ScyllaDB Compliance Management
ScyllaDB is a high-performance NoSQL database designed for scale and availability. It powers applications requiring low latency and massive throughput, making it a popular choice in finance, e-commerce, and cloud-native environments. However, as organizations adopt ScyllaDB for mission-critical workloads, compliance becomes a challenge.
Regulations such as GDPR, HIPAA, PCI DSS, and SOX demand visibility, auditing, masking, and consistent policy enforcement across distributed data systems. While ScyllaDB offers basic logging, meeting compliance requirements often requires additional layers of monitoring and automation.
This article reviews ScyllaDB’s native compliance-related features and explains how DataSunrise enhances compliance management with centralized monitoring, automated controls, and real-time protection.
Importance of Compliance Management
Compliance management is more than just a regulatory obligation—it is a foundation of trust, security, and operational efficiency. For organizations running on ScyllaDB, the stakes are even higher because of the scale and sensitivity of data it often stores.
- Regulatory Pressure: Industries such as healthcare, finance, and e-commerce must align with strict requirements like GDPR, HIPAA, and PCI DSS. Non-compliance can lead to fines, reputational damage, and legal consequences.
- Data Protection: Compliance frameworks enforce best practices in data security, including role-based access controls, encryption, and activity monitoring, helping prevent breaches and insider threats.
- Audit Readiness: Regulations demand evidence of data handling processes. Without centralized audit trails, organizations face lengthy, error-prone reviews.
- Business Trust: Demonstrating compliance builds confidence among customers, partners, and regulators, strengthening long-term relationships.
- Operational Efficiency: Automating compliance tasks reduces manual workload, lowers operational costs, and accelerates time-to-market for new applications.
In short, effective compliance management for ScyllaDB ensures security, reduces risks, and supports sustainable business growth.
Native ScyllaDB Compliance Capabilities
ScyllaDB provides some baseline features that help with compliance management. While useful, these features often require manual effort to align with regulatory expectations.
Authentication & Authorization
ScyllaDB supports role-based access control (RBAC), allowing administrators to define roles and assign specific privileges. This helps ensure that only authorized users can view or modify sensitive datasets. See also access controls for more context.
Example: Creating a role and granting it restricted access to a keyspace.
-- Create a role for compliance auditors
CREATE ROLE compliance_auditor WITH LOGIN = true;
-- Grant read-only access to sensitive keyspace
