How to Mask Sensitive Data in CockroachDB
In today's data-driven landscape, protecting sensitive information within distributed databases has become critical. According to IBM's 2024 Cost of a Data Breach Report, organizations with comprehensive data masking implementations reduce breach-related costs by up to 51%. With breach costs reaching $4.88 million in 2024, implementing robust data masking for distributed SQL databases like CockroachDB is essential for security and compliance.
CockroachDB, a cloud-native distributed SQL database, handles sensitive data across multiple regions. CockroachDB's role-based access control provides foundational security, but organizations often require additional data protection capabilities. This guide explores CockroachDB's native masking capabilities and demonstrates how DataSunrise's Zero-Touch Data Masking enhances distributed database security with Intelligent Policy Orchestration.
Understanding Data Masking in CockroachDB
Data masking obscures personally identifiable information by replacing original values with realistic alternatives. In CockroachDB's distributed architecture, effective masking must address multi-region deployment, maintain high availability, preserve referential integrity, support role-based access controls, and ensure application compatibility without breaking functionality.
Native CockroachDB Data Masking Approaches
While CockroachDB doesn't include built-in data masking functionality, administrators can implement basic masking using SQL functions and views. For more details on CockroachDB's security features, refer to the CockroachDB security documentation.
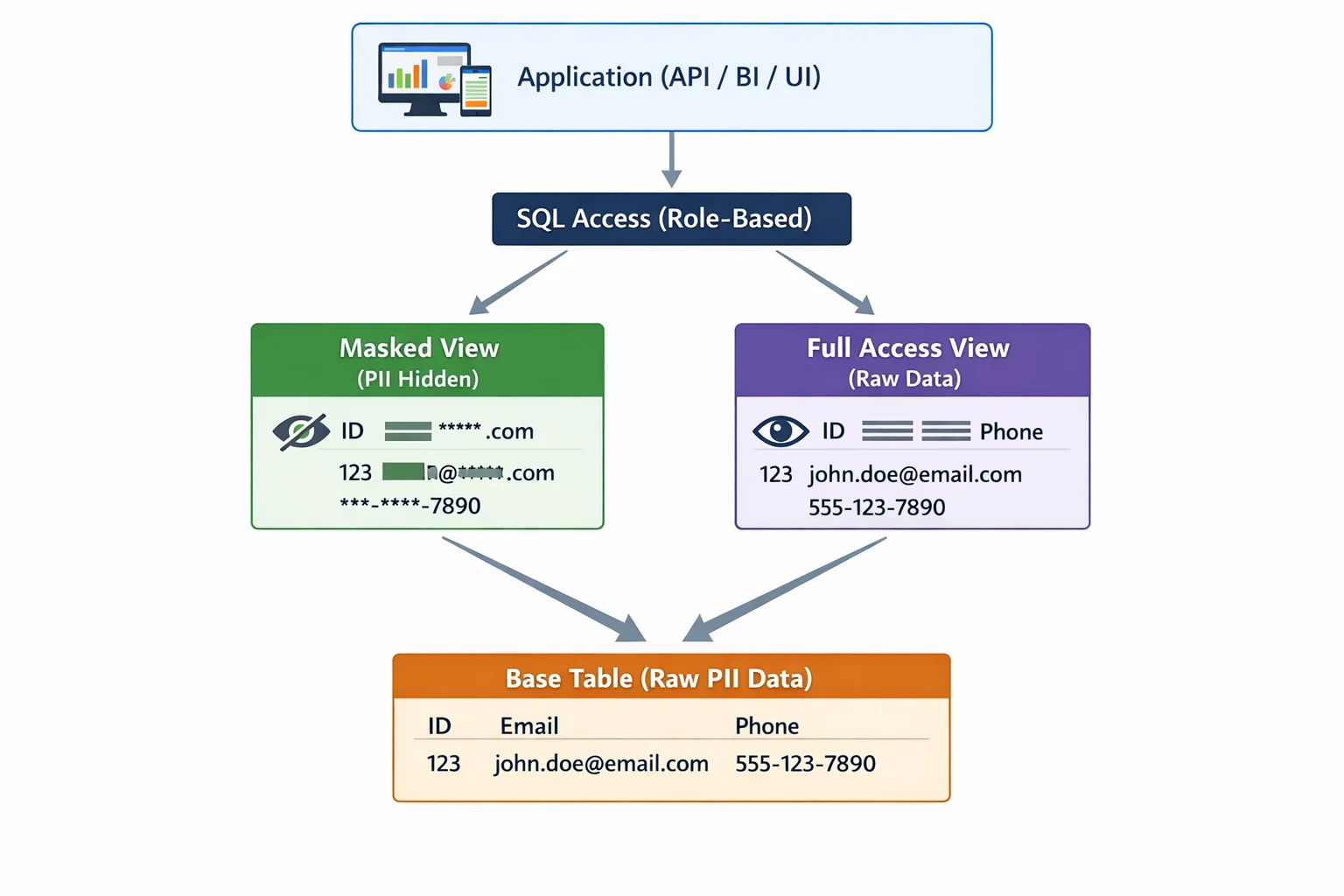
1. View-Based Masking with SQL Functions
Create database views that apply masking functions to sensitive columns:
-- Create table with sensitive data
CREATE TABLE customers (
customer_id UUID PRIMARY KEY DEFAULT gen_random_uuid(),
full_name STRING NOT NULL,
email STRING NOT NULL,
ssn STRING,
credit_card STRING
);
-- Insert sample data
INSERT INTO customers (full_name, email, ssn, credit_card)
VALUES ('Alice Johnson', '[email protected]', '123-45-6789', '4532-1234-5678-9012');
-- Create masked view
CREATE VIEW customers_masked AS
SELECT
customer_id,
regexp_replace(full_name, '.', '*') AS full_name,
regexp_replace(email, '(.{3}).*(@.*)', '\1***\2') AS email,
'***-**-****' AS ssn,
regexp_replace(credit_card, '(\d{4}).*(\d{4})', '\1-****-****-\2') AS credit_card
FROM customers;
-- Grant permissions
CREATE ROLE external_user;
GRANT SELECT ON customers_masked TO external_user;
2. Testing Native Masking Implementation
-- Query as external user
SET ROLE external_user;
SELECT * FROM customers_masked LIMIT 2;
Limitations of Native CockroachDB Masking Approaches
| Native Feature | Key Limitation | Business Impact |
|---|---|---|
| View-Based Masking | Manual creation for each table | High administrative overhead |
| SQL Functions | Limited algorithms | Insufficient protection for complex data |
| Role Management | Complex permission matrices | Difficult to maintain at scale |
