ClickHouse Data Audit Trail
ClickHouse’s columnar engine and distributed execution model make it one of the fastest analytical databases available. That same architecture, however, creates a real headache for governance: high-frequency ingestion, parallel execution threads, and multi-node clusters generate a huge amount of operational noise. Organizations in finance, telecom, healthcare, and other regulated environments must maintain a complete data audit trail—one that tracks query activity, user behavior, and administrative actions with enough detail to meet compliance frameworks such as GDPR, PCI DSS, HIPAA, SOX, and ISO 27001.
ClickHouse includes several native telemetry sources: system.query_log, system.part_log, server logs, access control logs, and query thread logs. These components are useful but fragmented. None of them provide a single unified, compliance-ready audit trail. This article explains how ClickHouse’s native logs work, their strengths, and how DataSunrise, through its Data Audit engine and unified Database Activity Monitoring, provides centralized monitoring, enriched analytics, and end-to-end ClickHouse audit governance.
For more information on ClickHouse itself, refer to the official documentation:
https://clickhouse.com/docs/en/
Importance of Data Audit Trail
A strong data audit trail is essential for keeping ClickHouse environments transparent and accountable. When operations run at high speed and across multiple nodes, you need a consistent record of who accessed which data, what changes were made, and how queries behaved. Without that visibility, compliance gaps and undetected misuse become inevitable.
A complete audit trail supports regulatory compliance, accelerates investigations, identifies insider risks, and ensures the integrity of data transformations. Without it, ClickHouse becomes powerful but opaque; with it, organizations gain control and verifiable trustworthiness. This aligns closely with principles outlined in DataSunrise’s Audit Logs and Data Activity History materials.
Native ClickHouse Data Audit Trail Capabilities
1. Query Execution Trail
The main audit surface in ClickHouse is the query log. When enabled, it records a detailed history of executed queries, including query text, user identity, source IP, execution timing, read and write volumes, exceptions, memory usage, and status. Such detailed tracking is foundational to any audit trail implementation.
SELECT
event_time,
query_kind,
query,
user,
client_hostname,
read_rows,
written_rows,
result_rows
FROM system.query_log
WHERE event_date >= today()
ORDER BY event_time DESC
LIMIT 50;
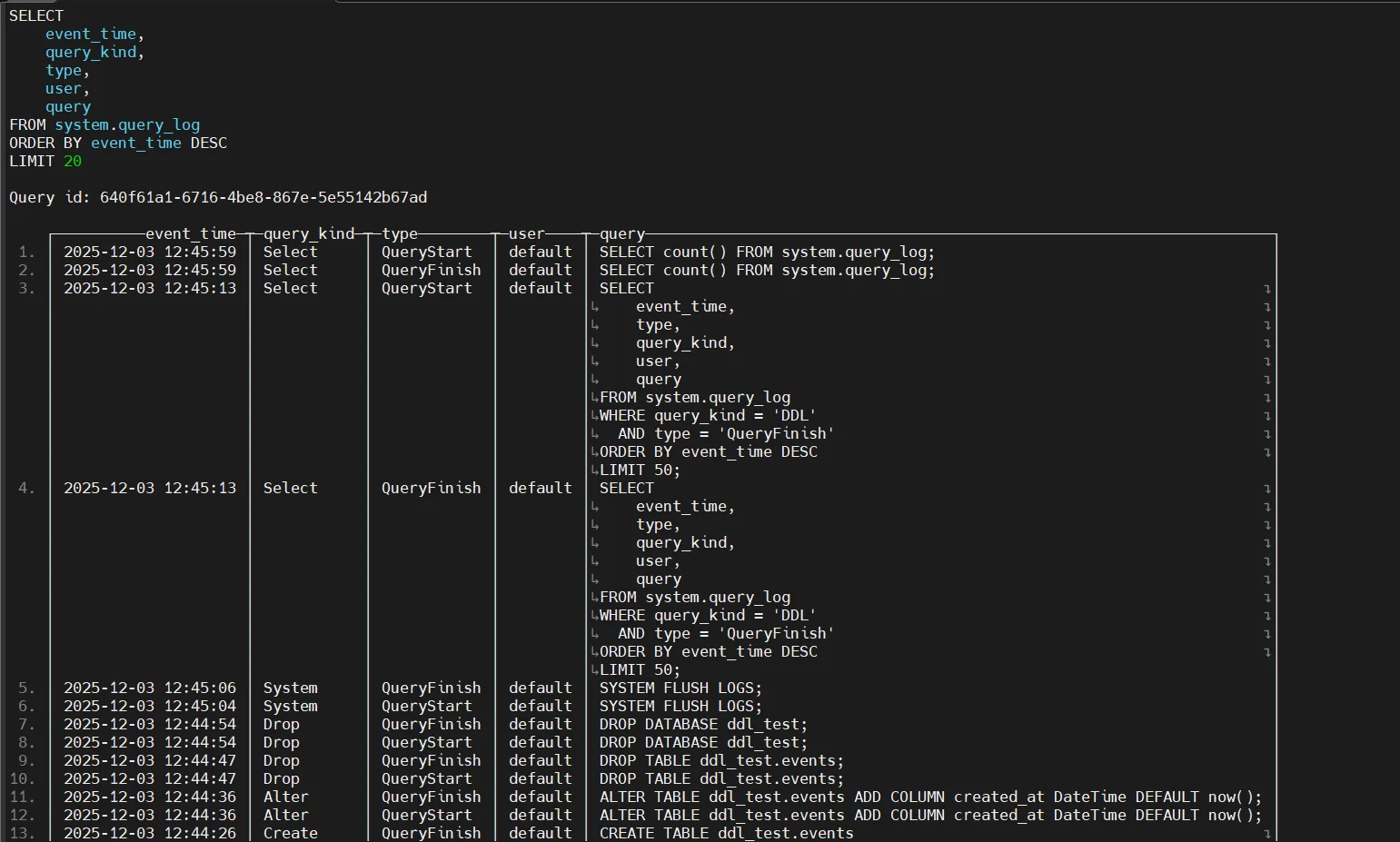
2. Query Thread Trail
This log provides insight into the internal execution of queries at the thread level. It is especially useful for performance forensics, troubleshooting distributed execution, and analyzing anomalous data access behavior across query fragments—similar in nature to how DataSunrise traces deep query flows within its Security analytics pipeline.
