
What Is SAP HANA Audit Trail

Modern generative‑AI (GenAI) applications lean on SAP HANA to stream vectors, customer profiles, and transactional facts at sub‑second latency. Each prompt, however, can disclose sensitive columns or skew a model if someone pokes the wrong table. What Is SAP HANA Audit Trail? It is the record that shows—query by query—who accessed which data, when, and why. A reliable trail anchors real‑time audit, dynamic masking, data discovery, and security controls required for clean GenAI pipelines and strict data‑compliance regimes.
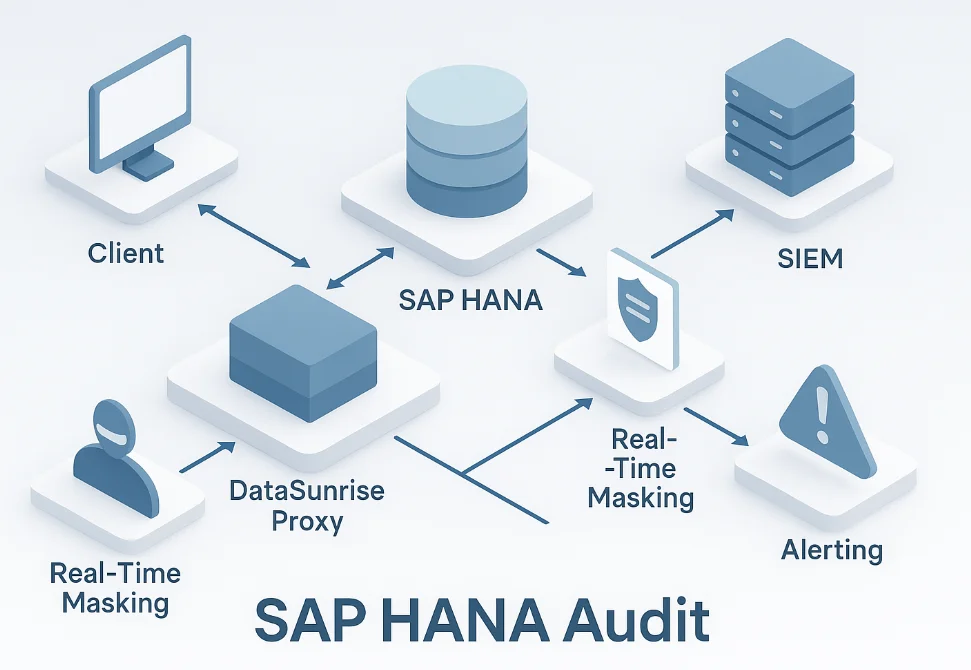
Why GenAI Raises the Stakes
Large language models feed on vast datasets. In an SAP HANA landscape, chatbots hit calculation views, summarization agents run SELECT TOP 1000, and fine‑tuning jobs extract multi‑year logs. Without continuous auditing, you cannot prove that private health records stayed masked or that only sanctioned roles queried training slices. A complete trail therefore unites security (detecting suspicious prompts instantly), data‑compliance (proving GDPR or SOX adherence), and model integrity (tracing every datum that influences a response).
Real‑Time Audit & Insight
SAP HANA writes events to internal tables, yet polling them hourly leaves blind spots—SAP HANA Security Guide recommends exporting logs to an external system for timely analysis. When the trail feeds a streaming collector such as the Audit Logs module in DataSunrise, events arrive in a SIEM within seconds, carry full SQL context, and push Slack or Teams alerts through the Real‑Time Notifications hook whenever a GenAI prompt touches a sensitive view.
