How to Manage Data Compliance for ScyllaDB
Organizations working with ScyllaDB face the same regulatory obligations as those running traditional relational systems. Compliance with GDPR, HIPAA, and PCI DSS requires strong visibility into data access, proper controls over sensitive information, and consistent reporting.
While ScyllaDB provides operational logging and monitoring, these native tools can be limited when applied to compliance audits. For example, node-local logs make it difficult to reconstruct a full activity history across distributed clusters. To bridge these gaps, organizations adopt platforms like DataSunrise that unify monitoring, automate compliance policies, and simplify reporting.
This article explains ScyllaDB’s baseline compliance features and demonstrates how DataSunrise extends them into a full compliance management solution.
What is Data Compliance?
Data compliance is the practice of ensuring that the way an organization collects, stores, processes, and shares information meets regulatory and internal standards. It involves both technical safeguards and governance processes that align data handling with laws such as GDPR, HIPAA, and SOX.
Key elements of data compliance include:
- Transparency – Users and regulators must know how personal data is collected and used.
- Security – Databases must enforce data security controls, encryption, and access restrictions.
- Auditability – Activities must be logged with reliable audit trails for accountability.
- Policy Enforcement – Organizations must apply rules consistently, such as role-based access control.
Managing data compliance for ScyllaDB therefore means combining its distributed data performance with tools that ensure accountability, visibility, and adherence to regulations.
Native ScyllaDB Compliance Capabilities
ScyllaDB includes several tools that can assist in compliance efforts, though they are primarily designed for operational monitoring rather than regulatory reporting.
Audit Logging
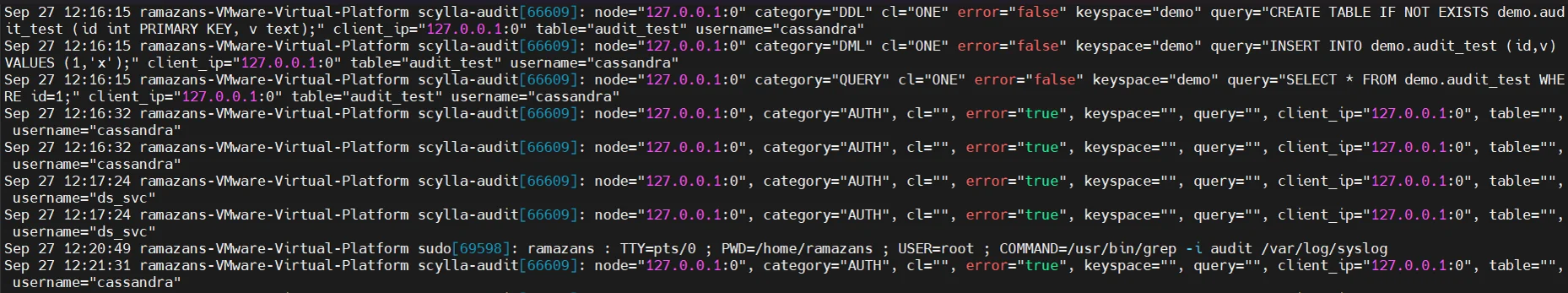
ScyllaDB’s audit logging allows organizations to record database activities such as logins, data changes, and schema modifications. This feature plays a central role in maintaining accountability and visibility for compliance purposes.
Through audit logging, administrators can maintain a historical record of operations that includes who accessed what data, which queries were executed, and when the actions took place. The information can be used to identify unauthorized activities or confirm adherence to internal access policies.
Role-Based Access Control (RBAC)
RBAC is a fundamental control mechanism that helps enforce the principle of least privilege. In ScyllaDB, administrators can create roles with granular permissions to restrict access to sensitive objects.
Example:
-- Create a role for compliance auditors
CREATE ROLE compliance_auditor WITH LOGIN = TRUE AND PASSWORD = 'securePass123';
-- Grant read-only access to a sensitive table
GRANT SELECT ON keyspace1.sensitive_table TO compliance_auditor;
-- Revoke write access if previously granted
REVOKE MODIFY ON keyspace1.sensitive_table FROM compliance_auditor;
This ensures that only authorized users can view compliance-sensitive data, and no one outside their scope can alter critical records.
