How to Audit Amazon DynamoDB
Amazon DynamoDB offers high performance, a fully managed serverless architecture, and seamless scalability. However, these operational advantages do not replace the need for reliable and comprehensive auditing. DynamoDB does not include a dedicated audit subsystem, and its visibility is instead distributed across multiple AWS services, each responsible for capturing specific aspects of access or data modification activity.
Regulatory standards such as GDPR, HIPAA, and PCI DSS require organizations to maintain complete, verifiable, and tamper-resistant audit records. Meeting these requirements is challenging when audit information must be assembled from several independent log sources. Many teams address this gap by adopting centralized tools that unify logs and policies, such as DataSunrise’s Data Audit platform, which provides required visibility and control.
This guide outlines how auditing for DynamoDB can be implemented using AWS-native tools and describes how DataSunrise can unify these data sources into a centralized, compliance-ready audit trail with real-time monitoring and granular policy controls.
Importance of Audit
Auditing Amazon DynamoDB is not just a best practice — it is a regulatory, operational, and security requirement. Because DynamoDB lacks a single cohesive audit layer, organizations must assemble visibility across several AWS services. Without proper auditing, accountability breaks down because there is no reliable proof of who accessed or modified sensitive data. Missing before-and-after states eliminates the ability to verify integrity and detect tampering.
Regulatory obligations from GDPR, HIPAA, PCI DSS, and SOX all require traceability of access and modifications, yet DynamoDB alone does not provide a unified audit trail that satisfies these requirements. This makes cloud database environments far more difficult to secure unless they adopt solutions offering consistent monitoring, such as DataSunrise’s Database Activity Monitoring. Security risks also increase when fragmented logs cause insider threats, credential abuse, or anomalous activity to go unnoticed. During a forensic investigation, incomplete or uncorrelated evidence slows response time and undermines incident reconstruction.
A complete audit trail restores transparency by enabling reconstruction of every read, write, update, or delete operation. It strengthens operational confidence by proving that least-privilege policies are enforced consistently, and it hardens security through real-time anomaly detection and unified governance across environments — particularly when paired with automated compliance controls like the Compliance Manager. For these reasons, assembling and unifying DynamoDB audit visibility — and extending it with DataSunrise — becomes mandatory for regulated and mission-critical workloads.
Native DynamoDB Audit Architecture
DynamoDB does not record operations in the way traditional relational databases do. Instead, AWS distributes operational, identity, and configuration telemetry across several services. To build a functional audit trail, organizations must combine the following components.
1. AWS CloudTrail — Identity and API Activity Logging
CloudTrail acts as the primary audit source for identity and API behavior, creating a detailed record of every interaction with DynamoDB. It logs operations such as PutItem, GetItem, UpdateItem, DeleteItem, Query, and Scan, as well as table creation, deletion, scaling changes, and configuration events. Each entry includes the caller identity—whether an IAM user, an assumed role (STS), or a federated identity—along with timestamps, request parameters, source IP address, and region. This is foundational information when building a structured audit trail for compliance and security investigations.
