MongoDB Data Governance
Organizations increasingly rely on MongoDB to store, query, and analyze large volumes of structured and semi-structured data. As adoption grows across industries, so do compliance and security demands. Data governance ensures sensitive information is consistently protected, properly classified, and accessed only by authorized users.
Native MongoDB tools provide baseline governance features, but production environments with stringent compliance regulations often require advanced controls. According to MongoDB’s official documentation, the platform supports authentication, role-based access, and auditing, yet lacks centralized cross-environment oversight. To bridge these gaps, organizations turn to solutions like DataSunrise to implement enterprise-ready governance frameworks.
This article explores MongoDB’s built-in governance features, then demonstrates how DataSunrise enhances them with automation, dynamic controls, and audit-ready reporting.
Importance of Data Governance
Effective data governance goes beyond access control—it provides a structured framework for how information is managed, protected, and used. For MongoDB, this is especially important given its role in storing high-volume, schema-flexible data across distributed environments.
Key reasons why data governance is essential include:
- Regulatory compliance: Frameworks such as GDPR, HIPAA, and PCI DSS require strict controls over sensitive information. Governance ensures MongoDB deployments meet these mandates.
- Data quality and consistency: Governance policies define ownership, classification, and lifecycle management, helping maintain accurate and reliable datasets. See DAMA International’s principles of data governance for industry-recognized best practices.
- Security and risk management: Structured governance reduces the likelihood of breaches, insider threats, and unauthorized data sharing. NIST’s Data Governance guidance also underscores the role of governance in protecting critical systems.
- Operational efficiency: Standardized policies make audits simpler and monitoring more effective, reducing time spent on manual reviews.
- Trust and transparency: Strong governance builds confidence among customers, partners, and regulators by showing that data handling practices are accountable.
By implementing clear governance policies, organizations can transform MongoDB into a compliant, resilient, and business-aligned data platform.
Native MongoDB Data Governance Capabilities
MongoDB offers several native features that support governance and compliance. Administrators can configure access controls, enable auditing, and enforce encryption at rest and in transit.
1. Authentication and Access Control
Authentication is the first step in protecting a MongoDB deployment. MongoDB supports:
- SCRAM (Salted Challenge Response Authentication Mechanism): The default mechanism that secures credentials through hashing and salting.
- LDAP Integration: Allows centralized authentication, ensuring consistency with enterprise identity management systems.
- x.509 Certificates: Provides certificate-based authentication, commonly used in environments with strict PKI policies.
In addition, MongoDB implements role-based access control (RBAC), which grants permissions at granular levels—such as database, collection, or cluster operations.
Example of creating a compliance-focused administrative user:
use admin
db.createUser({
user: "complianceAdmin",
pwd: "StrongPassword123",
roles: [ { role: "userAdminAnyDatabase", db: "admin" } ]
})
This ensures that only authorized administrators can manage accounts, roles, and permissions. For governance, RBAC is critical, as it enforces the principle of least privilege and prevents privilege creep over time.
2. Native Auditing
MongoDB Enterprise edition includes a built-in auditing system that captures detailed logs of database events. This feature is especially relevant for organizations that must provide evidence during compliance inspections.
Auditing can record:
- User logins and authentication attempts
- Role and privilege changes
- Database operations, such as inserts, updates, and deletions
- Administrative actions, including schema changes and replication events
Audit logs are typically written in JSON format, which makes them compatible with SIEM platforms such as Splunk or Elastic Stack.
Sample configuration in mongod.conf:
auditLog:
destination: file
format: JSON
path: /var/log/mongodb/audit.json
With this setup, administrators can filter events by operation type, user, or database. While the system provides transparency, scaling log management across sharded or replicated clusters introduces complexity. Organizations often need third-party tools to centralize and correlate events effectively.
3. Encryption
Encryption is another cornerstone of MongoDB governance. The platform provides two major layers of protection:
- Encryption in Transit: By enabling TLS/SSL, MongoDB ensures that data exchanged between clients and servers cannot be intercepted or tampered with. Certificates can be signed by internal or public Certificate Authorities, depending on compliance needs.
