Dynamic Data Masking in Vertica
Dynamic Data Masking in Vertica allows organizations to protect sensitive information in real time without changing database schemas or duplicating datasets. Vertica is commonly used as a high-performance analytics platform for reporting, data science, and large-scale processing. As a result, the same tables often serve many different consumers: analysts, BI dashboards, ETL pipelines, and machine learning workloads. Without proper controls, sensitive values such as names, card numbers, or contact details can easily appear in query results.
Static approaches to data protection, such as manually created views or masked table copies, do not scale in Vertica environments. Schemas evolve, projections multiply, and new users gain access frequently. Dynamic data masking addresses this challenge by applying protection at query time, ensuring that sensitive values are hidden based on policy, not on how the data is stored, and aligns with broader data security requirements.
In Vertica, where performance and concurrency are critical, dynamic masking must operate transparently and efficiently. This is why many organizations deploy an external masking layer that intercepts SQL queries and rewrites result sets before data reaches the client, often as part of centralized database activity monitoring.
Dynamic masking works best when combined with automated data classification. Identifying sensitive columns early ensures that new tables and projections inherit protection automatically through data discovery.
Why Dynamic Masking Is Essential in Vertica
Vertica’s columnar architecture and projection model are optimized for fast analytics, not for fine-grained data redaction. A single logical column may appear in multiple projections, and analytical queries often retrieve large result sets. Once a query returns data, Vertica itself does not distinguish between sensitive and non-sensitive values.
Several common scenarios increase the risk of data exposure:
- BI users exporting query results that include personal identifiers.
- Data scientists exploring customer datasets in SQL editors or notebooks.
- ETL jobs moving data into downstream systems without filtering sensitive columns.
- Shared Vertica clusters accessed by both internal teams and external contractors.
Role-based access control alone cannot handle these cases. RBAC decides who can query a table, but it does not decide which values within that table should be visible. Dynamic data masking fills this gap by enforcing column-level protection dynamically, based on context, and complements role-based access control rather than replacing it.
For a deeper look at how Vertica stores and accesses data internally, see the official Vertica architecture documentation.
How Dynamic Data Masking Works with Vertica
Dynamic data masking for Vertica is typically implemented using a proxy-based architecture. Client applications connect to a masking gateway instead of connecting directly to Vertica. Every SQL query passes through this gateway, where policies are evaluated before execution.
The masking engine performs several steps:
- Analyzes the SQL statement and identifies referenced columns.
- Checks whether any of those columns are classified as sensitive.
- Evaluates masking rules based on user, application, and connection context.
- Rewrites the result set so that sensitive values are masked.
The underlying Vertica tables and projections remain unchanged. Masking happens only in the returned results, which preserves performance and avoids data duplication. This enforcement model aligns with centralized data compliance strategies.
This approach aligns with the principles described in data security best practices and modern compliance frameworks such as GDPR.
Dynamic Masking Rule Configuration in Vertica
The screenshot below shows a dynamic masking rule configured for a Vertica database instance. In this example, the rule applies to a specific database user and targets sensitive columns discovered earlier.
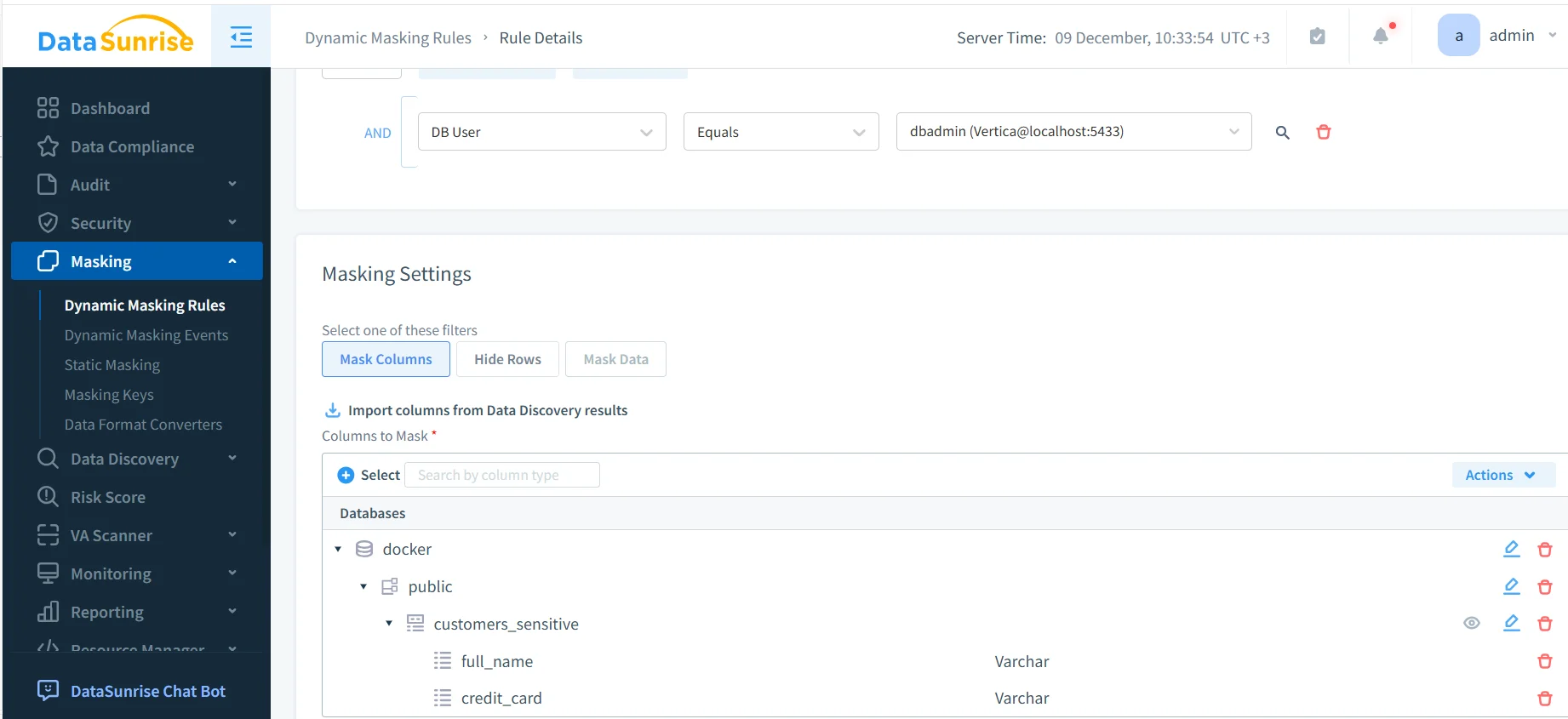
