What Is Amazon OpenSearch Audit Trail
What Is Amazon OpenSearch Audit Trail is a question that becomes increasingly important as Amazon OpenSearch is adopted for security analytics, observability, log aggregation, and customer-facing workloads. In practice, OpenSearch often stores authentication events, operational telemetry, application activity, and user-related data. Because of this, every interaction with the cluster can represent a security-relevant action that must be traceable.
At a fundamental level, an Amazon OpenSearch audit trail provides a structured record of database activity. It shows who accessed OpenSearch, what operations were performed, which indices or documents were affected, and when those actions occurred. Unlike simple system logs, an audit trail supports accountability, investigations, and regulatory compliance.
To clarify how this works in real environments, this article explains what an Amazon OpenSearch audit trail is, how it differs from native logging, and how DataSunrise implements a centralized, audit-ready trail for OpenSearch deployments using data audit controls.
Understanding Audit Trails in OpenSearch
An audit trail represents a chronological record of database activity. Within Amazon OpenSearch, this record focuses on REST-based interactions with the cluster rather than on infrastructure metrics or performance statistics.
Specifically, an effective OpenSearch audit trail captures:
- Authentication and access attempts
- Index creation, deletion, and configuration changes
- Document indexing, updates, and deletions
- Administrative and security-related API calls
Together, these records strengthen database security and data security by making user actions transparent, reviewable, and defensible during internal reviews or external audits.
Native Amazon OpenSearch Logging vs Audit Trails
Amazon OpenSearch includes native logging mechanisms and security plugins that capture request metadata. While these logs are useful for troubleshooting and diagnostics, they do not form a complete audit trail.
Several practical limitations appear when teams rely only on native OpenSearch logging:
- Requests appear as isolated events with no session context
- Correlation across multiple REST calls is not available
