ClickHouse Audit Log
ClickHouse moves obscene amounts of data at blistering speed — great for analytics, terrible for anyone who must prove exactly who touched what and when. Columnar execution, distributed processing, and real-time ingestion create environments where logs scatter across nodes like shotgun pellets. Regulations such as SOX, HIPAA, PCI DSS, and GDPR, however, demand complete, immutable, centralized audit evidence.
ClickHouse does provide native telemetry, but it was never designed to function as a complete, compliance-ready audit log. Instead, it emits fragments: system tables, text logs, diagnostic streams, and operational metadata. Understanding these capabilities — and their limits — is step one. Step two is seeing how DataSunrise turns ClickHouse's telemetry into a unified, enriched, auditable system.
What Is an Audit Log?
An audit log is a chronological and tamper-resistant record that captures every action performed against a data system. It describes who accessed the system, what operation occurred, which objects were involved, when the action took place, where the request originated, and how the system responded. To serve its purpose, an audit log must remain immutable, ensuring that no retroactive modifications can occur. It must also be complete, capturing all relevant activity without gaps; correlated, so that all events across sessions, users, and nodes form a coherent narrative; enriched, meaning each entry contains contextual details such as identity information, data sensitivity, and risk; and exportable, allowing organizations to produce regulatory evidence on demand.
Debug logs, query logs, and cluster logs are not audit logs. They are diagnostic outputs without the guarantees, structure, or accountability required for compliance or forensic reconstruction. A true audit log satisfies regulatory, forensic, and operational requirements — not merely system introspection. ClickHouse’s native logging produces raw signal, but not an auditable record. DataSunrise provides the structure, enrichment, consolidation, and compliance alignment necessary to transform those raw signals into a verifiable audit trail.
Native ClickHouse Audit Logging Overview
ClickHouse exposes operational and query-level telemetry through system tables and rotating log files. These form the foundation of a basic audit log.
1. Query Log Tables
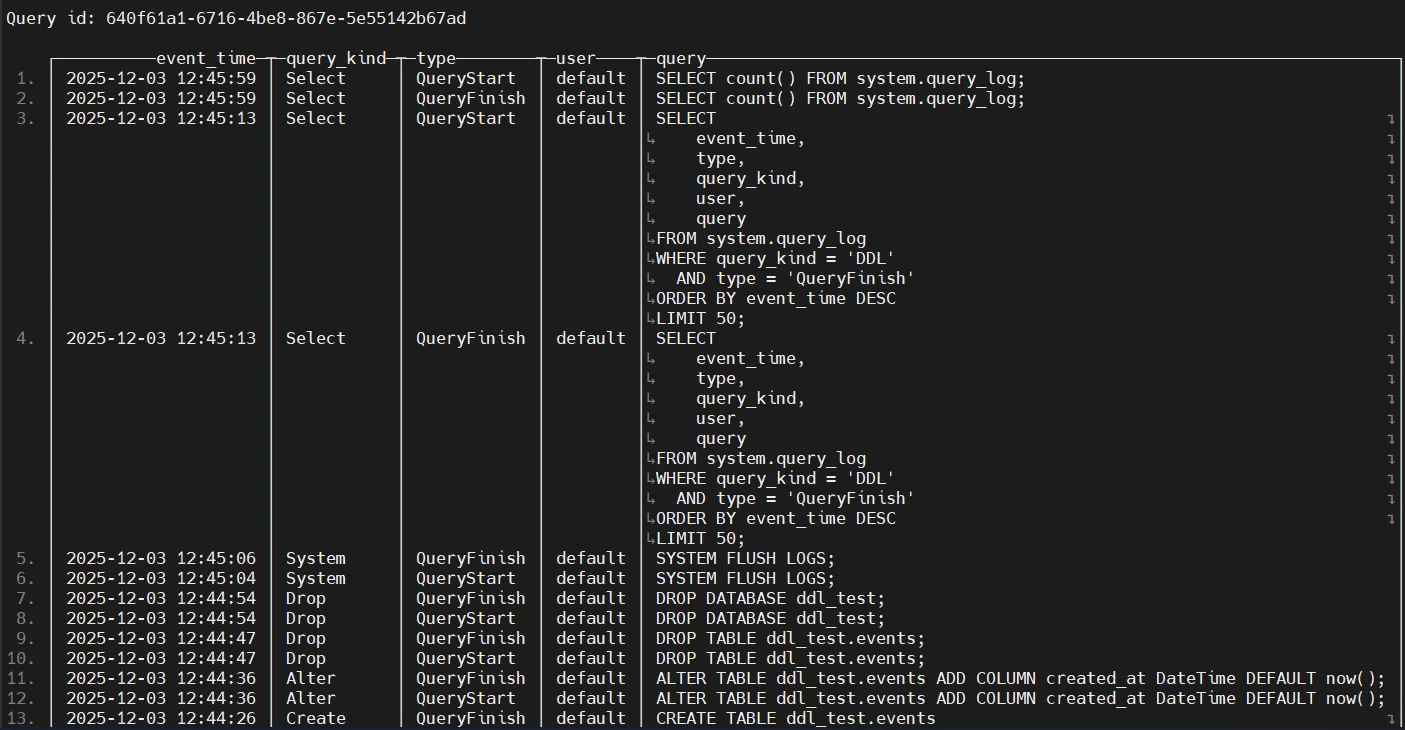
