ScyllaDB Data Governance
ScyllaDB is a high-performance NoSQL database designed for scale and low latency. It powers mission-critical applications in industries such as finance, e-commerce, and telecommunications. With its distributed nature, ScyllaDB provides resilience and performance, but ensuring proper data governance remains a challenge.
Organizations face strict compliance requirements like GDPR, HIPAA, PCI DSS, and SOX. Meeting these demands requires visibility, access control, sensitive data protection, and audit-ready reporting. While ScyllaDB offers basic tools, advanced governance platforms like DataSunrise can extend capabilities with automation and centralized management.
Importance of Data Governance
Data governance is more than a compliance requirement — it is a foundation for security, accountability, and operational efficiency. In distributed systems like ScyllaDB, where data is replicated across clusters and regions, governance ensures:
- Consistency: Unified policies across all environments reduce risks of data silos and unmonitored access.
- Accountability: Clear tracking of who accessed what data, when, and why enables effective auditing.
- Security: Strong governance frameworks enforce access controls and data protection, limiting unauthorized exposure.
- Compliance: Alignment with standards such as GDPR, HIPAA, and PCI DSS avoids penalties and strengthens trust.
- Operational Clarity: Well-defined governance prevents compliance drift when new users, roles, or keyspaces are introduced.
Without effective governance, organizations risk data breaches, regulatory fines, and reputational damage — challenges amplified in fast-scaling platforms like ScyllaDB.
Native ScyllaDB Governance Features
ScyllaDB inherits its security model from Apache Cassandra. Its governance foundation relies on:
1. Authentication and Role-Based Access Control (RBAC)
ScyllaDB provides internal authentication with role management. You can create users and assign roles with privileges at the keyspace and table level. This ensures only authorized accounts can perform read or write operations.
-- Create a new role with login capability
CREATE ROLE compliance_user
WITH LOGIN = true
AND PASSWORD = 'StrongPass123!';
-- Grant read-only access to a sensitive keyspace
GRANT SELECT ON KEYSPACE sensitive_data TO compliance_user;
For stronger security, administrators can combine RBAC with custom roles and role inheritance, creating layered access models:
-- Create a base role with read-only privileges
CREATE ROLE readonly_role;
-- Assign privileges
GRANT SELECT ON KEYSPACE sensitive_data TO readonly_role;
-- Attach role to user
GRANT readonly_role TO compliance_user;
With RBAC, organizations can enforce the principle of least privilege, ensuring that users only have the minimum rights needed for their responsibilities.
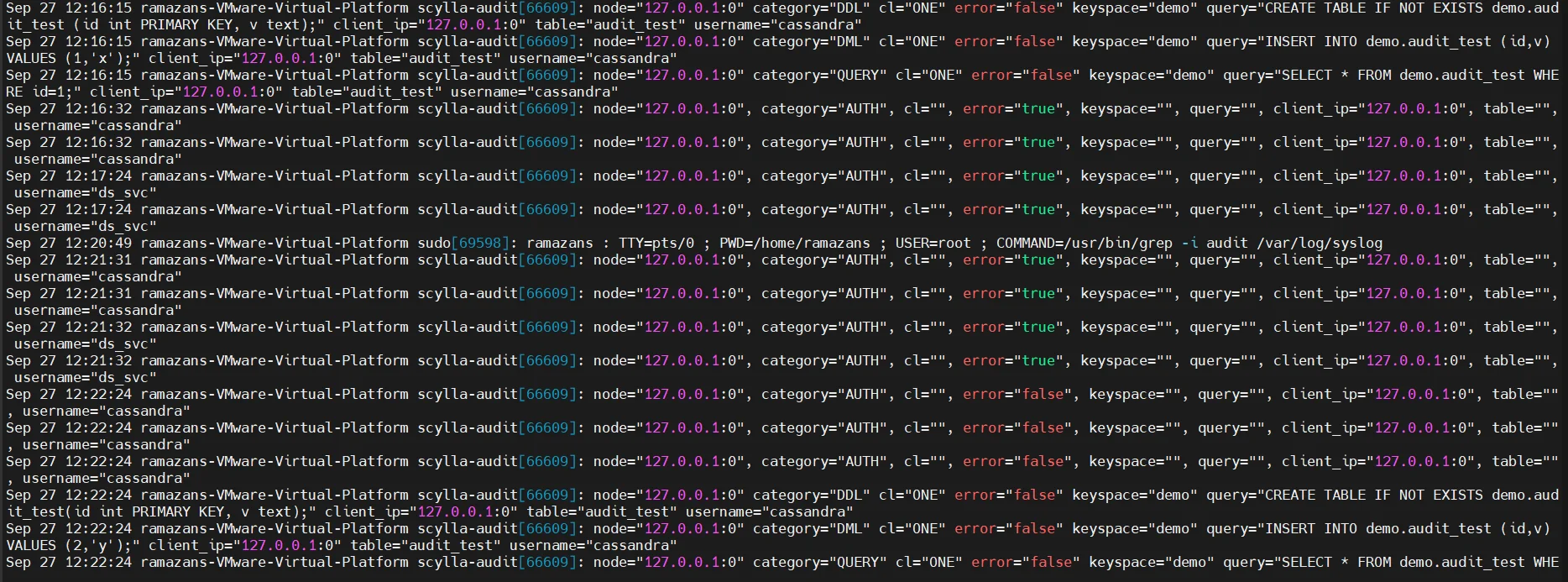
2. Auditing and Logging
ScyllaDB supports audit logging, which records login attempts, queries, and schema modifications. This provides visibility into who is doing what inside the database. Administrators can extend audit functionality by integrating ScyllaDB logs with external monitoring and alerting platforms, ensuring consistent visibility across distributed environments.
