Sensitive Data Protection in SAP HANA
In today's enterprise landscape, protecting sensitive data within in-memory databases has become essential for organizations managing business-critical information. According to IBM's 2024 Data Breach Report, organizations with comprehensive data protection frameworks detect security incidents 87% faster and reduce breach costs by up to $2.3 million.
SAP HANA, SAP's high-performance in-memory database platform, processes massive volumes of transactional and analytical data in real-time. Organizations can learn more about SAP HANA's capabilities in the official SAP HANA documentation. While SAP HANA offers native security policies, organizations operating under stringent compliance requirements often need more sophisticated solutions to ensure comprehensive data protection.
This article explores SAP HANA's native sensitive data protection capabilities and demonstrates how DataSunrise can enhance these features with Zero-Touch Data Masking and automated sensitive data discovery.
Understanding Sensitive Data Protection Requirements for SAP HANA
Sensitive data protection in SAP HANA encompasses multiple security controls designed to safeguard PII, financial records, PHI, and intellectual property. Key challenges include:
- Data Classification: Systematic identification across multiple schemas and diverse data types
- Access Control Complexity: Managing granular permissions at enterprise scale through role-based access controls
- Compliance Requirements: Satisfying GDPR, HIPAA, PCI DSS, SOX simultaneously
- Performance: Protection without degrading real-time processing capabilities
- Multi-Tenancy: Isolating sensitive data between business units
Native SAP HANA Sensitive Data Protection Capabilities
SAP HANA includes several built-in features for protecting sensitive information through access controls and database encryption mechanisms. For detailed configuration guidance, refer to the SAP HANA Security Guide.
1. SAP HANA Security Configuration
SAP HANA offers native database security features for sensitive data protection:
-- Create schema with restricted access
CREATE SCHEMA SENSITIVE_DATA;
CREATE USER finance_analyst PASSWORD "SecurePass123!";
GRANT SELECT ON SCHEMA SENSITIVE_DATA TO finance_analyst;
-- Create table with sensitive information
CREATE COLUMN TABLE SENSITIVE_DATA.CUSTOMER_RECORDS (
customer_id BIGINT PRIMARY KEY,
full_name NVARCHAR(200),
social_security_number NVARCHAR(11),
credit_card_number NVARCHAR(19),
email_address NVARCHAR(255),
account_balance DECIMAL(15,2)
);
2. Row-Level Security Implementation
-- Apply security filter using SQL views
CREATE VIEW SENSITIVE_DATA.CUSTOMER_VIEW AS
SELECT customer_id, full_name, email_address, account_balance
FROM SENSITIVE_DATA.CUSTOMER_RECORDS
WHERE region_id = SESSION_CONTEXT('USER_REGION');
3. Column-Level Encryption
-- Enable encryption for sensitive columns
ALTER TABLE SENSITIVE_DATA.CUSTOMER_RECORDS
ALTER (
social_security_number NVARCHAR(11) ENCRYPTED,
credit_card_number NVARCHAR(19) ENCRYPTED
);
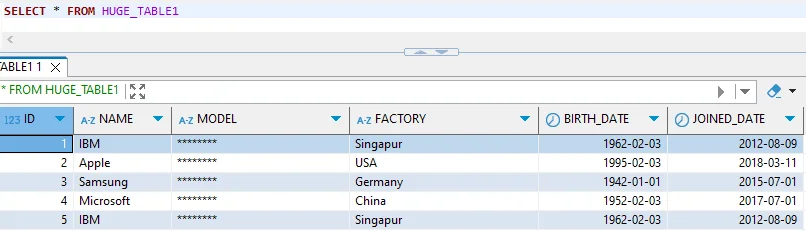
While SAP HANA's native features provide essential protection, organizations with complex compliance requirements encounter limitations including manual column configuration, complex SQL requirements for row-level security, no automated sensitive data identification, and limited native data masking capabilities.
Enhanced Sensitive Data Protection with DataSunrise
DataSunrise significantly enhances sensitive data protection through Autonomous Compliance Orchestration designed for enterprise in-memory databases. Unlike basic security approaches, DataSunrise delivers comprehensive data security with Zero-Touch Data Masking and No-Code Policy Automation, helping organizations mitigate security threats and prevent data breaches.