ClickHouse records extensive query lifecycle details inside several system tables. The system.query_log table captures information such as query text, execution duration, memory consumption, and the authenticated user. Additional depth is stored in system.query_thread_log, which tracks per-thread execution metadata, and system.part_log, which documents insert, merge, and replication-related operations on data parts. Lower-level diagnostic messages are written to system.text_log, which serves as a stream of internal server events. Administrators frequently query system.query_log to extract recent activity, for example:
SELECT
event_time,
query_kind,
query,
user,
client_hostname,
client_name
FROM system.query_log
WHERE event_time > now() - INTERVAL 1 HOUR
ORDER BY event_time DESC;
These tables provide raw visibility but do not automatically assemble a cohesive audit trail.
2. Access & Authorization Logging
ClickHouse emits access-related information through various authorization and RBAC mechanisms. This includes signals such as role-based access control checks, failed authentication attempts, user and role modifications, and outcomes of privilege enforcement. These events appear inside system logs and system tables but are not unified into a compliance-focused audit structure.
A typical inspection of authorization failures might look like this:
SELECT event_time, type, user, client_address, error_message
FROM system.text_log
WHERE type = 'Information'
AND error_message ILIKE '%Authentication failed%'
ORDER BY event_time DESC;
Extracting RBAC-related modifications may require querying ClickHouse RBAC metadata:
SHOW GRANTS;
Because these signals remain dispersed, correlating authentication behavior with actual query execution requires external consolidation.
3. Server Log Streams
Beyond query and authorization logging, ClickHouse produces operational logs that often contain audit-relevant details. These include entries in clickhouse-server.log, traces from the replication subsystem, configuration reload events, and DDL operation messages. For example, investigating server-level events typically requires reviewing the raw log file:
sudo tail -n 200 /var/log/clickhouse-server/clickhouse-server.log
Operators may also analyze DDL activity by querying ClickHouse’s system tables:
SELECT event_time, query
FROM system.query_log
WHERE query_kind = 'DDL'
ORDER BY event_time DESC;
Although these outputs provide useful telemetry, they exist across separate streams and formats. ClickHouse does not merge them into a structured audit record, leaving organizations to manually correlate operational events when building a compliance-grade audit trail.
DataSunrise Audit Log for ClickHouse
DataSunrise transforms fragmented ClickHouse telemetry into a fully normalized audit layer with correlation, enrichment, policy enforcement, and compliance automation.
