
Cloud-Based Data Security Posture Management (DSPM) with DataSunrise
As organizations increasingly rely on cloud environments, data breaches remain one of the most critical risks across industries. Research indicates that nearly 68% of these incidents are caused not by direct technical exploits, but by human error, configuration oversights, and social engineering attacks. This underscores the need for adaptive security models rather than purely defensive controls. Data Security Posture Management (DSPM) delivers a continuous, automated approach to identifying data assets across cloud and hybrid ecosystems, evaluating their exposure, enforcing compliance requirements, and proactively correcting vulnerabilities before they result in a breach. According to the Cloud Security Alliance, misconfigurations remain one of the top root causes of cloud data exposure worldwide.
By offering ongoing visibility into where sensitive data is located, who can access it, and how it is used, DSPM helps organizations maintain a strong, compliant security posture. When combined with automated data classification, contextual risk scoring, and seamless integration with platforms like SIEM and IAM, DSPM supports faster detection of abnormal behavior and consistent policy enforcement across dynamic infrastructures. This comprehensive and adaptive strategy reduces both the probability and the potential impact of security incidents, shifting data protection from reactive response to intelligent, continuous control.
What is Data Security Posture Management?
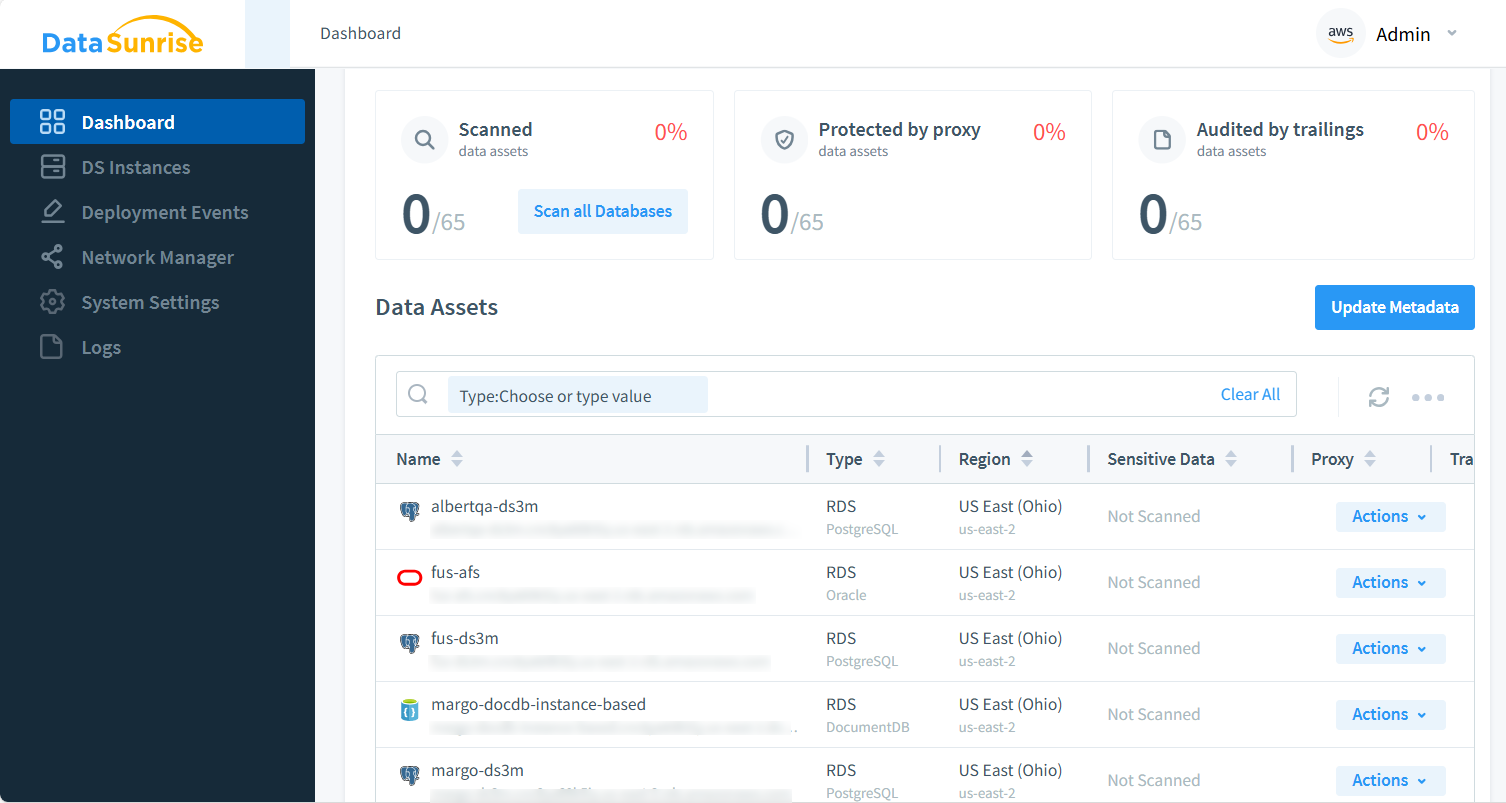