- Integration with SIEM platforms (such as Splunk or ELK) allows centralized log correlation.
- Alerts can be configured for suspicious activity, such as repeated failed logins or schema changes.
- Audit data supports compliance reviews, enabling organizations to demonstrate adherence to GDPR, HIPAA, PCI DSS, and SOX.
3. Encryption and Security
ScyllaDB supports TLS encryption for client-server and inter-node communication, preventing data exposure during transit. At-rest protection can be achieved with database encryption.
TLS configuration example in scylla.yaml:
client_encryption_options:
enabled: true
optional: false
keystore: conf/.keystore
keystore_password: myStrongPass
server_encryption_options:
internode_encryption: all
keystore: conf/.server_keystore
keystore_password: AnotherPass
truststore: conf/.server_truststore
truststore_password: TrustPass
Encryption ensures that data packets cannot be intercepted between nodes or clients. However, encryption alone does not address governance aspects like:
- Monitoring user activity and changes.
- Automated data discovery of sensitive fields.
- Compliance reporting aligned with regulatory standards.
These require additional governance tools.
Enhanced ScyllaDB Data Governance with DataSunrise
While ScyllaDB’s native capabilities form a baseline, DataSunrise provides a comprehensive governance framework:
Centralized Activity Monitoring
Centralized monitoring enables administrators to capture and search activity across all ScyllaDB clusters from a single interface. Instead of manually collecting logs from individual nodes, DataSunrise aggregates them automatically. This unified view allows:
- Rapid reconstruction of user activity during security investigations.
- Long-term retention of logs for compliance audits.
- Seamless integration with SIEM systems for enterprise-wide visibility.
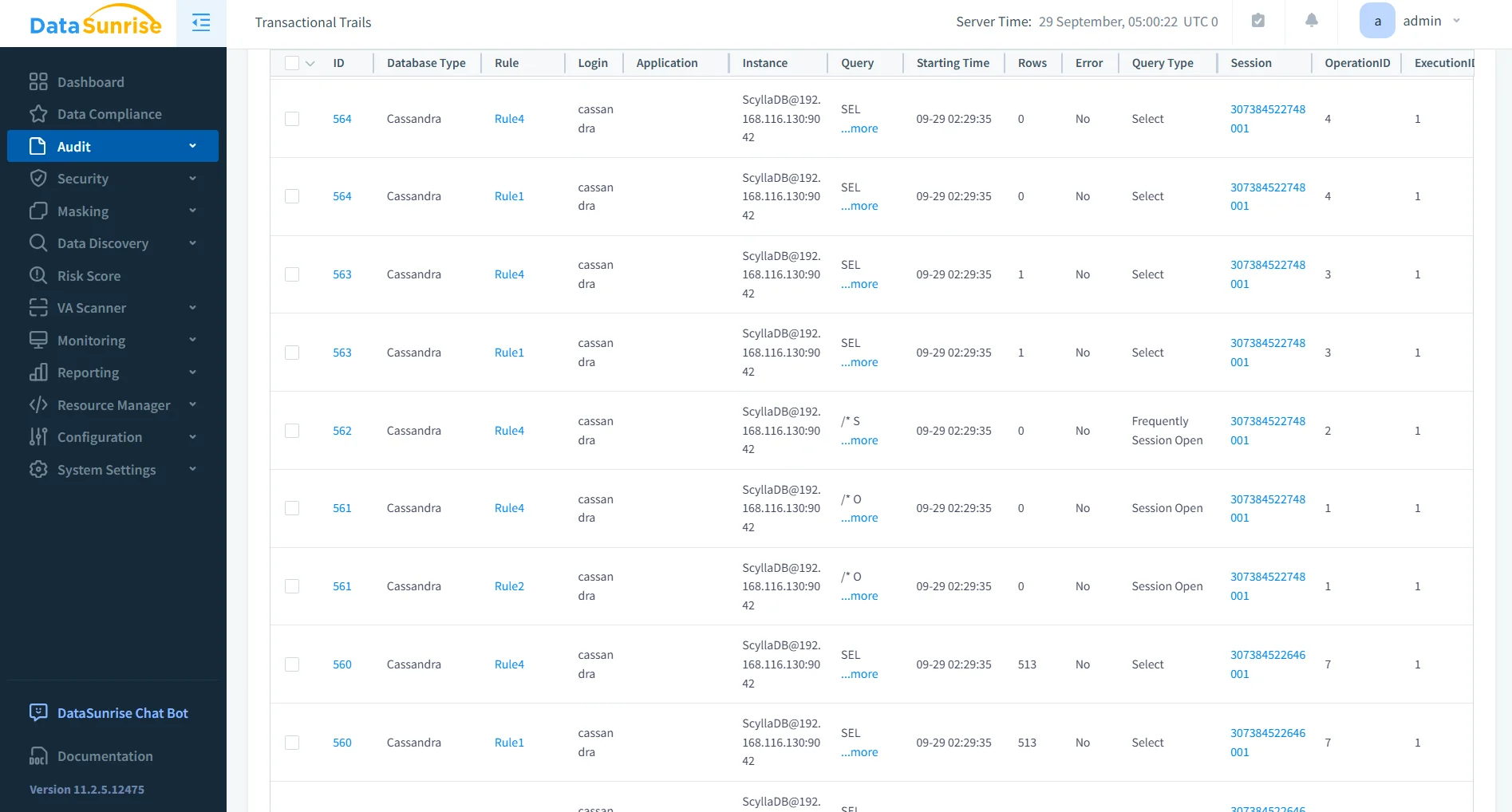
Granular Audit Rules