1. Cluster-Wide Unified Audit Log
DataSunrise creates a unified audit view across the entire ClickHouse deployment by consolidating query logs, authentication events, RBAC activity, server-level operations, session contexts, and sensitive object mappings. Instead of leaving this telemetry scattered across multiple tables and log files, DataSunrise correlates it into a single chronological audit trail that dramatically improves visibility and ensures that analytical, administrative, or operational actions can all be traced with full context.
Additional information:
- Ensures node-level and cluster-level events appear in one timeline.
- Removes the need for manual log stitching across distributed ClickHouse environments.
- Provides consistent formatting regardless of the original log source.
- Enables long-term retention with immutable storage for forensic continuity.
References:
Audit Logs,
Data Activity History,
Database Activity Monitoring
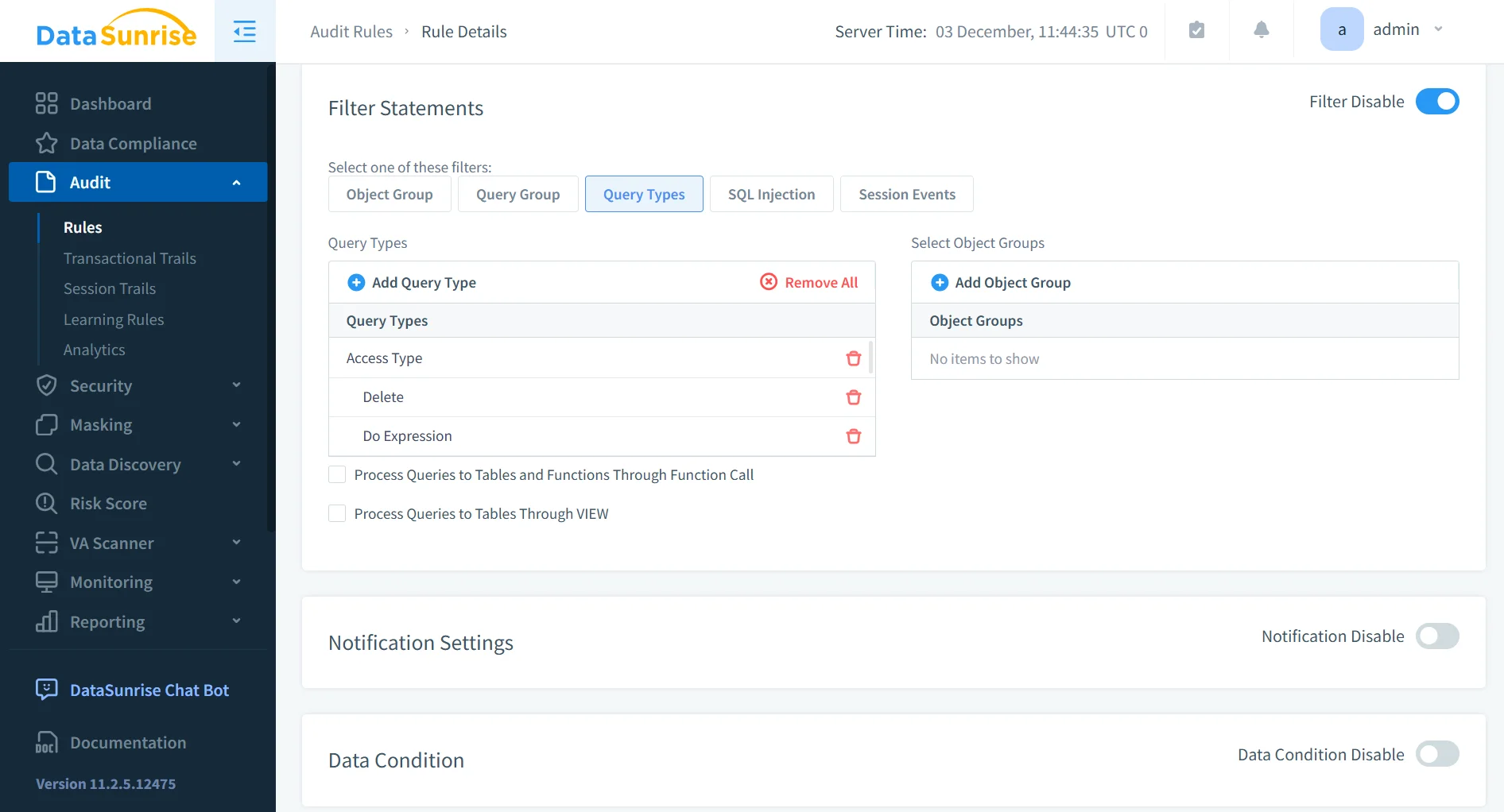
2. Granular & Targeted Audit Rules
DataSunrise allows organizations to define highly granular audit controls specifying which operations, tables, or columns must be monitored and under what conditions. Sensitive data access, DDL activity, administrative actions, or behavior exceeding configurable thresholds can all be logged with surgical precision. This ensures the audit trail remains efficient, purposeful, and aligned with compliance requirements.