Data Security Posture Management is a systematic approach to identifying, assessing, and mitigating data risks in cloud environments. DSPM maps where sensitive data resides, who has access, and whether safeguards meet policy and regulatory standards—delivering real-time visibility and automated remediation instead of one-off audits.
| Deployment Mode | Purpose | When to Use |
|---|---|---|
| Discovery Mode | Scans cloud environments for sensitive data using a single instance | Initial audits, low-volume environments, or periodic compliance reviews |
| High Availability Mode | Deploys multiple instances with load balancing and redundancy | Production systems, always-on compliance enforcement, mission-critical data |
The effectiveness of DSPM lies in its ability to provide continuous monitoring and automated analysis of security measures. This proactive approach enables organizations to identify and address potential vulnerabilities before they can be exploited by malicious actors. Through comprehensive security assessments and automated responses, DSPM tools help organizations maintain a strong security posture while optimizing resource utilization.
The Power of Cloud-Based Discovery
DataSunrise DSPM stands at the forefront of cloud-based asset discovery innovation. The platform employs sophisticated scanning techniques to create a comprehensive inventory of an organization's data assets. This discovery process extends across multiple cloud environments, encompassing various data storage systems and database technologies.
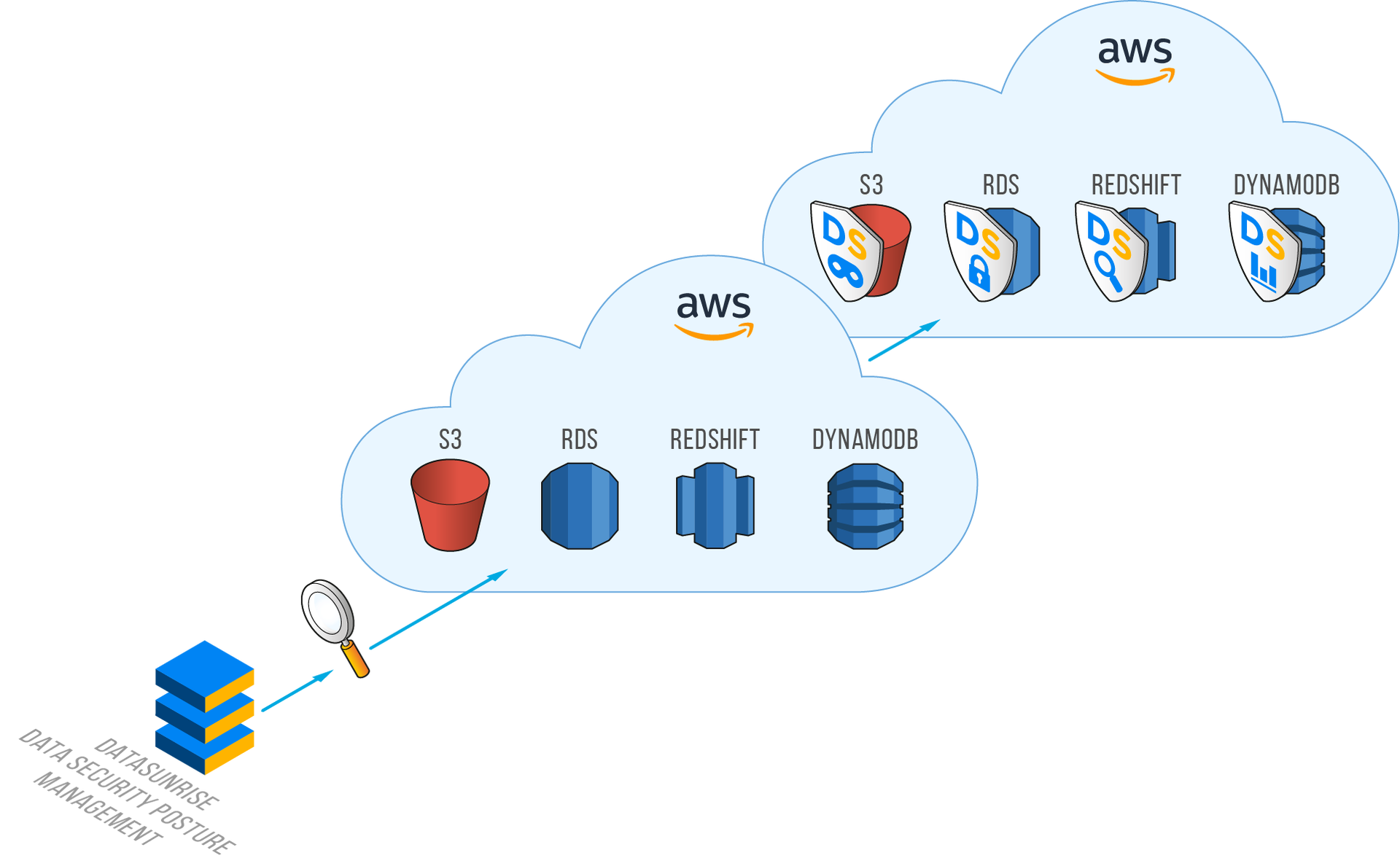