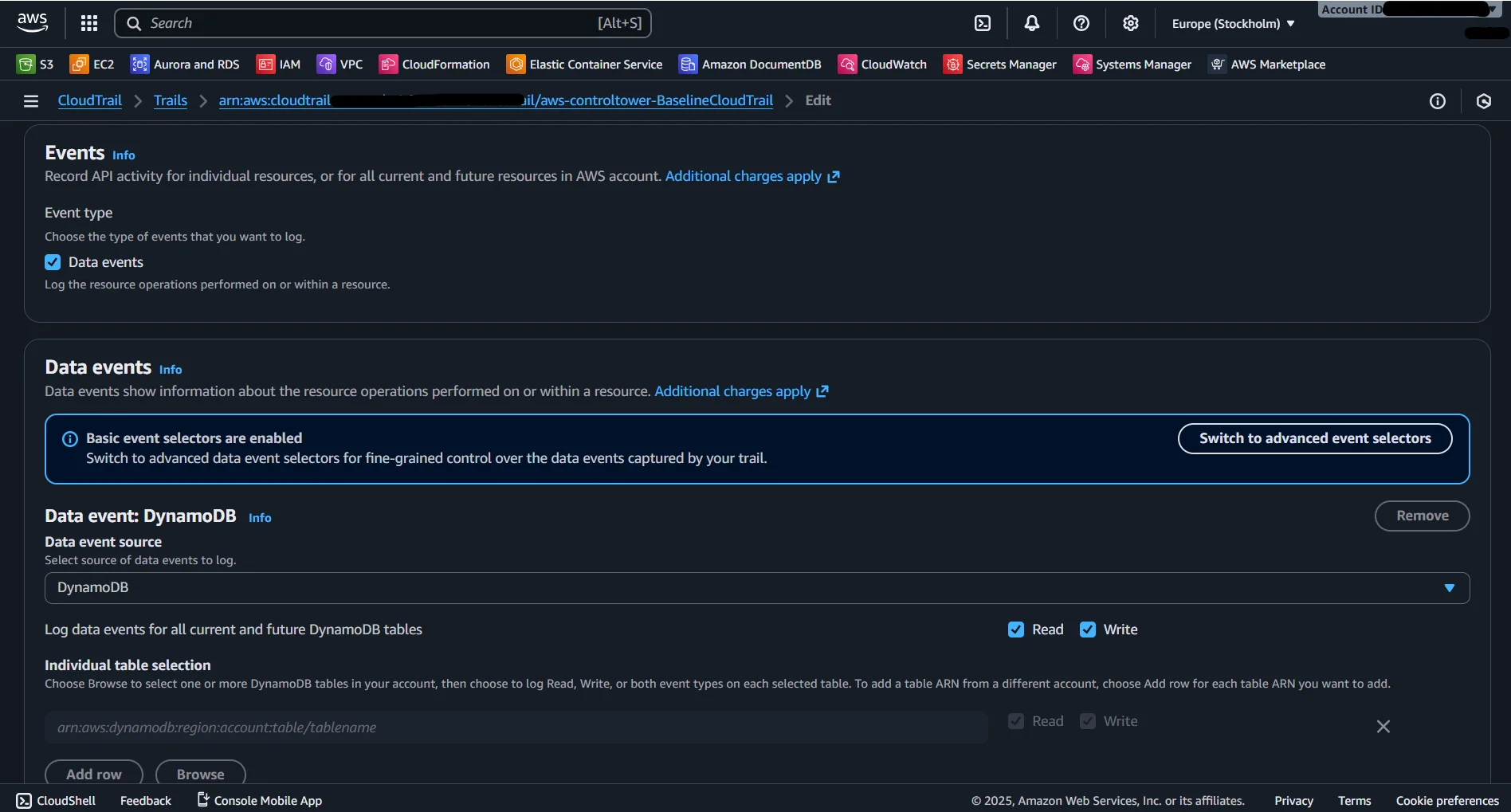
2. AWS DynamoDB Streams — Item-Level Change Tracking
DynamoDB Streams supplies the granular item-level visibility that CloudTrail lacks by providing a chronological sequence of inserts, updates, and deletions. Each stream record contains both old and new item images, allowing organizations to reconstruct exactly what changed during a write operation. This capability supports integrity verification, forensic reconstruction, and compliance requirements around monitoring modifications to regulated or sensitive data. When correlated with CloudTrail, Streams make it possible to connect individual data changes with the identities responsible for them — similar to how DataSunrise reconstructs changes in Data Activity History.
Additional details include:
- Streams integrate with Kinesis and Lambda for automated workflows.
- Retention is limited to 24 hours, requiring timely ingestion.
- Sharding preserves ordered delivery by partition key.
- Events can trigger compliance checks or anomaly detection routines.
3. AWS CloudWatch Logs — Centralization, Analytics, and Alerting
CloudWatch acts as a centralized hub for retention, visualization, and analysis of DynamoDB-related telemetry. It consolidates CloudTrail logs, application logs, and Stream-derived events in one location, making it easier to detect unusual patterns such as spikes in Query or Scan operations, access attempts from unexpected regions, or repeated conditional failures. CloudWatch Insights supports structured querying for investigations, while alarms and dashboards provide real-time monitoring. CloudWatch is also used to forward logs into security ecosystems or integrate with external tools.
Additional insights include:
- Logs can be archived into S3 for long-term retention.
- Metric filters convert log patterns into security metrics.
- Multi-account log aggregation simplifies enterprise auditing.
- Data can be seamlessly exported into SIEM systems for correlation.
