
How to Apply Data Governance for Percona Server for MySQL

Organizations that rely on Percona Server for MySQL handle significant volumes of sensitive, business-critical information every day. This may include customer records, payment card data, financial transactions, and intellectual property — all of which must be protected from unauthorized access or misuse. The risks are not limited to external attackers; insider threats and human errors also remain persistent challenges.
Global regulations such as GDPR, HIPAA, and PCI DSS continue to tighten requirements for data handling and reporting. According to the Verizon Data Breach Investigations Report 2024, system intrusions and data misuse are among the top causes of security incidents across industries. Without effective governance, organizations risk penalties, reputational damage, and operational disruption.
Percona Server for MySQL provides a strong technical foundation, extending standard MySQL with additional features for performance, reliability, and security. Capabilities like role-based access control (RBAC), audit plugins, and encryption help improve database oversight. However, these tools alone may not be enough to satisfy evolving compliance demands. Many organizations integrate specialized platforms such as DataSunrise, which extend Percona’s governance capabilities with advanced monitoring, masking, automated compliance reporting, and multi-environment policy management.
What is Data Governance?
Data governance refers to the set of policies, processes, and technologies that ensure data is accurate, secure, and used responsibly. It provides a framework for defining how data is accessed, protected, and audited across an organization.
Effective governance supports:
- Accountability – Defining roles and responsibilities for managing data.
- Compliance – Meeting external regulations like SOX, HIPAA, and GDPR.
- Security – Protecting sensitive data with encryption, masking, and access controls.
- Transparency – Maintaining audit trails that track who accessed or modified data.
In the context of Percona Server for MySQL, governance ensures that every query, role, and dataset is controlled under strict policies. This builds trust with stakeholders while minimizing compliance risks.
Native Governance Features in Percona
Role-Based Access Control (RBAC)
RBAC enables administrators to define roles with precise privileges, ensuring that only authorized individuals can access or modify sensitive information. For example:
- Administrators may have broad privileges for database management.
- Developers can be restricted to non-production schemas.
- Auditors can receive read-only access to logs and reports.
This fine-grained control helps enforce the principle of least privilege, minimizing the attack surface and preventing accidental exposure of confidential information. RBAC also simplifies compliance audits by showing a clear mapping between job roles and system permissions.
Practical SQL Examples:
-- Create roles
CREATE ROLE 'admin_role', 'dev_role', 'auditor_role';
-- Assign privileges
GRANT ALL PRIVILEGES ON *.* TO 'admin_role';
GRANT SELECT, INSERT, UPDATE, DELETE ON appdb.* TO 'dev_role';
GRANT SELECT ON appdb.* TO 'auditor_role';
-- Create users and assign roles
CREATE USER 'alice'@'%' IDENTIFIED BY 'StrongPassword#1';
CREATE USER 'dev_jane'@'%' IDENTIFIED BY 'StrongPassword#2';
CREATE USER 'aud_bob'@'%' IDENTIFIED BY 'StrongPassword#3';
GRANT 'admin_role' TO 'alice'@'%';
GRANT 'dev_role' TO 'dev_jane'@'%';
GRANT 'auditor_role' TO 'aud_bob'@'%';
-- Set default roles
SET DEFAULT ROLE 'admin_role' TO 'alice'@'%';
SET DEFAULT ROLE 'dev_role' TO 'dev_jane'@'%';
SET DEFAULT ROLE 'auditor_role' TO 'aud_bob'@'%';
Audit Logging
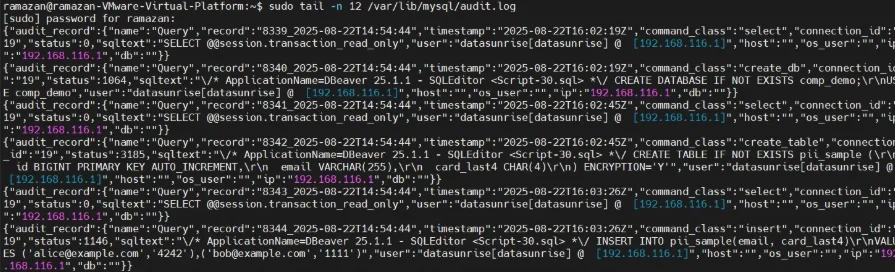
The audit log plugin captures queries, connections, and access attempts, producing a chronological record of database activity. This log is invaluable for investigating security incidents, proving compliance, and maintaining accountability.
