Data Compliance Automation for Amazon DynamoDB
Automating data compliance for Amazon DynamoDB requires a fundamentally different approach than traditional relational databases. DynamoDB is fully managed, schema-flexible, and tightly integrated with AWS infrastructure services. As a result, compliance controls are distributed across identity management, encryption, telemetry, and external monitoring layers, rather than implemented inside the database engine itself. This model aligns DynamoDB compliance with broader data compliance and data management practices rather than database-native mechanisms.
For organizations storing regulated or sensitive data in DynamoDB—such as personal data, financial records, or healthcare information—manual compliance processes quickly become unmanageable. Automation is essential to maintain visibility, enforce consistent controls, and produce audit-ready evidence as environments scale. In practice, this requires continuous database activity monitoring combined with structured data security enforcement outside the database engine.
This article explains how compliance automation works in DynamoDB environments, what native AWS services provide, where their limitations appear, and how centralized automation platforms can close those gaps.
What Data Compliance Means in DynamoDB Environments
In DynamoDB, compliance is not enforced through query-level auditing or database triggers. Instead, it relies on coordinated AWS services that operate before, during, and after data access. This model aligns compliance with centralized access controls and infrastructure-level enforcement rather than database-native mechanisms.
Key compliance objectives typically include:
- Enforcing least-privilege access to tables and indexes
- Protecting sensitive data at rest and in transit
- Capturing verifiable access and change history
- Supporting regulatory audits and internal investigations
- Detecting policy drift as architectures evolve
Because DynamoDB does not expose native SQL logs or internal query histories, compliance automation must be built around identity enforcement, infrastructure logging, and external monitoring. In practice, this requires continuous database activity monitoring combined with structured data security controls outside the database engine.
Native AWS Controls for DynamoDB Compliance
AWS provides several foundational services that contribute to DynamoDB compliance. These services are powerful, but they operate independently and require careful coordination to support automated compliance workflows.
Identity and Access Management (IAM)
AWS Identity and Access Management (IAM) is the primary enforcement layer for DynamoDB access. Every request is evaluated against IAM policies before execution.
IAM policies define:
- Which principals can access DynamoDB
- Which actions are allowed (
GetItem,PutItem,Query,Scan, etc.) - Which tables or indexes can be accessed
- Optional conditions such as source IP or VPC endpoint
Example IAM policy restricting read access to a single table:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"dynamodb:GetItem",
"dynamodb:Query"
],
"Resource": "arn:aws:dynamodb:us-east-1:123456789012:table/Orders"
}
]
}
IAM is highly effective for access control, but it does not provide historical visibility into how data was used—only whether access was allowed.
Encryption and Infrastructure Protection
DynamoDB encrypts all data at rest by default using AWS-managed keys. For regulated environments, organizations typically adopt customer-managed AWS KMS keys to meet compliance requirements for key ownership, rotation, and revocation.
Example DynamoDB table using a customer-managed KMS key:
{
"SSESpecification": {
"Enabled": true,
"SSEType": "KMS",
"KMSMasterKeyId": "arn:aws:kms:us-east-1:123456789012:key/abcd-1234-efgh-5678"
}
}
In addition:
- TLS protects data in transit
- AWS infrastructure controls protect physical storage
- Backup and point-in-time recovery support data integrity requirements
These controls satisfy many baseline security requirements, but they do not provide activity-level compliance evidence.
CloudTrail and Operational Logging
Because DynamoDB does not generate query logs, AWS CloudTrail becomes the primary source of activity records.
CloudTrail captures:
- API calls to DynamoDB
- Identity making the request
- Timestamp and source
- Success or failure status
Example CloudTrail event for a DynamoDB operation:
{
"eventSource": "dynamodb.amazonaws.com",
"eventName": "PutItem",
"awsRegion": "us-east-1",
"userIdentity": {
"type": "IAMUser",
"userName": "app-service-user"
},
"requestParameters": {
"tableName": "Orders"
},
"responseElements": {
"consumedCapacity": null
}
}
This data is critical for accountability, but it has important limitations:
- No visibility into item-level data access
- No understanding of sensitive data context
- No built-in compliance logic
- High log volume requiring post-processing
CloudTrail provides raw telemetry — not compliance automation.
Automating DynamoDB Compliance with Centralized Monitoring
To automate compliance effectively, organizations introduce an external compliance layer that operates around DynamoDB, not inside it. This approach aligns with centralized data compliance architectures rather than database-native controls.
This layer focuses on:
- Centralized policy definition
- Continuous activity monitoring
- Sensitive data awareness
- Automated compliance reporting
- Cross-environment consistency
Unlike native AWS logs, compliance automation platforms apply context-aware logic to activity streams, transforming raw events into structured compliance evidence through advanced database activity monitoring.
Compliance-Aware Activity Monitoring
Automated compliance monitoring evaluates DynamoDB activity based on who accessed what, how, and under which conditions. This model extends traditional logging by incorporating data security and regulatory context.
Instead of storing every event blindly, compliance-aware monitoring:
- Filters events based on regulatory relevance
- Correlates identities, actions, and data sensitivity
- Detects anomalous or risky behavior patterns using user behavior analysis
- Maintains tamper-resistant audit trails
This approach significantly reduces noise while improving audit clarity.
Policy-Driven Compliance Automation
Centralized compliance automation relies on policy-driven enforcement, where rules are defined once and applied consistently. Policies are typically aligned with enterprise access controls and compliance objectives rather than application logic.
Policy logic can include:
- Which DynamoDB tables contain regulated data
- Which identities are allowed access under which conditions
- What activity must be logged for specific regulations
- How violations or anomalies are flagged
Because policies are external to the database, they remain consistent across development, staging, and production environments—even across multiple AWS accounts.
