
Amazon S3 Data Activity History

Introduction
When teams talk about Amazon S3 audit logs, and data activity history most think about end‑users reading or writing files—but activity history goes far beyond. It captures meta‑level changes: permission changes, lifecycle transitions, replication events, and anomalous access patterns across environments. A comprehensive activity history is invaluable to security engineers, audit teams, and DevOps architects seeking forensic clarity and operational visibility.
This deep‑dive explores the architectural foundations, native mechanisms (CloudTrail, server logs, Storage Lens), and advanced patterns (EventBridge, OpenSearch, Lambda) needed to establish a scalable S3 activity history pipeline that’s compliant, performant, and searchable.
Core Components of S3 Activity History
1. CloudTrail Data Events (Object‑level)
CloudTrail can log object-level API calls—like GetObject, PutObject, DeleteObject, tags, and object versioning operations. These logs include identity, source IP, request parameters, and time stamps. Note: data events are disabled by default and incur additional costs (Amazon S3 CloudTrail events).
2. Server Access Logs
This legacy feature logs each request to S3 with requester, bucket, key, operation, HTTP code, bytes transferred, and timestamp. Logs are stored in S3 but require heavy parsing. They’re useful for tracking anomalies like unusual HEAD requests or unexpected IP patterns (Server Access Logs Guide, AWS Blog Post).
3. S3 Inventory and Storage Lens
- S3 Inventory: A scheduled CSV/Parquet report listing all objects with metadata such as encryption status, replication, storage class, and last modified timestamp. Great for auditing configuration state, but not for real‑time access events (S3 Inventory Guide).
- Storage Lens: Provides organization-wide metrics (e.g. PUT/GET request counts, unencrypted storage ratio). Can feed CloudWatch dashboards and anomaly detection alerts (S3 What's New).
Why Basic Logs Alone Are Not Enough
| Requirement | Native AWS Support |
|---|---|
| Real-time anomaly alerts | Requires custom pipelines |
| Cross-account unified search | No native aggregation |
| Historical change tracking of bucket policies | Only IAM logs, separate from data access |
| Object classification context (PII, PHI) | No built-in data tagging |
| Queryable access history interface | Needs Athena, OpenSearch, or external UI |
S3 native logs answer "what happened", but not "why" or "is it policy‑compliant". Security teams need unified visibility across buckets, accounts, and time ranges.
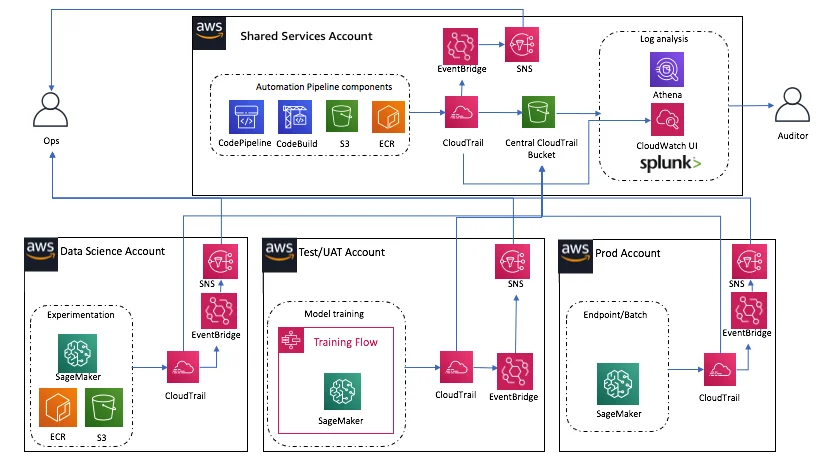
Building a Centralized S3 Activity History — AWS Reference Pattern
A modern pattern, recommended by AWS Enterprise Search and Audit guidance, centralizes events from multiple AWS accounts into an aggregation account—processing them to a searchable backend like Amazon OpenSearch Service (AWS Architecture Guide, Architecture PDF, Prescriptive Logging Guidance):
- Enable CloudTrail data events for all relevant buckets across accounts.
- Route these events to EventBridge and forward to a central aggregation account.
- Use SNS/SQS to buffer event streams flowing into Lambda processors.
- Lambdas enrich events: add object metadata (via HEAD), tag patterns, risk scoring.
- Store enriched records in OpenSearch, indexed by bucket, user, operation, tags.
- Optional UI: a static website or Kibana-based dashboard for searching/tagging.
This architecture supports fast queries like “show all GetObject requests on bucket X accessing keys matching GDPR patterns in region EU west‑1”.
