Google Cloud SQL Data Governance
Google Cloud SQL Data Governance has become a priority for organizations running relational workloads in the cloud. Cloud SQL supports PostgreSQL, MySQL, and SQL Server, but responsibility for security and compliance remains shared: Google maintains infrastructure, while customers must manage auditing, masking, discovery, and reporting. For teams working under GDPR, HIPAA, or PCI DSS, a clear governance strategy is not optional—it is required.
This article explores how governance can be achieved with Cloud SQL’s native tools and with DataSunrise, focusing on audit, security, and compliance.
Governance Priorities in Cloud SQL
Strong governance involves continuous monitoring of database activity, managing sensitive data exposure, and aligning operational practices with regulation. In Cloud SQL, these priorities translate into three practical areas:
- Auditing user and system activity to understand who did what.
- Protecting data through masking and role-based controls.
- Discovering sensitive fields so policies can be applied effectively.
Each of these areas can be addressed with native configuration or extended through advanced tools.
Native Audit Configuration
Google Cloud SQL integrates with Cloud Audit Logs and IAM to capture administrative actions. For SQL-level auditing, additional configuration is required.
In PostgreSQL, the pgAudit extension provides detailed records of statements. An example configuration looks like this:
-- Enable pgAudit
CREATE EXTENSION pgaudit;
-- Log read, write, and role activity
ALTER SYSTEM SET pgaudit.log = 'read, write, role';
-- Reload configuration
SELECT pg_reload_conf();
The resulting logs can be exported into Cloud Logging or BigQuery for retention and analysis.
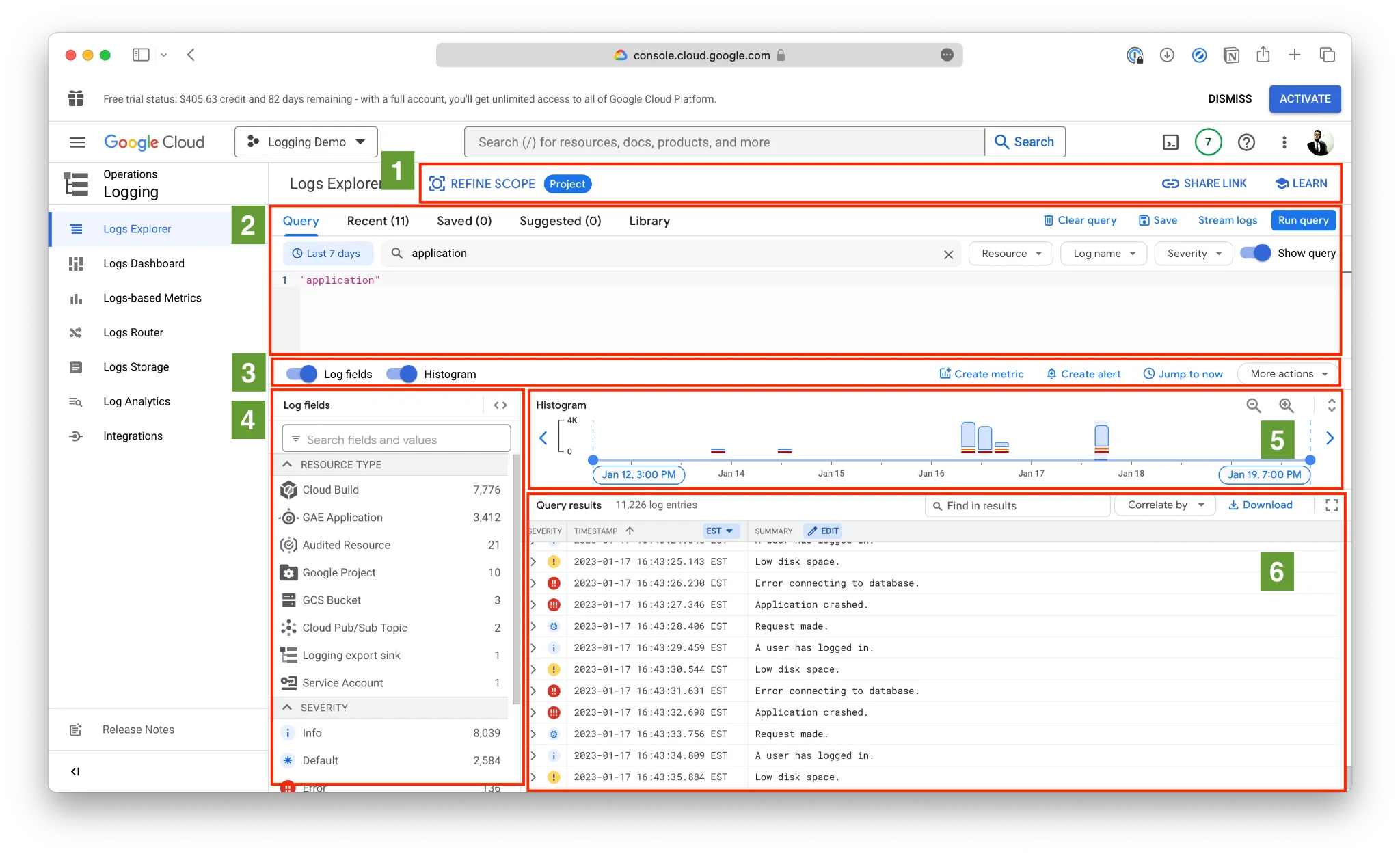
For MySQL, Cloud SQL supports enabling the general_log flag to record activity. Administrators can then query the mysql.general_log table for user activity:
SELECT event_time, user_host, argument
FROM mysql.general_log
WHERE command_type = 'Query'
LIMIT 20;
While these logs provide transparency, they are fragmented across instances and lack built-in tools for correlation, which complicates large-scale compliance.
Discovery and Masking
Cloud SQL does not include automated data discovery. Teams often rely on schema reviews or manual scans to identify personal or financial data. This limitation can delay compliance projects, especially in environments with many databases.
Masking is also limited natively. Developers can create views or stored procedures to hide sensitive fields. For example, a SQL Server instance could expose only the last four digits of a card number:
CREATE VIEW masked_cards AS
SELECT