| Sensitive Data Discovery | No automated classification | Critical data may remain unmasked |
| Performance Impact | View queries affect optimization | Potential degradation |
Enhanced Data Masking with DataSunrise
DataSunrise significantly enhances distributed database security through Comprehensive Data Discovery and intelligent masking designed for cloud-native SQL environments, delivering enterprise-grade Dynamic Data Masking with sophisticated policy automation.
Setting Up DataSunrise for CockroachDB Data Masking
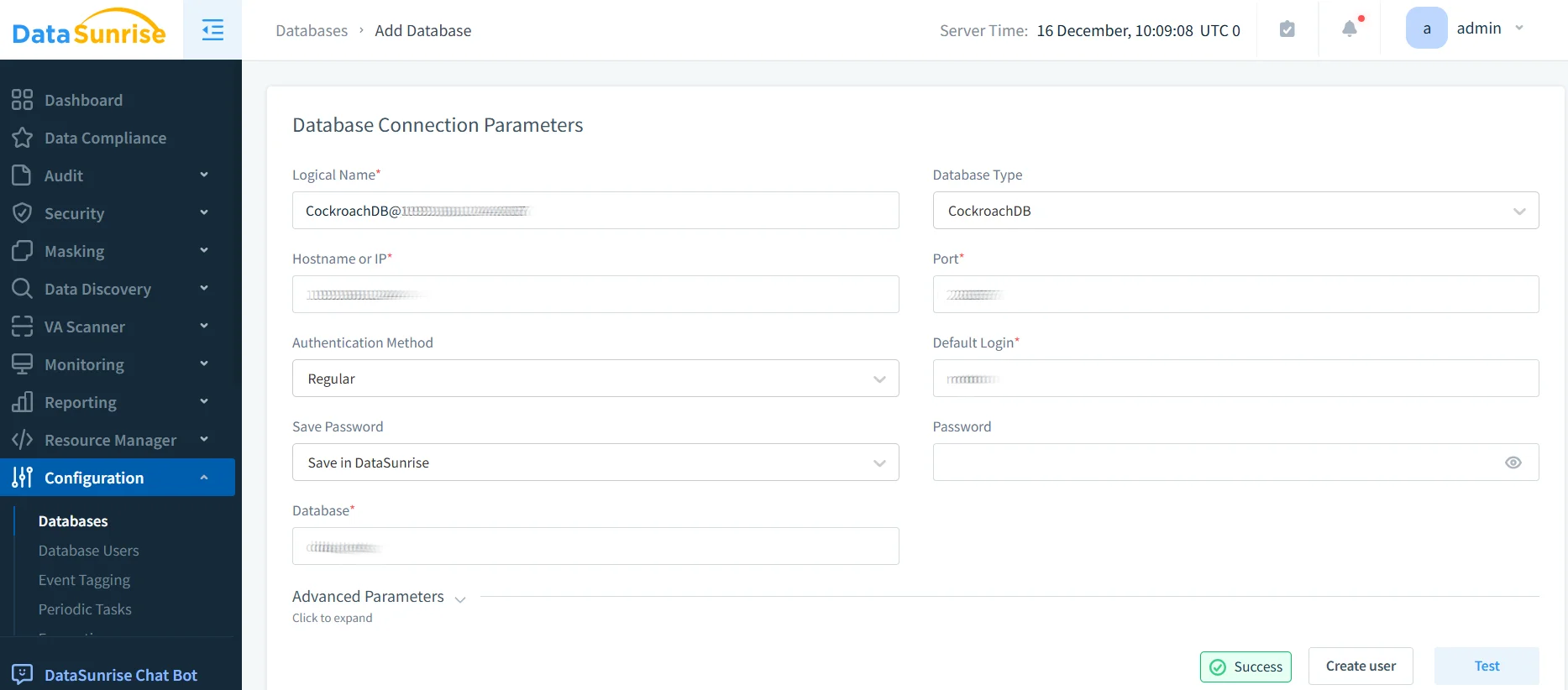
1. Connect to CockroachDB Cluster
Establish a secure connection between DataSunrise and your CockroachDB cluster through the administrative interface, providing consistent masking policies across all nodes.
2. Auto-Discover Sensitive Data
DataSunrise's Auto-Discover & Classify engine automatically scans your environment using NLP algorithms to identify PII, PHI, and financial data with regulatory mapping for GDPR, HIPAA, PCI DSS, and SOX requirements.
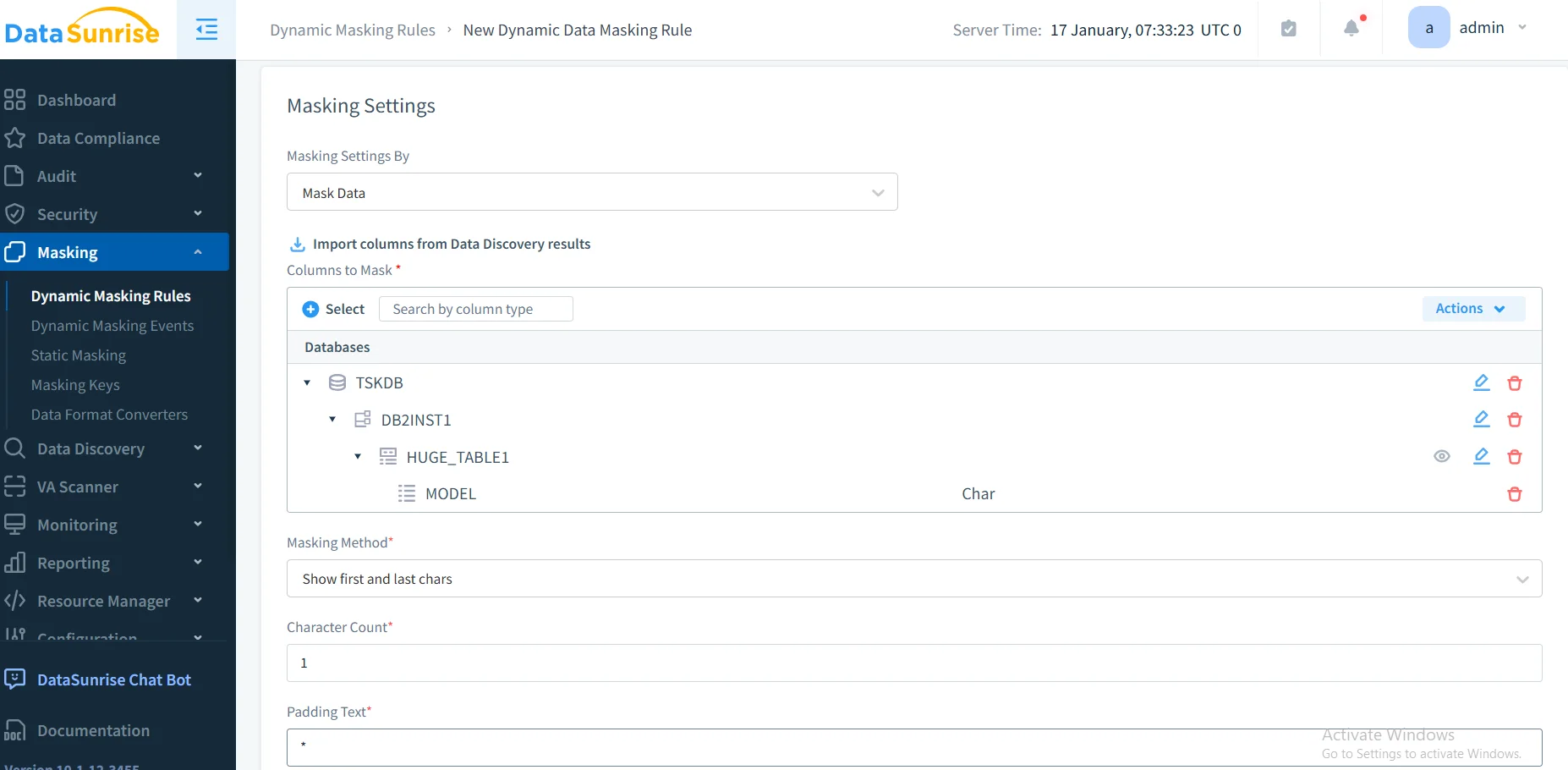
3. Create Dynamic Masking Rules
Configure granular policies using No-Code Policy Automation with role-based masking, context-aware protection, format-preserving masking, and conditional rules.
4. Monitor Masked Data Access
Access comprehensive visibility into all masked data access through DataSunrise's unified database activity monitoring dashboard.
Key Advantages of DataSunrise for CockroachDB
Auto-Discover & Mask: Automatically identify and protect sensitive data using NLP and machine learning with up to 95% greater coverage than manual approaches.
No-Code Policy Automation: Create sophisticated masking policies without complex SQL, reducing implementation time from weeks to hours.
Surgical Precision Masking: Implement context-aware protection with multiple masking algorithms including substitution, shuffling, nulling, hashing, and format-preserving encryption.
Real-Time Protection: Apply dynamic masking without modifying database structures or application code, maintaining seamless data accessibility.
User Behavior Analytics: Detect anomalies that might indicate data breaches or unauthorized access through advanced threat detection.
Comprehensive Audit Trails: Maintain detailed audit logs with automated compliance reporting for GDPR, HIPAA, PCI DSS, and SOX.
Cross-Platform Integration: Manage policies across heterogeneous environments with support for over 40 data storage platforms.
Conclusion
As organizations increasingly rely on CockroachDB for distributed operations, implementing robust data masking has become essential. While SQL-based approaches provide foundational capabilities, organizations with complex security requirements benefit from enhanced solutions like DataSunrise.
DataSunrise provides comprehensive data security for distributed SQL environments, offering Zero-Touch Data Masking with Intelligent Policy Orchestration and automated compliance reporting. With flexible deployment modes, DataSunrise transforms CockroachDB data masking into strategic security assets.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now