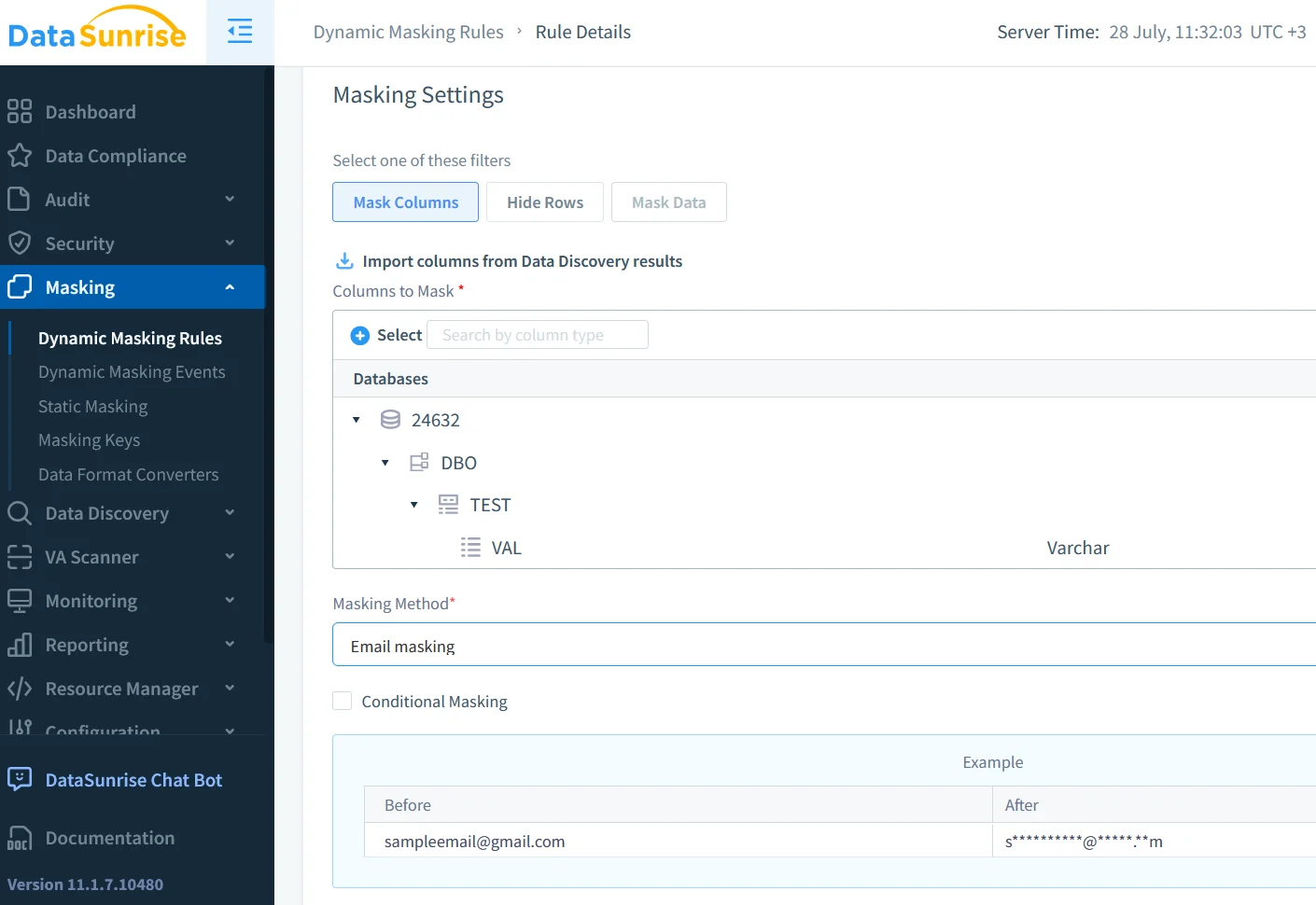
Dynamic Masking That Adapts to Prompts
Even a perfect trail cannot redact data already shown in a chat. Dynamic Data Masking intercepts results and hides PII according to role, IP, or—in GenAI workflows—prompt intent. For example, a finance bot can retrieve revenue totals while email addresses appear masked, and yet the audit shows both queries side by side for comparison.
