trusted backbone for enterprise data in industries like finance, healthcare, and government. Yet even the most secure database can fall short if administrators lack visibility into how data is accessed or changed.
Audit tools bridge this gap by recording database actions — who accessed data, what they did, and when it happened — creating the foundation for transparent, verifiable operations.
Without strong auditing, it’s nearly impossible to detect insider misuse, accidental data leaks, or compliance violations in time to prevent damage. A reliable audit trail helps organizations maintain accountability and support data protection obligations under laws such as GDPR, HIPAA, and PCI DSS.
For IBM Db2, this process starts with its native audit framework — and can be expanded with DataSunrise Data Audit for automation and compliance intelligence.
Why Auditing Matters
Auditing is not just a defensive measure; it’s an operational necessity.
Regulators expect verifiable audit evidence, and incident responders rely on historical logs to understand what went wrong. Without them, even routine maintenance can appear suspicious during compliance reviews.
Effective auditing provides:
- Accountability: Every privileged action leaves a traceable record.
- Visibility: Security teams can identify who interacted with sensitive data.
- Forensic depth: Logs reconstruct the timeline of a breach or policy violation.
- Regulatory proof: Detailed logs simplify audits for SOX or PCI DSS.
A sound auditing process transforms technical operations into business-grade assurance — demonstrating that access to information is managed, justified, and reviewable.
For a deeper look into how audit mechanisms support compliance management, see DataSunrise’s Audit Guide and Regulatory Compliance Center.
Core Audit Functions in IBM Db2
IBM Db2 includes the db2audit utility, which monitors user and system activities at both the instance and database levels. It captures who connects, what SQL statements are executed, and how privileges or roles are modified — all crucial details for compliance and security analytics.
Key functions include:
- Logging authentication successes and failures
- Recording SQL operations and schema access
- Tracking configuration or privilege changes
- Maintaining both local and centralized audit files
The IBM documentation on Db2 security auditing offers additional details on configuring these features in production environments.
Using the db2audit Utility
Enabling Auditing
To begin auditing, administrators enable the audit facility and start logging all categories:
db2audit configure scope all status both
db2audit start
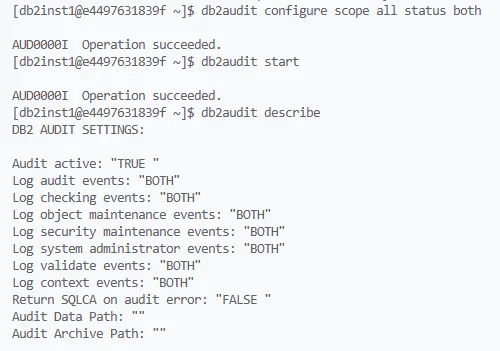
Checking Configuration
To confirm what is being logged:
db2audit describe
Extracting Readable Logs
Audit data is stored in binary form. To view it in text format:
db2audit extract delasc
This generates a delimited ASCII file showing events like logins, SQL execution, and privilege use — a chronological record that can be filtered or archived.
Example: Tracking Access to a Sensitive Table
Auditing can be scoped to specific databases or actions.
For example, to track access to employee_salary:
Enable database-level auditing:
db2audit configure scope db status bothPerform the action under audit:
db2 connect to HRDB user admin using securepass select * from employee_salary;Extract and review:
db2audit extract delasc more db2audit.delasc
This workflow reveals who queried the table, when, and from which client — essential for investigating access patterns or responding to compliance checks.
Limitations of Native Db2 Audit Tools
While db2audit is reliable and deeply integrated with Db2, it remains a manual, log-based system that can be challenging to maintain in large or hybrid environments.
| Limitation | Operational Impact |
|---|---|
| Manual extraction and parsing | Increases administrative effort |
| No real-time alerting | Security teams may miss critical events |
| Limited reporting tools | Requires external scripts for compliance formatting |
| Single-instance scope | Difficult to unify across multiple servers |
| Potential performance overhead | Heavy audit logging can slow busy systems |
Organizations that manage multiple databases or strict compliance frameworks often need automation and central visibility beyond what db2audit offers by default.
Extending Db2 Auditing with DataSunrise
While IBM Db2 provides solid native auditing, it wasn’t designed to automate compliance processes or provide enterprise-wide monitoring. This is where DataSunrise adds value.