The system excels in identifying sensitive data across diverse cloud infrastructures. It can detect and analyze databases and search engines running on EC2 instances, providing detailed insights into data storage and usage patterns. Furthermore, the platform's capability extends to identifying file systems within cloud environments, ensuring no data repository goes unmonitored.
The discovery process includes thorough analysis of both relational and NoSQL databases, creating a complete picture of an organization's data landscape. This comprehensive approach ensures that security measures can be appropriately tailored to protect different types of data storage systems effectively.
Advanced Security Architecture and Implementation
DataSunrise DSPM implements a sophisticated security architecture that prioritizes both protection and availability. The platform automatically collects and analyzes AWS or Azure account metadata, providing deep insights into network architecture and security configurations. This analysis encompasses virtual private clouds, network configurations, and security group settings, creating a holistic view of the organization's security landscape.
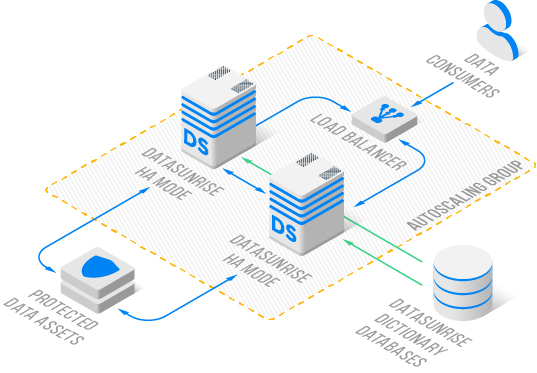
The system's high-availability protection features implement a proxy-based solution that ensures continuous data protection without compromising performance. This approach enables load-balanced access to protected resources while maintaining robust security measures. The platform's automated scaling capabilities ensure that protection measures can grow alongside organizational needs, while redundant security coverage prevents single points of failure.