INSTALL PLUGIN audit_log SONAME 'audit_log.so';
SET GLOBAL audit_log_policy = 'ALL';
Once enabled, the plugin records user logins, SQL queries, schema changes, and failed access attempts. Logs can later be exported for further audit trail analysis or integration with external database activity monitoring tools.
Encryption and Security
Percona Server for MySQL strengthens database security with built-in encryption and transport protection.
- Data at Rest: Encryption via keyring plugins ensures sensitive data on disk is secure.
- Data in Transit: SSL/TLS secures client-server communication, preventing interception or tampering.
- Backup Protection: Encrypted backups reduce the risk of exposure in case of storage compromise.
- Key Management: Integration with external key management systems provides safer rotation and lifecycle handling of encryption keys.
- Monitoring: Administrators can track encryption status and certificate validity to maintain continuous compliance.
These security measures are critical for compliance with standards like HIPAA and PCI DSS. However, they don’t prevent misuse by authorized users, highlighting the need for masking and behavioral analytics.
Applying Data Governance with DataSunrise
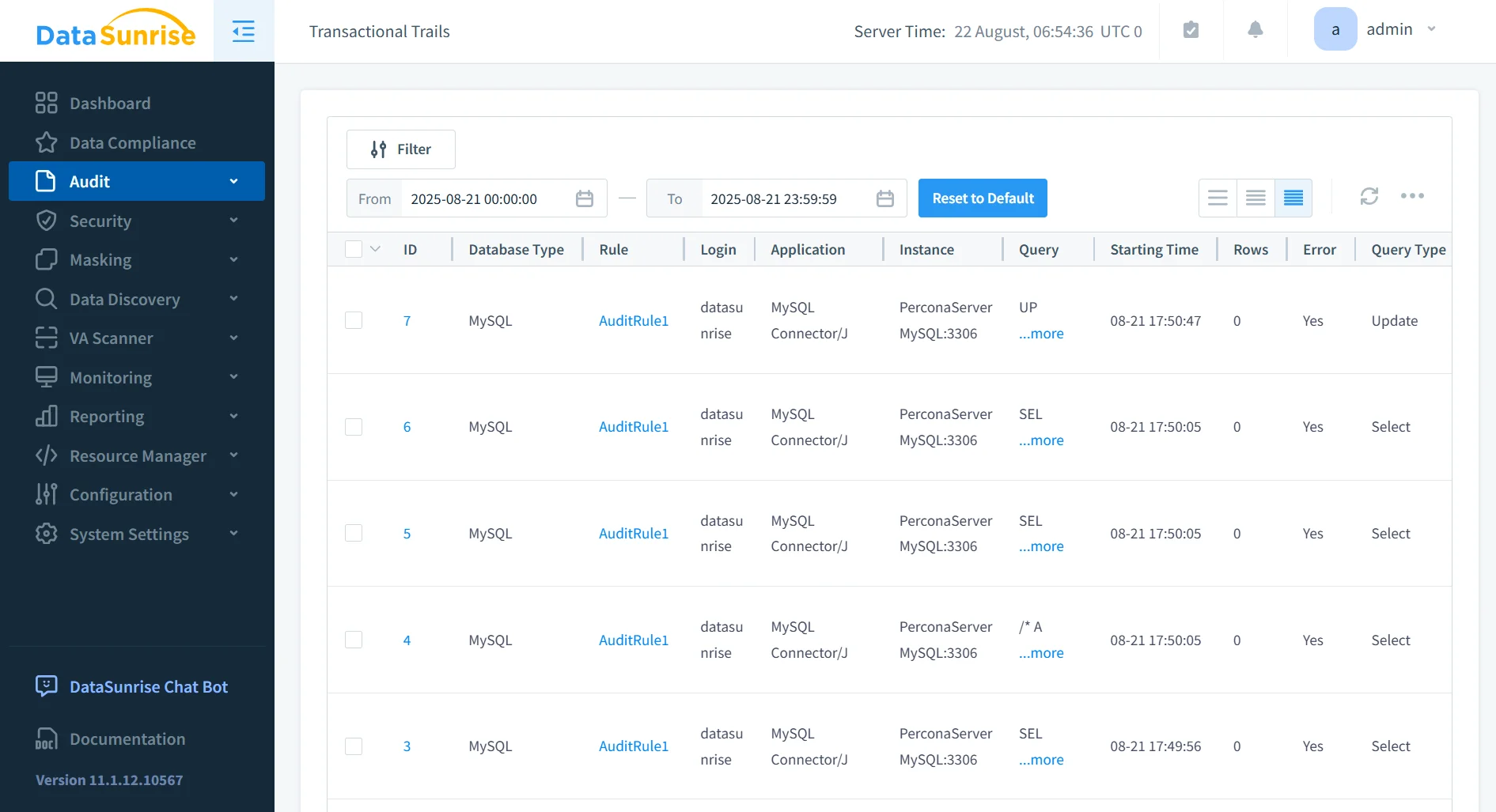
Centralized Audit Trails