GRANT SELECT ON KEYSPACE sensitive_data TO compliance_auditor;
-- Assign role to a specific user
GRANT compliance_auditor TO user_jane;
This setup ensures auditors can review data without altering it, meeting compliance requirements for least-privilege access.
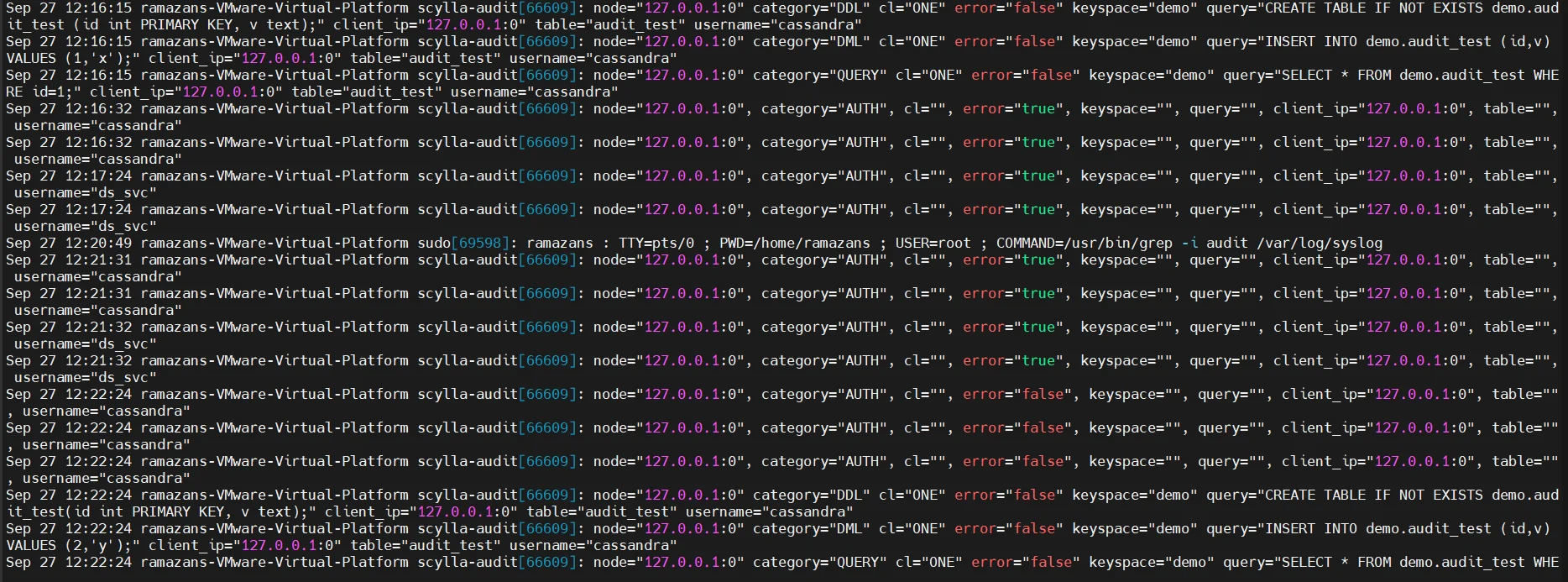
Audit Logging
ScyllaDB can log authentication attempts, queries, and schema modifications. These logs provide a foundation for data activity history and forensic analysis.
Audit logs help administrators reconstruct events during security reviews and supply evidence for compliance audits. However, since logs are stored locally on each node, aggregating them across large clusters can become complex. A more advanced approach is described in audit logs and audit rules.
Encryption
ScyllaDB supports TLS encryption in transit and encryption at rest, protecting sensitive information against interception or theft. Encryption practices are further covered in database encryption.
Enable TLS in scylla.yaml:
client_encryption_options:
enabled: true
certificate: /etc/scylla/ssl/cert.pem
keyfile: /etc/scylla/ssl/key.pem
require_client_auth: true
Enable encryption at rest (using scylla.yaml):
transparent_data_encryption:
enabled: true
keystore: /etc/scylla/keystore.jks
keystore_password: mySecretPassword
This ensures all communications and stored records comply with encryption requirements mandated by regulations like HIPAA and PCI DSS.
Access Control Policies
ScyllaDB implements Cassandra-compatible GRANT/REVOKE mechanisms for fine-grained access control. This helps enforce policies such as the principle of least privilege.
Example: Limiting access to a table containing payment information.
-- Revoke all privileges for safety
REVOKE ALL ON KEYSPACE sensitive_data FROM PUBLIC;
-- Grant only SELECT permissions on the "transactions" table
GRANT SELECT ON TABLE sensitive_data.transactions TO compliance_auditor;
By narrowing privileges, organizations can reduce the risk of data misuse while meeting compliance demands.
These features are valuable but fragmented. Logs are stored locally per node, compliance reporting is manual, and sensitive data often appears unmasked in audit records. For organizations facing audits, this creates significant overhead.
ScyllaDB Compliance with DataSunrise
DataSunrise Compliance Manager extends ScyllaDB with enterprise-grade automation and control. Instead of relying on node-local logs, DataSunrise delivers centralized, auditor-ready compliance infrastructure.
Centralized Activity Monitoring
DataSunrise unifies database activity monitoring across ScyllaDB clusters. Administrators gain a single point of visibility into distributed workloads, which reduces complexity and response time during audits or investigations.
- Single dashboard for all nodes and clusters.
- Advanced filtering by user, query type, or object.