Deployment Flexibility and Operational Excellence
This tool streamlines the deployment process by automating the creation of DataSunrise instances and enabling you to assign them to protect your specific data assets.
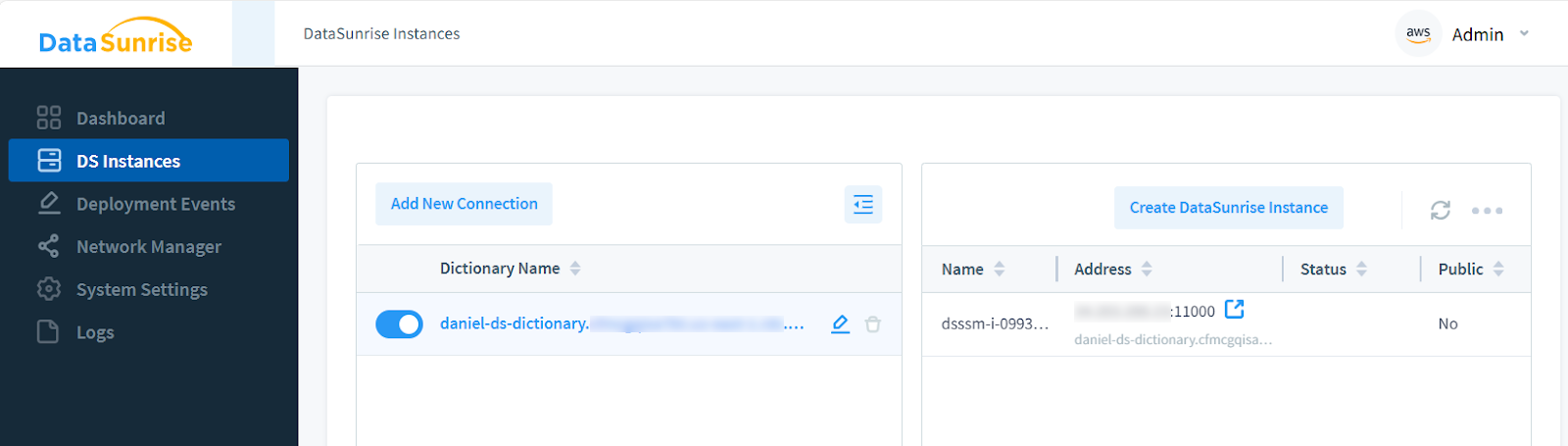
Organizations can choose between two primary deployment modes, each tailored to specific security requirements. The Discovery Mode utilizes a single instance for sensitive data detection, ideal for initial security assessments and periodic audits. In contrast, the High Availability Mode deploys multiple instances with sophisticated load balancing, providing enhanced protection for critical data assets.
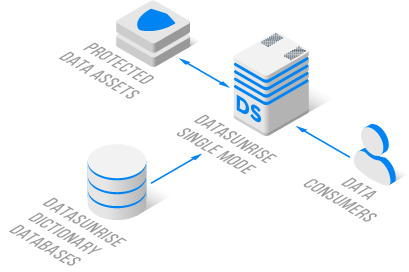
The platform's audit configuration capabilities automate the setup and maintenance of security monitoring. This includes integration with Cloud Option Groups and Parameter Group level implementations, ensuring comprehensive coverage of all data assets. The system generates detailed audit trails, providing valuable insights into data access patterns and potential security incidents.
The third option of asset protection is an audit trail. This is configured as shown below. Note there should be available at least one DataSunrise Instance.