SELECT
event_time,
query_id,
thread_name,
read_rows,
memory_usage
FROM system.query_thread_log
ORDER BY event_time DESC
LIMIT 100;
3. Access Control Logging
Authentication and authorization activity appears in server logs rather than structured system tables. These logs capture failed logins, invalid privileges, and other access control events—critical signals for security and compliance investigations, reinforcing the least-privilege approach described in DataSunrise’s RBAC guide.
Authentication failed for user 'analytics_user' from 10.21.10.54: password mismatch
Access denied: user 'bi_reader' has no privileges for SELECT on sensitive.payments
4. Part & Merge Trail
ClickHouse stores data in “parts,” which undergo merges, mutations, deletions, and lifecycle events. system.part_log provides visibility into these operations, showing how data is reorganized or modified over time—essential for validating integrity and understanding internal data operations.
SELECT event_type, part_name, rows, duration_ms
FROM system.part_log
ORDER BY event_time DESC
LIMIT 20;
5. Server Logs
Server logs contain a wide range of operational metadata: executed DDL statements, user and role changes, replication events, cluster-level failures, connection issues, and configuration reloads. Although unstructured, they provide critical context during audits and investigations.
2025.01.18 14:22:11.904751 [ 15 ] {} <Information> executeQuery: (from 10.21.12.44) CREATE TABLE analytics.events (id UInt64, ts DateTime) ENGINE = MergeTree ORDER BY id
2025.01.18 14:22:12.017843 [ 33 ] {} <Warning> Access: Access denied: user 'readonly_user' cannot execute INSERT on table analytics.events
2025.01.18 14:22:13.129004 [ 42 ] {} <Error> ReplicationQueue: Lost connection to replica replica01: Connection refused
2025.01.18 14:22:14.350112 [ 17 ] {} <Information> Configuration: Reloaded config from /etc/clickhouse-server/config.xml
DataSunrise Data Audit Trail for ClickHouse
DataSunrise introduces a centralized audit layer that unifies ClickHouse telemetry from all nodes into a structured, enriched, compliance-ready audit trail. It correlates queries, execution paths, user identities, and system events, transforming fragmented raw logs into a cohesive forensic and compliance dataset. This aligns with the broader DataSunrise platform design detailed in their Overview and multi-environment Deployment Modes.