DataSunrise is a comprehensive data security and compliance platform that enhances native tools across more than 40 databases, including IBM Db2.
It unifies auditing, masking, and monitoring under one interface — capturing real-time database activity without requiring code changes or intrusive agents.
Operating in proxy, sniffer, or native log trailing modes, it delivers full visibility while maintaining Db2’s performance and configuration integrity.
Key Enhancements for Db2 Environments
- Automated Log Management: Aggregates audit data across Db2 instances with no manual extraction.
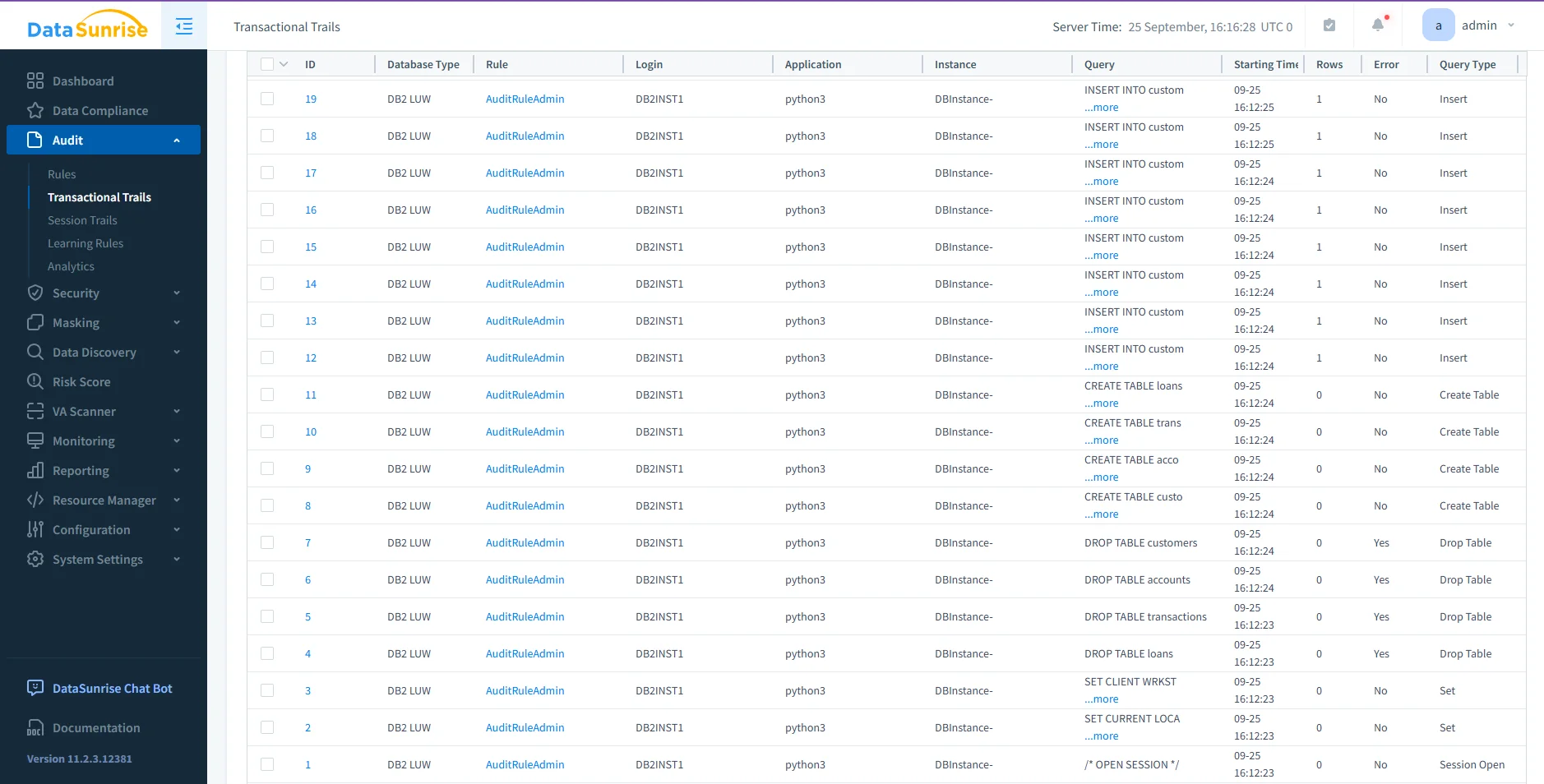
DataSunrise Audit panel displaying transactional trails for IBM Db2 LUW. Each record lists the rule, login, instance, application, query type, timestamp, and result status, providing full visibility into database activity across insert, create, and drop operations. - Real-Time Alerts: Triggers notifications via email, Slack, or SIEM when anomalies occur.
