What Is ClickHouse Audit Trail
ClickHouse is designed for high-performance analytical workloads, using vectorized execution, efficient compression, distributed storage, and replicated clusters to deliver exceptional speed. However, this architecture impressive as shown in the ClickHouse documentation — does not automatically provide strong governance capabilities. In practice, the system’s distributed nature makes it difficult to maintain consistent visibility. Queries execute across multiple nodes, logs reside in separate system tables, and operational events may be dispersed across background processes such as merges and part management.
This is why implementing a ClickHouse audit trail is essential.
An audit trail establishes a chronological and tamper-resistant record of activity within the cluster, showing who performed which actions, when they occurred, and how they were executed. It correlates query behavior, access patterns, metadata changes, and server-level operations — principles aligned with Data Audit
and core auditing practices presented in Audit Trails.
Together, these elements form the foundation for accountability, forensic analysis, and regulatory compliance.
ClickHouse offers useful telemetry through components such as system.query_log, system.part_log, system.query_thread_log, and server logs. However, these sources operate independently and do not provide a unified, compliance-ready audit layer. Organizations governed by frameworks such as GDPR, SOX, HIPAA, and PCI DSS typically require more comprehensive audit consolidation and context, similar to the visibility offered through Database Activity Monitoring.
Importance of Audit Trail
A proper ClickHouse audit trail is essential for maintaining control in a system built for speed. High-throughput workloads generate massive noise, and without structured visibility, teams have no reliable way to understand who did what and why. A unified audit trail provides clear accountability by tying each query, connection, or schema change to a specific user or application, eliminating ambiguity during investigations.
It also enables accurate forensic reconstruction. When data is deleted, altered, or produces unexpected analytical results, an audit trail reveals the exact sequence of events, preventing guesswork and shortening incident resolution time.
