Data Obfuscation in CockroachDB
In today's distributed database landscape, implementing robust data obfuscation strategies for CockroachDB has become essential for data security and regulatory compliance. According to recent research from Gartner, organizations with comprehensive data obfuscation reduce data exposure risk by up to 82% while maintaining operational efficiency.
CockroachDB, a cloud-native distributed SQL database, handles sensitive data across multiple nodes and geographic regions. With breach costs averaging $4.88 million in 2024 and regulations like GDPR, HIPAA, and PCI DSS imposing strict requirements, effective data obfuscation has become a business necessity. For more details on CockroachDB's architecture and security features, refer to the official CockroachDB documentation and security best practices guide.
This article explores CockroachDB's native capabilities and how DataSunrise enhances obfuscation with Zero-Touch Data Masking and No-Code Policy Automation.
Understanding Data Obfuscation in CockroachDB
Data obfuscation in CockroachDB disguises sensitive information to protect it from unauthorized access while maintaining utility for legitimate operations. This critical aspect of database security includes techniques such as dynamic data masking, tokenization, database encryption, and anonymization.
CockroachDB's distributed architecture requires special considerations:
- Multi-node data replication demanding consistent obfuscation policies
- Geographic distribution requiring location-aware strategies aligned with data compliance regulations
- High availability architecture needing seamless obfuscation during failures
- Performance at scale maintaining CockroachDB's characteristics
- Distributed transactions requiring consistent data security policy application
Native CockroachDB Data Protection Capabilities
CockroachDB provides built-in data protection features:
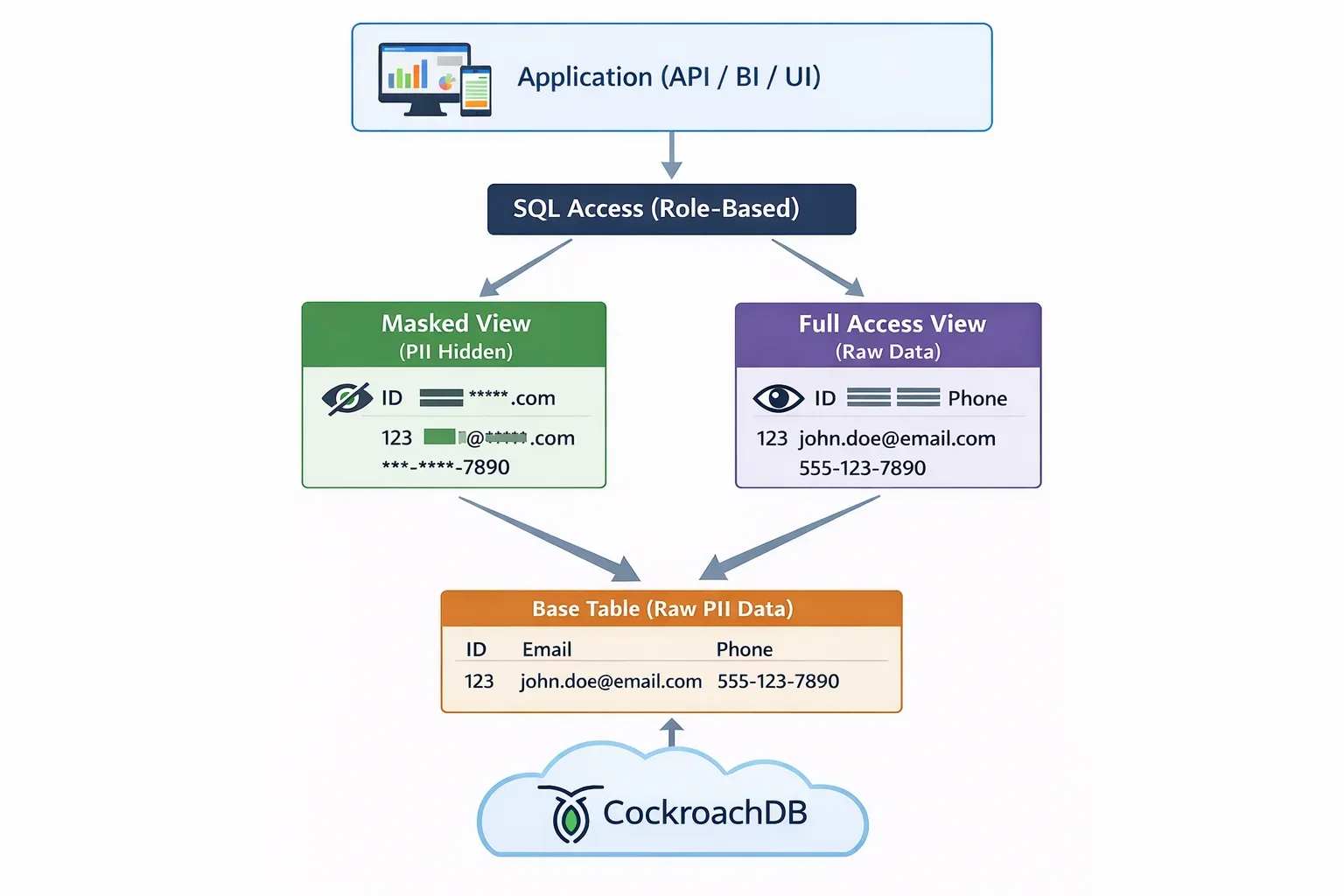
1. Role-Based Access Control (RBAC)
Implement role-based access controls to restrict data visibility:
-- Create role and grant permissions
CREATE ROLE analyst;
GRANT SELECT ON TABLE customers TO analyst;
GRANT SELECT (customer_id, first_name, email) ON TABLE customers TO analyst;
2. Views for Data Abstraction
-- Create view with masked sensitive data
CREATE VIEW customers_masked AS
SELECT
customer_id,
first_name,
CONCAT(SUBSTRING(email, 1, 2), '***@***', SUBSTRING(email FROM '@.*')) AS email_masked,
CONCAT('***-**-', SUBSTRING(ssn, 8, 4)) AS ssn_masked
FROM customers;
Enhanced Data Obfuscation with DataSunrise
DataSunrise significantly enhances data obfuscation through Autonomous Compliance Orchestration designed for distributed databases. Unlike basic view-based approaches, DataSunrise delivers enterprise-grade data masking with Zero-Touch implementation.
Setting Up DataSunrise for CockroachDB Data Obfuscation
1. Connect to CockroachDB: Establish a secure connection through the administrative interface supporting all deployment models.
2. Auto-Discover Sensitive Data: DataSunrise automatically scans and classifies sensitive data using NLP and machine learning to detect PII, financial, and health data.
3. Create Masking Rules: Configure policies using No-Code Policy Automation with column-level, role-based, and context-aware obfuscation.