With comprehensive audit logs, DataSunrise creates tamper-proof records across Percona and other databases. Unlike native audit logs, these can be viewed and analyzed centrally. Administrators gain unified visibility across hybrid environments, which reduces manual effort and enhances database activity monitoring. Centralized trails also simplify forensic analysis by maintaining consistent formats across multiple platforms.
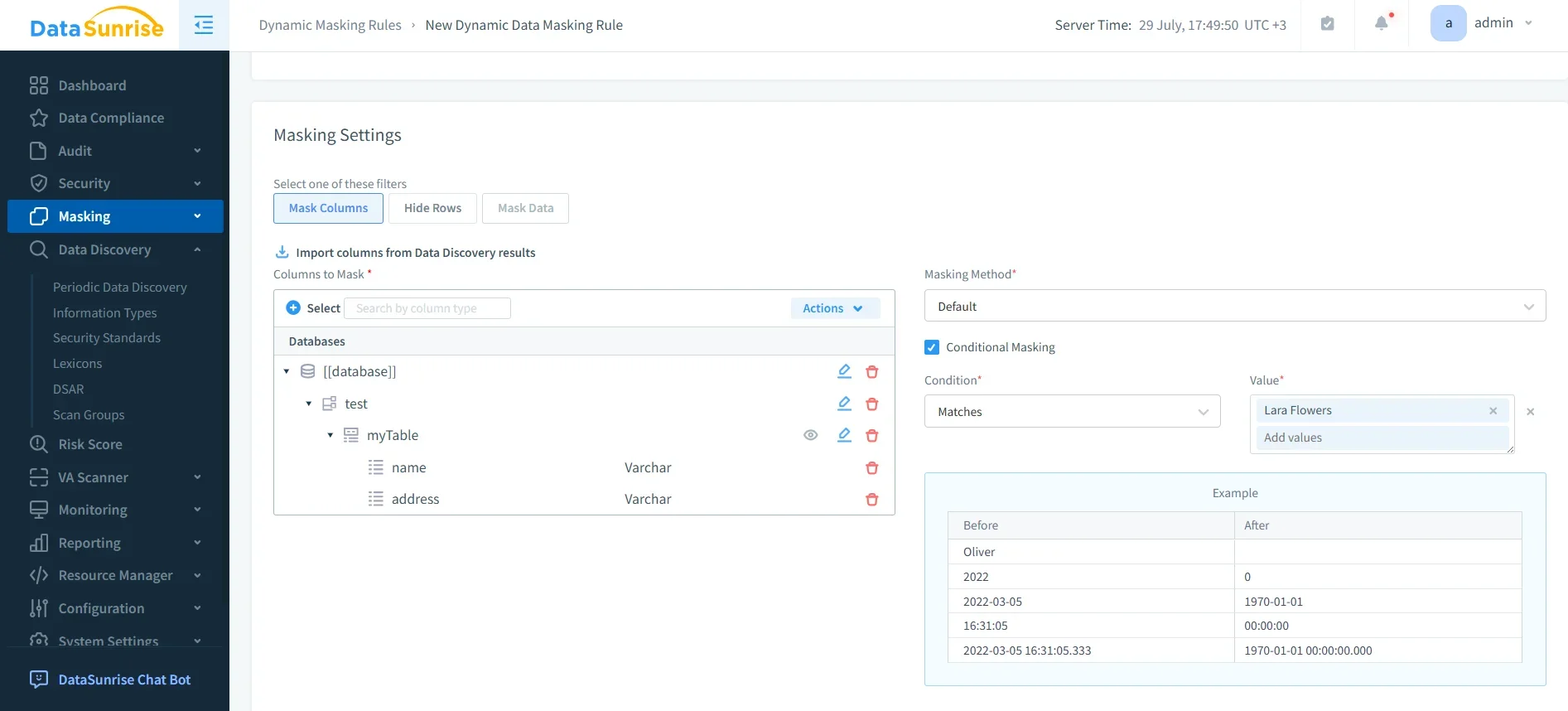
Dynamic Data Masking
Sensitive fields such as credit card numbers or personal identifiers can be protected in real time through dynamic data masking. Unauthorized users see obfuscated values while authorized processes continue to function without disruption. Masking rules can be configured per user role, ensuring fine-grained control and compliance with privacy laws. Unlike static masking, this dynamic approach adapts in real time to requests, supporting continuous application usability.
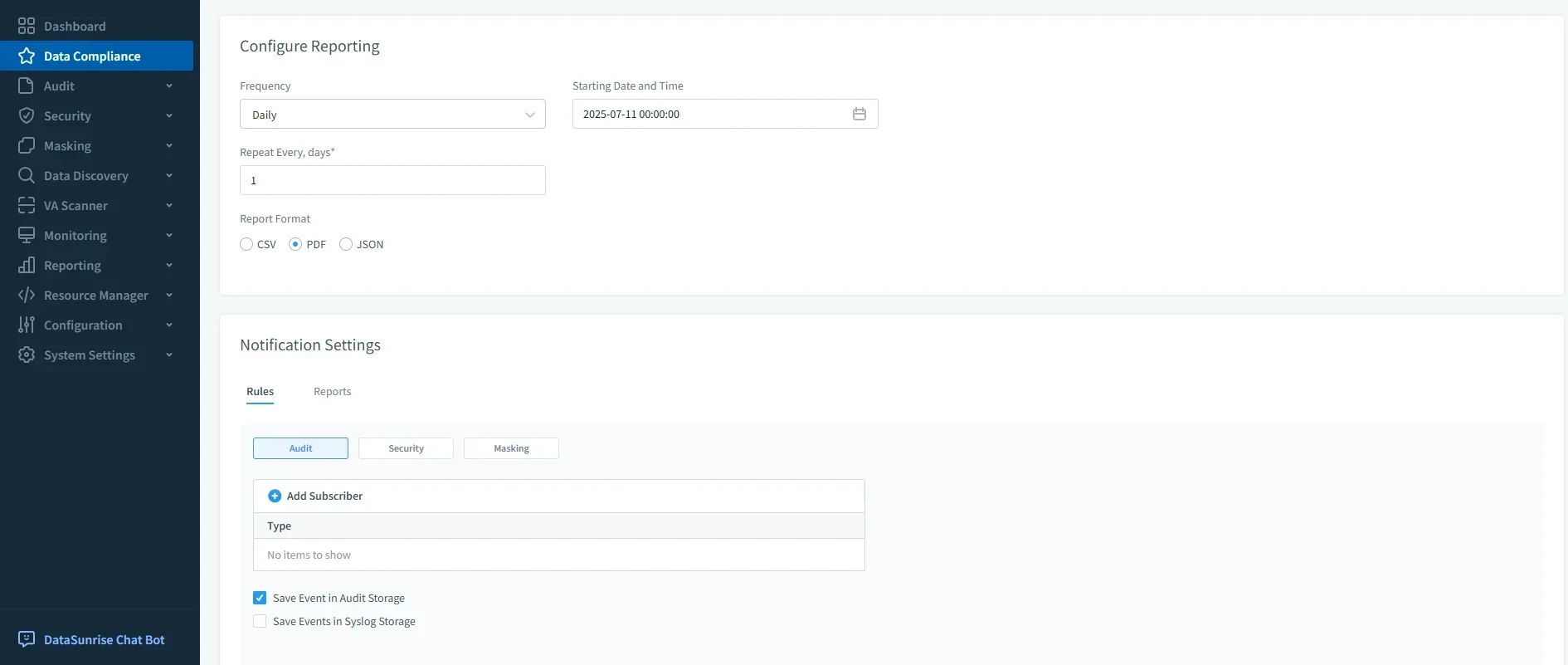
Automated Compliance Reporting
Through Compliance Manager, organizations can generate reports for audits under SOX, HIPAA, PCI DSS, and GDPR. This automation reduces preparation time and helps maintain continuous compliance posture. Reports can be scheduled to run periodically and exported in formats suitable for regulators. By removing manual report generation, DataSunrise lowers audit preparation costs while ensuring consistency across all frameworks.
User Behavior Analytics