4. AWS Config — Configuration and Policy Change Auditing
AWS Config captures the historical evolution of DynamoDB configuration settings. It continuously records changes to encryption configuration, TTL settings, IAM policies, index definitions, and throughput modes. This long-term change history is essential for validating compliance frameworks, ensuring encryption policies remain active, and detecting misconfigurations before they become violations. Config complements CloudTrail by revealing how the environment changed over time.
Additional supporting information:
- Config Rules automatically assess compliance with configuration standards.
- Historical snapshots support long-range forensic analysis.
- Config integrates with AWS Security Hub for unified governance.
- Drift detection ensures long-term adherence to encryption and IAM requirements.
Together, these AWS components form the raw ingredients of a DynamoDB audit trail, but correlating them manually requires substantial effort and tooling.
Unified DynamoDB Audit with DataSunrise
DataSunrise provides what DynamoDB does not: a unified, normalized, end-to-end audit trail across SQL, NoSQL, and cloud platforms, built on principles aligned with the MASS Linguistic Framework.
DataSunrise combines AWS-native telemetry with its own traffic inspection and policy engine, merging all data into one consistent audit narrative. It is commonly deployed via proxy mode, native log trailing, or sniffer mode, depending on environment constraints and integration needs.
1. Real-Time Audit Trails
DataSunrise generates enriched audit records containing the API operation executed, the target table and key, before-and-after images (masked if required), caller identity, timestamps, and detailed execution context. These unified logs provide a depth of visibility not possible when relying solely on distributed AWS-native logs. This capability mirrors the structured, chronological methodology used throughout the Audit Guide.
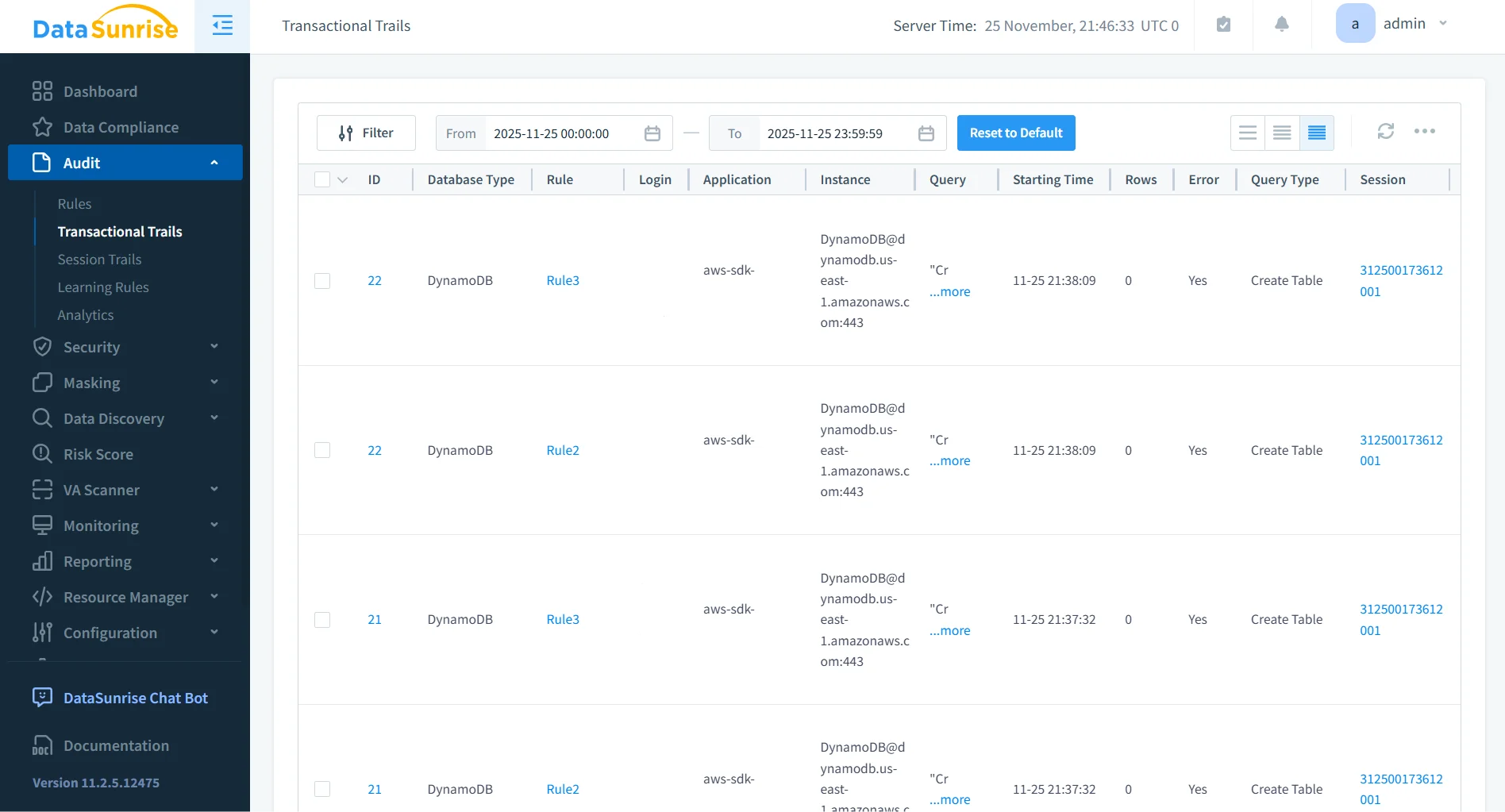
2. Granular Audit Rules
