Amazon OpenSearch Audit Log
Amazon OpenSearch Audit Log
Amazon OpenSearch Audit Log provides organizations with visibility into how users, applications, and services interact with OpenSearch clusters. In practice, Amazon OpenSearch often stores operational logs, security events, customer support records, and application telemetry. Because these datasets frequently include sensitive or regulated information, database-level auditing becomes a mandatory security control rather than an optional feature.
Audit logs allow security and compliance teams to answer critical questions: who accessed OpenSearch, what operations were performed, which indices or documents were affected, and when those actions occurred. Without a structured audit log, reconstructing these details during an investigation or audit becomes slow and unreliable.
This article explains how Amazon OpenSearch audit logging works, why native logging mechanisms are insufficient, and how DataSunrise delivers centralized, audit-ready logging for OpenSearch environments.
What an Audit Log Captures in Amazon OpenSearch
An audit log focuses on database activity rather than system performance or availability. In the context of OpenSearch, audit logging typically includes:
- User and service authentication events
- Index creation, modification, and deletion
- Document indexing, updates, and removals
- Administrative and configuration API calls
These events differ from standard operational logs, which primarily support troubleshooting. Audit logs, by contrast, support database security, data security, and formal compliance processes.
Why Native OpenSearch Logs Fall Short
Amazon OpenSearch generates internal logs that record request metadata and system events. While operators use these logs for diagnostics, they were not designed to function as a complete audit trail aligned with data compliance regulations.
Native audit limitations include:
- No session-level or transaction-level correlation
- Limited visibility into full request context
- Retention tied to cluster lifecycle and storage
- No centralized audit reporting or evidence management
