
Amazon S3 Data Audit Trail

In modern cloud environments, Amazon S3 often holds sensitive datasets—from regulatory documents to machine learning models, PII, and healthcare records. Capturing a structured and enriched audit trail of object-level activity is essential not only for compliance but also for proactive data security.
This article explores architecture patterns, native AWS capabilities, and value-added features from DataSunrise that transform logs into strategic insights.
Native Amazon S3 Data Audit Trail: Foundations and Limitations
AWS offers multiple built-in options to record S3 activity:
- CloudTrail Data Events track detailed operations like
GetObject,PutObject,DeleteObject, ACL changes, and tagging. Object‑level logging must be enabled per bucket and comes at an extra cost. - Server Access Logs log request-level metadata (HTTP code, bytes transferred, operation type) and need parsing to extract structure.
- Storage Lens and S3 Inventory offer organization-wide metrics and configuration snapshots—useful for compliance checks, but not sufficient for access event forensics.
Native tooling lacks rich content context, dynamic masking, anomaly detection, or centralized audits across accounts.
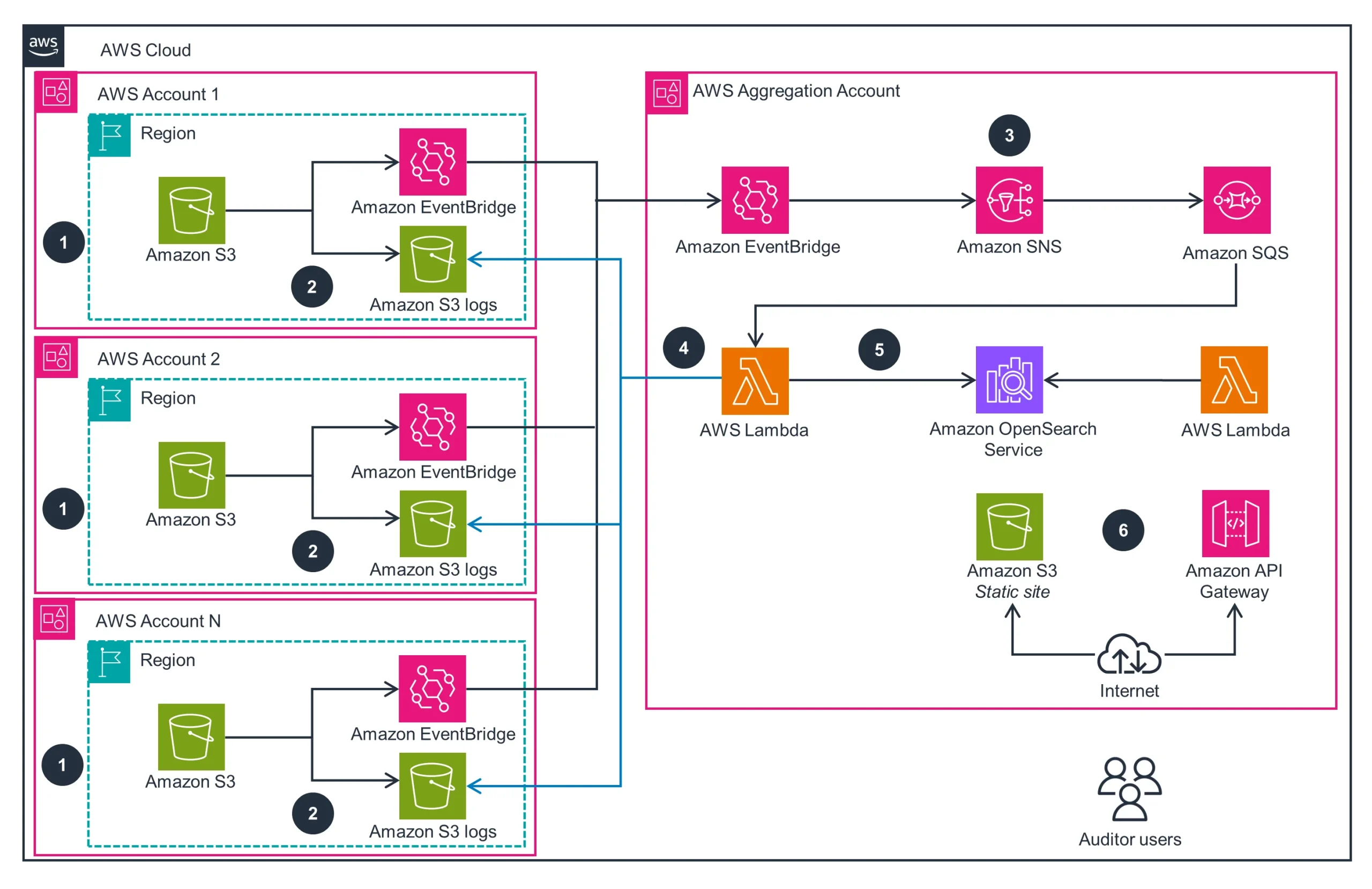
AWS Architectural Pattern: Centralized Activity History
A proven architecture for enterprise-scale S3 audit visibility follows a centralized aggregation pattern:
- Enable CloudTrail data events in each AWS account.