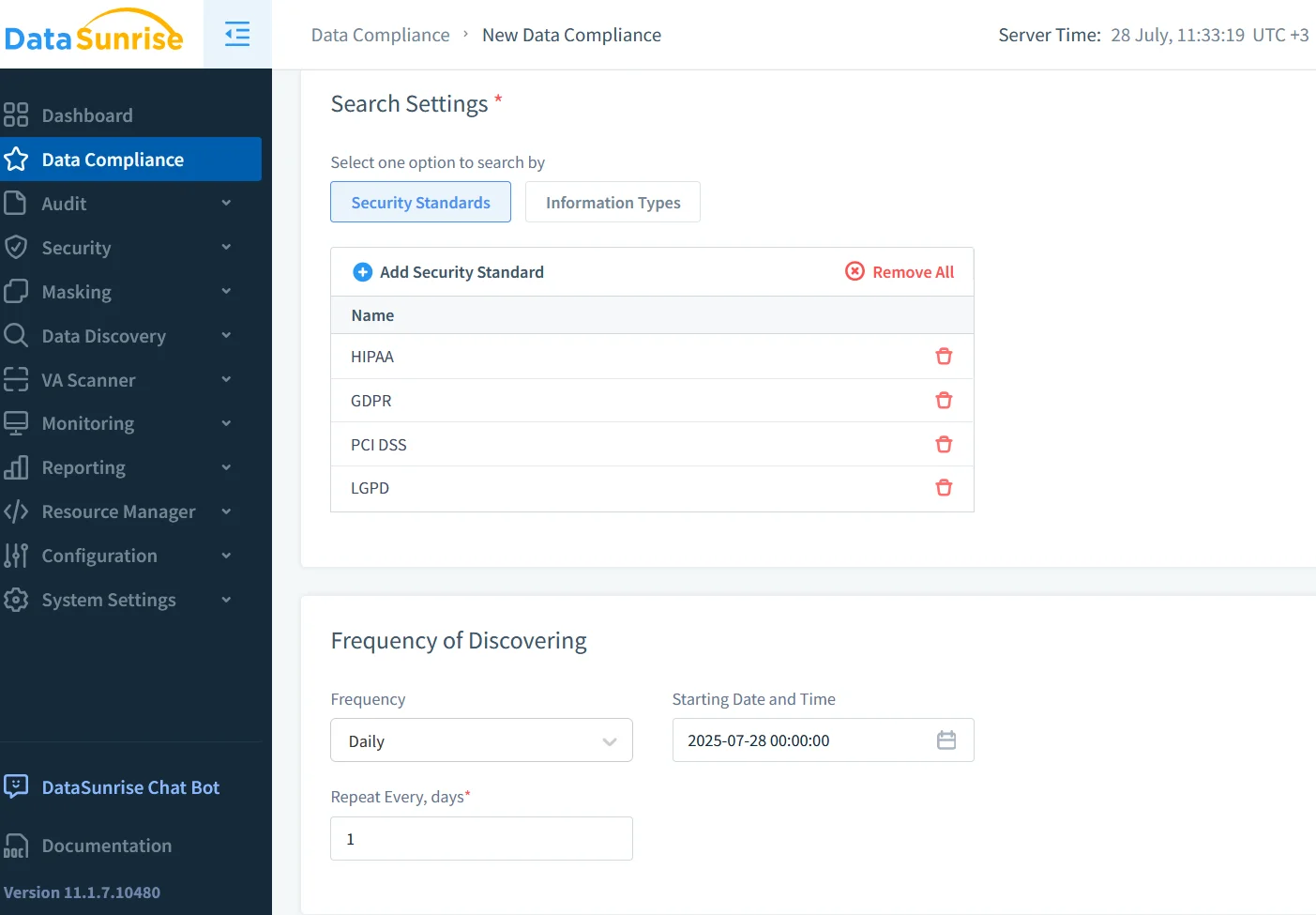
Data Discovery Powers the Policy Engine
Schemas evolve daily, so manual rules lag behind change. Automated Data Discovery scans fresh tables, tags sensitive columns, and feeds labels to masking and audit policies. Combined with Data Activity History, unused sensitive fields become easy to archive—shrinking the GenAI attack surface.
