Data Audit for Amazon OpenSearch
Data Audit for Amazon OpenSearch is essential when teams rely on managed search clusters for analytics, observability, and security monitoring. Amazon OpenSearch often stores logs, events, traces, and business records that quickly drift into sensitive territory. Because multiple applications, users, and automated pipelines hit the same endpoints, you need a reliable way to prove who accessed what, when, and from where—without guessing during an incident.
According to AWS security guidance in the official Amazon OpenSearch documentation, auditability is a core control for protecting managed OpenSearch environments. Meanwhile, security standards such as ISO/IEC 27001 emphasize traceability and monitoring for access to data systems.
This guide explains how to implement a practical, investigation-ready data audit for Amazon OpenSearch using DataSunrise Data Audit. You will see how to define audit rules, validate transactional trails, reduce noise, and align auditing outputs with compliance goals—without changing index structures or rewriting application code.
Core Challenges of Data Audit for Amazon OpenSearch
Amazon OpenSearch behaves differently than relational databases. It exposes REST APIs, accepts JSON payloads, and supports bulk operations that can modify huge volumes of data in a single request. As a result, audit requirements shift from SQL-only visibility to protocol-aware tracking of operations across indices and endpoints.
API-driven access patterns
OpenSearch operations arrive as HTTP methods (POST, PUT, DELETE) and bulk calls. If you only rely on platform logs, you often lose the “why” and “who” behind each call. A strong audit logs strategy must capture request context, user/session identity, and affected indices.High-volume event streams
Many OpenSearch clusters handle thousands of requests per second. Without centralized filtering, auditing becomes noisy and expensive. Therefore, you need rules that target high-value events while still preserving an evidence-grade timeline for investigations.Sensitive payload exposure
Indexed documents often contain emails, identifiers, IPs, or financial fields. These fall under PII and similar regulated categories. If access is uncontrolled, you can end up with accidental exposure through search queries, exports, or dashboards.Compliance and forensics gaps
Frameworks and regulations require demonstrable, reviewable trails. If your audit evidence is scattered, incomplete, or inconsistent, auditors will not care that “the cluster is managed.” You still need clear audit trails, retention, and reportability across GDPR, HIPAA, PCI DSS, and SOX.
Auditing Amazon OpenSearch with DataSunrise
DataSunrise adds an external audit and security layer that works transparently between clients and Amazon OpenSearch. In practice, it operates as a controlled proxy and captures every request and response without modifying index structures or application logic. This approach fits modern database activity monitoring models and helps standardize auditing across diverse data stores.
Because policy enforcement happens outside OpenSearch itself, you can audit consistently even when multiple applications or tools access the same cluster. You also gain a centralized place to manage audit configuration, filtering, storage, and reporting.
Creating Audit Rules for Amazon OpenSearch Traffic
Audit rules define what should be captured and how audit events should be stored. For Amazon OpenSearch, rule design typically focuses on:
- Which endpoints and indices to monitor
- Which HTTP methods represent “meaningful” actions
- Which users, roles, or source networks require tighter scrutiny
- How to store evidence without flooding your storage backend
In DataSunrise, you can also control evaluation order with rules priority, which is critical when you want strict auditing for sensitive indices and lighter coverage for low-risk operational traffic.