- Route events via EventBridge into a central aggregation account.
- Buffer messages with SNS → SQS, processed in Lambda.
- Use Lambda to add HEAD metadata and tag classification.
- Index enriched data in Amazon OpenSearch Service.
- Offer a UI on S3 static hosting or Kibana for interactive search.
This foundation supports queries like “all GETs of GDPR-tagged keys in EU-West-1 in the last 7 days.”
Platform Enrichment: Why DataSunrise Amplifies Audit Value
DataSunrise takes the architecture above and enhances it with intelligent automation, contextual insight, and built-in compliance support.
- Sensitive Data Discovery: Scans S3 objects for PII, PHI, PCI using OCR and NLP-based detection to classify files dynamically.
- Dynamic Data Masking: Enforce masking rules based on user roles, IP ranges, or time contexts.
- Granular Audit Rules: Configure fine-grained audit policies that auto-log or block based on object type, tag, and user behavior.
- User Behavior Analytics: Monitor access patterns to detect anomalies and threats in real time.
- Compliance Automation: Prebuilt templates and reporting tools for GDPR, HIPAA, PCI DSS, and SOX.
- SIEM & Notification Integration: Deliver alerts to Slack, Microsoft Teams, email, or directly into your SIEM pipeline.
Sample Architecture with Enrichment Layer
This architecture uses DataSunrise as a smart enrichment layer atop AWS-native logs:
- Data events flow into aggregation pipelines
- HEAD metadata and content classification are applied automatically
- Risk scoring and masking occur in real time
- Events are indexed into OpenSearch or long-term audit storage
- Reports and dashboards are generated live for auditors and DevSecOps
Strategic Outcomes
| Objective | Native AWS Approach | With DataSunrise |
|---|---|---|
| Sensitive data visibility | None | Automated discovery and tagging |
| Access masking | Manual redaction | Role/IP/time-based real-time masking |
| Rule-based filtering | Custom Lambda logic | Configurable audit rules via UI |
| Alerting on high-risk behavior | Custom SIEM or scripts | Built-in anomaly detection & alert pipelines |
| Compliance reporting | Athena + manual report building | One-click templates for auditors and executives |
| Cross-platform correlation | Separate logging per service | Unified S3 + Athena + RDS + MongoDB audits |
Getting Started with Amazon S3 Data Audit Trail in DataSunrise
To deploy a DataSunrise-powered S3 audit trail quickly:
- Connect your S3 environment to DataSunrise (proxy or CloudTrail mode)
- Define audit rules for access types, object tags, or sensitivity levels
- Enable real-time masking and alert rules
- Integrate with dashboards, SIEM, or Slack notifications
Conclusion
Amazon S3 Data Audit Trails built with AWS-native services offer raw access visibility—but DataSunrise enables content-level insight, risk-aware enforcement, and auditor-ready reporting.
By pairing automation with deep audit capabilities, you unlock scalable governance and reduce time-to-detection.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now