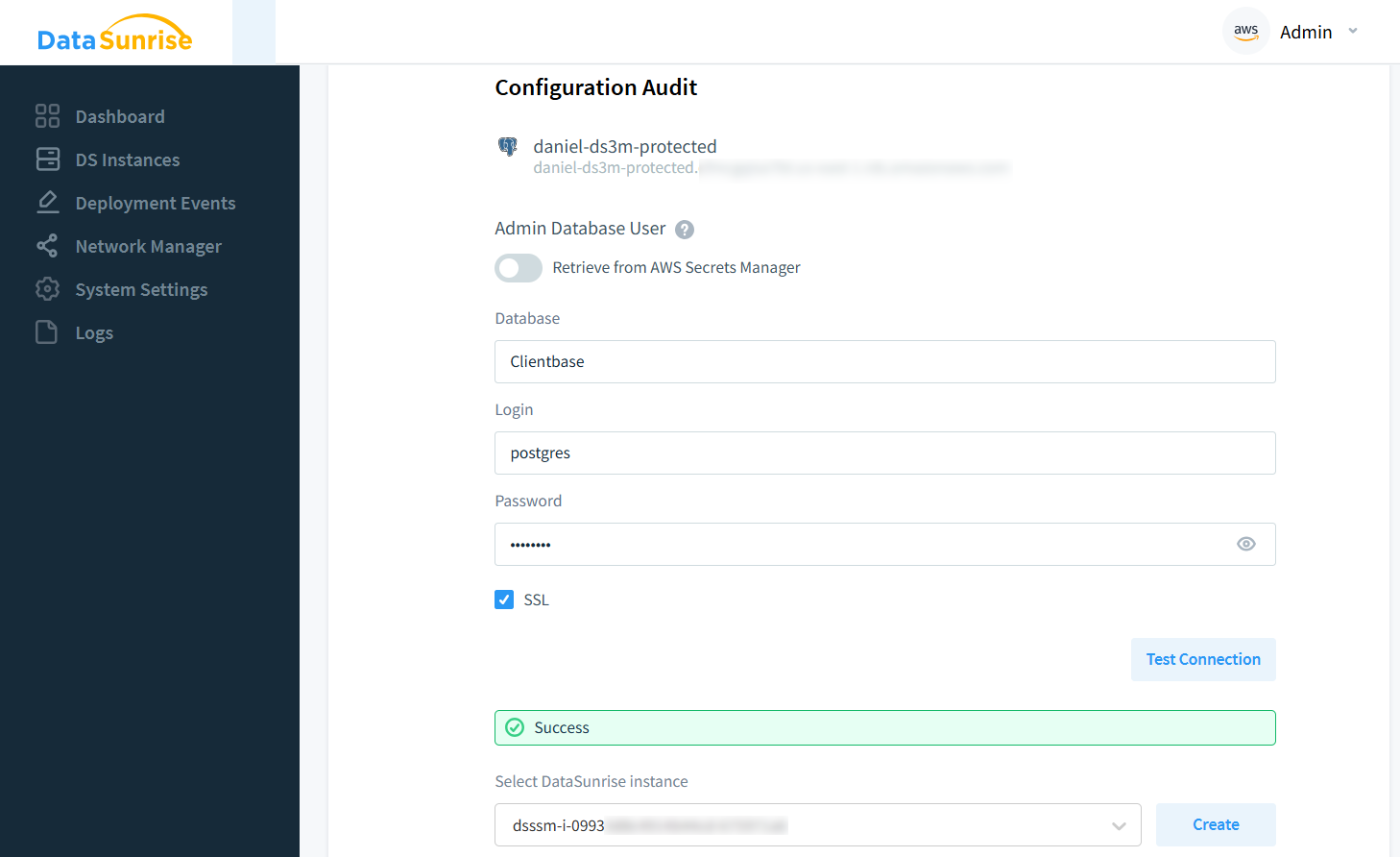
Audit Configuration page displaying a configured instance (‘dsssm-i-…’) that will monitor and audit a PostgreSQL database.
Comprehensive Network Management and Monitoring
Network management capabilities within DataSunrise DSPM provide unprecedented visibility into network infrastructure.