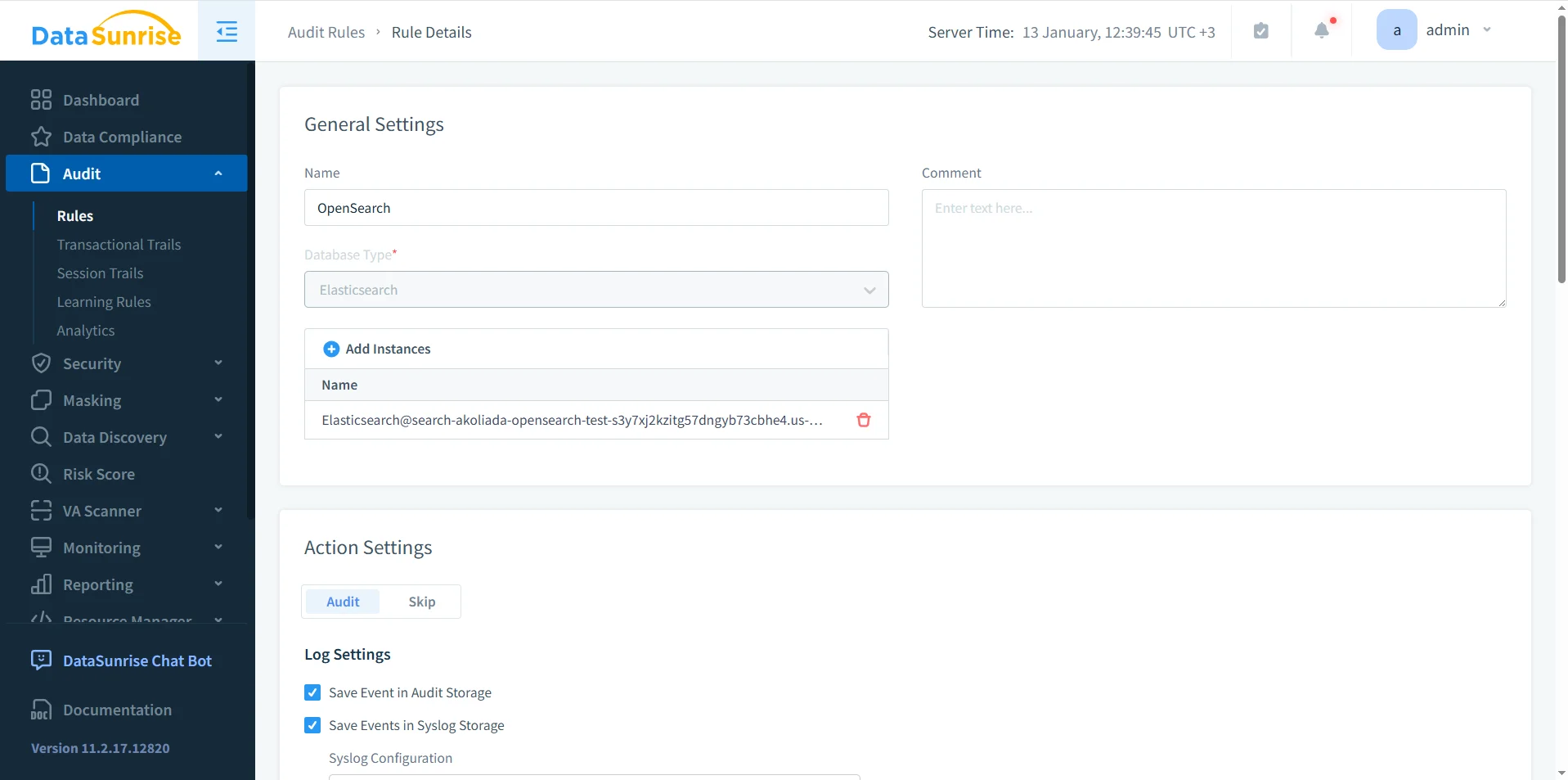
Once you bind an OpenSearch instance to an audit policy, DataSunrise begins capturing request metadata and building an investigation-friendly trail. If you want to bootstrap rule coverage faster, you can also use learning rules and audit to observe traffic patterns and derive baseline policies.
Transactional Audit Trails and Session Visibility for Amazon OpenSearch
After rule activation, DataSunrise records OpenSearch interactions into structured trails. Instead of hunting through fragmented logs, you can review events in data activity history and correlate operations across sessions. This is especially useful when one application call triggers multiple OpenSearch actions (bulk ingest, refresh, query, export).
