Effortless Data Compliance for Amazon OpenSearch
Effortless data compliance for Amazon OpenSearch sounds like marketing fluff—until you realize how quickly OpenSearch turns into a regulated data store. Teams start with log analytics, observability dashboards, or security search. Then OpenSearch quietly becomes the central collector of authentication events, customer activity trails, request payload fragments, and operational metadata. If any of that includes personal or regulated information, compliance requirements apply the same way they would for a database.
AWS provides a managed platform and baseline security features for Amazon OpenSearch Service, but compliance responsibility stays with the organization operating the data. “Effortless” does not mean “no work.” It means replacing manual, error-prone processes with automated discovery, scoped policies, query-level protection, and audit-ready reporting—so compliance keeps working even when indices, pipelines, and teams change.
Why OpenSearch Falls Under Compliance Scope
OpenSearch is often treated as “just logs,” but modern logs are not harmless. They commonly contain direct identifiers, quasi-identifiers, and sensitive business context. In real deployments, OpenSearch indices frequently include:
- Emails, names, phone numbers, and IP addresses
- Customer IDs, device IDs, session IDs, and account references
- Support and incident data with personal or confidential details
- Security telemetry tied to individuals or systems
Once sensitive content is indexed, your controls must align with data compliance regulations and an auditable governance program. The first practical step is being able to reliably identify PII and other regulated patterns across OpenSearch—not just in one “sensitive” index, but everywhere it can appear.
What “Effortless” Compliance Actually Means
Effortless compliance is not a single checkbox inside OpenSearch. It is a workflow that runs continuously and produces evidence automatically. For OpenSearch, that workflow usually includes:
- Visibility: automated data discovery to find sensitive values in fields and payloads
- Scope: governance controls applied to the right objects (not the entire cluster by default)
- Control: centralized access controls with RBAC
- Protection:
- Proof:
DataSunrise supports these layers through a unified compliance platform that works across OpenSearch deployments. Instead of stitching together discovery scripts, access reviews, and reporting exports, you operate one set of policies and evidence pipelines via Compliance Manager.
Step 1: Discover Sensitive Data Before You Try to Govern It
Compliance fails when the team cannot answer a basic question: “What regulated data exists in our OpenSearch indices?” OpenSearch documents are semi-structured and often include unstructured payloads, so manual reviews miss too much.
DataSunrise discovery automates identification of sensitive content and reduces reliance on assumptions. Discovery results also provide the foundation for scoping policies, assigning ownership, and defining what needs masking or auditing. This discovery-first workflow is the fastest way to make compliance feel “effortless” instead of reactive.
Step 2: Scope Compliance to the Right OpenSearch Objects
A common reason compliance programs break dashboards is overreach—applying strict controls everywhere without scoping. OpenSearch clusters may contain both low-risk telemetry and high-risk user activity data. Governance works best when you explicitly select the objects that require compliance controls and exclude irrelevant datasets.
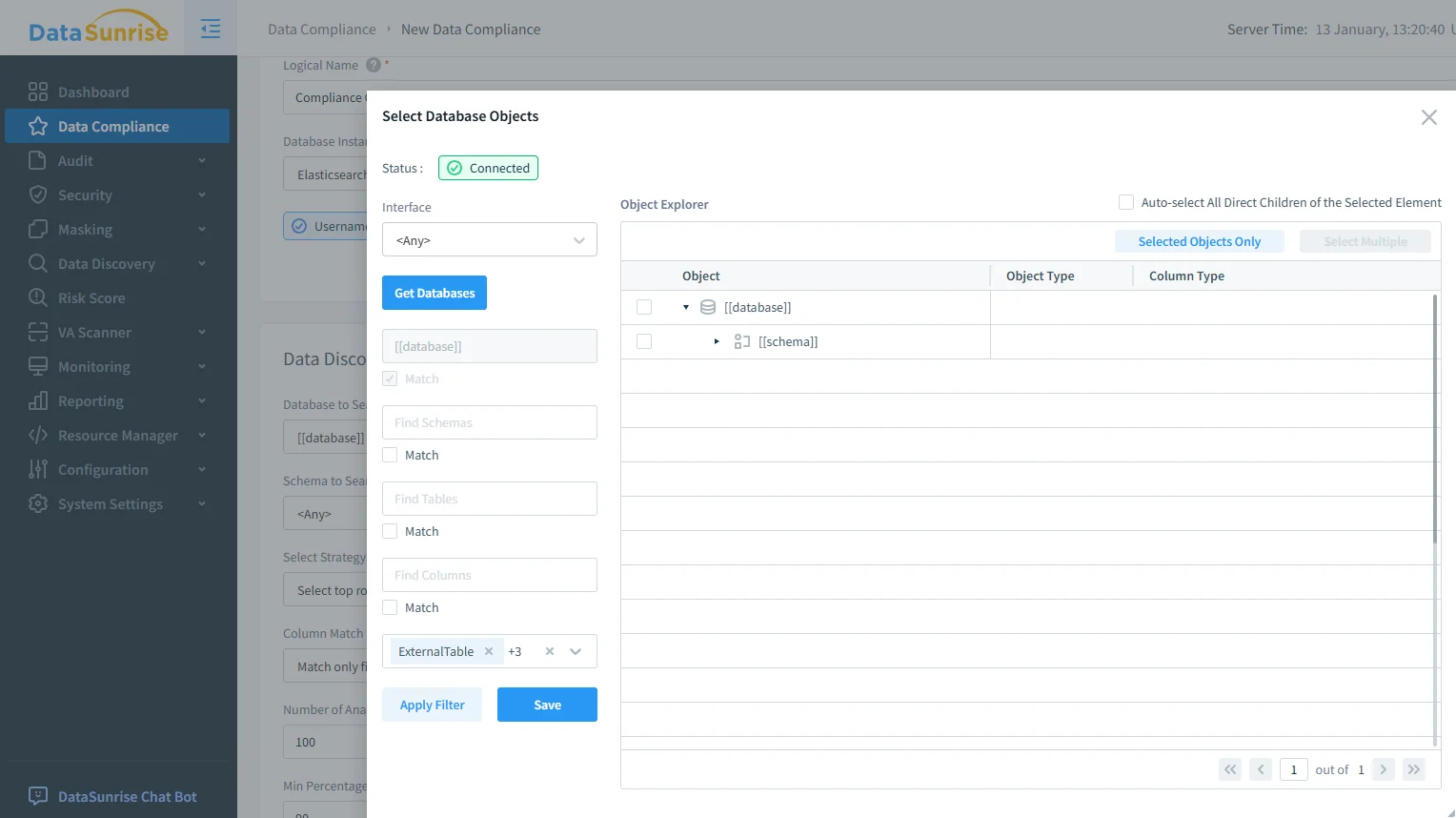
This approach reduces noise, keeps operational analytics usable, and gives you a defensible compliance boundary. It also helps enforce the principle of least privilege by limiting governed access to what each role actually needs.
Step 3: Enforce Policies with Deterministic Compliance Rules
Once scope is defined, compliance becomes a policy problem. You need rules that specify when to audit, when to mask, and when to block or alert. DataSunrise policies enable consistent enforcement and reduce the “snowflake configuration” problem where every OpenSearch environment behaves differently.