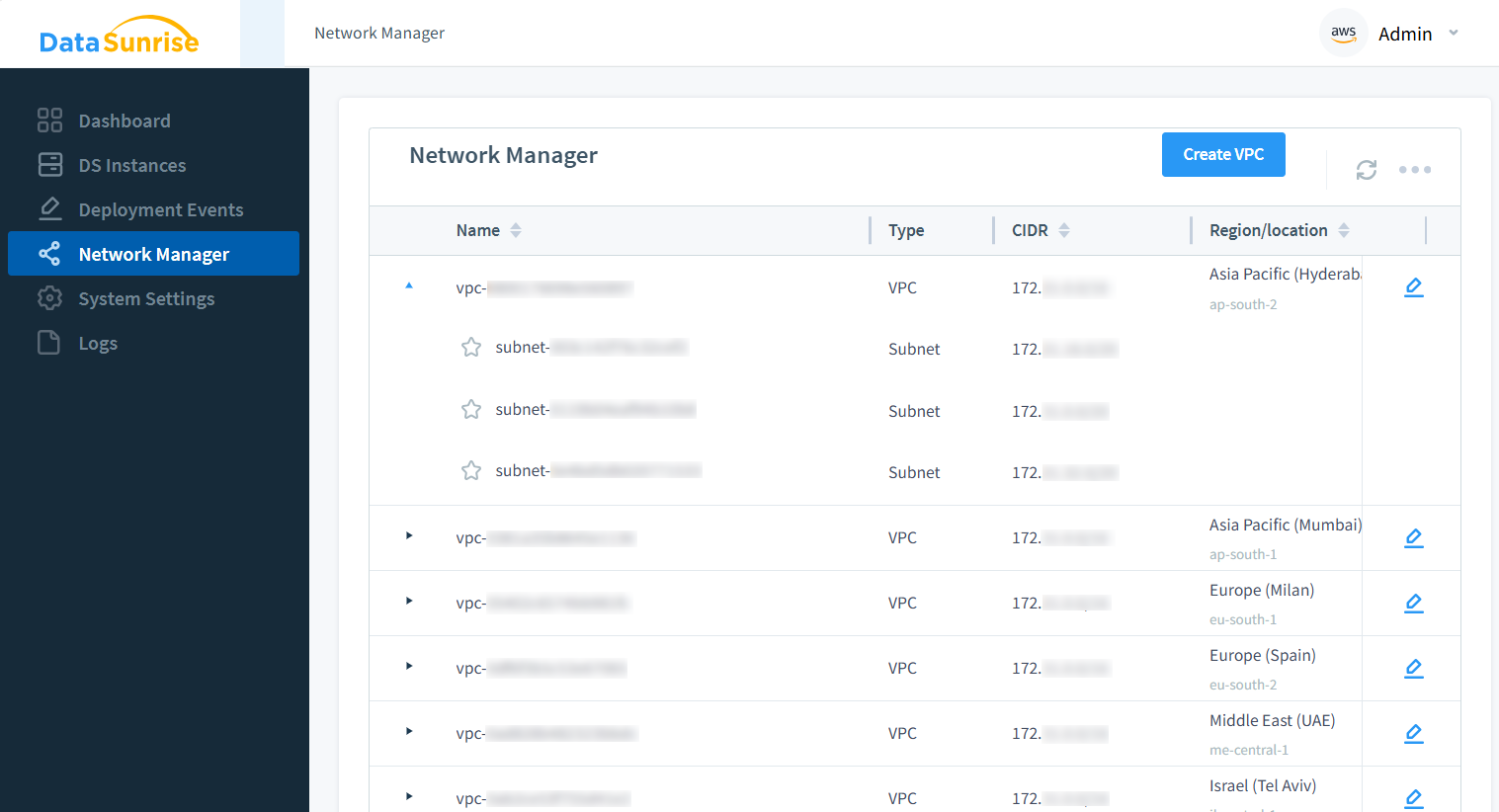
The system consolidates network information and enables efficient subnet management, streamlining security implementations across complex network architectures. Support for VPC peering connections and Private DNS Zone linking ensures seamless integration with existing network infrastructure.
Regulatory Compliance and Industry Standards
In today's regulatory environment, maintaining compliance with industry standards is crucial. DataSunrise DSPM helps organizations meet stringent requirements for regulations such as HIPAA and GDPR. The platform's comprehensive monitoring and protection capabilities ensure that compliance standards are not just met but exceeded, providing peace of mind for security administrators and stakeholders alike.
