Data Obfuscation in MongoDB
Modern applications built on MongoDB frequently handle highly sensitive information, including customer records, authentication credentials, financial details, healthcare data, and operational telemetry. Although MongoDB offers native encryption and access control mechanisms, protecting sensitive values in real time requires additional safeguards beyond basic configuration. For reference, MongoDB’s official security documentation outlines its built-in authentication and encryption capabilities.
Data obfuscation in MongoDB reduces exposure risk by transforming sensitive fields into masked or unreadable formats while preserving document structure and maintaining application functionality. Instead of blocking access entirely, obfuscation limits visibility, ensuring that only appropriate portions of data remain accessible. This approach aligns with broader principles of data security, where minimizing exposure is just as important as preventing unauthorized access.
Unlike encryption, which protects data at rest or in transit, obfuscation minimizes exposure during query execution and user interaction. This distinction is especially important in development environments, analytics pipelines, third-party integrations, and internal support workflows, where broad database access may be operationally necessary but full data visibility is not. Industry research from IBM’s Cost of a Data Breach Report further highlights the financial impact of exposure incidents and reinforces the need for layered protection strategies.
As regulatory frameworks such as GDPR, HIPAA, and PCI DSS impose stricter accountability standards, structured and controlled obfuscation becomes a critical component of secure MongoDB deployments. Organizations must ensure that sensitive information remains protected not only from external threats but also from unnecessary internal exposure. Implementing dynamic data masking alongside obfuscation strategies strengthens compliance posture and reduces operational risk.
This guide examines native MongoDB mechanisms related to obfuscation, demonstrates practical implementation approaches, outlines the limitations of manual methods, and explains how DataSunrise enables autonomous, enterprise-grade data obfuscation for MongoDB environments.
What is Data Obfuscation?
Data obfuscation is a security technique that transforms sensitive information into a modified format that prevents direct interpretation while preserving the usability of the underlying dataset. Unlike encryption, which requires cryptographic keys for decryption, obfuscation focuses on limiting human readability and reducing exposure during access, analytics, and operational workflows.
In database environments such as MongoDB, obfuscation typically applies to fields containing personally identifiable information (PII), financial attributes, health records, credentials, or proprietary business data. Instead of returning full values, the system replaces them with masked, truncated, randomized, or tokenized equivalents. For example:
- Displaying only the last four digits of a credit card number
- Replacing email addresses with partially hidden formats
- Substituting names with realistic but fictional values
- Randomizing identifiers while preserving format
The objective is not to permanently encrypt data, but to minimize unnecessary exposure while maintaining structural consistency for applications, reporting tools, and analytics processes.
Data obfuscation can be implemented in multiple ways:
- Static obfuscation, where data is transformed before being copied to non-production environments (see static data masking)
- Dynamic obfuscation, where data is modified in real time during query execution (see dynamic data masking)
- Context-aware obfuscation, where transformation depends on user roles, source IP, or access policies
When properly implemented, obfuscation supports principles such as least privilege and zero-trust data access. It allows teams to work with operational datasets without exposing full sensitive values, reducing insider risk and helping organizations meet regulatory obligations.
In MongoDB deployments, data obfuscation becomes especially important in environments where developers, analysts, third-party vendors, or support teams require access to production-like data but should not see raw confidential information.
Native Approaches to Data Obfuscation in MongoDB
MongoDB does not provide a built-in obfuscation engine. However, administrators can combine several native capabilities to approximate limited protection of sensitive data. These approaches can reduce exposure in specific scenarios, but they do not provide centralized, policy-driven obfuscation.