Compliance frameworks such as GDPR, HIPAA, SOX, and PCI DSS require documented user activity and verifiable monitoring controls. A ClickHouse audit trail supplies the traceability and evidence needed to satisfy auditors.
Beyond regulation, an audit trail reinforces internal security by surfacing abnormal behavior early — privilege misuse, unusual access timings, mass extraction attempts, or unexpected schema modifications. It also supports operational governance in fast-changing ClickHouse clusters, documenting metadata shifts, merges, and structural updates so teams maintain continuity even as environments scale.
Native ClickHouse Audit Signals
ClickHouse logs a wide variety of activity — just not in one place. Core logs include:
1. system.query_log
Captures execution details such as query text, user, client IP, execution time, read/write metrics, and error codes. This is essential for tracing what ran, who ran it, and how expensive it was.
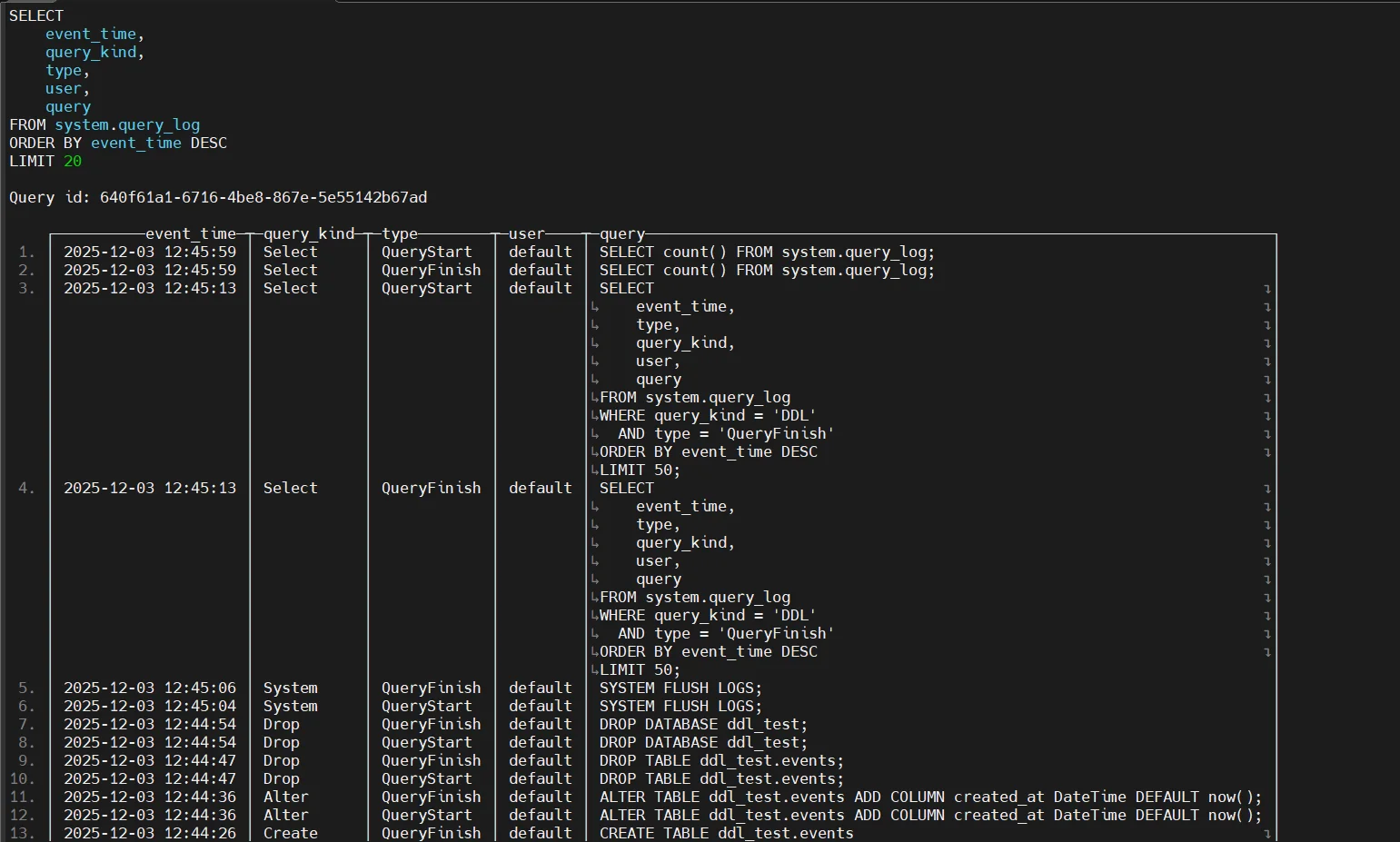
2. system.query_thread_log
Provides thread-level visibility across distributed execution.
Example: Viewing Thread-Level Activity
SELECT
event_time,
query_id,
thread_name,
read_rows,
read_bytes,
memory_usage
FROM system.query_thread_log
WHERE event_date = today()
ORDER BY event_time DESC
LIMIT 15;
Why It Matters
- Helps pinpoint slow shards
- Exposes internal thread behavior
- Supports deep forensic correlation
3. system.part_log
Tracks table-part lifecycle, merges, mutations, and general storage dynamics.
Example: Detecting Part Mutations
SELECT
event_time,
event_type,
table,
part_name,
rows,
bytes_on_disk,
duration_ms
FROM system.part_log
WHERE event_type IN ('NewPart', 'MergeStart', 'MergeEnd', 'MutatePart')
ORDER BY event_time DESC
LIMIT 20;
Benefits
- Identifies merge pressure
- Detects mutation regressions
- Correlates user actions with storage behavior
4. Server Logs
Expose authentication attempts, configuration reloads, replication issues, and system exceptions.
Example (Log File):
grep "Authentication" /var/log/clickhouse-server/clickhouse-server.log
Example (system.text_log):
SELECT
event_time,
host_name,
client_ip,
message
FROM system.text_log
WHERE message ILIKE '%Authentication%'
ORDER BY event_time DESC
LIMIT 20;
Why Server Logs Matter
- Capture failed logins
- Reveal cluster instability
- Provide deep operational diagnostics
These logs support layered security methods such as
Database Firewall.