Dynamic masking settings for sensitive Vertica columns.
In this configuration, the administrator selects the database, schema, and table that contain sensitive data. Columns such as full_name and credit_card are explicitly added to the masking rule. Once the rule is active, these fields are automatically masked whenever an unauthorized user queries the table.
Masking rules can be tailored in several ways:
- Apply only to specific database users or roles.
- Apply only when queries originate from certain applications.
- Use different masking formats depending on sensitivity.
Dynamic masking does not change stored data. Any downstream system that bypasses the masking layer may still receive unmasked values if direct database access is allowed, which is why masking is often combined with database audit trails.
Masked Query Results in Practice
From the user’s perspective, dynamic masking does not change how queries are written. Analysts and applications issue standard SQL queries, and Vertica executes them as usual. The difference appears only in the returned values.
For example, consider the following query:
/*
SELECT
id,
full_name,
SUBSTR(email, 1, 5) AS email_prefix,
credit_card,
phone
FROM customers_sensitive;
*/
Without masking, this query would return real names, card numbers, and phone details. With dynamic masking enabled, non-privileged users see masked or pseudonymized values instead.
Crucially, aggregates, joins, and filters continue to work correctly. Analysts can still group, count, and analyze data, but sensitive values never appear in clear text, preserving principle of least privilege enforcement.
Auditing and Visibility for Masked Queries
Dynamic masking alone is not enough for compliance. Organizations must also demonstrate that masking was applied consistently and correctly. This is where auditing becomes essential.
Every masked query generates an audit record that includes:
- The database user and client application.
- The executed SQL statement.
- Which masking rule was triggered.
- The time and context of execution.
These records form a centralized audit trail that compliance teams can review during internal checks or external audits. Instead of parsing multiple Vertica system tables, teams get a unified view of data access and protection events, supporting database activity history.
This audit model complements database activity monitoring and simplifies evidence collection for regulations such as HIPAA and SOX.
Dynamic Masking vs Other Protection Approaches
| Approach | How It Works | Limitations in Vertica |
|---|---|---|
| Static masked tables | Create copies with sensitive data removed | Data duplication, high maintenance, schema drift |
| SQL views | Expose masked columns via predefined views | Bypassed by ad-hoc queries, fragile over time |
| RBAC only | Restrict access at table or schema level | No column-level protection, no contextual logic |
| Dynamic data masking | Rewrite results at query time | Requires external enforcement layer |
Best Practices for Dynamic Data Masking in Vertica
To get the most value from dynamic data masking, teams typically follow these practices:
- Start with classification. Use discovery to map sensitive fields first.
- Keep policies central. Avoid scattering masking logic across views.
- Test with real queries. Validate masking using production-like workloads.
- Monitor continuously. Review audit trails and risk indicators regularly.
Conclusion
Dynamic Data Masking in Vertica enables organizations to protect sensitive information without sacrificing analytical flexibility or performance. By applying masking at query time, teams avoid fragile workarounds such as copied tables or custom views.
Combined with centralized auditing, policy management, and discovery, dynamic masking provides a scalable foundation for secure analytics in Vertica. It allows organizations to expand data access confidently, knowing that sensitive information remains protected across every query and workload.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now