1. Field Projection and Redaction
Developers can use field projection to exclude sensitive attributes from query results. For example, the following query hides Social Security numbers and credit card fields and another approach involves using aggregation pipelines to conditionally transform values. In the example below, the email field is partially masked:
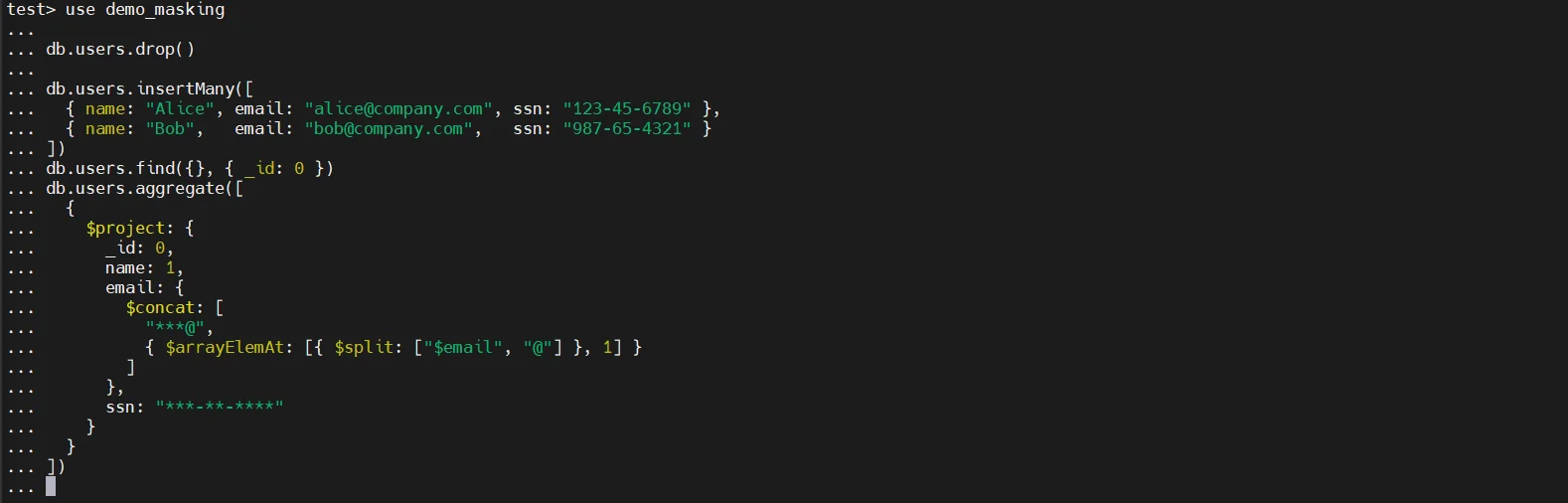
This method allows partial masking through query logic. However, it requires developers to embed masking rules directly into application queries. As a result, protection depends entirely on consistent implementation across all services and integrations.
2. Client-Side Field Level Encryption (CSFLE)
MongoDB supports Client-Side Field Level Encryption (CSFLE), which encrypts selected fields before they are written to the database. This provides strong cryptographic protection for sensitive attributes.
Below is a simplified example of inserting an encrypted field using CSFLE in MongoDB (Node.js example):
const { MongoClient } = require("mongodb");
const client = new MongoClient(uri, {
autoEncryption: {
keyVaultNamespace: "encryption.__keyVault",
kmsProviders: {
local: {
key: Buffer.from(process.env.LOCAL_MASTER_KEY, "base64")
}
}
}
});
async function run() {
await client.connect();
const db = client.db("sales");
const collection = db.collection("customers");
await collection.insertOne({
name: "Alice Johnson",
ssn: "123-45-6789", // Automatically encrypted
credit_card_number: "4111111111111111" // Automatically encrypted
});
}
run();
In this configuration, sensitive fields such as ssn and credit_card_number are encrypted on the client side before being stored in MongoDB.
While effective for encryption use cases, CSFLE is not a true obfuscation mechanism. It protects stored values but does not provide flexible, context-aware masking during query execution.
3. Role-Based Access Controls (RBAC)
MongoDB supports granular permissions through Role-Based Access Controls (RBAC). Administrators can define custom roles with specific privileges, such as read-only access to selected collections.
db.createRole({
role: "limitedAccess",
privileges: [
{ resource: { db: "sales", collection: "customers" }, actions: [ "find" ] }
],
roles: []
})
RBAC restricts access at the database or collection level. However, once a user is granted permission to query a collection, the full content of accessible fields is returned.
There is no native mechanism for context-aware transformation of field values based on role, identity, or policy logic. RBAC controls access — it does not dynamically obfuscate data.
Data Obfuscation in MongoDB with DataSunrise
While MongoDB provides projection, encryption, and access control mechanisms, these tools do not deliver centralized, policy-driven obfuscation across environments. Enterprise deployments require consistent enforcement, automated discovery, and regulatory alignment without modifying application logic.