- Encryption at Rest: MongoDB’s WiredTiger storage engine supports native encryption of database files. With Key Management Interoperability Protocol (KMIP) support, MongoDB can integrate with external key management systems (KMS).
These encryption features are crucial for meeting requirements under GDPR (data privacy), HIPAA (protection of PHI), and PCI DSS (cardholder data protection).
However, encryption management requires continuous oversight. Keys must be rotated, policies maintained, and storage monitored. Without centralized governance, administrators risk gaps in compliance or potential misconfigurations.
Enhanced MongoDB Data Governance with DataSunrise
DataSunrise extends MongoDB governance beyond what native tools provide, offering centralized policy management, automation, and advanced compliance features.
Comprehensive Audit Trails
Comprehensive audit trails in DataSunrise maintain detailed audit logs of all MongoDB activity. Unlike MongoDB’s local auditing, DataSunrise consolidates records across clusters, replicas, and even hybrid environments. This ensures a complete accountability chain that captures who accessed data, what actions were taken, and when events occurred. Administrators can filter results by user, role, or data object, making forensic analysis and compliance reporting far more efficient.
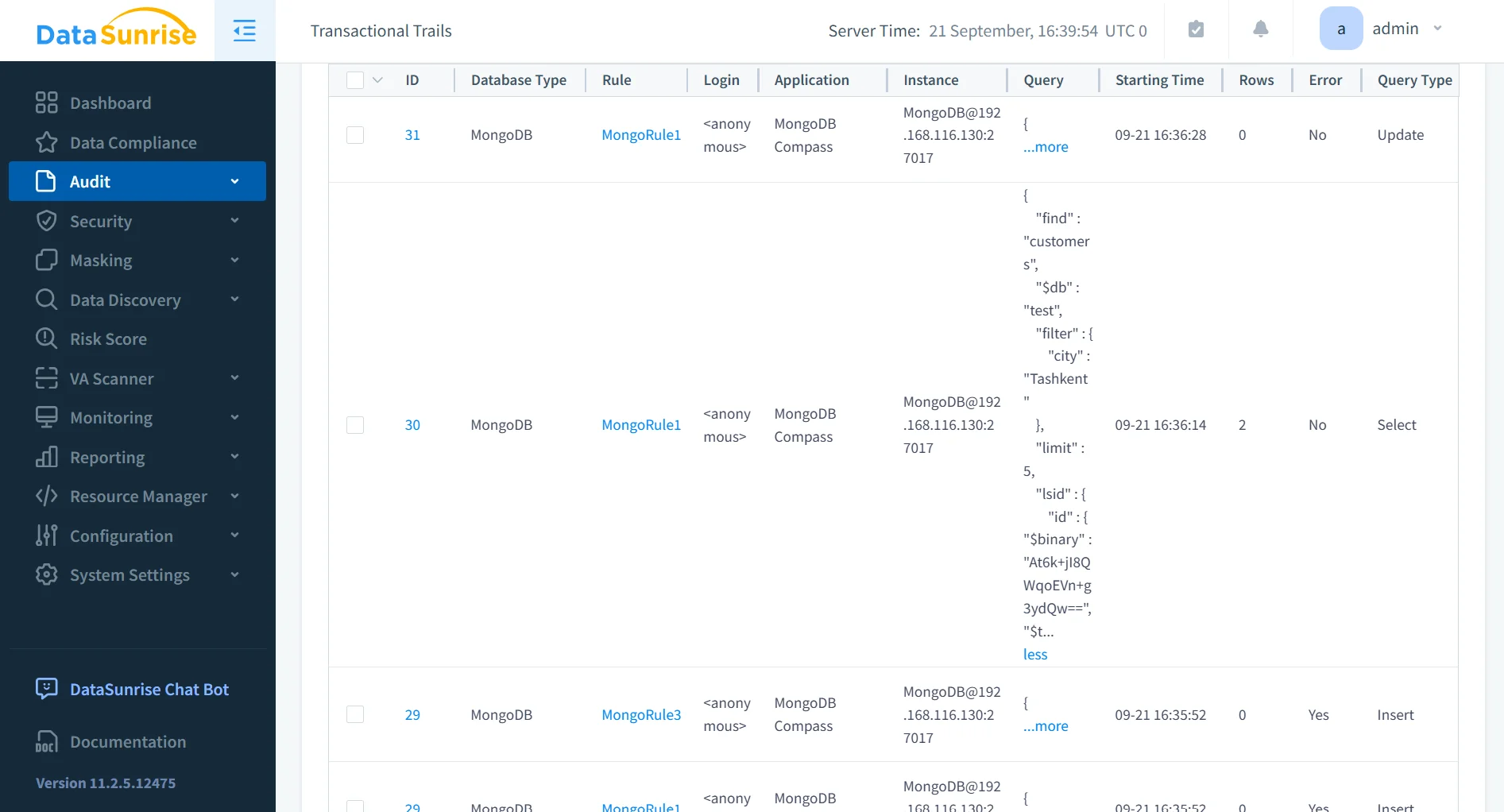
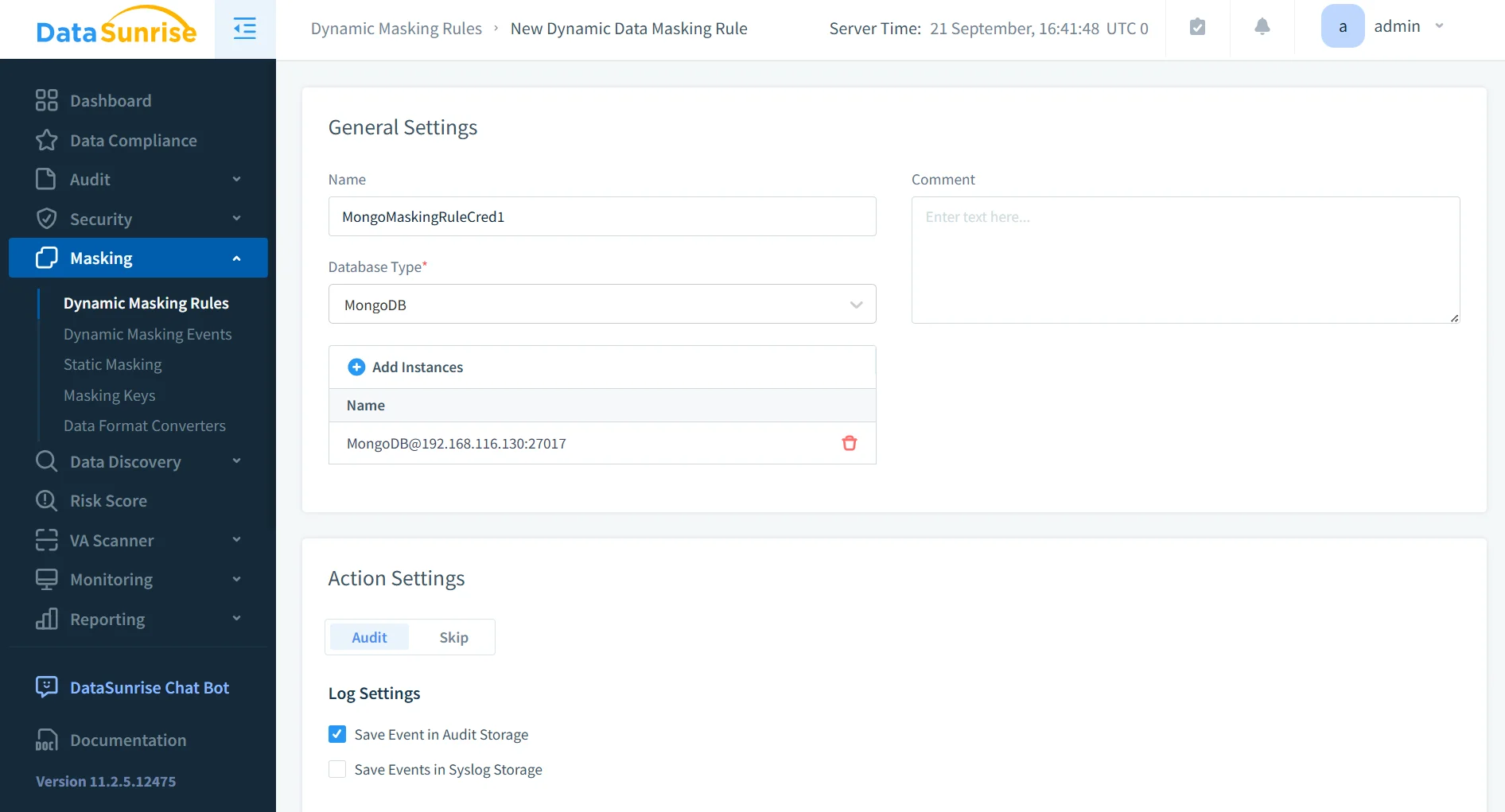
Dynamic Data Masking
With dynamic data masking, sensitive MongoDB fields such as PII or financial records can be hidden in real time from unauthorized users. For example, a support engineer may only see partial credit card digits, while compliance officers can access full records. This prevents accidental data exposure, helps organizations comply with privacy regulations, and reduces insider threat risks without modifying the underlying database.
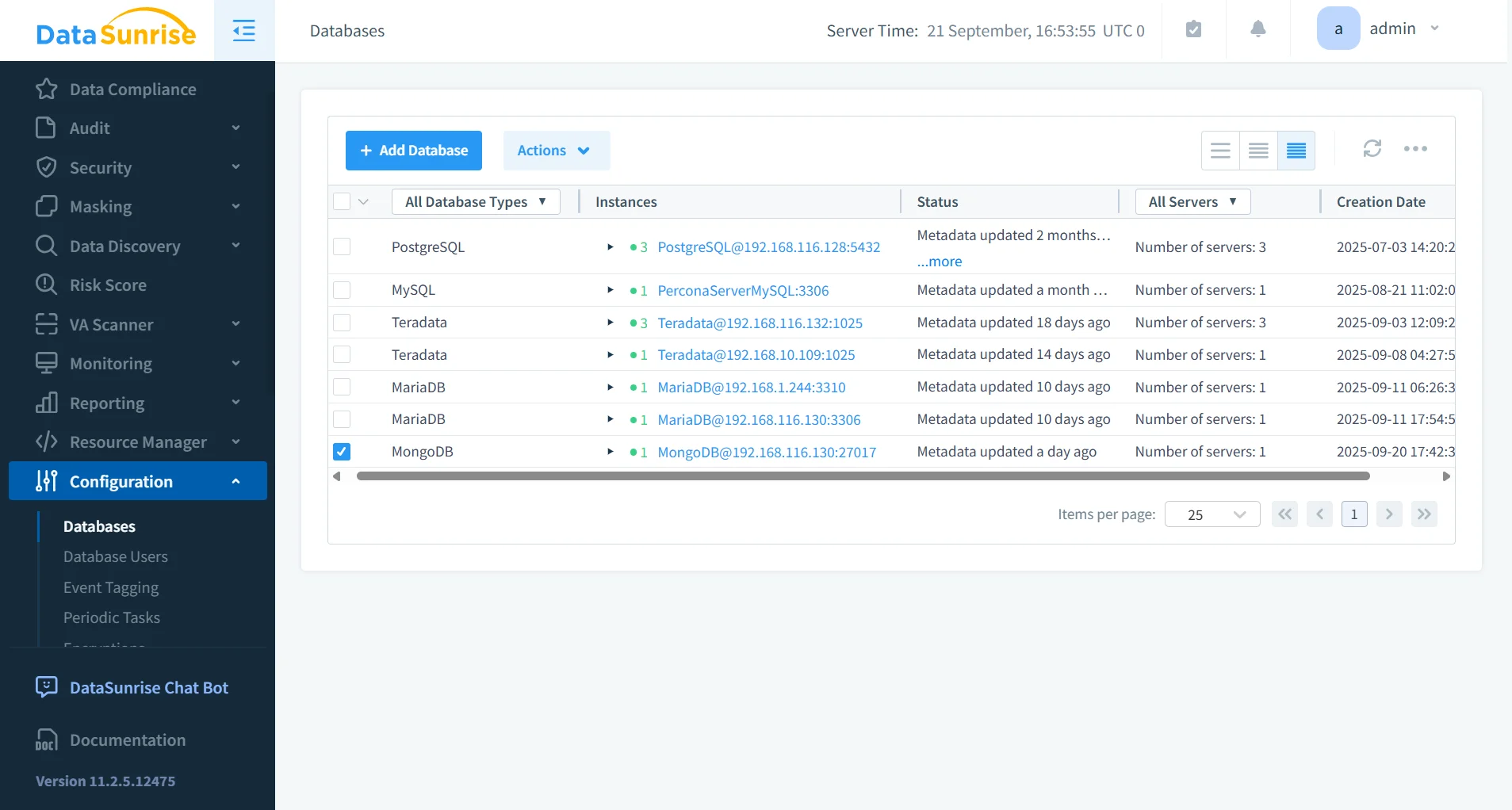
Centralized Monitoring
