IBM Informix Data Compliance Automation
In today's regulatory landscape, organizations using IBM Informix face mounting pressure to demonstrate continuous compliance. According to Verizon's 2024 Data Breach Investigation Report, organizations implementing automated compliance solutions reduce audit preparation time by 78% and compliance-related costs by up to 64%. With regulatory fines averaging $5.9 million per violation in 2024, manual compliance approaches are no longer viable.
Data compliance regulations like GDPR, HIPAA, PCI DSS, and SOX require comprehensive audit trails, stringent access controls, and continuous monitoring. For Informix environments, IBM's security documentation provides foundational guidance, but organizations require more sophisticated solutions. This article explores how DataSunrise's Compliance Autopilot transforms Informix compliance management through Zero-Touch Data Protection and Autonomous Compliance Orchestration.
Understanding Data Compliance Automation for Informix
Data compliance automation for Informix encompasses systematic implementation of policies, controls, and monitoring that ensure continuous adherence to regulatory frameworks without manual intervention. Key components include:
- Continuous Data Discovery: Automated identification of sensitive data across all Informix databases
- Policy Orchestration: Intelligent enforcement of access controls and security policies
- Real-Time Monitoring: Continuous tracking with automated violation detection through database activity monitoring
- Audit Trail Generation: Automatic creation of comprehensive audit logs
- Compliance Reporting: Automated documentation for regulatory frameworks
Organizations using Informix must typically satisfy multiple compliance requirements: GDPR (personal data protection), HIPAA (PHI security), PCI DSS (cardholder data protection), and SOX (financial data integrity).
Native Informix Compliance Capabilities
IBM Informix includes built-in database security features that provide foundational compliance capabilities, though they require significant manual configuration.
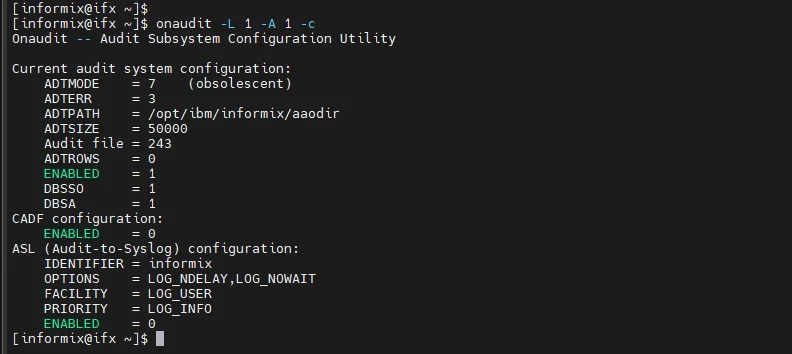
1. Audit Configuration with onaudit
The onaudit utility enables basic audit trail generation:
# Enable comprehensive auditing
onaudit -L 1 -A 1 -c
2. Viewing Audit Data
Review audit logs using:
onshowaudit | grep -E "ACTB|AUTH|ACTT"
Limitations of Native Informix Compliance Tools
| Native Feature | Key Limitation | Compliance Impact |
|---|---|---|
| Manual Configuration | Extensive setup required | High overhead, configuration gaps |
| Basic Auditing | Limited contextual information | Difficulty demonstrating compliance |
| No Automated Classification | Manual sensitive data identification | Risk of unprotected data |
| Static Policies | Manual updates needed | Compliance drift |
| Limited Reporting | No regulatory framework mapping | Time-consuming audits |
| Single-Instance Focus | Per-database configuration | Inconsistent policies |
Enhanced Informix Compliance Automation with DataSunrise
DataSunrise transforms Informix compliance management through Compliance Autopilot with No-Code Policy Automation and Continuous Regulatory Calibration.