Setting Up DataSunrise for SAP HANA
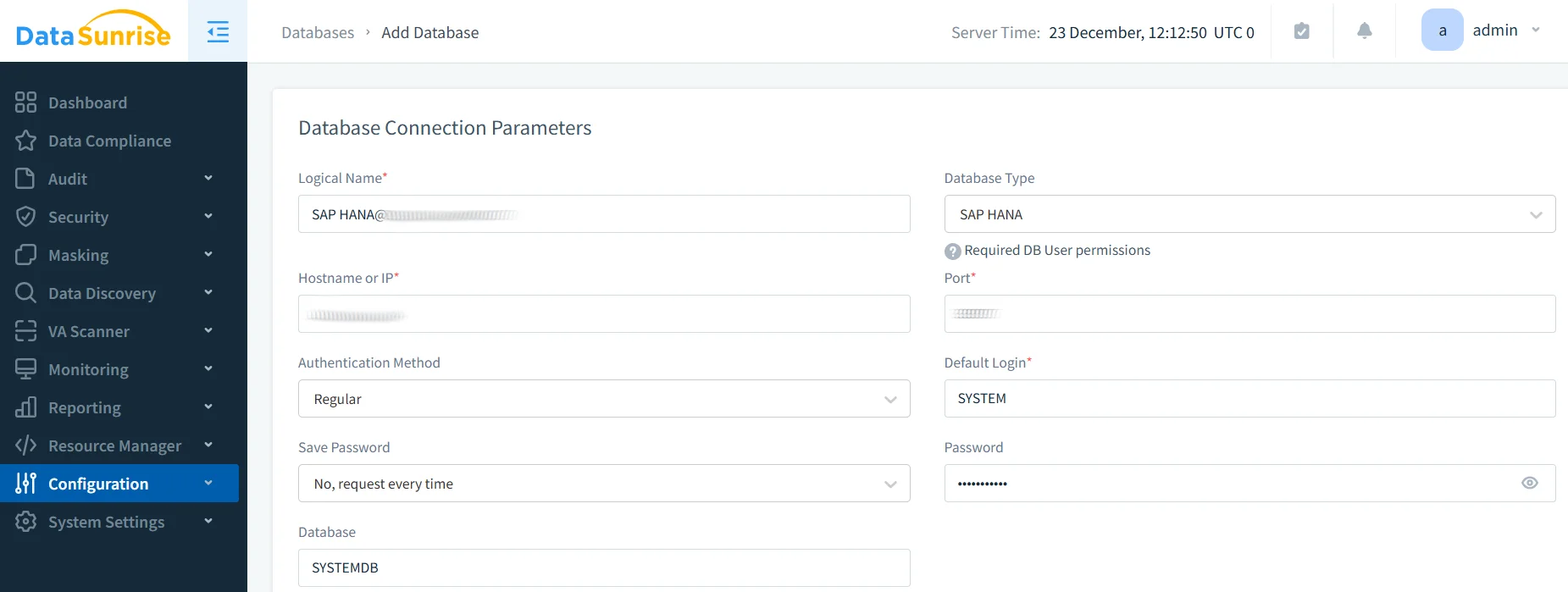
1. Connect to SAP HANA: Establish a secure connection to your SAP HANA environment through DataSunrise's administrative interface. Supports single-node systems, scale-out clusters, and SAP HANA Cloud.
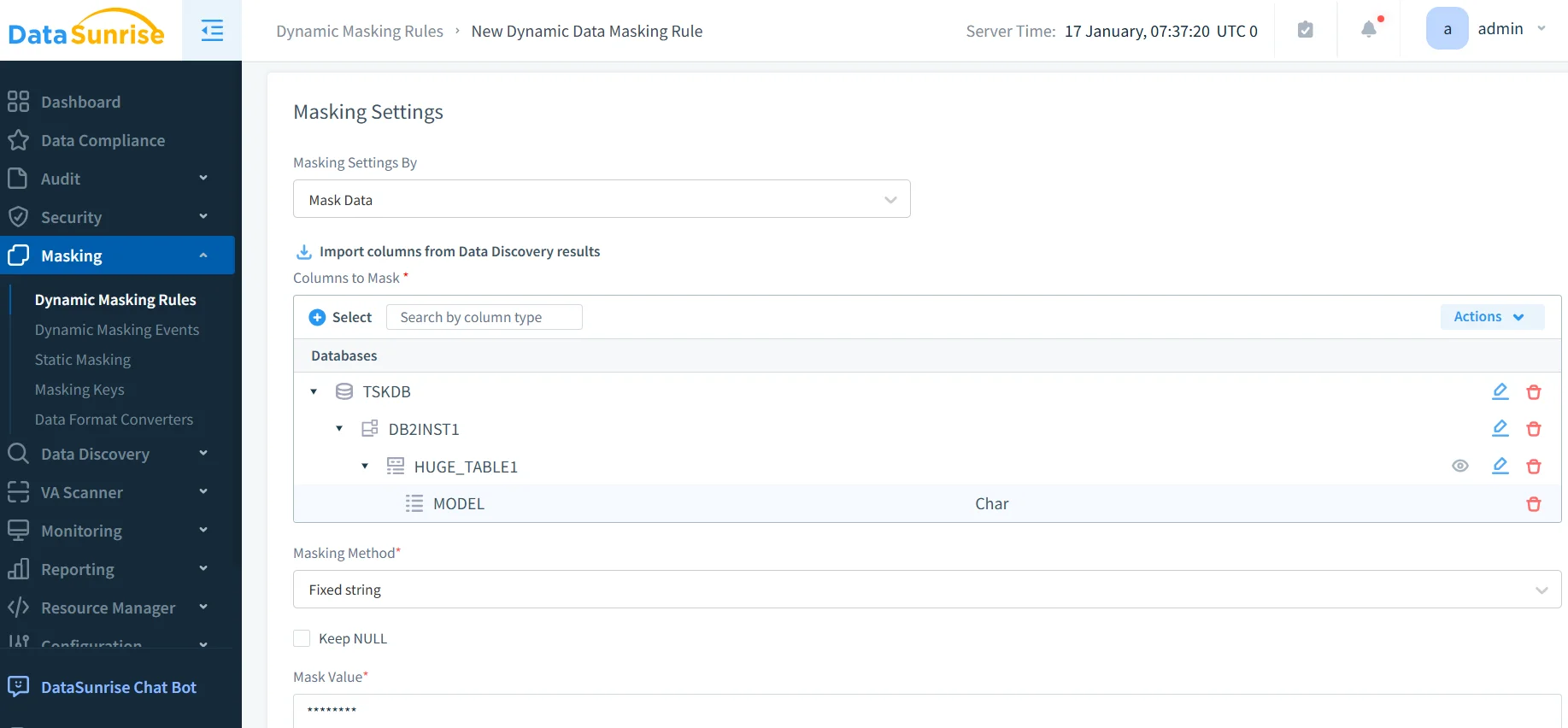
2. Automated Discovery: DataSunrise's Auto-Discover & Classify engine automatically identifies sensitive data including PII, financial data, health information, and credentials across all schemas.
3. Configure Masking Rules: Create masking policies using No-Code Policy Automation with options for full masking, partial masking, conditional masking based on user context, and consistent masking across related tables.
4. Enable Real-Time Protection: Activate continuous monitoring with query analysis, dynamic masking, threat detection, and automated response capabilities.
Key Advantages of DataSunrise for SAP HANA
Comprehensive Sensitive Data Detection: Automatically identify and classify sensitive information using NLP algorithms and machine learning, ensuring 95% greater coverage than manual approaches.
Zero-Touch Data Masking: Protect sensitive fields in real-time without application code changes or performance degradation through transparent dynamic masking.
No-Code Policy Automation: Create sophisticated protection policies through an intuitive interface, reducing implementation time from weeks to hours with surgical precision controls through security rules.
Behavioral Analytics: Establish baselines for normal access patterns and detect anomalies using ML algorithms that identify potential insider threats and enable effective threat detection.
Automated Compliance Reporting: Generate pre-configured reports for GDPR, HIPAA, PCI DSS, and SOX with automated compliance mapping.