- Long-term storage of audit trails for forensic analysis.
- Integration with SIEM and security platforms.
Unlike native logging, this approach allows cross-cluster correlation of events, providing a complete view of user behavior across the entire deployment. This is critical for organizations with geographically distributed environments, where compliance teams must quickly identify anomalies across thousands of nodes. It also improves incident response by enabling correlation between suspicious activity and user behavior patterns in real time.
For more details, see database activity history.
Sensitive Data Discovery
Data discovery is automated with DataSunrise, removing the need for error-prone manual schema reviews. Discovery can run continuously or on-demand, ensuring new datasets are quickly brought under compliance coverage.
- Scans ScyllaDB schemas for PII, PHI, and PCI data.
- Uses pattern recognition, NLP, and even OCR for semi-structured or unstructured fields.
- Generates reports on where sensitive data resides.
- Enables instant configuration of masking, auditing, or firewall rules.
Beyond identification, discovery results integrate directly into policy enforcement. For example, once credit card fields are detected, administrators can immediately assign dynamic masking policies. This tight linkage between discovery and enforcement reduces compliance blind spots and ensures sensitive fields never remain unprotected. Continuous scanning also supports evolving environments, where new tables or columns are frequently introduced without explicit compliance oversight.
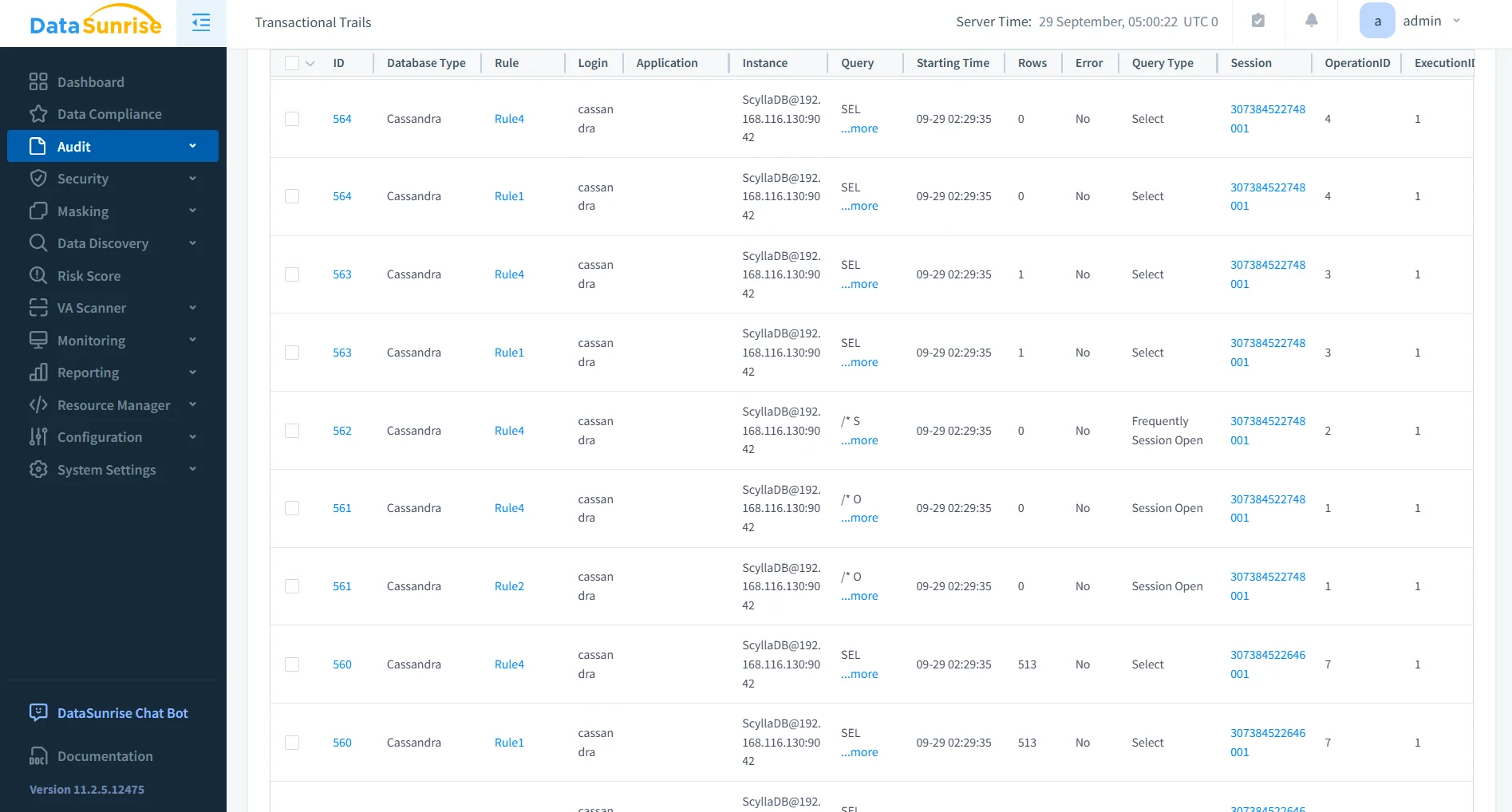
Granular Audit Rules
With flexible audit rules, administrators can define compliance controls with precision. Rules can be adapted to different regulations or internal security requirements, enabling targeted monitoring without unnecessary overhead.
- Track access to sensitive columns (e.g., customer identifiers, payment data).
- Focus on DDL/DML operations that affect regulated datasets.
- Schedule audits for specific time frames, reducing performance impact.
- Export logs in standardized formats for reporting.
This ensures compliance teams capture only what is needed, minimizing log noise while preserving visibility where it matters most. You can also review audit goals for strategic application.
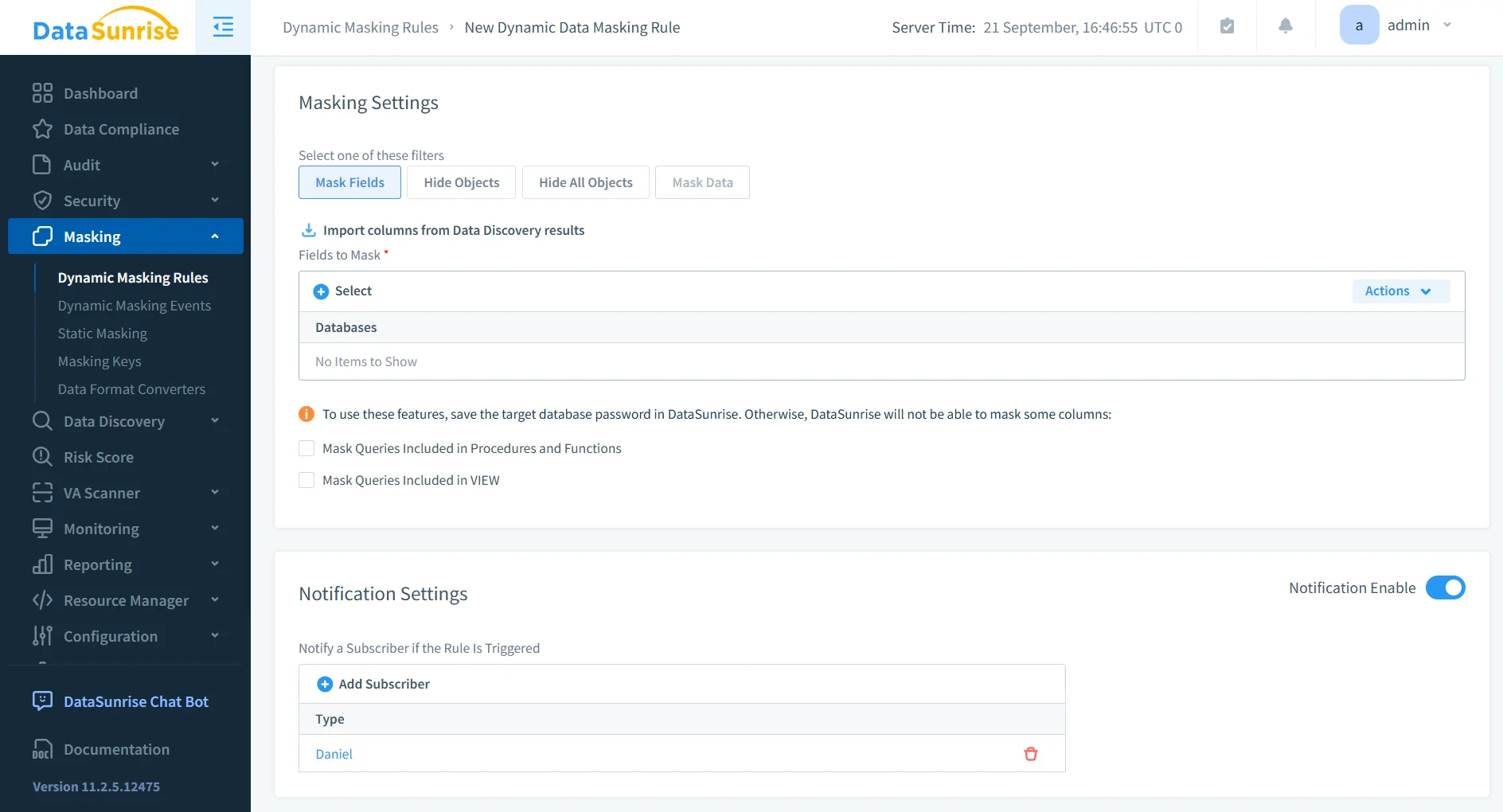
Dynamic Data Masking