Setting Up DataSunrise for Informix Compliance Automation
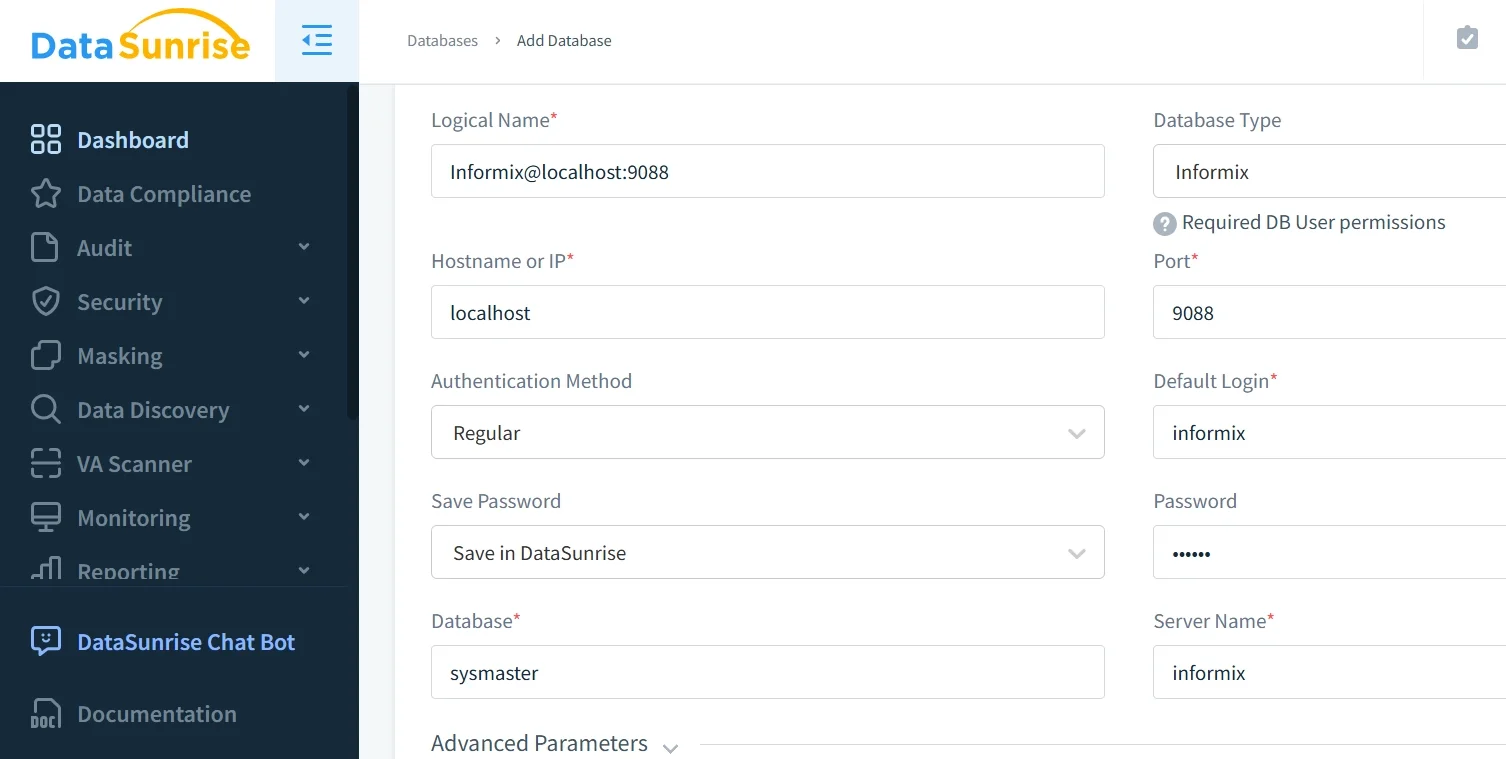
1. Connect Informix Instance
Establish a secure connection to your Informix database through DataSunrise's interface, supporting all deployment modes.
2. Automated Sensitive Data Discovery
DataSunrise's Auto-Discover & Classify engine automatically identifies PII, PHI, payment data, and custom patterns using NLP algorithms.