DataSunrise offers centralized monitoring that consolidates governance across MongoDB and 40+ supported platforms. Instead of managing logs and rules separately for each instance, administrators gain a unified dashboard for enforcing policies, generating alerts, and reviewing activity. This drastically reduces administrative overhead and ensures uniform governance across heterogeneous infrastructures.
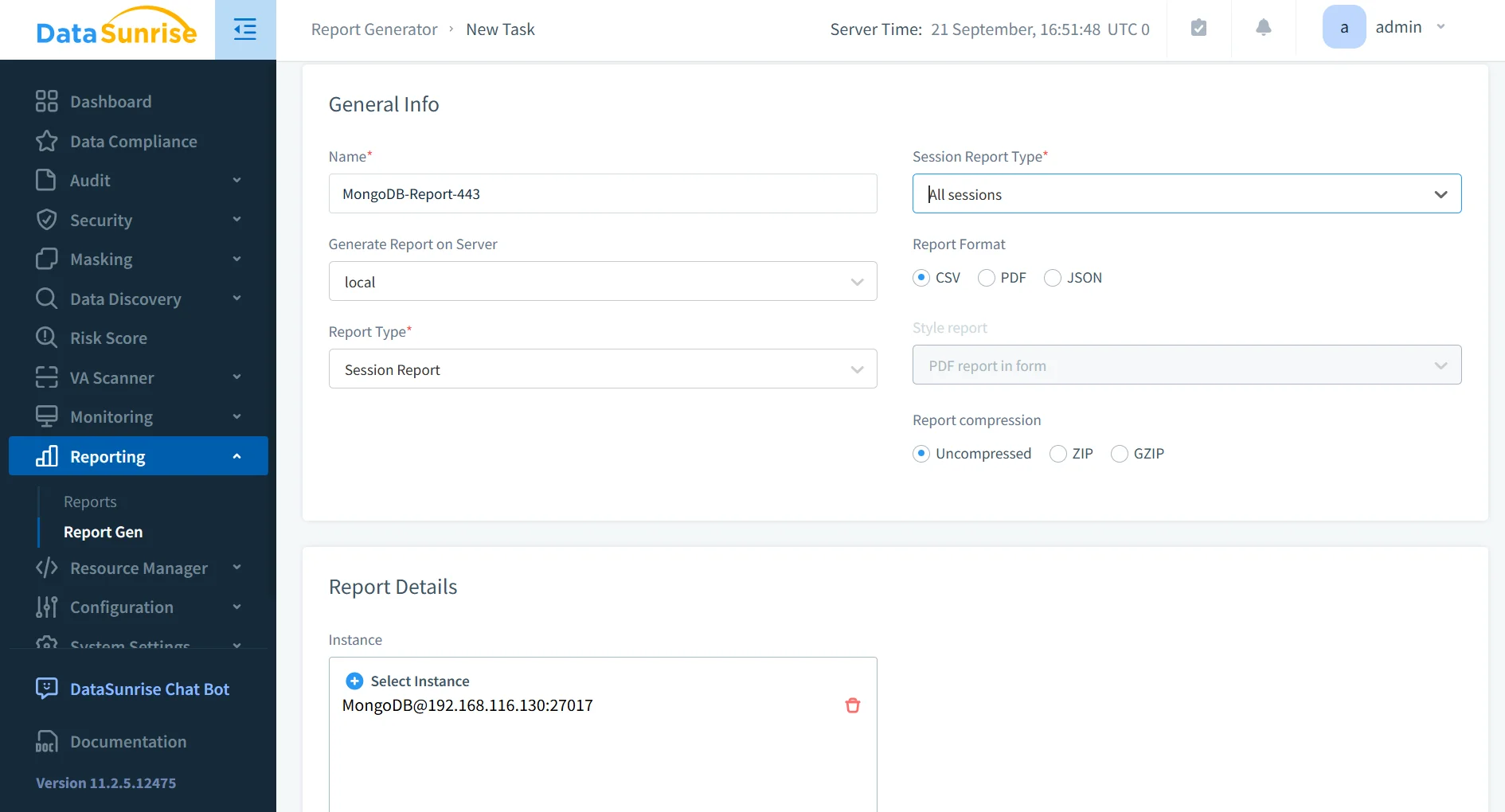
Automated Compliance Reporting
Through automated compliance reporting, DataSunrise streamlines audit preparation. Predefined templates generate one-click reports aligned with GDPR, HIPAA, SOX, and PCI DSS. Reports can be scheduled to run automatically, guaranteeing that compliance evidence is always available when regulators or auditors request it. This not only reduces manual documentation efforts but also ensures continuous readiness for inspections.
Behavior Analytics
Behavior analytics powered by machine learning helps detect abnormal activity within MongoDB environments. By analyzing query patterns, access frequency, and user actions, DataSunrise can identify insider threats, compromised accounts, or suspicious data exports in real time. Administrators can then act immediately, mitigating risks before they escalate into breaches or compliance violations.
