
Data Audit for Amazon S3

Introduction
Amazon S3 is one of the most widely used object storage services in the cloud. It holds everything from backups and logs to sensitive customer data and intellectual property. But unlike databases, object storage lacks native query auditing—making it easy for unauthorized access or data leakage to go undetected without proper monitoring in place.
A data audit for Amazon S3 helps organizations track access events, detect anomalies, and meet security and compliance requirements. This article explores native audit options like AWS CloudTrail and shows how DataSunrise enhances audit trails with context-rich visibility, masking, and real-time alerts.
The Importance of Data Audit for Amazon S3
S3 doesn’t behave like a database. There’s no SQL, no session, no DDL/DML. Every interaction is a discrete HTTP operation—GET, PUT, DELETE, etc.—issued through SDKs, APIs, or CLIs.
Auditing S3 is crucial because:
- Access is often distributed across hundreds of apps and users
- Breaches can occur through misconfigured buckets or IAM roles
- Sensitive files may be accessed or exfiltrated without detection
Tracking every S3 action ensures accountability, especially for regulated industries subject to GDPR, HIPAA, or PCI DSS.
Native Audit Logging with AWS CloudTrail
Amazon S3 integrates with AWS CloudTrail to capture API activity. These logs include:
- Event name (e.g.,
GetObject,PutObject,DeleteObject) - Bucket and object key
- IAM user or role
- Source IP
- Timestamp
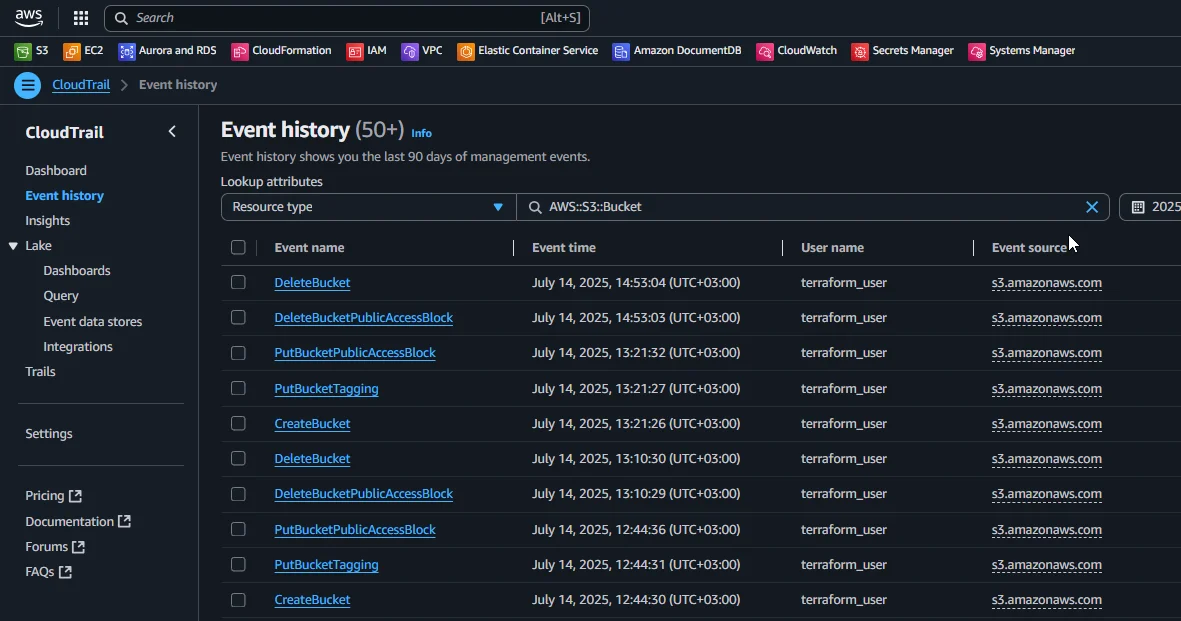
Example log snippet:
{
"eventName": "GetObject",
"requestParameters": {
"bucketName": "customer-archive",
"key": "records/2025_q2.csv"
},
"sourceIPAddress": "198.51.100.27",
"userIdentity": {
"type": "IAMUser",
"userName": "data_analyst"
},
"eventTime": "2025-07-25T12:34:56Z"
}
📝 CloudTrail logs are stored in S3 or streamed to CloudWatch, but querying and correlating them requires Athena or third-party tooling.
Limitations of Native S3 Audit
| Capability | AWS Native Tools |
|---|---|
| Real-time detection | ❌ Delayed |
| Policy-based masking | ❌ Not supported |
| Unified multi-bucket view | ❌ Manual setup |
| Alerts on sensitive access | ❌ Requires Lambda or custom scripts |
| Compliance reporting | ❌ Not audit-ready |
| Context-aware audit decisions | ❌ No |
CloudTrail shows “what happened,” but not “was it allowed?” or “was it sensitive?”—that context is critical for enterprise data security.