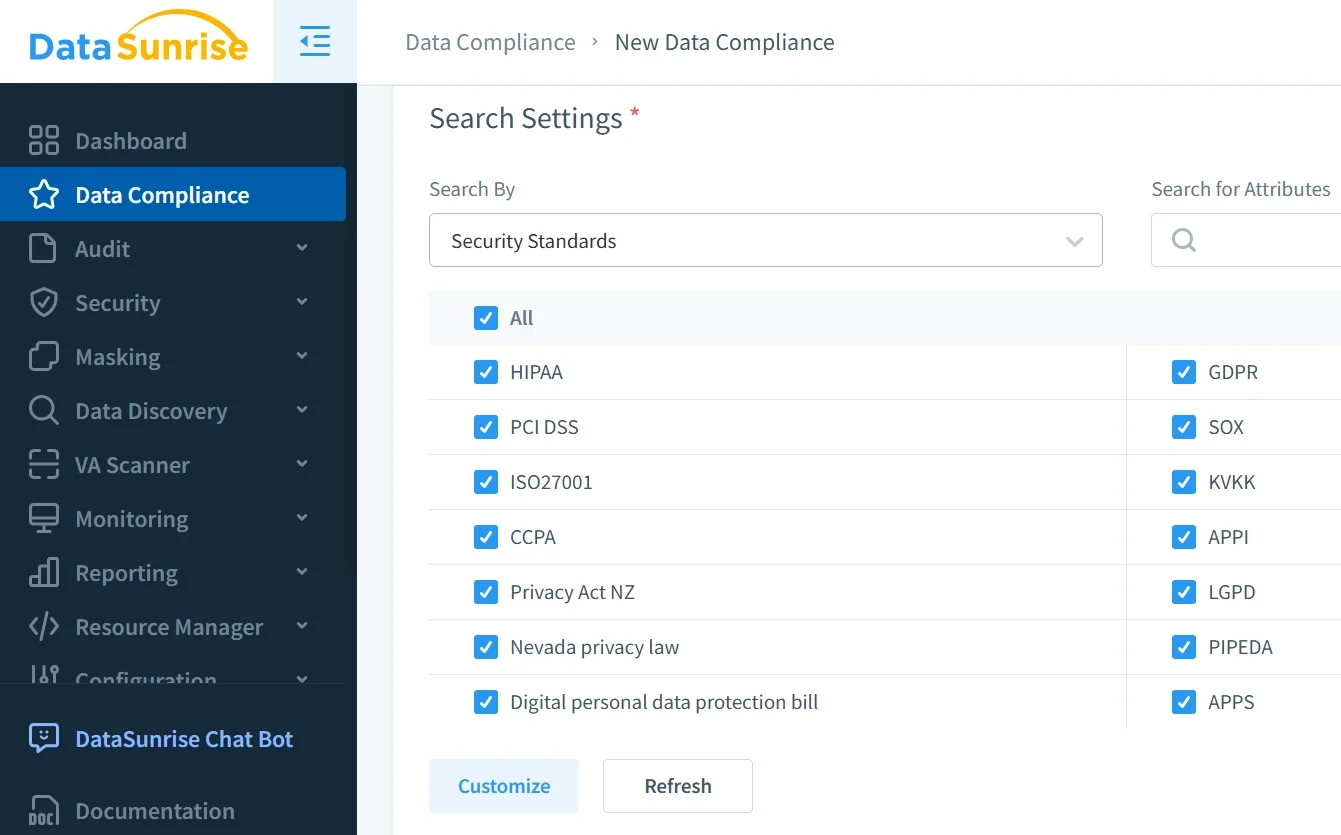
3. Configure Compliance Audit Rules
Create sophisticated audit rules using pre-configured templates for major compliance frameworks.
4. Implement Dynamic Data Masking
Protect sensitive information with dynamic data masking based on user roles and context, ensuring data protection while maintaining functionality.
5. Review Compliance Activity
Access comprehensive compliance monitoring through DataSunrise's unified dashboard.
Key Advantages of DataSunrise for Informix Compliance Automation
Compliance Autopilot
Autonomous Compliance Orchestration continuously monitors regulatory changes and automatically updates policies, ensuring Continuous Compliance Posture.
Intelligent Policy Orchestration
No-Code Policy Automation enables security teams to create sophisticated policies through an intuitive interface, reducing implementation time from weeks to hours with Surgical Precision Masking. Combined with database firewall capabilities, DataSunrise provides comprehensive protection.
Real-Time Regulatory Alignment
Real-time notifications for compliance violations enable rapid response. ML Suspicious Behavior Detection identifies anomalous access patterns.
Automated Compliance Reporting
One-click Audit-Ready Reporting for GDPR, HIPAA, PCI DSS, and SOX compliance.
Cross-Platform Centralized Policy Management
Unified Security Framework with support for over 40 data storage platforms ensures consistent policies across Informix and other databases.
User Behavior Analytics
Behavioral analytics establish baselines and detect anomalies, providing Context-Aware Protection that transforms compliance into predictive risk management.
Conclusion
As regulatory requirements evolve, manual approaches to Informix compliance have become unsustainable. While IBM Informix provides foundational security capabilities, organizations operating in regulated industries require comprehensive automation to maintain continuous compliance.
DataSunrise transforms compliance through Compliance Autopilot, No-Code Policy Automation, and Continuous Regulatory Calibration. By delivering Zero-Touch Data Protection with Real-Time Regulatory Alignment, DataSunrise enables organizations to satisfy multiple compliance frameworks while reducing costs and accelerating audit preparation.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now