4. Monitor and Analyze: Access analytics through the unified dashboard for policy effectiveness and compliance status.
Key Advantages of DataSunrise for CockroachDB
| Feature | Description |
|---|---|
| Surgical Precision Masking | Granular rules at column, row, or cell level with dynamic masking adapting in real-time |
| No-Code Policy Automation | Create policies without SQL, reducing implementation from weeks to hours |
| Intelligent Data Discovery | Automatically identify sensitive data using NLP and machine learning |
| Context-Aware Protection | Adapt based on user roles, application context, and query patterns |
| Compliance Autopilot | Maintain alignment with GDPR, HIPAA, PCI DSS, and SOX |
| Real-Time Notifications | Immediate alerts for policy triggers |
| Cross-Platform Consistency | Uniform policies across over 40 data storage platforms |
Advanced Data Obfuscation Techniques with DataSunrise
DataSunrise supports multiple obfuscation methods optimized for CockroachDB:
Dynamic Data Masking: Real-time obfuscation during query execution – character masking, partial masking, randomization, and nullification providing access controls based on user context.
Static Data Masking: Permanent obfuscation for non-production with database cloning, test data management, and data sampling supporting data-driven testing.
Tokenization: Replace sensitive data with tokens maintaining referential integrity through format-preserving tokenization and secure distributed token vaults.
Data Anonymization: Irreversible transformation with k-anonymization, differential privacy, and data generalization techniques ensuring data accessibility without compromising privacy.
Use Cases for Data Obfuscation in CockroachDB
Healthcare: Protect PHI in electronic health records while enabling research and analytics in HIPAA compliance, safeguarding personally identifiable information.
Financial Services: Secure payment data and account details across distributed banking applications meeting PCI DSS requirements with comprehensive security rules and threat detection.
E-Commerce: Safeguard customer information and purchase history while enabling personalized marketing, implementing proper data management practices.
SaaS Applications: Protect multi-tenant data ensuring tenant isolation and privacy with static data masking for development environments.
Development/Testing: Create realistic non-production environments with obfuscated data following the principle of least privilege.
Conclusion
As organizations rely on CockroachDB for globally distributed applications, implementing robust data obfuscation is essential for database security and compliance. While CockroachDB provides foundational security through encryption and access controls, organizations with complex requirements benefit from enhanced solutions.
DataSunrise provides comprehensive data obfuscation for distributed databases, offering Zero-Touch Data Masking, Surgical Precision controls, and Automated Compliance Reporting. With flexible deployment modes, DataSunrise transforms data obfuscation into a strategic security asset.
Unlike solutions requiring constant tuning, DataSunrise delivers autonomous protection adapting to evolving threats and regulations. The platform combines user-friendly interfaces with granular controls, enabling enterprise-grade obfuscation in days rather than months.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now