Enhanced Data Audit for Amazon S3 with DataSunrise
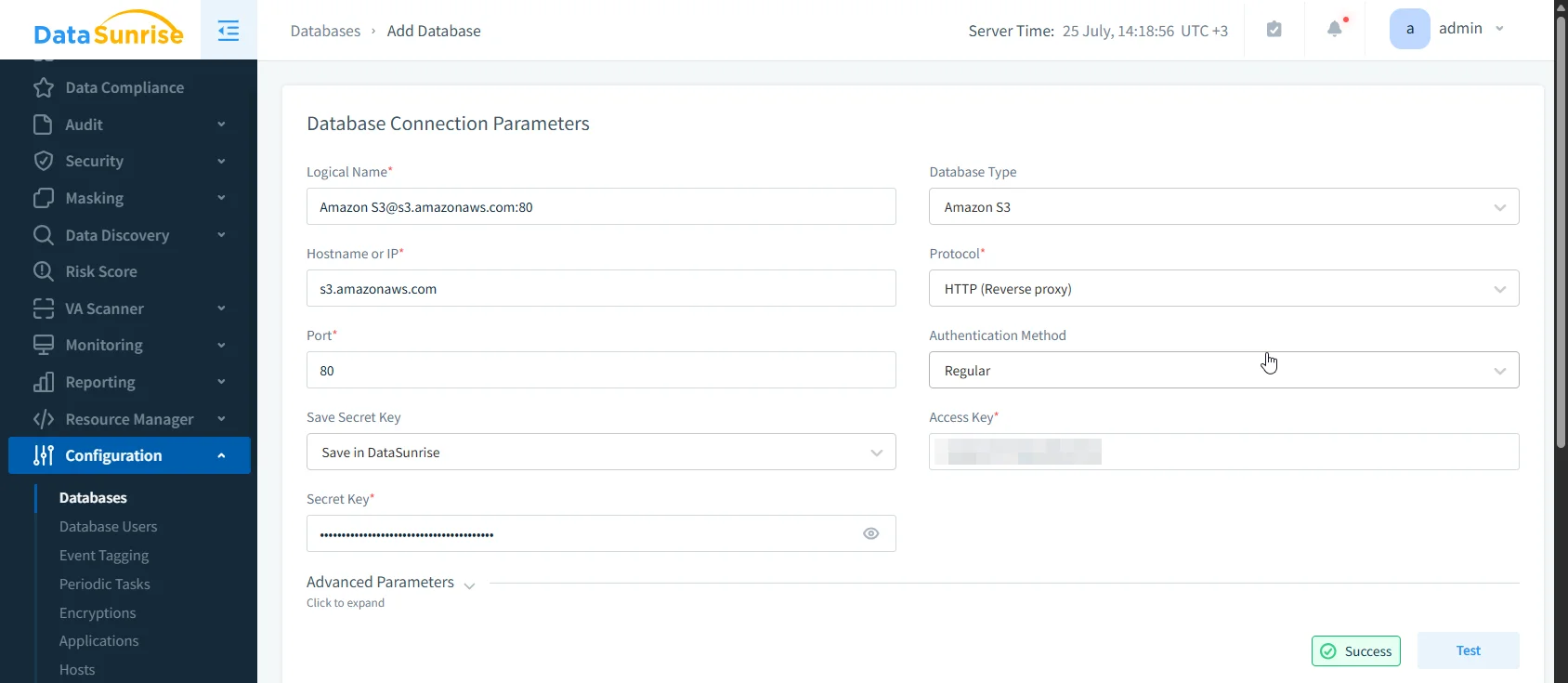
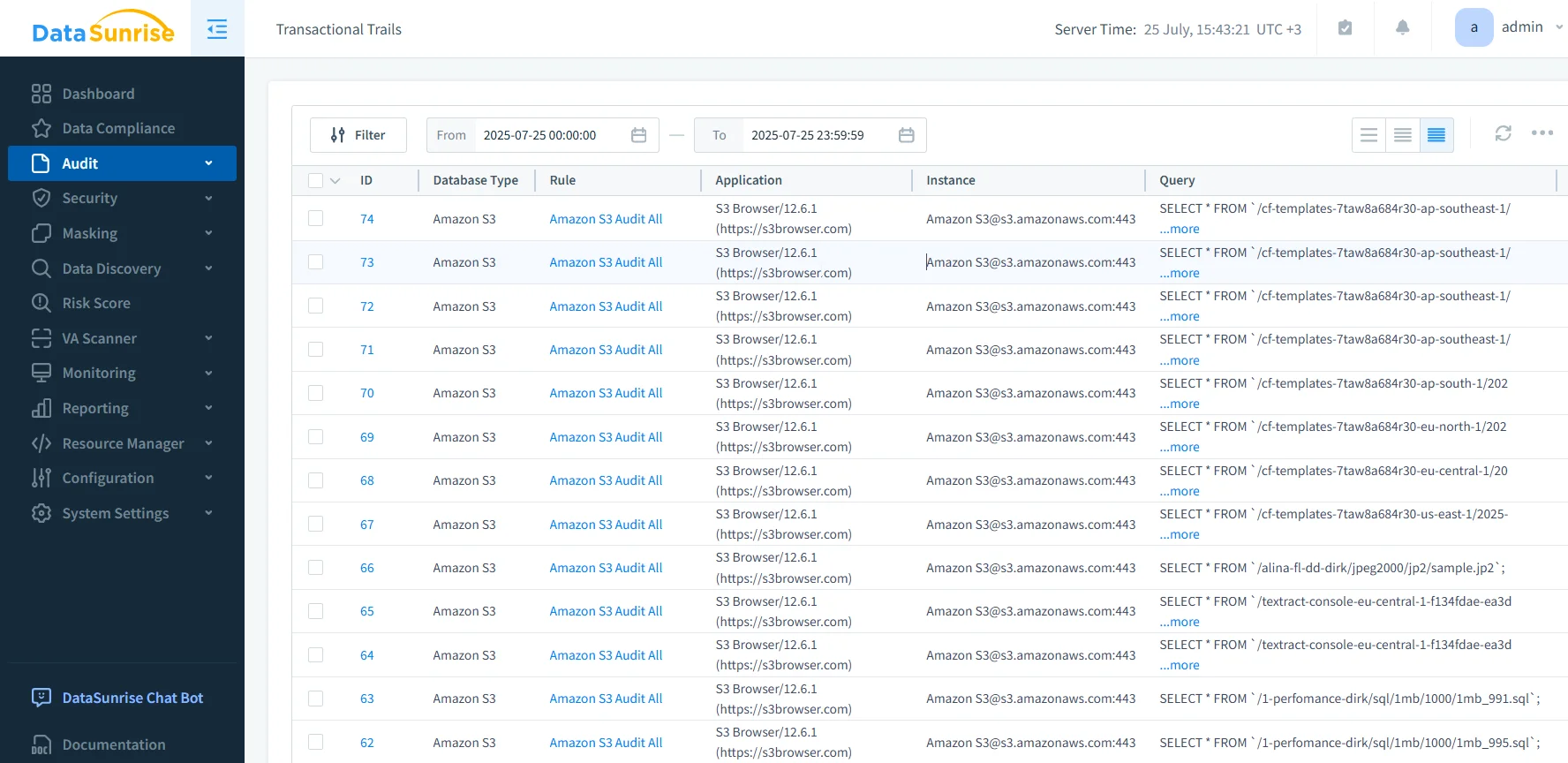
DataSunrise augments S3 audit capabilities by integrating with your S3 endpoints and centralizing audit logic in a zero-touch proxy architecture. You get real-time analysis of S3 API operations, deep content inspection, and customizable compliance workflows.
Key Features
- Sensitive data discovery across S3 buckets (text, JSON, CSV, logs, PDFs)
- Dynamic masking of confidential data during object access
- Real-time notifications for unauthorized actions or data exfiltration attempts
- Audit log export to SIEM or storage for long-term compliance
- Unified view across S3, RDS, Redshift, and more
- Automated compliance reporting for GDPR, SOX, and PCI
DataSunrise brings centralized audit enforcement to cloud-native environments like S3—something AWS alone cannot do without heavy scripting.
Data Audit in Amazon S3 DataSunrise
Connect S3 to DataSunrise using access credentials or IAM role assumption.
Navigate to Audit Rules.
Create a rule:
- Bucket:
sensitive-documents - User/IP:
internal-audit-team - Actions:
GET,DELETE - Masking: Enabled on object content with PII patterns
- Bucket:
Enable live alerting and configure log retention/export settings.
From this point on, all relevant access is logged, masked, and correlated—even across buckets and regions.
Business Benefits
By combining audit, security, and discovery into one solution, DataSunrise provides:
- Streamlined evidence collection for external audits
- Faster breach detection via behavior-based monitoring
- Simplified governance with centralized audit trail management
- Reduced operational overhead through no-code policy automation
Unlike raw CloudTrail logs, DataSunrise produces human-readable, audit-ready reports with full context—ready to present to auditors or compliance officers.
Conclusion
Auditing S3 means more than collecting logs. You need visibility, control, and the ability to respond in real time.
While AWS CloudTrail provides the raw events, DataSunrise delivers a full compliance and security layer on top—transforming event trails into actionable, policy-enforced insights.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now