CONCAT('XXXX-XXXX-XXXX-', RIGHT(card_number, 4)) AS card_display,
customer_id
FROM payments;
However, this approach requires schema changes and applies the same masking to all users, without considering context or role.
DataSunrise for Governance
DataSunrise enhances Cloud SQL governance without altering database design. It acts as a proxy, intercepting queries in real time.
Its Audit features provide centralized, tamper-proof audit trails across all instances. Unlike native logs, audit rules can be created to capture specific query types or sensitive fields, and results can be sent directly to SIEM platforms.
For sensitive data, dynamic data masking hides values depending on the user’s role or session context, ensuring that a developer sees masked information while a compliance officer has full visibility.
Finally, Data Discovery automatically scans Cloud SQL schemas for PII and regulated fields, building an inventory that feeds into both masking and auditing policies.
Security and Compliance
While Cloud SQL provides IAM-based access control and network security, threats like injection or misuse require deeper defenses. DataSunrise applies behavior analytics and role-based access control to detect anomalies such as bulk exports or repeated login failures.
For compliance, DataSunrise Compliance Manager automates reporting against frameworks like SOX, PCI DSS, and HIPAA. Instead of manually correlating logs, teams can generate audit-ready evidence with minimal effort.
Native Audit vs. DataSunrise Audit
Native Cloud SQL audit features are valuable but limited to instance-level visibility. They help answer “who executed what query,” but they require manual setup and export for compliance reporting.
By comparison, DataSunrise centralizes audit across platforms, enforces granular rules, and provides reports that map directly to compliance controls. This difference shifts governance from reactive log collection to proactive policy enforcement.
Business Value of Governance
Implementing structured Google Cloud SQL Data Governance improves resilience against security threats, reduces regulatory risk, and builds trust with customers. The combination of native logs and DataSunrise features offers both breadth and depth: Cloud SQL provides foundational records, while DataSunrise transforms them into actionable, compliant governance.
Conclusion
Google Cloud SQL offers the tools to begin governance—logging, IAM, and monitoring—but they leave gaps in discovery, masking, and compliance reporting. Augmenting native features with DataSunrise delivers a unified governance framework, ensuring that sensitive data remains secure, auditable, and compliant with global standards.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now