Encryption Options
To secure data in transit, ScyllaDB supports TLS encryption for both client-to-node and node-to-node communication. Enabling TLS is an important requirement for data protection.
In scylla.yaml, encryption settings are configured as follows:
client_encryption_options:
enabled: true
optional: false
keystore: conf/.keystore
keystore_password: myPassword
server_encryption_options:
internode_encryption: all
keystore: conf/.keystore
keystore_password: myPassword
truststore: conf/.truststore
truststore_password: myPassword
This configuration enforces encrypted connections across all nodes and between clients and the database. Proper certificate management ensures data cannot be intercepted or tampered with during transmission.
Managing ScyllaDB Compliance with DataSunrise
DataSunrise extends ScyllaDB with compliance-first architecture, delivering automated discovery, auditing, masking, and reporting. Unlike native logging, DataSunrise consolidates compliance management across clusters and integrates seamlessly with external SIEM and security platforms.
Sensitive Data Discovery
DataSunrise automatically scans ScyllaDB schemas to identify sensitive fields such as PII, PHI, and PCI data. It uses pattern recognition, NLP, and context-aware detection to locate personal or financial information across structured and semi-structured formats.
- Detects credit cards, medical IDs, and social security numbers.
- Works with JSON and other flexible data types.
- Generates detailed reports for compliance coverage.
Discovery tasks can be scheduled to run automatically, ensuring that new datasets are continuously scanned and categorized. Results are directly integrated into masking and auditing workflows, enabling quick remediation of compliance gaps.
More on this feature: Data Discovery.
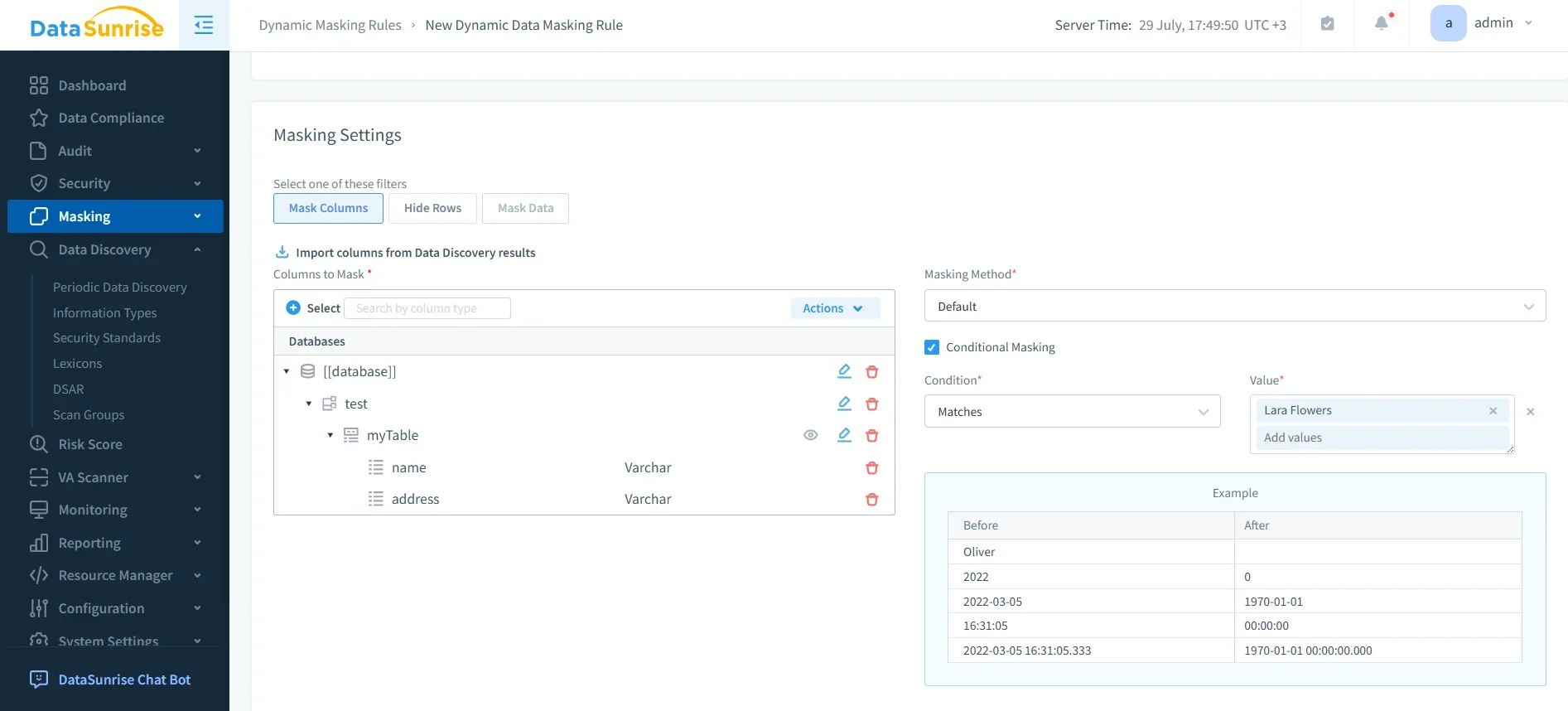
Dynamic Data Masking
To prevent exposure of sensitive fields, DataSunrise enforces dynamic masking policies at query execution.
- Role-based masking ensures analysts only see partial values.
- No schema changes or application rewrites required.
- Protects compliance-sensitive fields in real time.
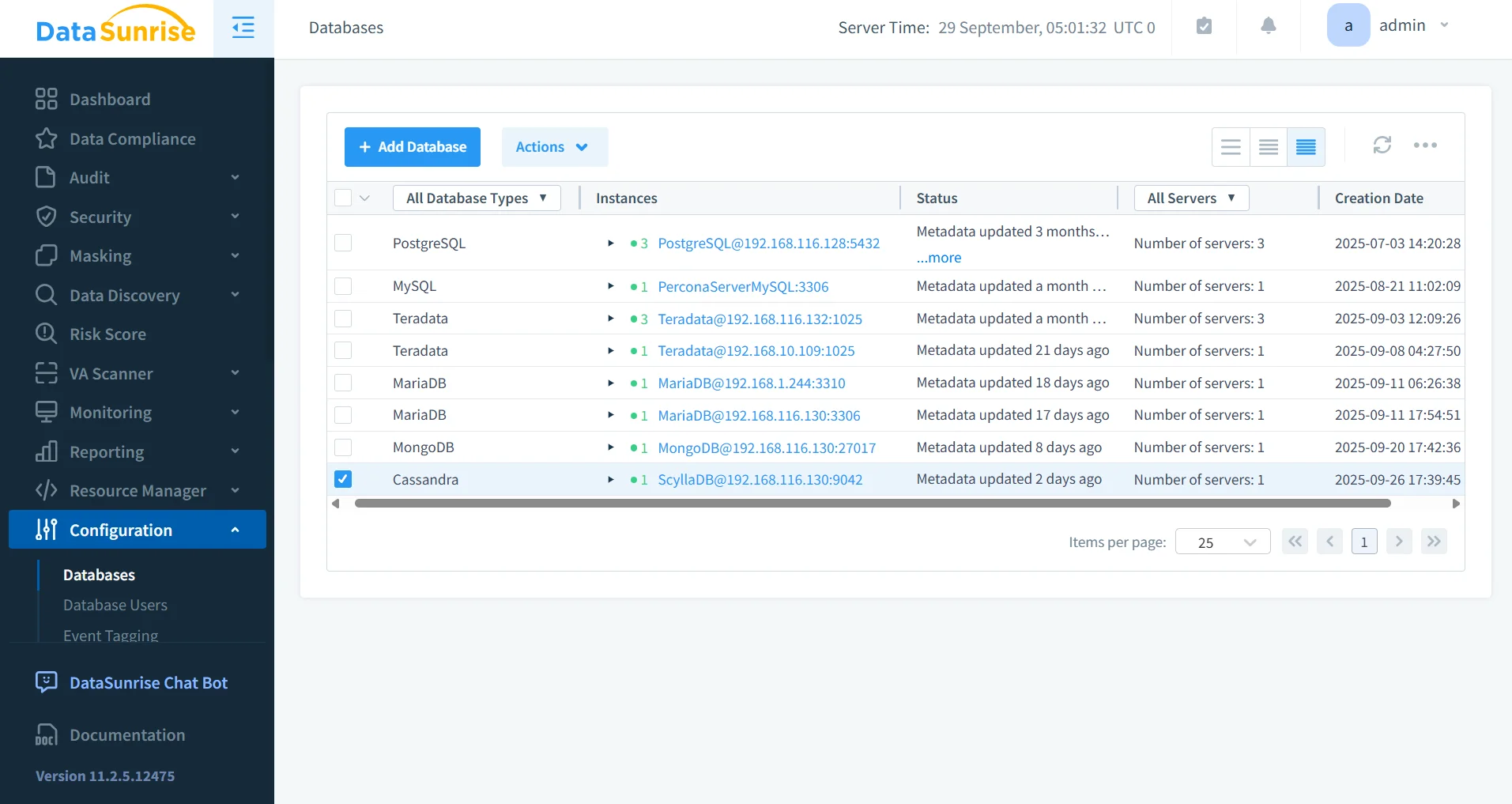
Centralized Activity Monitoring
Unlike node-local logs, DataSunrise provides centralized database activity monitoring.
- Unified dashboard across ScyllaDB clusters.
- Filtering by user, query type, or object.