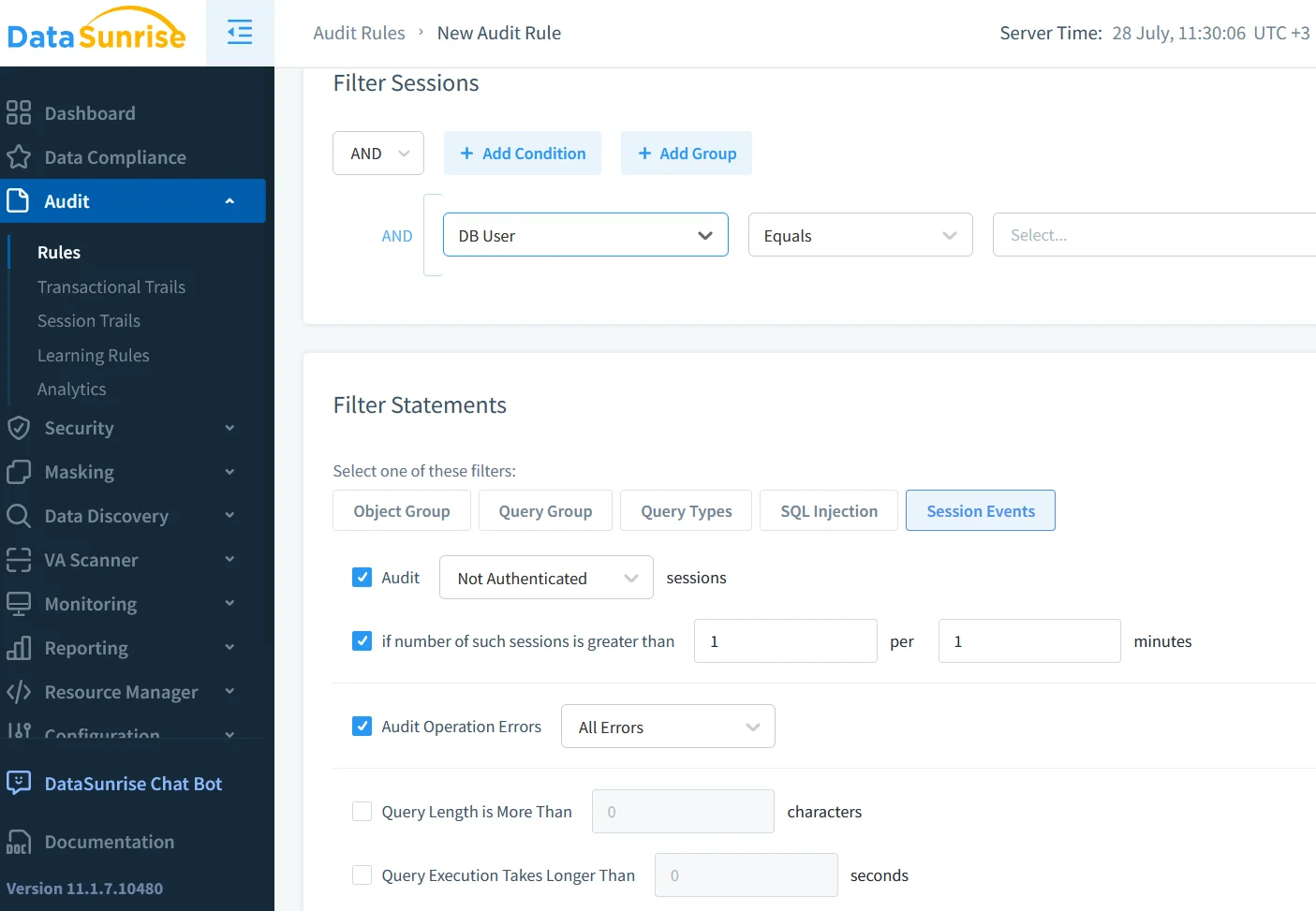
Configuring Native SAP HANA Audit
SAP HANA ships with a flexible audit subsystem documented in the SAP HANA Auditing Guide. A typical workflow looks like this:
-- 1. Activate auditing
ALTER SYSTEM ALTER CONFIGURATION ('audit','system')
SET ('global_audit_active') = 'true' WITH RECONFIGURE;
-- 2. Capture all SELECTs on a sensitive table except the bot user
CREATE AUDIT POLICY pii_selects
ACTION SELECT
ON TABLE "SALES"."CUSTOMERS"
WHEN USER != 'REPORTING_BOT';
ENABLE AUDIT POLICY pii_selects;
-- 3. Inspect the latest events
SELECT EVENT_TIME, USER_NAME, OBJECT_NAME, STATEMENT_STRING
FROM _SYS_AUDIT.AUDIT_LOG
WHERE POLICY_NAME = 'PII_SELECTS'
ORDER BY EVENT_TIME DESC
LIMIT 5;
Administrators now hold verifiable proof of each access. For implementation nuances, explore the community walkthrough on HANA Audit Best Practices. Caveats remain: logs are tenant‑local until exported, masking is absent, and real‑time alerts demand extra scripting.
Feature Comparison: Native SAP HANA Audit vs DataSunrise
| Capability | Native SAP HANA Audit | DataSunrise Proxy |
|---|---|---|
| Configuration effort | SQL policies created per tenant | Central rule engine via web UI or CLI |
| Real-time streaming | Requires XS jobs or custom scripts | Built-in sub-second forwarding to SIEM/SOAR |
| Dynamic masking | Not available | Role-, IP-, and prompt-aware masking |
| Bind-variable capture | Limited to statement text | Full capture for accurate replay and debugging |
| Compliance templates | Manual mapping to GDPR, PCI DSS, etc. | Ready-made packs in Compliance Manager |
| Cross-cluster visibility | Tenant-local only | Unified view across all HANA hosts |