DataSunrise delivers Zero-Touch Data Masking and Obfuscation for MongoDB, enabling real-time protection through a non-intrusive architecture. Operating in Proxy, Sniffer, or Native Log Trailing modes, the platform integrates seamlessly into cloud, on-premise, and hybrid infrastructures without requiring application changes. Learn more about Reverse Proxy mode and available deployment modes.
Autonomous Sensitive Data Discovery
Before obfuscation policies can be enforced, sensitive fields must be identified. DataSunrise performs automated Sensitive Data Discovery across structured and semi-structured MongoDB documents, including JSON-based datasets.
The discovery engine identifies personally identifiable information (PII), financial attributes, authentication credentials, and health-related records. By automating this process, organizations eliminate manual field mapping and significantly accelerate time-to-compliance while reducing human error.
No-Code Obfuscation Policy Management
DataSunrise enables administrators to configure obfuscation policies through a centralized interface. Policies are defined once and enforced consistently across all connected MongoDB environments.
Supported transformation methods include static pattern replacement, partial value reveal (such as exposing only the first four digits), randomized or tokenized substitution, and context-aware display based on role, identity, or source.
These capabilities support Zero-Trust Data Access, Surgical Precision Masking, and centralized policy governance without altering application queries or business logic.
Real-Time Context-Aware Enforcement
Obfuscation is dynamically applied during query execution. Enforcement logic adapts based on user identity, role and privilege level, source IP or network segment, query type, and regulatory scope.
Unlike static masking techniques, this model enables Continuous Regulatory Calibration across production, staging, analytics, and testing environments, ensuring that sensitive values are consistently protected according to policy and compliance requirements.
Compliance Autopilot Integration
Data obfuscation is integrated into DataSunrise’s broader compliance framework. Through Compliance Autopilot, MongoDB environments remain continuously aligned with regulatory requirements such as GDPR, HIPAA, PCI DSS, and SOX.
Organizations can review full compliance coverage and leverage automated reporting via Compliance Manager.
This ensures audit-ready reporting, one-click compliance evidence, real-time regulatory alignment, and elimination of compliance drift.
Unified Security Framework
DataSunrise extends beyond obfuscation to deliver a centralized security architecture that combines Data Obfuscation, Dynamic Masking, Static Masking, Database Firewall, Database Activity Monitoring, and Behavior Analytics.
Additional information on Dynamic Data Masking explains how runtime transformation enhances sensitive data protection.
The platform supports SQL and NoSQL databases, data lakes, and cloud storage systems across heterogeneous environments. A full list of supported systems is available here: More than 50 data storage platforms.
Unlike solutions that require constant rule adjustments, DataSunrise delivers autonomous protection through ML-driven adaptation and centralized governance. Through unified visibility and automated enforcement, it enables enterprise-grade data obfuscation in MongoDB while reducing operational overhead and compliance risk.
Comparison: Native MongoDB vs DataSunrise Data Obfuscation
| Capability | Native MongoDB | DataSunrise |
|---|---|---|
| Field Masking | Manual query-based projection | Centralized, no-code policy enforcement |
| Context-Aware Control | Not supported | Role-, identity-, and IP-based dynamic obfuscation |
| Sensitive Data Discovery | Manual identification | Automated discovery engine |
| Compliance Support | No built-in automation | Integrated Compliance Autopilot (GDPR, HIPAA, PCI DSS, SOX) |
| Reporting | Limited, external tools required | Audit-ready automated reporting |
| Deployment | Application-dependent | Proxy, Sniffer, Native Log Trailing modes |
Native MongoDB provides foundational controls. DataSunrise delivers centralized, autonomous data obfuscation with compliance alignment and reduced operational overhead.
Conclusion
MongoDB provides powerful database capabilities and essential security controls. However, native mechanisms such as projection, encryption, and access roles do not deliver centralized, compliance-aligned data obfuscation across complex enterprise environments.
DataSunrise enhances MongoDB with Zero-Touch Data Masking, Autonomous Compliance Orchestration through its Compliance Manager, Continuous Regulatory Calibration, and a Unified Security Framework supported by Database Activity Monitoring and advanced data security controls. Together, these capabilities provide consistent, policy-driven obfuscation with automated discovery, real-time enforcement, and regulatory alignment.
The platform is deployable across on-premise, cloud, and hybrid infrastructures without configuration complexity, enabling organizations to strengthen security posture while maintaining operational efficiency and compliance readiness.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now