By applying user behavior analysis, DataSunrise detects anomalies like unusual query frequency or access attempts outside normal working hours. It applies baselines of normal activity to detect insider threats or compromised accounts earlier than traditional audit logs. Organizations benefit from proactive alerts that reduce incident response times and strengthen governance oversight.
- Detects suspicious login times and unusual query spikes
- Provides contextual insights to distinguish false positives from real threats
- Supports compliance by documenting anomalies for audit reviews
Centralized Policy Management
A single interface for security policies enables administrators to enforce rules consistently across hybrid or multi-cloud environments. This reduces policy drift and ensures alignment with corporate and regulatory requirements. With centralized management, updates apply instantly across databases, lowering administrative overhead and ensuring stronger policy compliance.
- Simplifies multi-database governance from one console
- Ensures uniform enforcement across on-premises and cloud platforms
- Reduces administrative workload by automating policy synchronization
Business Impact
| Aspect | Percona Native Governance | Governance with DataSunrise |
|---|---|---|
| Audit Trails | Basic audit logs captured with plugin; manual export and parsing required | Centralized, tamper-proof audit trails with cross-platform visibility |
| Data Protection | Encryption at rest and SSL/TLS in transit | Dynamic data masking for sensitive fields, role-based access enforcement, and in-depth data security |
| Compliance Reporting | Manual compilation of logs for frameworks such as GDPR, HIPAA, PCI DSS | Automated compliance reporting with templates for SOX, PCI DSS, HIPAA, GDPR |
| User Monitoring | Logs provide access and query details but lack analytics | Behavior analytics with anomaly detection and insider threat monitoring |
| Policy Management | Policies must be enforced per instance | Centralized policy management across hybrid and multi-cloud deployments |
| Cross-Platform | Limited to MySQL ecosystem | Supports over 40 platforms, ensuring consistent governance |
| Operational Efficiency | High manual effort for log handling and reporting | Automated workflows and report generation |
| Risk Mitigation | Baseline protection but limited anomaly detection | Continuous real-time monitoring and proactive alerts |
Conclusion
Percona Server for MySQL offers a strong foundation for data governance with features like RBAC, encryption, and audit logging. Yet, modern compliance challenges demand broader visibility, automation, and advanced protection.
By integrating DataSunrise, organizations can elevate their governance strategy with dynamic masking, intelligent analytics, and centralized compliance reporting. This not only ensures alignment with global regulatory standards but also strengthens resilience against evolving data threats.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now