Elevating the Trail with DataSunrise
DataSunrise places a reverse proxy in front of HANA, records every request—success or error—and stores enriched events centrally. A single rule can span dozens of HANA hosts, capture bind values, and invoke context‑aware policies.
Because masking, discovery, and Compliance Manager packs run in the same engine, blocked or masked queries appear alongside native events, giving auditors a single timeline enriched with verdicts and LLM metadata.
Security & Compliance in One Loop
When DataSunrise flags a disallowed prompt, it masks or blocks the answer, logs the outcome, and notifies stakeholders—all before the LLM forms a response. This closed loop promotes zero‑trust data access without slowing development.
Chatbot Request Walkthrough
A user asks, “Show me last month’s invoices for [email protected].” The proxy evaluates context, masks the email column to a****@example.com, writes an audit entry marked MASK_APPLIED, and returns anonymised aggregates to the model. Every hop remains traceable, enabling swift root‑cause analysis if the request later appears in a breach investigation.
Putting It All Together
What Is SAP HANA Audit Trail? It is the backbone of GenAI security and compliance. Additional reference: the SAP HANA Audit Logging Wiki. Native SAP HANA auditing lights the first beacon; DataSunrise extends it with discovery, dynamic masking, and real‑time insight. Together they safeguard intellectual property, satisfy regulators, and keep language models honest. Ready to see it live? The Data Audit page links to an interactive DataSunrise Demo that traces prompts from entry to audit log in seconds.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now