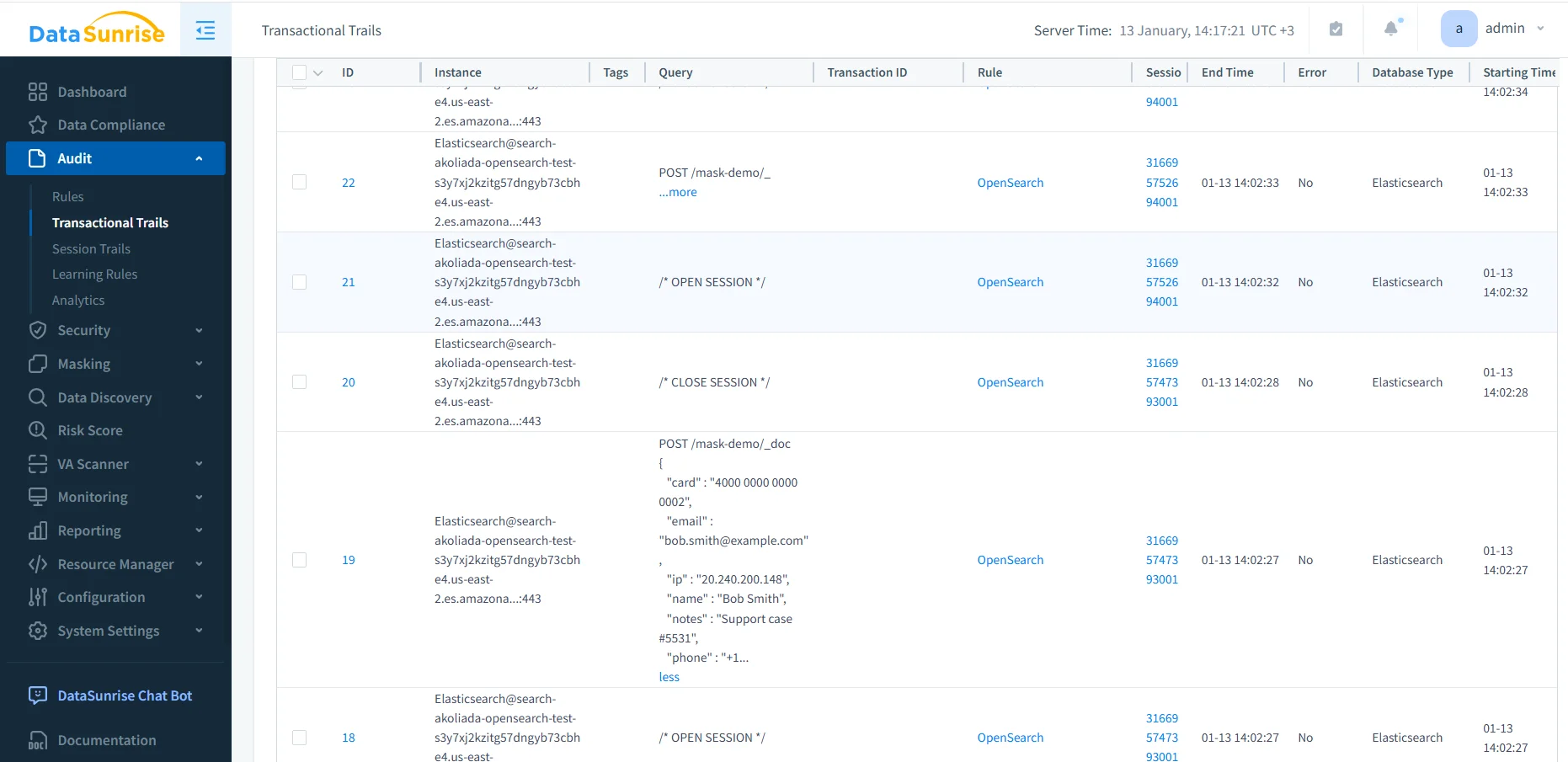
Captured evidence typically includes HTTP method, endpoint, index name, selected payload fragments, user/session identifiers, source IP, timestamps, and rule context. With this structure, a data audit for Amazon OpenSearch becomes usable during real investigations, not just “logging for compliance.”