Organizations can define highly precise audit rules targeting specific tables, sensitive attributes, IAM identities, operation types, or behavioral anomalies. This allows teams to focus audits on regulated datasets, detect suspicious access patterns, or trigger alerts when thresholds are exceeded. This level of granularity aligns closely with the rule-based architecture described in DataSunrise’s Rules Priority framework.
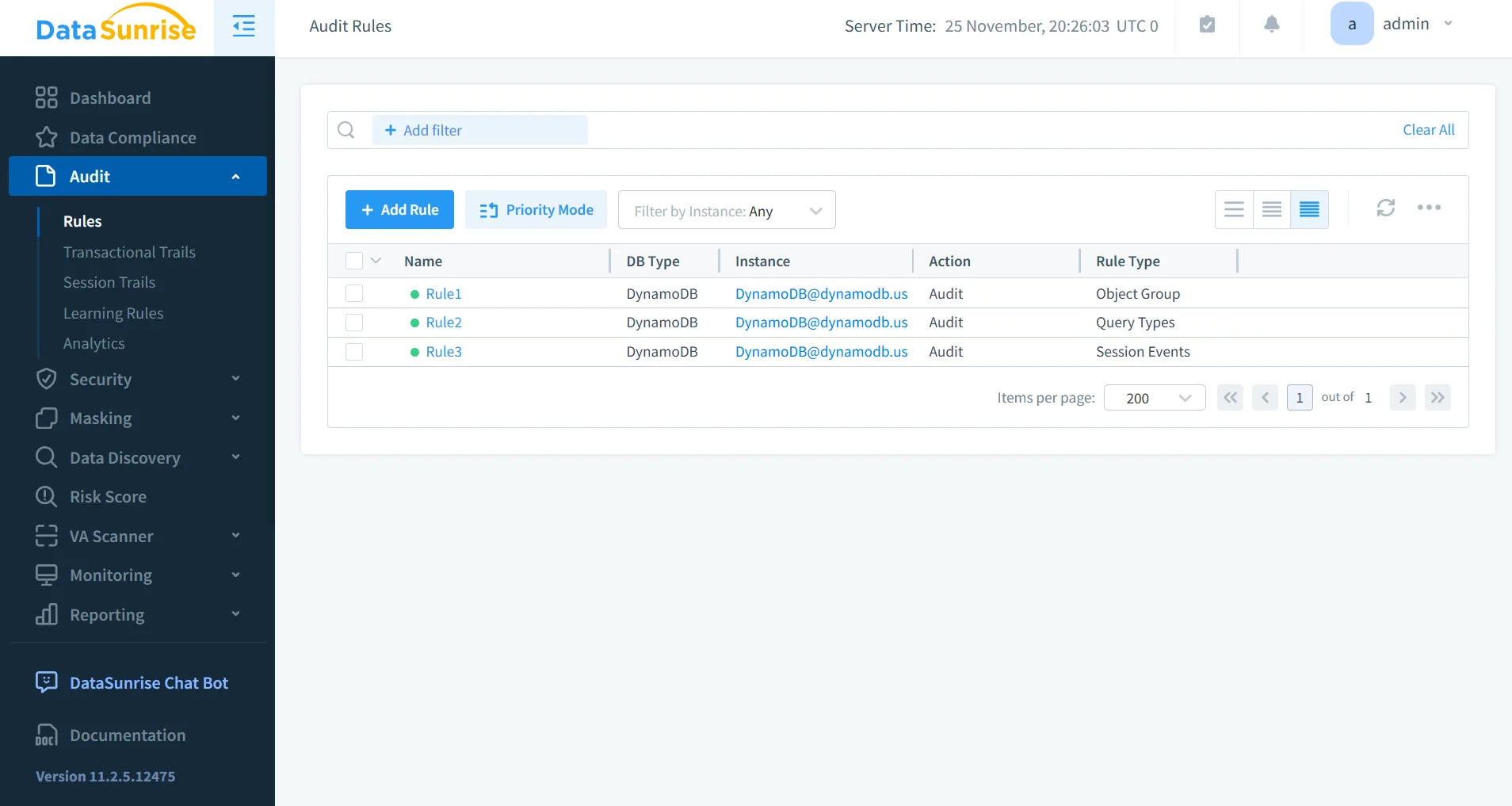
3. Dynamic Data Masking for DynamoDB
DataSunrise applies dynamic masking to ensure sensitive data never appears in clear text within logs, dashboards, reports, or live traffic analysis. Masking rules can be set for PII, PHI, financial attributes, and any custom-defined sensitive values, ensuring full privacy compliance while maintaining analytical visibility.
Additional key points include:
- Masking rules adapt based on user role or request context.
- Templates ensure consistent anonymization across all logs.
- Masking preserves analytical value while hiding real identifiers.
- Rules support compliance requirements related to least-privilege access.
4. Compliance Automation
DataSunrise maps DynamoDB activity to GDPR, HIPAA, PCI DSS, and SOX requirements. It detects configuration drift, generates audit-ready evidence, and conducts scheduled compliance checks. This automation supports enterprise programs and integrates into larger governance processes, including those represented within data compliance regulations.
5. Centralized Cross-Platform Monitoring
DataSunrise aggregates DynamoDB audit data alongside SQL databases, NoSQL platforms, data warehouses, and cloud storage systems. This provides a single governance plane for activity analysis across the entire data infrastructure.
Additional information includes:
- Unified dashboards simplify security investigations.
- Cross-system correlation reveals multi-vector attack chains.
- Enterprise-ready reporting aligns with audit requirements.
- Centralization ensures consistent policy application across environments.