- User Behavior Profiling: Tracks normal query and access patterns for each user, creating baselines for comparison.
- Anomaly Detection: Identifies deviations such as mass exports, repeated failed logins, or privilege misuse.
- Insider Threat Identification: Flags unusual internal activity that may indicate malicious intent from employees or contractors.
- Real-Time Alerts: Notifies administrators instantly via email, Slack, or Teams when high-risk behavior is detected.
- Compliance Support: Generates detailed reports of abnormal activity, supporting forensic investigations and regulatory audits.
Business Benefits of MongoDB Data Governance with DataSunrise
| Benefit Area | Business Impact |
|---|---|
| Risk Reduction | Prevents unauthorized access, SQL injections, and insider threats with fine-grained access control and masking. |
| Regulatory Alignment | Simplifies adherence to global frameworks like GDPR, HIPAA, and PCI DSS with automated compliance reporting. |
| Operational Efficiency | Centralizes monitoring across hybrid MongoDB deployments, reducing manual oversight and accelerating audits. |
| Scalability | Supports governance across multi-cluster, multi-cloud MongoDB environments without added complexity. |
| Trust and Transparency | Provides verifiable audit evidence, building confidence among customers, partners, and regulators. |
Conclusion
While MongoDB’s native security and auditing features lay the foundation for governance, they fall short in large-scale or multi-cloud deployments. DataSunrise addresses these gaps with centralized monitoring, compliance automation, and real-time protection.
By combining MongoDB’s native strengths with DataSunrise’s advanced governance framework, organizations can ensure comprehensive oversight, minimize risks, and maintain continuous compliance in evolving regulatory landscapes.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now