As a result, native logs rarely satisfy regulatory or internal audit requirements on their own. Organizations that rely solely on them often struggle to demonstrate access accountability or investigate suspicious behavior.
Audit Rule Configuration for Amazon OpenSearch
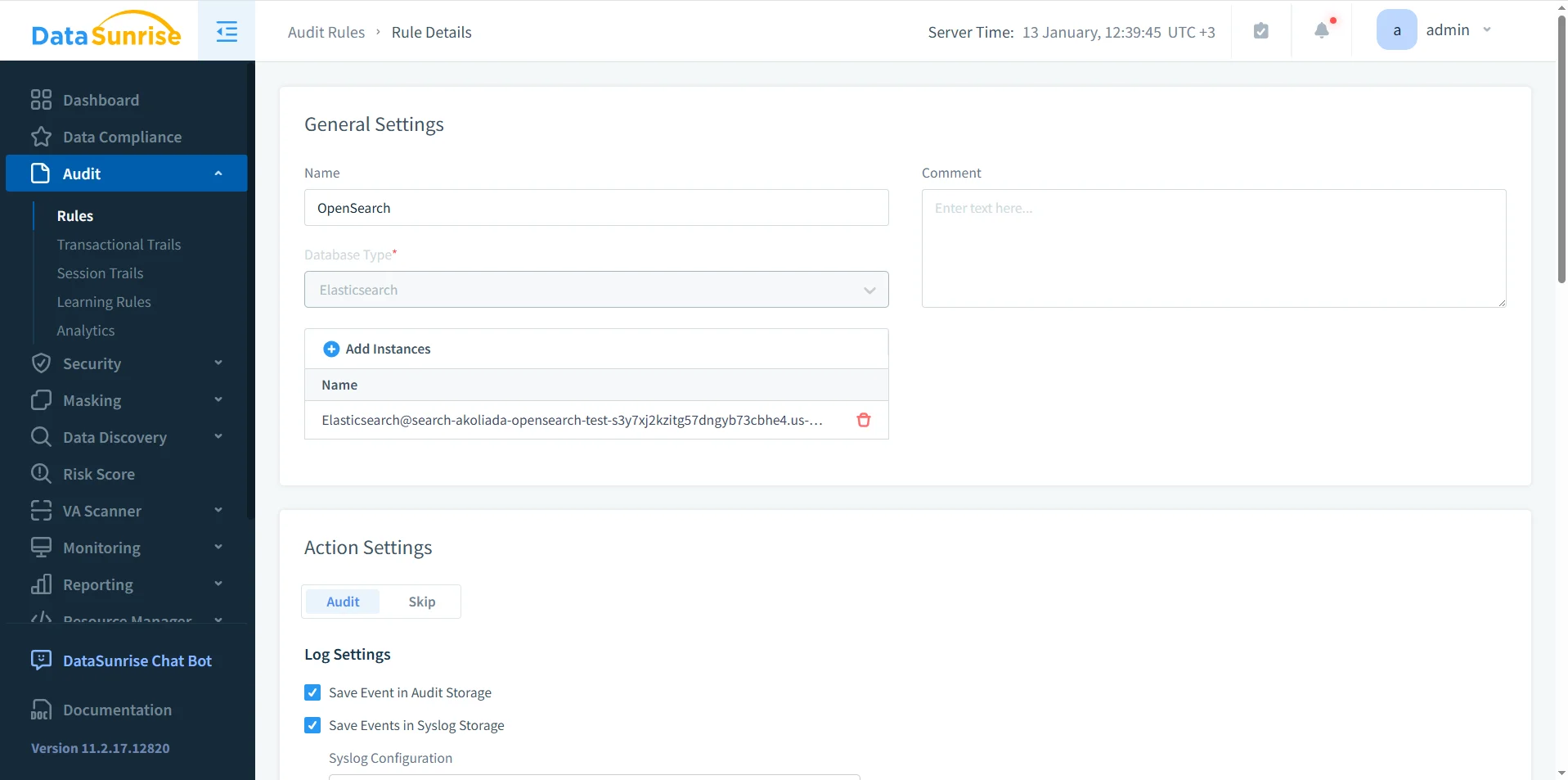
DataSunrise implements OpenSearch audit logging through explicit audit rules. These rules define which OpenSearch instances are monitored, which operations are logged, and where audit events are stored.
Audit rules allow teams to focus on high-risk operations such as document writes, updates, deletions, and administrative actions. This selective approach aligns with data audit and audit logs best practices.
Rule evaluation follows a deterministic priority model described in the rules priority guide, ensuring consistent enforcement even in environments with overlapping security policies.
Transactional Trails and Correlated Audit Events
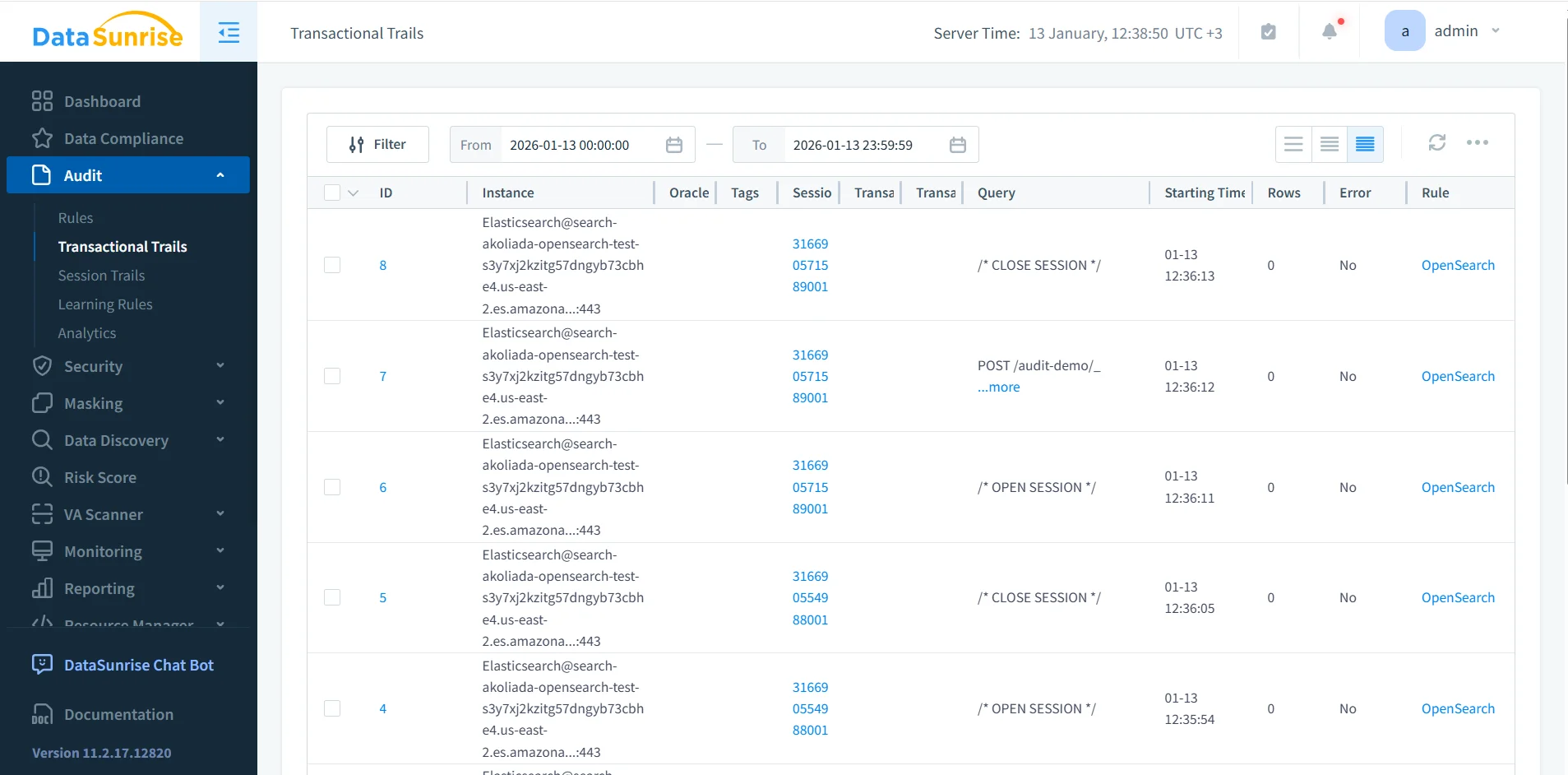
OpenSearch processes each REST request independently. Although this design improves scalability, it complicates auditing because related operations appear as disconnected events.
DataSunrise resolves this challenge by correlating individual OpenSearch requests into transactional audit trails. These trails group related operations based on timing, connection attributes, and request metadata, providing a complete database activity history.
From an audit perspective, transactional trails provide essential context. They show how a user or application interacted with OpenSearch over time, not just which individual requests occurred.
Centralized Audit Logging Architecture
DataSunrise captures OpenSearch activity as an external audit layer rather than relying on database internals. This approach uses traffic inspection and reverse proxy techniques to observe database interactions.
This architecture delivers several advantages:
- Audit data remains independent of OpenSearch clusters
- Users cannot tamper with stored audit records
- Centralized retention policies apply across environments
- Audit history persists through upgrades and migrations
Centralized storage also integrates with optimized audit storage and automated compliance reporting.
Example: Audited OpenSearch Operation