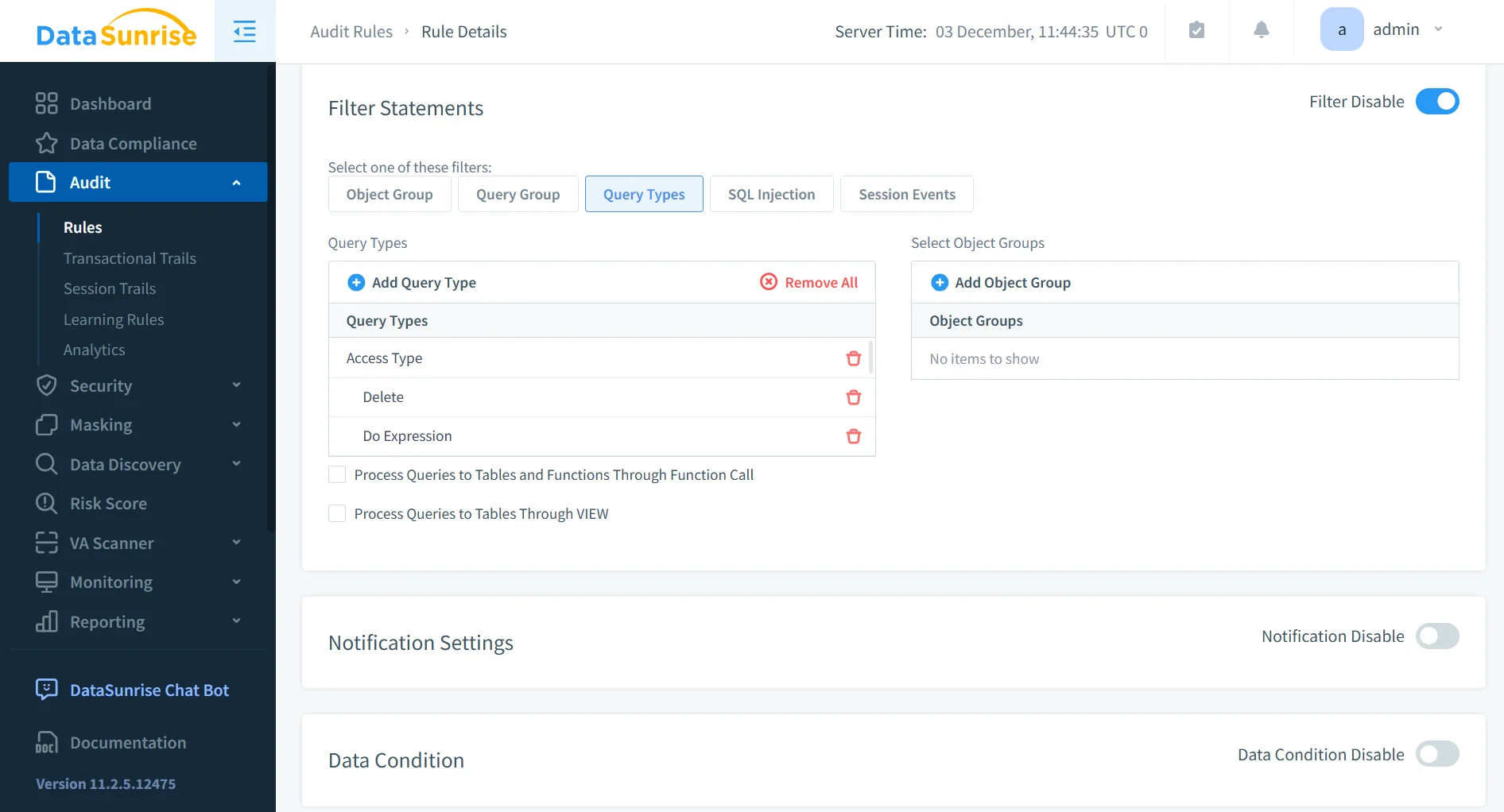
1. Centralized Audit Rules
DataSunrise offers fine-grained rule configuration enabling targeted auditing of specific tables, operations, schema areas, and sensitive datasets—fully compatible with DataSunrise’s Audit Guide.
- Enables isolating activity on specific schemas.
- Helps limit audit scope to high-risk operations.
- Reduces noise by filtering non-critical queries.
2. Real-Time Monitoring & Event Correlation
All activities are correlated in real time, offering deep traceability similar to capabilities described in the Behavior Analytics engine.
- Tracks all query flows across multiple nodes.
- Connects user identity to execution behavior.
- Highlights spikes or unusual traffic patterns.
3. Enriched Data Activity History
Enhanced record structures include row-impact metrics, object mapping, masked/unmasked indicators, and session-behavior sequences—extending ClickHouse’s native audit signals in the same way covered in DataSunrise’s Database Activity History.
- Shows exactly how much data each query accessed.
- Highlights access to sensitive datasets.
- Reveals long-running or abnormal query sequences.
4. Intelligent Security Controls
Integrated SQL injection detection, privilege misuse identification, and anomaly detection (UEBA) convert logs into active security monitoring—similar to the adaptive controls described in DataSunrise’s dedicated Security Rules.
- Detects unsafe or malicious SQL patterns.
- Flags access outside of normal behavior baselines.
- Generates alerts for critical threat events.
6. Automated Compliance Reporting
DataSunrise automatically compiles reports aligned with GDPR, HIPAA, PCI DSS, and SOX, following the structured audit evidence generation detailed in the Compliance Manager documentation.
- Creates auditor-ready reports instantly.
- Tracks all violations and exceptions.
- Reduces manual compliance workload dramatically.
Business Impact
| Benefit | Description |
|---|---|
| 60–80% audit effort reduction | Centralized visibility eliminates manual log correlation and speeds up investigations. |
| Full compliance alignment | Suitable for GDPR, HIPAA, PCI DSS, SOX, and internal governance. |
| Improved insider threat detection | Behavioral analytics and correlation expose suspicious or abnormal activity. |
| Cross-platform visibility across 40+ systems | Unified auditing across databases, warehouses, and cloud platforms. |
| Lower operational overhead | Automation removes repetitive and error-prone manual work. |
Conclusion
ClickHouse provides valuable observability but lacks centralized governance essential for enterprise compliance and forensic analysis. DataSunrise fills this gap by enriching audit visibility, correlating events across nodes, adding security intelligence, and automating compliance workflows. The result is a fully auditable, controlled, and compliant ClickHouse deployment that aligns with modern data-security disciplines such as Data Protection and Data Management.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now