- Long-term storage of audit trails for investigations.
- Integration with SIEM tools for enterprise oversight.
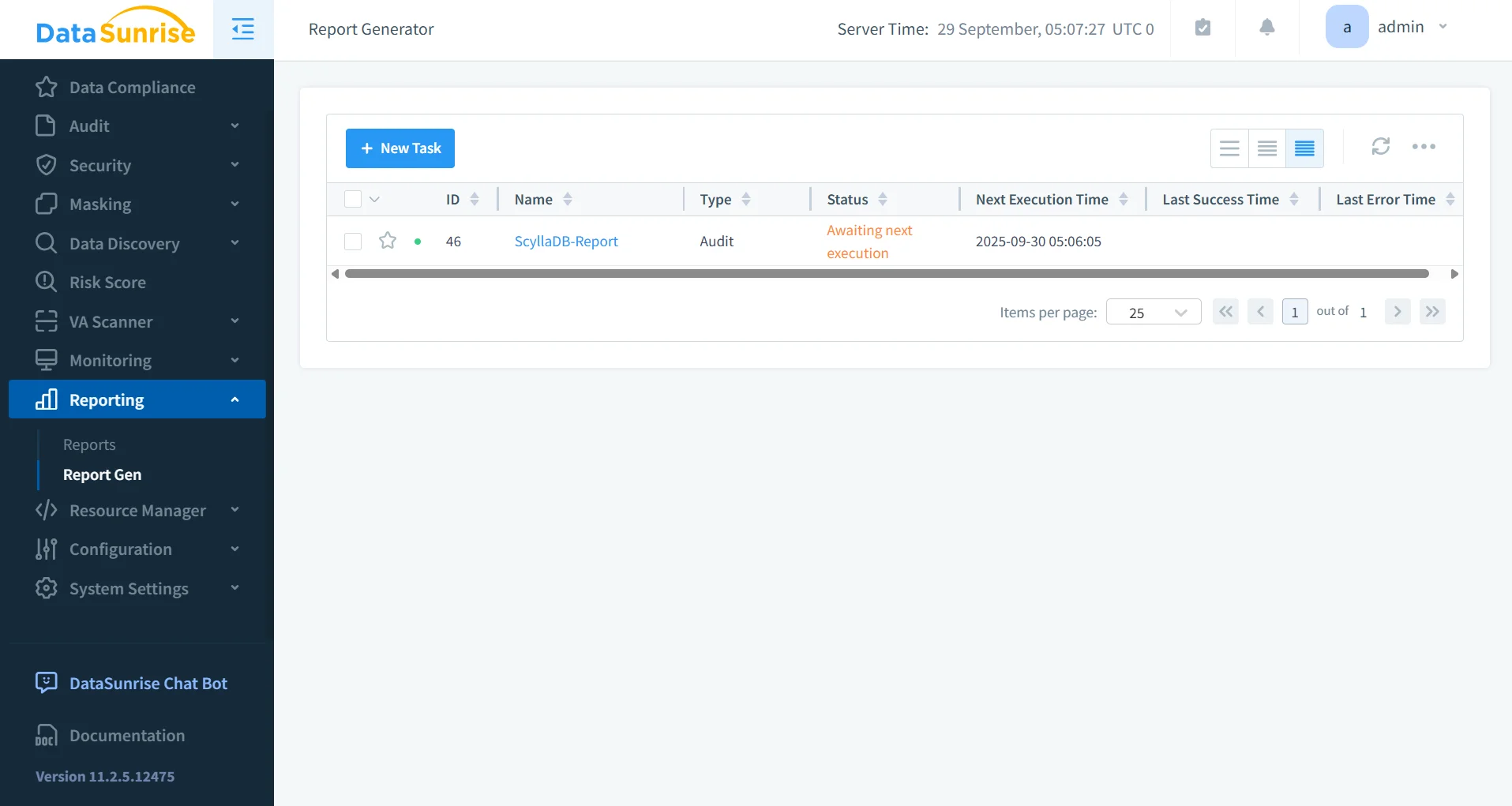
Automated Compliance Reporting
DataSunrise’s Compliance Manager automates reporting for GDPR, HIPAA, PCI DSS, and SOX.
- Pre-built templates for auditor-ready evidence.
- Scheduled or on-demand report generation.
- Reduces manual effort and ensures consistency.
Security Enforcement
Beyond compliance reporting, DataSunrise strengthens ScyllaDB with multiple real-time protection layers that help maintain both security and compliance integrity.
- Database Firewall inspects every query in real time and blocks malicious attempts such as SQL injections, brute-force logins, and unauthorized data extraction.
- User Behavior Analytics applies machine learning algorithms to detect anomalies in query behavior, such as unusual access times or massive data exports.
- Vulnerability Assessment continuously evaluates ScyllaDB configurations, permission structures, and network settings to detect weaknesses such as overly permissive roles or missing encryption.
Together, these tools form a proactive defense system. Administrators can detect, block, and remediate risks before they evolve into compliance incidents.
Business Benefits of Compliance Management for ScyllaDB
| Benefit | Impact |
|---|---|
| Risk Reduction | Proactively detect and mitigate data breaches before they escalate. |
| Audit Efficiency | Generate auditor-ready reports in minutes, not days. |
| Trust & Transparency | Demonstrate strong compliance to customers and regulators. |
| Operational Simplicity | Centralized dashboards reduce administrative complexity. |
| Future-Proofing | Automated policy adaptation keeps pace with evolving regulations. |
Conclusion
Managing compliance for ScyllaDB requires more than basic logs or RBAC. While ScyllaDB provides foundational capabilities, true compliance readiness demands centralized oversight, automated discovery, dynamic masking, and audit-ready reporting.
DataSunrise delivers these features in a unified platform, ensuring that organizations using ScyllaDB can maintain regulatory alignment without overwhelming administrative workloads.
Ready to strengthen your ScyllaDB compliance strategy? Schedule a demo and see how DataSunrise automates compliance across your data infrastructure.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now