The following request demonstrates how DataSunrise records a document indexing operation as part of the Amazon OpenSearch audit log. The request format follows the official OpenSearch indexing API.
curl -X POST "http://localhost:9201/audit-demo/_doc" \
-H "Host: search-your-opensearch-domain.us-east-2.es.amazonaws.com" \
-H "Content-Type: application/json" \
-d '{
"user": "bob.smith",
"action": "support_case_update",
"ip": "220.240.200.148",
"timestamp": "2026-01-13T14:02:27Z"
}'
DataSunrise records this operation as an auditable database event. The audit entry includes client identity, source address, operation type, execution time, and the matched audit rule. This context supports investigations and database activity monitoring.
Audit and Compliance Use Cases
A structured Amazon OpenSearch audit log supports multiple security and compliance scenarios:
- Incident response and forensic analysis
- Access accountability for administrators and support teams
- Evidence generation for internal and external audits
- Detection of anomalous behavior using user behavior analysis
These capabilities help organizations align OpenSearch deployments with GDPR, HIPAA, PCI DSS, and SOX using centralized data security policies and continuous audit enforcement.
Begin audit logging with high-risk operations such as index changes and administrative API calls. Expanding coverage gradually helps control log volume while preserving audit value.
Do not rely solely on native OpenSearch logs for compliance audits. Without centralized retention and request correlation, audit evidence may be incomplete or unavailable when it is needed most.
Conclusion: Building a Reliable OpenSearch Audit Log
Amazon OpenSearch delivers powerful search and analytics functionality. However, native logging alone does not provide a complete audit log suitable for security investigations or compliance reviews.
By deploying DataSunrise as an external audit layer, organizations gain a centralized, tamper-resistant Amazon OpenSearch audit log. This approach strengthens security posture, simplifies compliance, and ensures long-term audit readiness.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now