Amazon S3 Data Activity History Sample Record (Enriched)
{
"eventType": "GetObject",
"timestamp": "2025-07-25T14:12:34Z",
"bucket": "confidential-reports",
"key": "2025/Q2/finance.xlsx",
"userIdentity": {
"type": "Role",
"principal": "analytics-service-role"
},
"sourceIP": "198.51.100.27",
"geo": "IE",
"matchedTag": "financial-pii",
"objectSize": 15487632,
"encryption": "SSE-KMS",
"policyAllowed": true,
"anomalyScore": 8.5
}
Compared to raw logs, this enriched activity history record adds context: whether the object had sensitive content, whether the access was policy-compliant, geolocation, and anomaly scoring.
Optional Enhancements & Tools
- Automatic monitoring: Configure AWS Lambda + SNS/Kinesis to fan out S3 event notifications into a history bucket or analytics stream (Monitoring Blog).
- Python Pandas + Athena: Parse server access logs at scale to generate custom reports (e.g. deletes during off-hours, high-volume GET spikes) (Monitoring Blog with Pandas).
- GuardDuty S3 protection: Works from CloudTrail logs to detect unusual data access patterns, IAM misuse, or brute-force attempts (Monitoring Overview).
Audience Use Cases
Security & Incident Response
- Investigate unauthorized downloads by cross-referencing IP+user+object tags.
- Build alerts around anomalous GET rates or infected usage volumes.
Compliance and Audit
- Show auditors a searchable trail of object access and lifecycle operations.
- Demonstrate encryption status over time and object-level metadata changes.
DevOps & Governance
- Ensure consistent bucket policies & ACLs across accounts by linking policy changes with access events.
- Track replication and object lock status for GDPR/retention compliance.
Quick Setup Checklist: AWS‑Native Activity History
- Enable CloudTrail data events for target buckets with object-level logging
- Deliver logs centrally via EventBridge into aggregation account
- Buffer and route events using SNS/SQS + Lambda
- Enrich records with HEAD metadata, tag classification, anomaly scores
- Store structured history in OpenSearch or a queryable data lake
- Visualize and search using Kibana, Athena, or static UI
Amazon S3 Data Activity History with DataSunrise
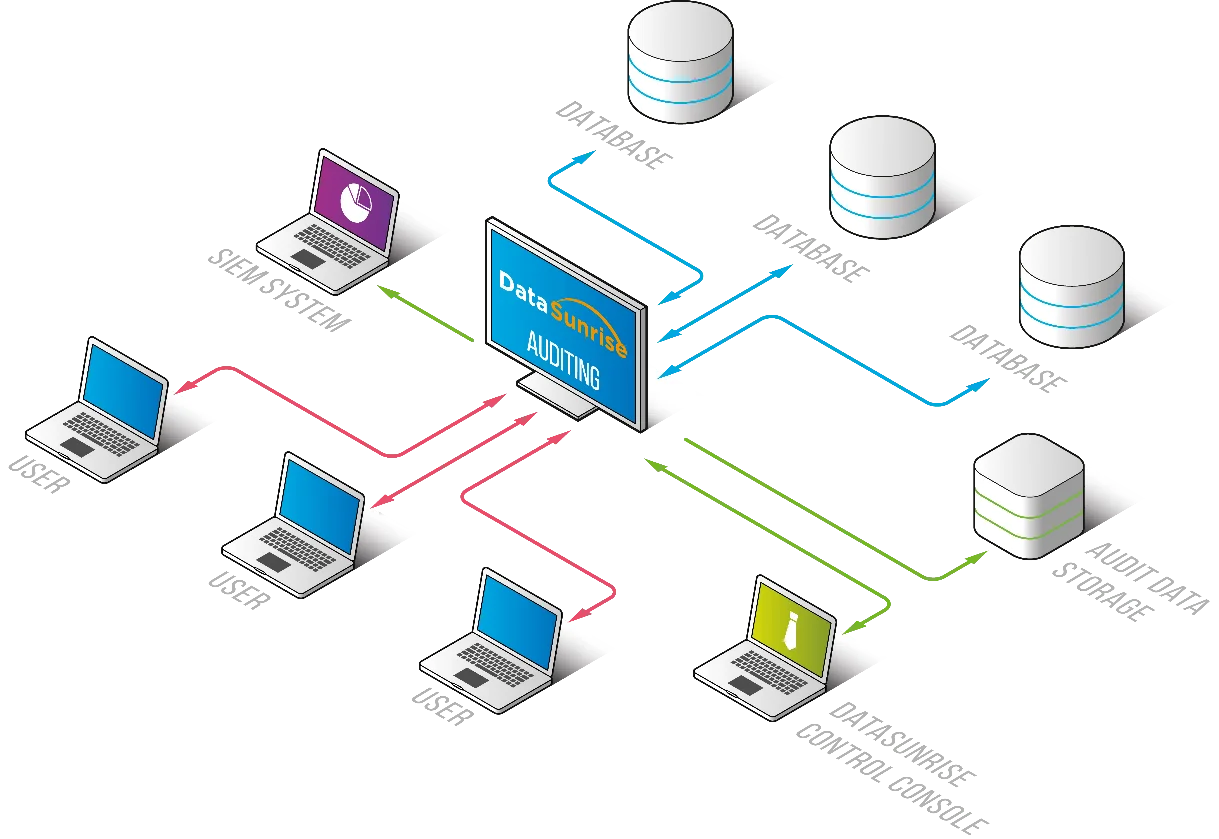
While native AWS tools like CloudTrail, Server Access Logs, and S3 Inventory provide foundational telemetry, platforms like DataSunrise significantly enhance S3 activity history by delivering a centralized, intelligent, and compliance-ready approach to tracking and securing object-level access.