Centralized Policy Management: Monitor and protect SAP HANA and other platforms from a unified console with support for over 40 data storage platforms, providing comprehensive database activity monitoring.
Business Benefits of Comprehensive Sensitive Data Protection
Implementing robust sensitive data protection for SAP HANA delivers multiple strategic advantages:
| Benefit | Description |
|---|---|
| Enhanced Security | Proactively protect against unauthorized access, data breaches, and insider threats through continuous monitoring |
| Streamlined Compliance | Automate regulatory adherence and reduce audit preparation time from weeks to hours |
| Risk Mitigation | Prevent data exposure through real-time threat detection and automated response mechanisms |
| Operational Efficiency | Maintain high-performance processing while implementing comprehensive protection |
| Cost Optimization | Reduce compliance costs and avoid regulatory penalties through automated policy enforcement |
Conclusion
As organizations rely on SAP HANA for business-critical operations, implementing comprehensive data protection has become essential for security and compliance. While SAP HANA offers foundational security controls, organizations with complex requirements benefit significantly from enhanced solutions like DataSunrise.
DataSunrise provides enterprise-grade sensitive data protection with Comprehensive Sensitive Data Detection, Zero-Touch Data Masking, and Continuous Compliance Alignment. With flexible deployment modes supporting on-premises, cloud, and hybrid environments, DataSunrise transforms SAP HANA sensitive data protection into strategic security assets.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now