The system's integration capabilities extend across various cloud services, including Amazon RDS, Amazon Redshift, and numerous EC2-based databases. This broad coverage ensures that organizations can maintain consistent security policies across their entire cloud infrastructure, regardless of the specific technologies in use.
Key Benefits of Implementing DSPM
- Unified Visibility: See all sensitive data assets across multiple cloud accounts in one dashboard.
- Continuous Compliance: Automated checks keep pace with changing regulations and infrastructure updates.
- Faster Incident Response: Real-time alerts shorten detection-to-response time for potential threats.
- Risk Reduction: Identify and close exposure points before they can be exploited.
Operational KPIs for DSPM Programs
| KPI | What It Indicates | Target Trend |
|---|---|---|
| Time to inventory new data stores | Speed at which DSPM discovers net‑new assets | Decreasing |
| % of sensitive data with enforced controls | Coverage of masking, access, and logging policies | Increasing |
| Mean time to remediate exposure | Time from alert to fix (e.g., open bucket, wide role) | Decreasing |
| Policy drift rate | Frequency of config/regression reopening risks | Decreasing |
| Audit readiness score | Availability of evidence for GDPR/HIPAA/SOX | Increasing |
Summary and Conclusions
DataSunrise Data Security Posture Management strengthens enterprise protection by combining automated discovery, continuous monitoring, and scalable policy enforcement within one platform. This gives organizations real-time insight, simplified compliance processes, and resilient controls that adapt to growth and new security challenges.
Beyond visibility, DSPM provides a unified governance layer across hybrid and multi-cloud environments, ensuring consistent enforcement even as data moves between platforms. Automated risk scoring and classification help teams prioritize remediation, while centralized audit intelligence eliminates blind spots often caused by fragmented tooling.
By aligning security controls directly with sensitive data—rather than relying solely on perimeter defenses—DataSunrise helps organizations confidently address modern threats such as insider misuse, misconfigured cloud services, over-privileged accounts, and accidental exposure during development or analytics workflows.
With its blend of flexibility, automation, and comprehensive coverage, DataSunrise DSPM serves as a key element of modern cloud security strategies—helping businesses protect sensitive data while maintaining efficient operations. As regulatory expectations evolve and environments grow more complex, centralized DSPM capabilities become essential for maintaining compliance, reducing operational risk, and accelerating secure digital transformation.
About DataSunrise
DataSunrise is a leading innovator in database and data security, providing a unified protection platform that redefines how organizations safeguard their critical information assets. Unlike traditional perimeter-based approaches, DataSunrise delivers deep, continuous visibility directly at the database layer—where the most valuable data resides. Its integrated suite combines intelligent Database Activity Monitoring (DAM) with advanced User Behavior Analytics (UBA), enabling real-time detection of anomalies, policy violations, and insider threats across both structured and unstructured environments.
Leveraging machine learning–powered analytics, DataSunrise not only detects abnormal access behaviors and suspicious SQL activities but also continuously adapts to emerging threat patterns, enabling faster and more precise responses from security teams. Its integrated vulnerability assessment tools perform ongoing scans of database settings, roles, and privileges—pinpointing weaknesses, misconfigurations, and unnecessary permissions before they become exploitable threats. This proactive intelligence allows organizations to maintain a secure, compliant, and efficiently governed database environment.
In addition to its advanced monitoring and analytical functions, DataSunrise delivers adaptive data masking, fine-grained access management, and robust query-level protection that safeguard sensitive data across every stage of its lifecycle—from storage and transmission to analysis and reporting. Operating seamlessly across on-premises, hybrid, and multi-cloud infrastructures, the platform enforces uniform security policies and auditability without impacting system performance or uptime.
Backed by continuous compliance validation, AI-driven threat modeling, and automated policy enforcement, DataSunrise elevates database security into a strategic foundation for digital resilience. Whether addressing insider risks, mitigating zero-day exploits, or ensuring compliance with global standards such as GDPR, HIPAA, SOX, and PCI DSS, DataSunrise empowers enterprises with an intelligent, scalable, and forward-looking defense framework—enabling secure innovation and sustainable growth.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now