- Retention depends on cluster configuration and available storage
- Audit evidence must be reconstructed manually
As a result, native logs alone rarely satisfy audit requirements defined by data compliance regulations. Organizations that need provable accountability typically require a dedicated audit trail layered on top of OpenSearch.
How DataSunrise Builds an Amazon OpenSearch Audit Trail
Rather than relying on OpenSearch internals, DataSunrise implements the Amazon OpenSearch audit trail as an external security layer. By observing database traffic through reverse proxy techniques, DataSunrise records audit events in a centralized repository designed for long-term retention.
This architecture ensures that audit data remains independent of the OpenSearch cluster itself. Consequently, database users cannot modify audit records, and the trail retains evidentiary value even during incidents or compliance reviews supported by Compliance Manager.
Audit Rule Configuration
Rule-based monitoring forms the foundation of an effective audit trail. Audit rules define which OpenSearch instances are monitored, which operations are logged, and where audit records are stored using audit logs.
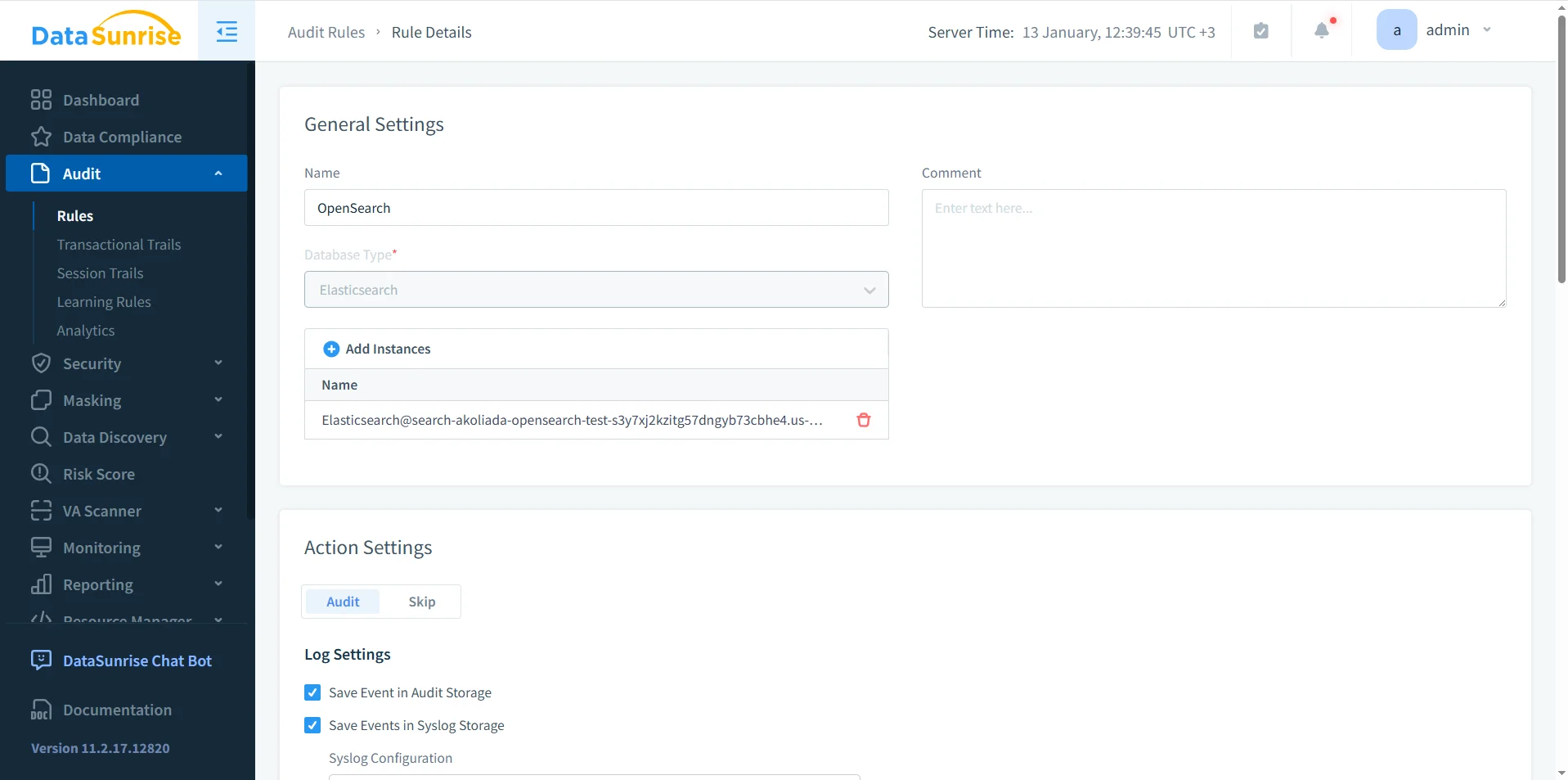
Audit rule configuration showing OpenSearch selected as the database type, associated instances, and enabled audit actions.
Through audit rules, teams can prioritize sensitive operations and suppress low-value traffic. Rule evaluation follows defined rule priority logic, which ensures consistent enforcement across complex environments.
Transactional Trails and Session Context
OpenSearch processes each REST request independently. As a result, native logs tend to fragment user activity into disconnected events.
To address this limitation, DataSunrise correlates individual requests into transactional audit trails. These trails group related operations into a single logical sequence that reflects how users and applications actually interact with OpenSearch, supporting database activity history.
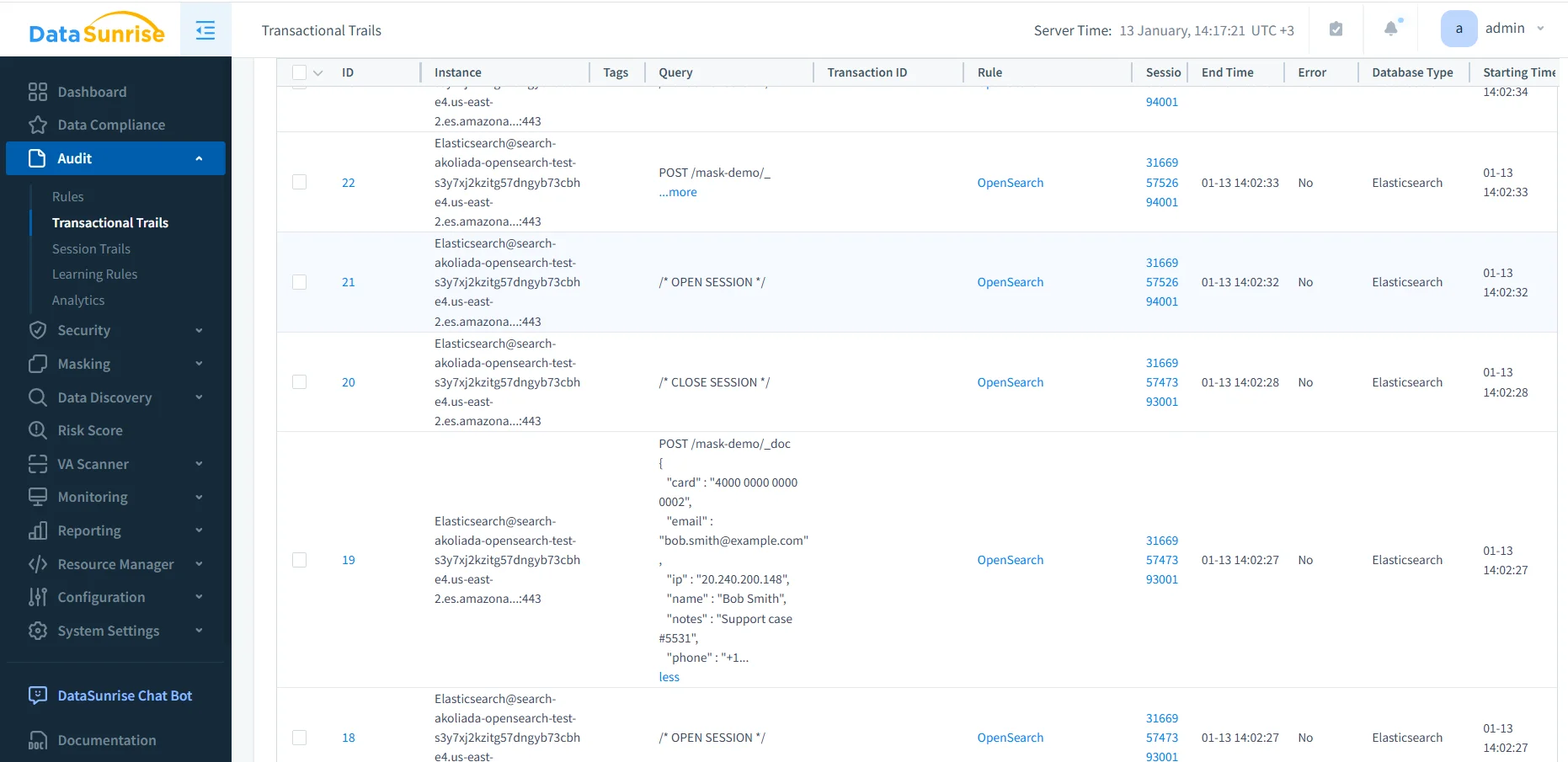
By presenting activity in this form, transactional trails significantly simplify investigations and support deeper database activity monitoring analysis.
Centralized Audit Trail Architecture