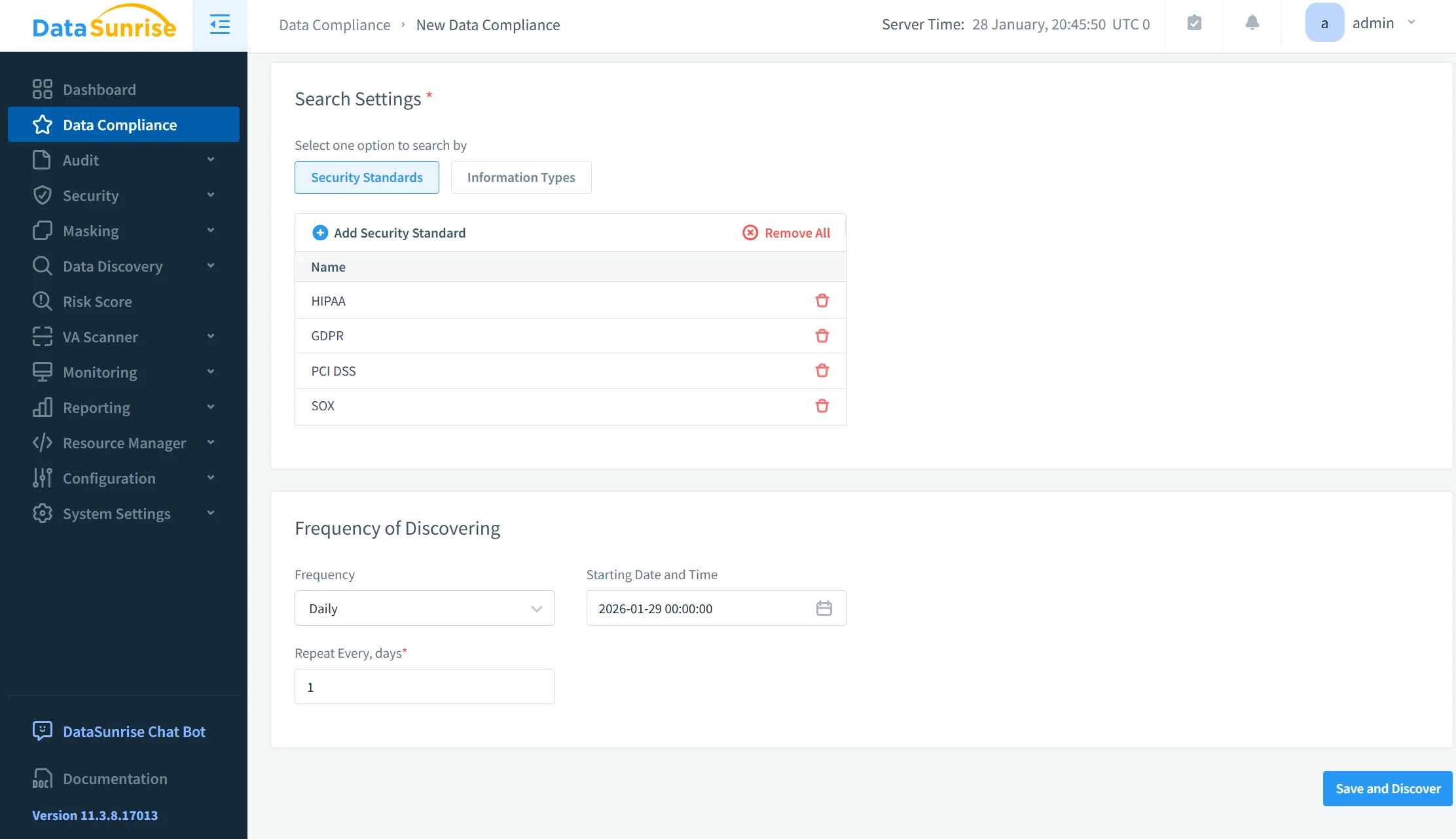
Automated Compliance Reporting
One of the most resource-intensive aspects of compliance is audit preparation. Automation platforms address this by generating audit-ready reports continuously using centralized compliance management workflows.
Automated reports can include:
- Access history by identity or role
- Administrative changes to DynamoDB resources
- Evidence of encryption and access controls
- Timeline views of sensitive data interactions
This eliminates manual log extraction and reduces audit cycles from weeks to hours.
Business Impact of Automated DynamoDB Compliance
| Business Outcome | Operational Impact |
|---|---|
| Reduced audit preparation time | Continuous evidence collection eliminates manual log aggregation and last-minute audit work |
| Lower risk of compliance gaps | Automated, policy-driven controls reduce human error and configuration drift |
| Consistent controls across environments | Identical compliance behavior across development, staging, and production AWS accounts |
| Improved visibility into data usage | Clear insight into who accessed DynamoDB resources, when, and under what conditions |
| Faster incident investigation and response | Centralized activity records accelerate root-cause analysis and containment |
Automation transforms compliance from a reactive obligation into a continuous, measurable operational capability rather than a periodic audit exercise.
Conclusion
Amazon DynamoDB provides secure, scalable infrastructure, but compliance automation does not happen automatically. Native AWS services deliver essential building blocks—identity enforcement, encryption, and telemetry—but they operate independently and lack compliance context. As a result, organizations must treat DynamoDB compliance as part of a broader data security and data compliance strategy rather than a database-level feature.
Automating data compliance for DynamoDB requires a centralized layer that unifies policy enforcement, activity monitoring, and reporting across environments. By externalizing compliance logic and continuously interpreting activity through structured database activity monitoring, organizations gain clarity, consistency, and audit readiness without slowing development or operations.
In DynamoDB environments, compliance is not about adding features to the database. It is about architecting visibility, control, and accountability around it—and automating those controls at scale using centralized compliance management workflows.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now