What a Data Audit for Amazon OpenSearch Captures
Well-configured auditing should answer simple questions quickly: Who accessed an index? What did they search? Did they modify documents? Did they attempt destructive operations? DataSunrise audit coverage for Amazon OpenSearch commonly includes:
- Index creation, deletion, and configuration changes
- Document ingestion via POST and bulk APIs
- Search and aggregation queries
- Session open and close events
- Error responses and failed operations
Events can be stored in a dedicated audit repository or forwarded to SIEM tooling for correlation. Either way, it supports broader data security and database security operations.
For high-throughput OpenSearch clusters, start with targeted audit rules scoped to sensitive indices and destructive methods (DELETE, bulk updates). You will cut noise while keeping audit trails useful for investigations and compliance evidence.
DataSunrise Controls Beyond Auditing Amazon OpenSearch
Auditing is visibility. It tells you what happened. However, security teams usually need more than visibility—they need prevention and enforcement. DataSunrise extends Amazon OpenSearch protection with controls that work alongside audit trails.
Dynamic and Static Data Masking for Sensitive Fields
Audit records often reveal that non-production users and tools query sensitive fields more often than expected. With dynamic data masking, you can obfuscate sensitive values at query time while preserving index structure and search usability. For data copies, exports, or test environments, static data masking helps permanently transform values before the data leaves controlled boundaries.
Security Rules and Threat Detection
OpenSearch endpoints attract automation: scraping, enumeration, and brute-force query patterns. DataSunrise can enforce security controls using security rules and integrate detection patterns into broader monitoring workflows. When needed, you can also align defensive posture with a database firewall style model for blocking suspicious behavior.
Discovery and Classification Before You Audit Everything
If you do not know what is sensitive, you cannot audit smartly. DataSunrise data discovery helps identify regulated fields and data categories across your storage landscape. That discovery can then guide what indices should have strict auditing, masking, or additional approvals.
In many environments, teams also use a proxy approach for deployment. If you want the architectural pattern, review how reverse proxy security layers work for traffic inspection and policy enforcement.
Audit-Ready Reporting and Operational Evidence
Audit data that cannot be reviewed or reported is just expensive noise. DataSunrise supports report workflows using report generation, making it easier to produce evidence packets for auditors and internal reviews. For performance planning, it also helps to align audit retention with audit storage considerations, especially when OpenSearch traffic is high-volume.
Compliance Alignment
Auditing Amazon OpenSearch is not just a security best practice—it is typically required once regulated or sensitive data appears in indices. DataSunrise maps audit evidence into compliance programs and supports frameworks such as compliance regulations, plus specific obligations under GDPR, HIPAA technical safeguards, PCI DSS, and SOX.
| Regulation | Amazon OpenSearch Requirement | DataSunrise Support |
|---|---|---|
| GDPR | Trace access to personal data and support auditability | Centralized audit logs, searchable trails, evidence retention |
| HIPAA | Monitor access to PHI and detect unauthorized activity | Session-level auditing and investigation-ready trails |
| PCI DSS | Log access to payment-related data and administrative actions | Auditable access history plus reporting workflows |
| SOX | Accountability for changes and privileged access | Traceable audit trails and compliance reporting support |
For ongoing audits, automated evidence packaging through the Compliance Manager reduces manual effort and helps keep controls consistent over time.
Conclusion: Data Audit for Amazon OpenSearch That Actually Works
Amazon OpenSearch is excellent at searching and aggregating data, but it does not magically solve accountability. Without structured auditing, OpenSearch can become a blind spot where sensitive data moves fast and oversight moves slowly.
A strong data audit for Amazon OpenSearch must capture request context, preserve traceability across sessions, and produce usable evidence for both incident response and compliance. DataSunrise delivers centralized audit trails, operational monitoring, and compliance-ready reporting for OpenSearch environments. When you combine auditing with discovery, masking, and security controls, you get visibility and enforcement without breaking application workflows.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now