With flexible audit rules, DataSunrise allows governance policies to be tailored with precision. Administrators can define rules to monitor:
- Access to specific keyspaces, tables, or even sensitive columns.
- Privileged user actions such as schema modifications.
- Certain SQL operations (INSERT, UPDATE, DELETE) critical to compliance.
This ensures that audit trails are not overloaded with unnecessary noise but remain sharply focused on compliance-sensitive operations.
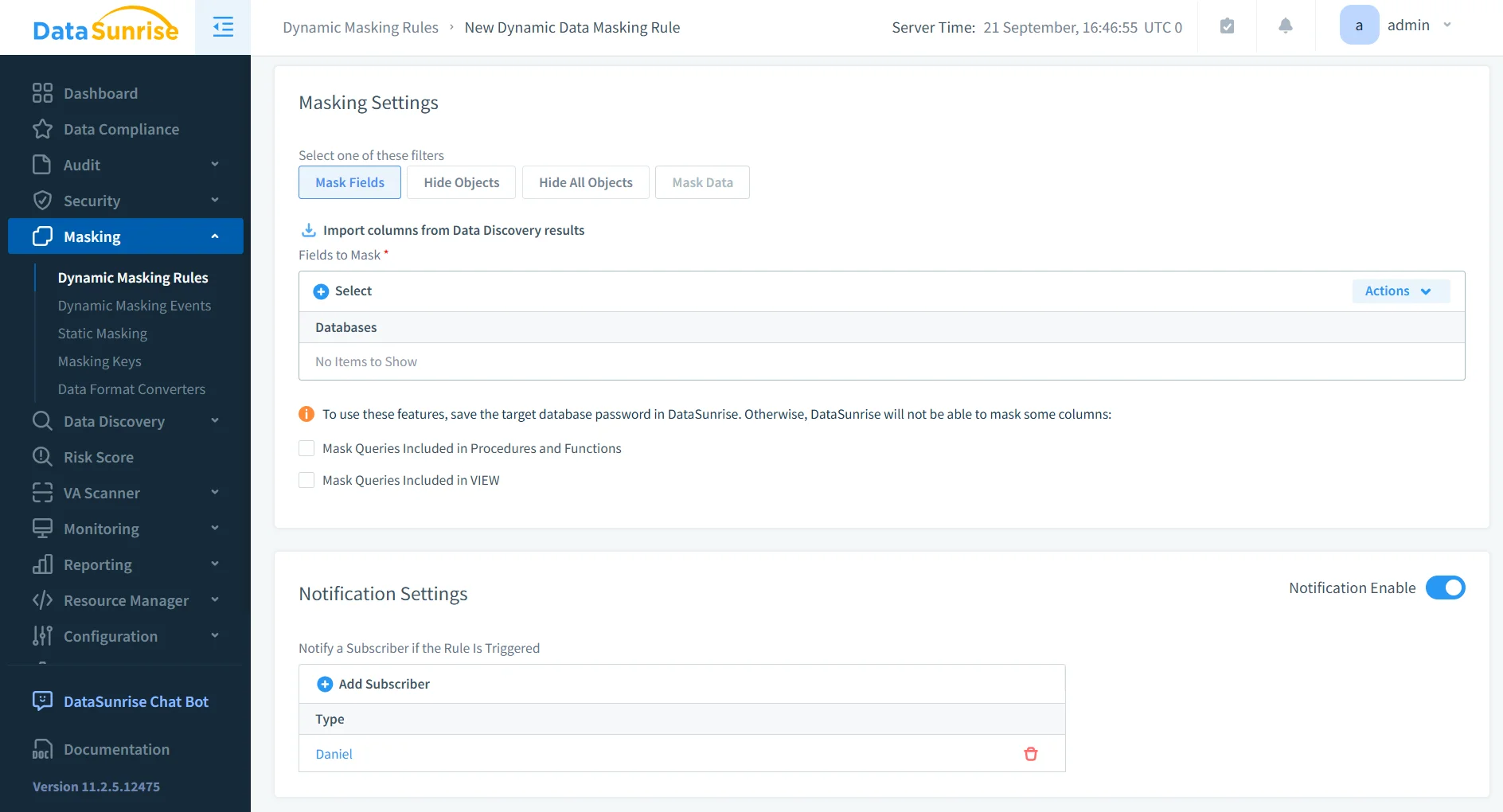
Dynamic Data Masking
Dynamic data masking protects sensitive data in real time. It prevents unauthorized users from seeing sensitive information while still allowing queries to run normally.
- Masks sensitive fields such as PII and PHI without altering underlying data.
- Adjusts masking dynamically based on user roles and access levels.
- Ensures compliance with privacy laws like GDPR and HIPAA by avoiding unnecessary data exposure.
Data Discovery
Data discovery automates the process of locating sensitive data across ScyllaDB schemas. DataSunrise employs pattern recognition, NLP, and OCR to identify PII, PHI, and financial records, even within semi-structured or unstructured data. Discovery tasks can be scheduled to:
- Continuously scan for new sensitive fields.
- Flag compliance gaps when new tables are created.
- Support reporting by mapping sensitive data locations across the cluster.
Automated Compliance Reporting
With automated compliance reporting, organizations can produce auditor-ready reports in one click. Reports can be scheduled daily, weekly, or monthly, ensuring evidence is always up to date. Features include:
- Predefined templates for GDPR, HIPAA, PCI DSS, and SOX.
- Export in PDF or HTML for easy submission to auditors.
- Historical compliance snapshots for long-term documentation.
This dramatically reduces the manual effort required to prepare for audits.
Database Firewall