Unlike raw log aggregation, DataSunrise offers real-time context, automated tagging, and security policy enforcement—without needing to build or maintain complex pipelines.
Key Enhancements with DataSunrise
- Sensitive Data Classification: Automatically detects PII, PHI, and PCI data inside S3 objects using deep content inspection and OCR-driven scanning, including image-based data and semi-structured files.
- Dynamic Data Masking: Enforce real-time masking based on user role, source IP, or API method. Mask or redact content in logs and dashboards to prevent unauthorized data exposure during investigations or audits.
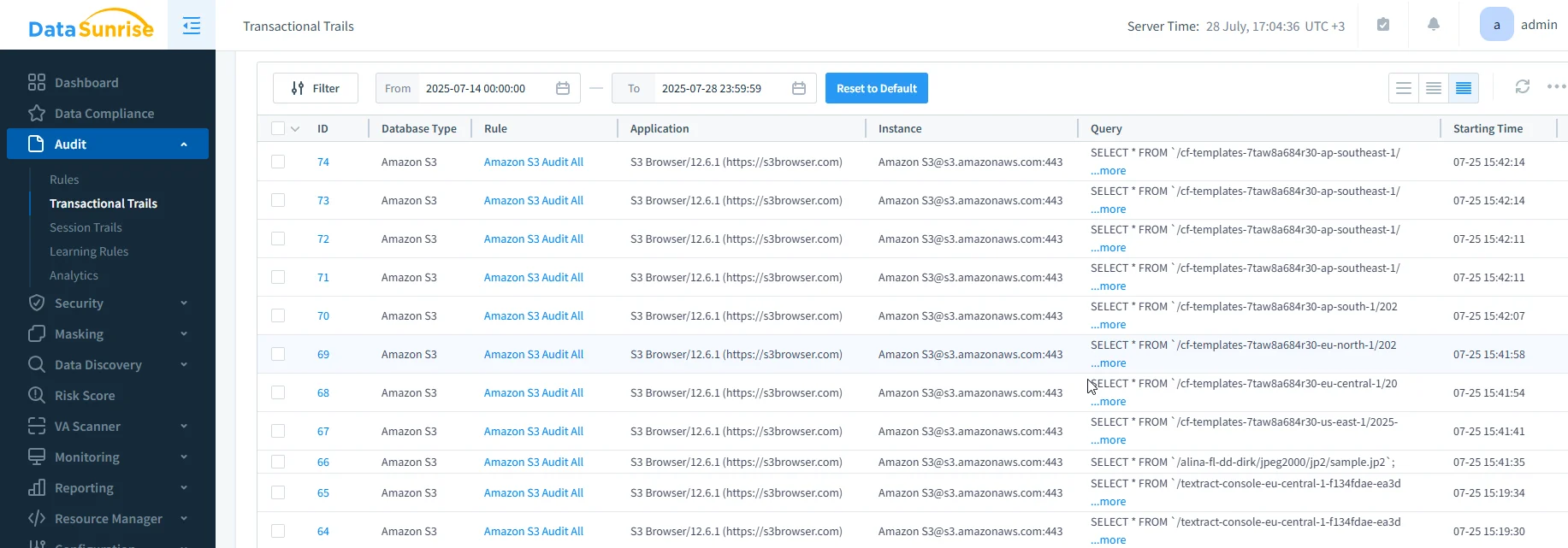
- Audit Rule Automation: Automatically apply granular audit rules based on object type, access patterns, user groups, or compliance tags—creating a targeted, noise-free audit trail.
- Integrated Threat Detection: Pair activity logs with user behavior analytics and anomaly scoring to detect suspicious downloads, privilege escalation, or brute-force access attempts.
- Real-Time Alerting: Configure notifications via Slack, Teams, SIEM, or email for any policy violation or sensitive data access event, reducing time to response.
- Cross-Platform Audit Correlation: Correlate S3 access events with RDS, Redshift, MongoDB, and file storage, building a unified view of data activity across your cloud footprint.