This multi-platform perspective ties directly to DataSunrise’s activity monitoring architecture.
Business Impact
| Business Benefit | Description |
|---|---|
| Regulatory Readiness | Structured, chronological audit evidence helps organizations meet GDPR, HIPAA, PCI DSS, and SOX requirements without manual log reconstruction. |
| Reduced Operational Overhead | Automated log correlation, unified auditing, and compliance workflows eliminate time-consuming manual processes and fragmented AWS log analysis. |
| Enhanced Security Posture | Real-time anomaly detection, behavioral analysis, and unified telemetry significantly reduce the attack surface and improve threat visibility. |
| Consistent Multi-Cloud Governance | Centralized auditing across SQL, NoSQL, and cloud platforms ensures uniform policy enforcement across hybrid and multi-cloud environments. |
| Protected Sensitive Data | Dynamic masking prevents exposure of PII/PHI in audit logs while maintaining operational traceability and compliance fidelity. |
Conclusion
DynamoDB’s audit telemetry is powerful but fragmented. CloudTrail provides identity and API activity, Streams capture item-level changes, CloudWatch offers monitoring and analytics, and Config records configuration drift. Although each service contributes essential visibility, none of them independently provides a unified audit trail.
DataSunrise solves this challenge by merging these distributed data sources into a single, consistent audit narrative. It enriches raw AWS telemetry with contextual detail, applies rule-based analysis to detect deviations, integrates masking to protect sensitive information, and automates compliance reporting. This enables organizations to maintain a verifiable, high-integrity audit posture.
For environments that rely on DynamoDB for regulated or mission-critical workloads, DataSunrise provides the unified visibility necessary to transform AWS’s distributed telemetry into a complete, auditor-ready source of truth.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now