Dynamic data masking protects sensitive values at query time, ensuring unauthorized users never see real information. Unlike static masking, it applies rules dynamically without altering stored data or requiring schema changes.
- Replace PII/PHI with masked values for unauthorized users.
- Apply masking policies by role, department, or regulation.
- Ensure real data is never exposed in logs or reports.
- Adapt masking automatically as user roles or regulations change.
This allows organizations to use realistic data for analytics and testing while staying compliant with privacy regulations. More about masking strategies can be found in static data masking.
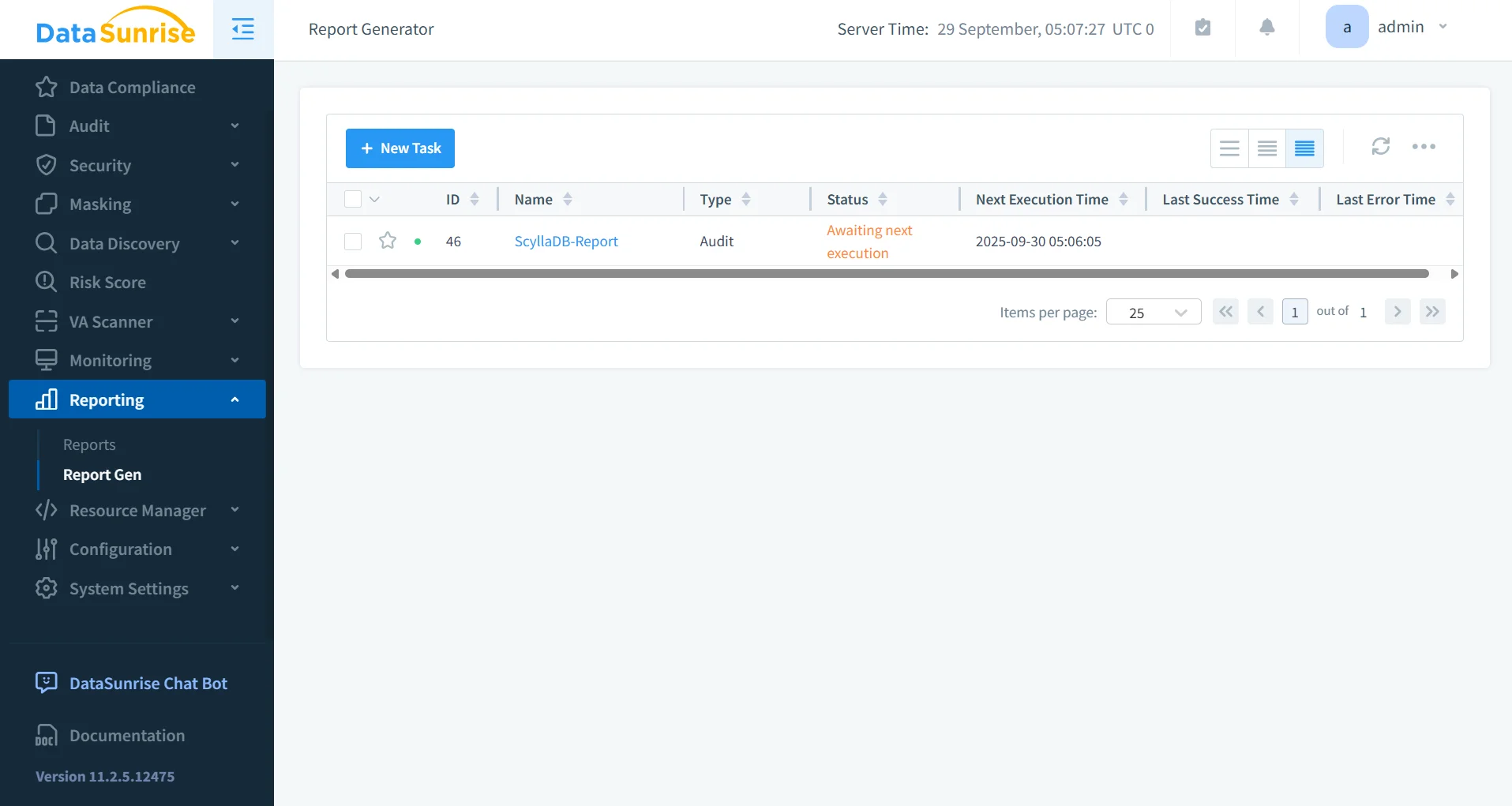
Automated Compliance Reporting
With automated compliance reporting, organizations can demonstrate adherence to regulators with minimal effort. Reports are designed for auditors, offering structured evidence instead of raw logs.
- Generate one-click reports for GDPR, HIPAA, PCI DSS, and SOX.
- Replace days of manual log reviews with auditor-ready evidence.
- Detect compliance drift and align policies continuously.
Automated reporting also provides audit consistency. Instead of each team preparing evidence differently, organizations maintain standardized templates across all audits, reducing confusion and accelerating approval by regulators. More detail is available in report generation.
Business Benefits
Implementing ScyllaDB compliance with DataSunrise yields measurable benefits:
| Benefit | Impact |
|---|---|
| Risk Reduction | Proactively mitigates data breaches and compliance failures. |
| Efficiency | Automates reporting, masking, and monitoring tasks. |
| Audit Readiness | Delivers structured evidence for regulators in minutes. |
| Cost Savings | Reduces manual oversight and compliance maintenance costs. |
| Scalability | Supports growth across hybrid and multi-cloud environments. |
See also compliance regulations overview for additional guidance.
Conclusion
ScyllaDB’s speed and scale make it an excellent choice for modern applications, but native tools alone rarely satisfy strict compliance requirements. By integrating DataSunrise, organizations gain a centralized compliance management platform that covers auditing, monitoring, masking, discovery, and reporting.
With features like Compliance Autopilot, real-time monitoring, and audit-ready reporting, DataSunrise ensures ScyllaDB deployments remain secure and compliant with global regulations while reducing operational overhead.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now