DataSunrise captures OpenSearch activity using traffic inspection techniques aligned with enterprise database firewall and monitoring architectures.
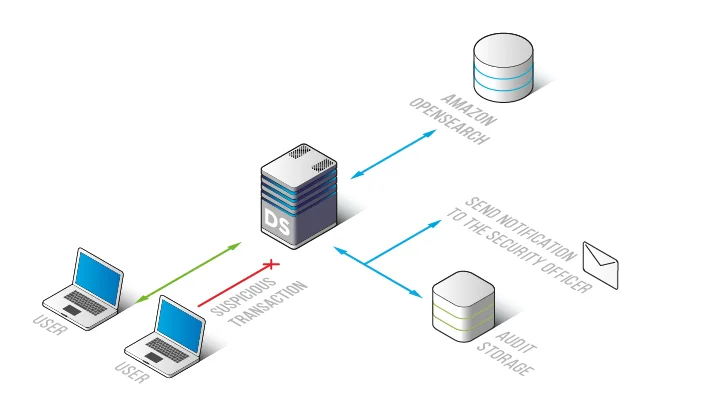
Architecture diagram showing how DataSunrise monitors OpenSearch traffic, stores audit records, and sends notifications for suspicious activity.
In addition, centralized storage integrates with optimized audit storage mechanisms and supports long-term retention policies required for regulatory compliance.
Additional Operational Benefits of an Audit Trail
Beyond security investigations and compliance audits, an Amazon OpenSearch audit trail also delivers operational value. For example, platform teams can use audit data to validate access models, review changes made by automation tools, and analyze the impact of administrative actions.
Over time, audit trails help organizations identify risky patterns such as excessive privilege usage, repeated failed access attempts, or unexpected configuration changes. These insights support continuous improvement of security controls and governance processes supported by user behavior analysis.
Security and Compliance Use Cases
An Amazon OpenSearch audit trail supports a wide range of security and governance scenarios:
- Incident response and forensic investigations
- Access accountability enforced through RBAC
- Detection of anomalous behavior using user behavior analysis
- Audit evidence for GDPR, HIPAA, PCI DSS, and SOX
In practice, these capabilities align closely with centralized audit logs and database activity monitoring strategies.
Start building your Amazon OpenSearch audit trail by focusing on administrative actions and data modification operations. Expanding coverage gradually helps control audit volume while preserving forensic value.
Conclusion
So, what is Amazon OpenSearch audit trail? It is a structured, chronological record of database activity that provides accountability, security visibility, and compliance support.
Although native OpenSearch logging offers basic visibility, it does not deliver a complete audit trail. By implementing DataSunrise, organizations gain a centralized, tamper-resistant Amazon OpenSearch audit trail that supports investigations, audits, and long-term governance.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now