Additional information:
- Rules can target individual users, roles, or entire application groups.
- Administrators can enable conditional auditing only for sensitive datasets.
- Supports separation of duties by isolating audit scope per team function.
- Reduces noise by capturing only activity that carries audit or compliance value.
References:
Audit Guide,
Rules Priority
3. Context-Rich Metadata Enrichment
DataSunrise enriches raw ClickHouse events with metadata that the native platform does not provide. Events are mapped to resolved identities, fingerprinted with application metadata, aligned with sensitivity classifications, and annotated with masking indicators or behavioral context. This transforms unstructured data into high-quality audit evidence reflecting intent, impact, and compliance relevance.
Additional information:
- Includes object-level sensitivity labels for PII, PHI, PCI, or custom taxonomies.
- Combines query context with user posture, session parameters, and risk scoring.
- Captures masked vs. unmasked data paths for compliance and audit verification.
- Makes downstream SIEM ingestion far more meaningful and structured.
References:
Data Discovery,
Role-Based Access Control
4. Real-Time Query Enforcement
DataSunrise not only records actions but enforces security policies the moment risky behavior occurs. It detects SQL injection attempts, privilege misuse, and anomalous actions identified through UEBA analytics. When necessary, DataSunrise immediately blocks high-risk operations, shifting auditing from passive observation to active, preventative defense.
Additional information:
- Enforcement occurs before ClickHouse executes the query.
- Policies can auto-penalize repeated suspicious behavior.
- Dynamic masking can be applied mid-session based on evolving risk.
- Integrates with notifications for instant security team alerting.
References:
Security Rules,
User Behavior Analysis
5. Automated Compliance Reporting
DataSunrise automatically generates compliance-ready reports mapped directly to SOX, GDPR, HIPAA, and PCI DSS requirements. These reports aggregate relevant activity, apply rule-based interpretation, and present audit evidence in formats suitable for regulators or internal auditors. This eliminates manual work and reduces friction during recurring audits.
Additional information:
- Reports can be scheduled, exported, or integrated into SIEM and GRC tools.
- Each audit record includes a compliance impact assessment.
- Supports multi-database compliance correlation across all platforms in scope.
- Reduces audit preparation time from weeks to minutes.
References:
Data Compliance,
Compliance Manager
Business Benefits
| Benefit | Description |
|---|---|
| Regulatory readiness | Verifiable audit evidence captured in a normalized, immutable structure. |
| Risk mitigation | Real-time enforcement prevents data misuse before exposure occurs. |
| Operational clarity | Complete user and query lineage across a distributed ClickHouse cluster. |
| Unified visibility | One auditing solution supporting over 40 data platforms. |
Conclusion
ClickHouse’s native logs provide valuable telemetry but fall short of delivering a complete, compliance-grade audit log. They lack correlation across nodes, contextual enrichment, immutability guarantees, and regulatory alignment.
DataSunrise converts these raw signals into a centralized, enriched, actionable audit trail suitable for modern governance requirements. With real-time threat prevention, granular rule configuration, automated compliance reporting, and multi-platform support, DataSunrise delivers the auditing foundation that ClickHouse environments require.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now