- Dynamic Masking: Obscures sensitive data on the fly without altering the database.
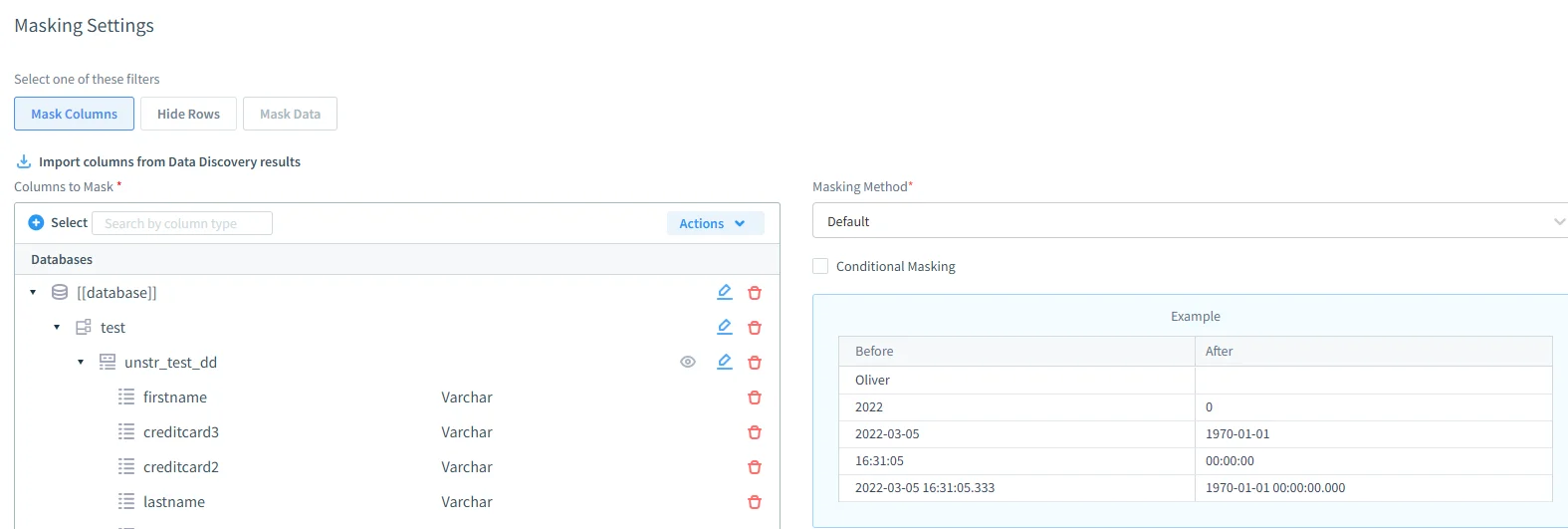
DataSunrise Masking Settings interface showing configured columns for masking within a test database. The panel displays column names, data types, and examples of masked values before and after transformation under the selected masking method. - Compliance Autopilot: Maps Db2 audit records to frameworks like GDPR, HIPAA, SOX, and PCI DSS.
- Machine Learning Audit Rules: Detect behavioral deviations using learning-based rule analysis.
Business Advantages
| Area | Benefit |
|---|---|
| Regulatory Alignment | One-click compliance evidence generation across frameworks |
| Operational Efficiency | Eliminates repetitive log parsing and manual reporting |
| Security Visibility | Detects anomalies across hybrid and cloud Db2 environments |
| Scalability | Centralized dashboard for 40+ supported platforms |
| Audit Readiness | Simplifies external audits with ready-to-export reports |
By integrating DataSunrise, teams gain continuous oversight and measurable reductions in both manual workload and compliance risk exposure.
Conclusion
IBM Db2’s native db2audit utility provides the technical foundation for secure, traceable data operations. However, as environments scale and regulations evolve, manual processes can’t always keep pace.
DataSunrise complements Db2 with centralized visibility, real-time monitoring, and automated compliance mapping — transforming standard audit logs into actionable intelligence.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now