The database firewall inspects incoming SQL queries before they reach ScyllaDB. Suspicious or non-compliant queries can be blocked in real time, preventing security incidents such as:
- SQL injection attempts.
- Mass export of sensitive records.
- Queries from unapproved applications or IP addresses.
By acting as a protective shield, the firewall reduces the risk of both insider and external threats.
User Behavior Analytics
User behavior analysis leverages machine learning to detect anomalies in database activity. It establishes a baseline of normal user behavior and flags deviations such as:
- A developer downloading thousands of records outside business hours.
- An administrator suddenly modifying sensitive tables.
- Suspicious access attempts from unusual locations.
This proactive detection capability helps prevent insider threats and data misuse before they escalate into breaches.
Business Benefits
| Benefit | Description |
|---|---|
| Regulatory Alignment | Meet international frameworks like GDPR, HIPAA, and PCI DSS without manual overhead. |
| Reduced Risk Exposure | Protect against both external threats and insider misuse. |
| Operational Efficiency | Automate repetitive tasks like log aggregation, report generation, and evidence preparation. |
| Trust and Transparency | Demonstrate accountability to auditors, customers, and partners. |
| Future-Ready Scalability | Support for over 40+ platforms ensures consistency across hybrid environments. |
Conclusion
ScyllaDB’s distributed design makes it an attractive choice for performance-driven workloads. However, governance requirements extend beyond native capabilities. By integrating DataSunrise, organizations gain centralized monitoring, automated compliance, dynamic masking, and proactive threat protection.
This combination transforms ScyllaDB into a compliance-ready platform that balances speed, scale, and regulatory accountability.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now