When multiple rules can match the same activity, enforcement must remain predictable. Using rules priority, organizations can control evaluation order and ensure outcomes remain consistent across teams, indices, and environments.
Defining OpenSearch compliance rules in DataSunrise: policy-driven enforcement supports auditing, protection, and compliance reporting.
Step 4: Capture Audit-Ready Evidence Automatically
Compliance is not only about enforcement—it is also about proof. Auditors and security teams need to reconstruct activity reliably: who accessed what, when, and under which policy.
DataSunrise provides centralized evidence collection through Data Audit, detailed audit logs, and immutable audit trails. For ongoing oversight, database activity monitoring helps detect risky patterns (abnormal query spikes, unusual access paths, repeated sensitive lookups) before they become incidents.
As a baseline reference for platform-native logging, AWS documents OpenSearch audit logging here: Amazon OpenSearch audit logs. Native logs can be useful, but centralized evidence is typically easier to defend during audits and investigations.
Step 5: Reduce Exposure with Masking and Safe Data Practices
Even when access is authorized, raw sensitive values are not always necessary. Exposure reduction is one of the most practical ways to make compliance less painful while improving security outcomes.
DataSunrise supports both dynamic data masking (query-time redaction) and static data masking (safe copies for lower environments). When teams need realistic datasets for analytics or testing without real identifiers, synthetic data generation provides a compliance-safe alternative.
Step 6: Automate Reporting and Keep Compliance Running
Effortless compliance requires automation not only for enforcement but also for reporting. Auditors do not want screenshots; they want consistent evidence packages that map controls to outcomes.
DataSunrise supports evidence generation through report generation and automated compliance reporting. This enables repeatable reporting aligned with frameworks such as GDPR compliance, HIPAA compliance, PCI DSS compliance, and SOX compliance.
To prevent drift as new indices and pipelines appear, pair reporting with continuous data protection practices and validate posture using vulnerability assessment. For active prevention against abusive access patterns, add a database firewall as part of your governance strategy.
Compliance Outcomes at a Glance
| Compliance pain point | What teams struggle with in OpenSearch | What “effortless” looks like |
|---|---|---|
| Sensitive data visibility | PII appears in unexpected fields and payloads | Automated discovery and living inventory |
| Access governance | Broad roles granted to avoid breaking dashboards | Scoped policies and least-privilege enforcement |
| Audit evidence | Logs are fragmented across systems and teams | Centralized audit trails and consistent reporting |
| Exposure reduction | Authorized users still see too much raw data | Masking and safe data practices by default |
Effortless compliance is a workflow, not a feature: automate discovery, scope policies tightly, enforce least privilege, and generate audit evidence on a schedule—before an audit forces it.
Do not treat OpenSearch as “safe” because it is not a transactional database. If secrets or identifiers are indexed and searchable, you have created a fast exfiltration path. Enforce masking, auditing, and scoped access before it becomes an incident.
Conclusion: Making OpenSearch Compliance Defensible Without Friction
Effortless data compliance for Amazon OpenSearch is achievable when compliance is engineered as an operational control plane: discover sensitive data continuously, scope governance precisely, enforce policies deterministically, reduce exposure with masking, and produce audit-ready evidence automatically. This approach keeps OpenSearch usable for analytics while making compliance measurable and defensible.
To explore platform capabilities and deployment options, review the DataSunrise overview and available deployment modes, then start with Download or request a guided Demo.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now