How DataSunrise Enhances ClickHouse Audit Trails
DataSunrise transforms fragmented ClickHouse telemetry into an enterprise-grade, contextual, and enforceable audit layer.
Centralized ClickHouse Audit Timeline
DataSunrise consolidates query logs, authentication events, DDL/DML actions, part operations, session metadata, and sensitive-data access into one chronological view. By correlating user identity, object interactions, query behavior, and storage dynamics, the platform produces a coherent forensic narrative that greatly simplifies investigation and compliance validation.
- Provides a unified timeline for all database actions
- Correlates user identities with real query and storage behavior
- Enables reconstruction of full event chains in complex clusters
- Reduces the effort required for audit preparation
- Enhances traceability for regulated workflows
Granular Audit Rules
DataSunrise allows administrators to define extremely precise audit policies targeting tables, schemas, users, operations, or sensitivity levels. These rules adapt dynamically to system requirements and risk posture.
- Audit only the objects that matter most
- Apply rules selectively to reduce noise
- Monitor privileged accounts with higher scrutiny
- Capture both DDL and DML actions with full context
- Flexibly adjust audit scope without service interruption
Sensitive-Data Mapping & Classification
Automated discovery identifies regulated fields and tags audit events accordingly, ensuring full visibility into which sensitive datasets were accessed.
- Detects PII, PHI, PCI, and custom sensitivity categories
- Links sensitivity labels directly to audit events
- Helps validate compliance with data-protection standards
- Supports analyst investigations with context-rich metadata
- Prevents blind spots around privileged or accidental exposure
Real-Time Enforcement
DataSunrise adds an active protection layer that monitors and blocks high-risk behavior. Controls include SQL injection detection, anomaly scoring, privilege misuse detection, and real-time blocking of suspicious operations.
- Blocks malicious queries before execution
- Detects abnormal access behavior using UEBA
- Identifies compromised or misused accounts
- Enforces rules dynamically during live operations
- Reduces the likelihood of insider-driven or external attacks
Automated Compliance Evidence
The system generates compliance-ready reporting aligned with GDPR, HIPAA, PCI DSS, and SOX. Reports summarize sensitive-data interactions, event patterns, anomalies, and triggered rules to support formal audit requirements.
- Automatically compiles structured audit evidence
- Reduces manual compliance workloads
- Highlights policy violations and security gaps
- Supports recurring audits with consistent formatting
- Improves audit readiness for highly regulated sectors
Additional compliance topics are found through
Data Compliance.
Cross-Platform Visibility
DataSunrise supports over 40 database platforms, delivering unified governance across hybrid, on-premises, and cloud environments.
- Ensures uniform policy enforcement across engines
- Eliminates monitoring blind spots in multicloud architectures
- Simplifies administration of security and audit workflows
- Enables centralized visibility for distributed teams
- Supports consistent compliance across diverse data stacks
Business Impact of a ClickHouse Audit Trail
| Business Impact Area | Description |
|---|---|
| Strong Regulatory Posture | Auditors receive immutable, structured evidence without manual work. |
| Faster Investigations | Timeline correlation cuts incident analysis time dramatically. |
| Lower Data-Misuse Exposure | Real-time enforcement stops threats before data leaves the system. |
| Clear Accountability | Every action maps to an identity — no ambiguity, no excuses. |
| Standardized Governance Across Systems | Consistent audit rules and reporting across all data platforms. |
Conclusion
A ClickHouse audit trail extends far beyond basic logging. It provides a unified, contextualized view of activity across a distributed analytical engine. Native telemetry delivers fragments of the truth, but converting those fragments into actionable, compliant audit evidence requires correlation, enrichment, and real-time control.
DataSunrise closes that gap by delivering a structured, high-fidelity, enterprise-ready audit trail for ClickHouse. For organizations operating in regulated environments or requiring tight governance, it transforms ClickHouse from a visibility challenge into a verifiable, auditable, and secure data platform.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now