- Compliance-First Architecture: Use built-in templates for SOX, HIPAA, PCI DSS, and GDPR to generate audit-ready reports that map user access to regulatory controls—automatically.
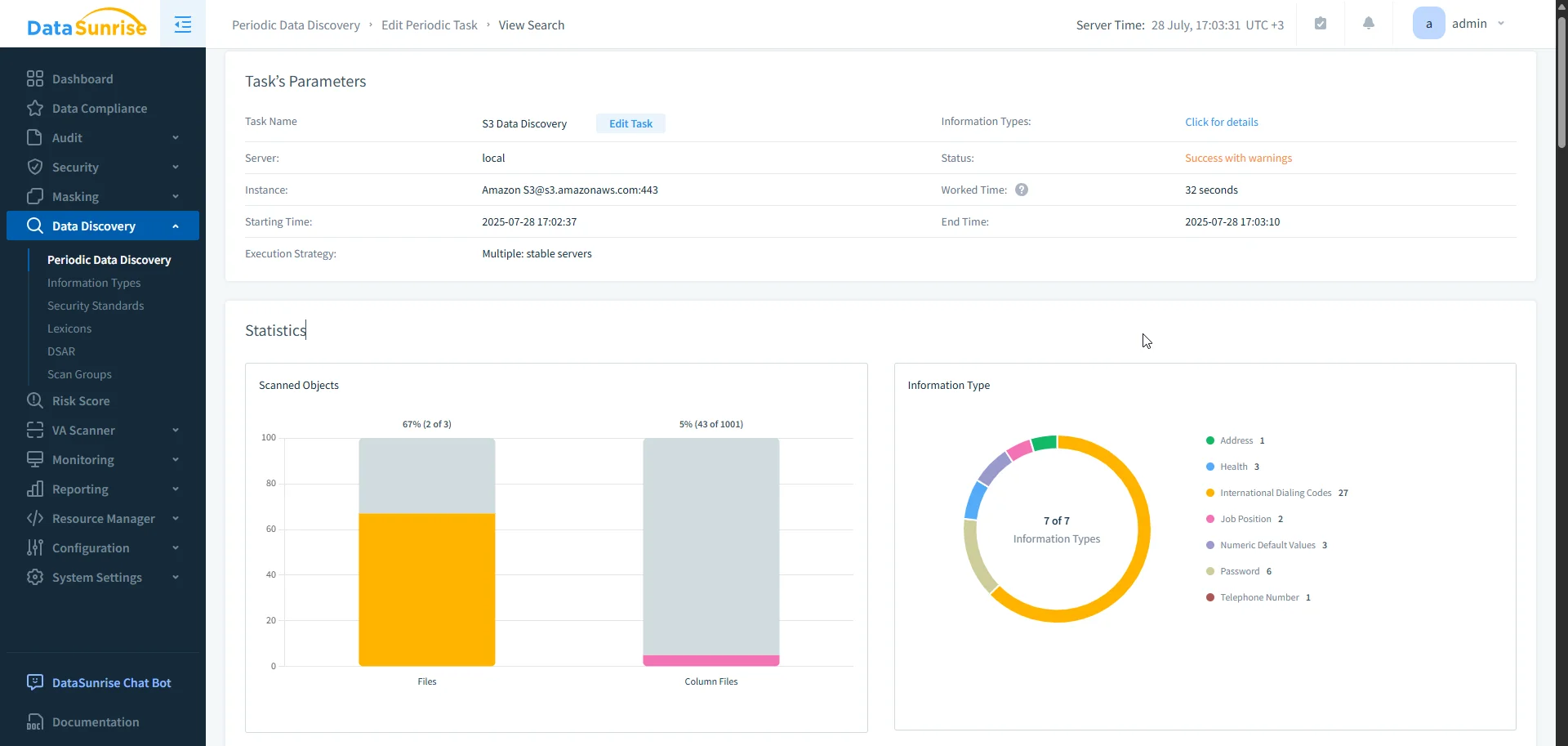
Business Value
By turning passive logs into actionable, policy-aware events, DataSunrise helps organizations move from reactive log reviews to proactive data protection and audit automation. This not only improves security posture but also reduces manual effort for security, compliance, and operations teams.
Looking to extend your S3 audit trail with zero-touch compliance and full-stack visibility? Try a live demo and discover how DataSunrise accelerates secure cloud operations.
Final Thoughts
Building a robust Amazon S3 activity history means thinking beyond simple read/write logs. It’s about crafting an audit-grade, searchable, enriched timeline of file-level operations, permission changes, and context-aware metadata—across teams, accounts, and timezones.
The AWS-built central aggregation architecture offers a scalable foundation—but security teams looking for faster deployment, richer context, and built-in compliance reporting may evaluate purpose-built platforms like DataSunrise.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now