
What Is IBM Netezza Audit Trail

The question “What Is IBM Netezza Audit Trail” has become far more than a definition exercise. In an era of ubiquitous AI assistants generating SQL on behalf of analysts, an audit trail is the only way to prove who really touched sensitive data, when, and why. This article (≈950 words) explores the native capabilities of IBM Netezza, shows how DataSunrise augments them with real‑time audit, dynamic masking, and discovery, and demonstrates how generative AI (GenAI) can add an additional layer of intelligent security.
The Business Imperative for Trustworthy Audit Trails
Modern lake‑house architectures deliver petabyte performance, but every performance boost widens the blast‑radius of a breach. A well‑configured audit trail answers regulators’ first questions after an incident: Was personal data accessed? Did anyone tamper with logs? The IBM Netezza Audit Trail does this by capturing login attempts, DDL, DML, and context such as client IP or application name. Organizations running under GDPR, HIPAA, or PCI‑DSS rely on these records to demonstrate continuous compliance. When paired with technologies like role‑based access controls and continuous data protection, the audit trail becomes a living control rather than an after‑thought.
Native IBM Netezza Audit Trail Fundamentals
IBM engineers purposely decoupled auditing from query history to minimise overhead. Audit events are staged to dedicated tables (_V$_A$_AUDIT_EVENT and friends) and can be off‑loaded to a target appliance for long‑term retention (IBM docs). Key design points include:
- Category‑based policies. Login, admin, DDL, DML, security and object‑access categories can be turned on or off per user or group.
- Immutable staging. Once an event is written it cannot be modified by standard SQL, preserving evidentiary value.
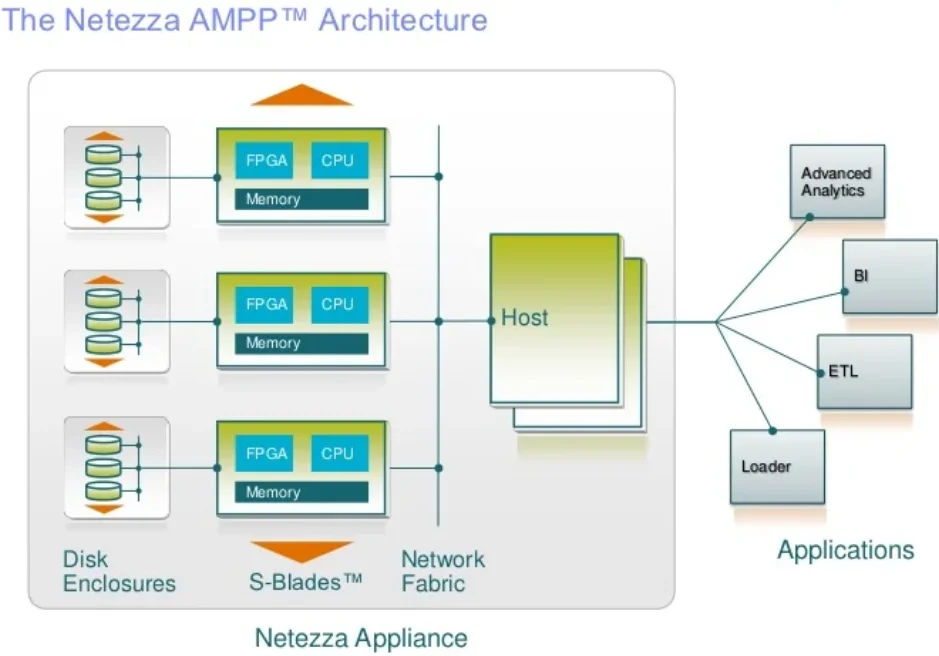
- Size safeguards. Administrators can set disk quotas; overflow halts new sessions, making mis‑configuration instantly visible.
Configuring Native Audit Logging in Minutes
The minimal path to a compliant trail is surprisingly short:
-- enable the audit engine\ nUPDATE SYSTEM SET AUDIT TRUE;\ n
-- create a reusable policy\ nCREATE AUDIT POLICY fulltrail
CATEGORIES (LOGIN, DDL, DML, OBJECT_ACCESS);\ n
-- attach to an application role\ nALTER GROUP marketing SET AUDIT fulltrail;\ n```
From this point, every qualifying event lands in NZ_AUDIT. Analysts can query it directly or stream to SIEM via nz_export. For more granular views, create views that JOIN the audit tables with _V_SYS_USER to enrich user metadata.
Tip: keep native retention short‑lived (e.g. seven days) and ship older records to a cheaper repository such as object storage, then catalog them in data activity history for searchability.
Why Stop There? Real‑Time Audit & Dynamic Masking with DataSunrise
Native auditing is robust, yet enterprises often need:
- Real‑time detection instead of periodic log scrapes;
- Dynamic data masking so production users see only what they should;
- Unified compliance reports across heterogeneous platforms.
DataSunrise Audit for IBM Netezza deploys transparently as a reverse proxy. Every packet is inspected before it reaches the appliance, letting you:
- Fire web‑hook or Slack alerts on rule violation (real‑time notifications);
- Apply dynamic data masking based on user, time or client address—no code changes;
- Run behavior analytics that profile normal query shapes and flag anomalies;
- Store compressed audit events for years without bloating the warehouse (audit storage best‑practices).
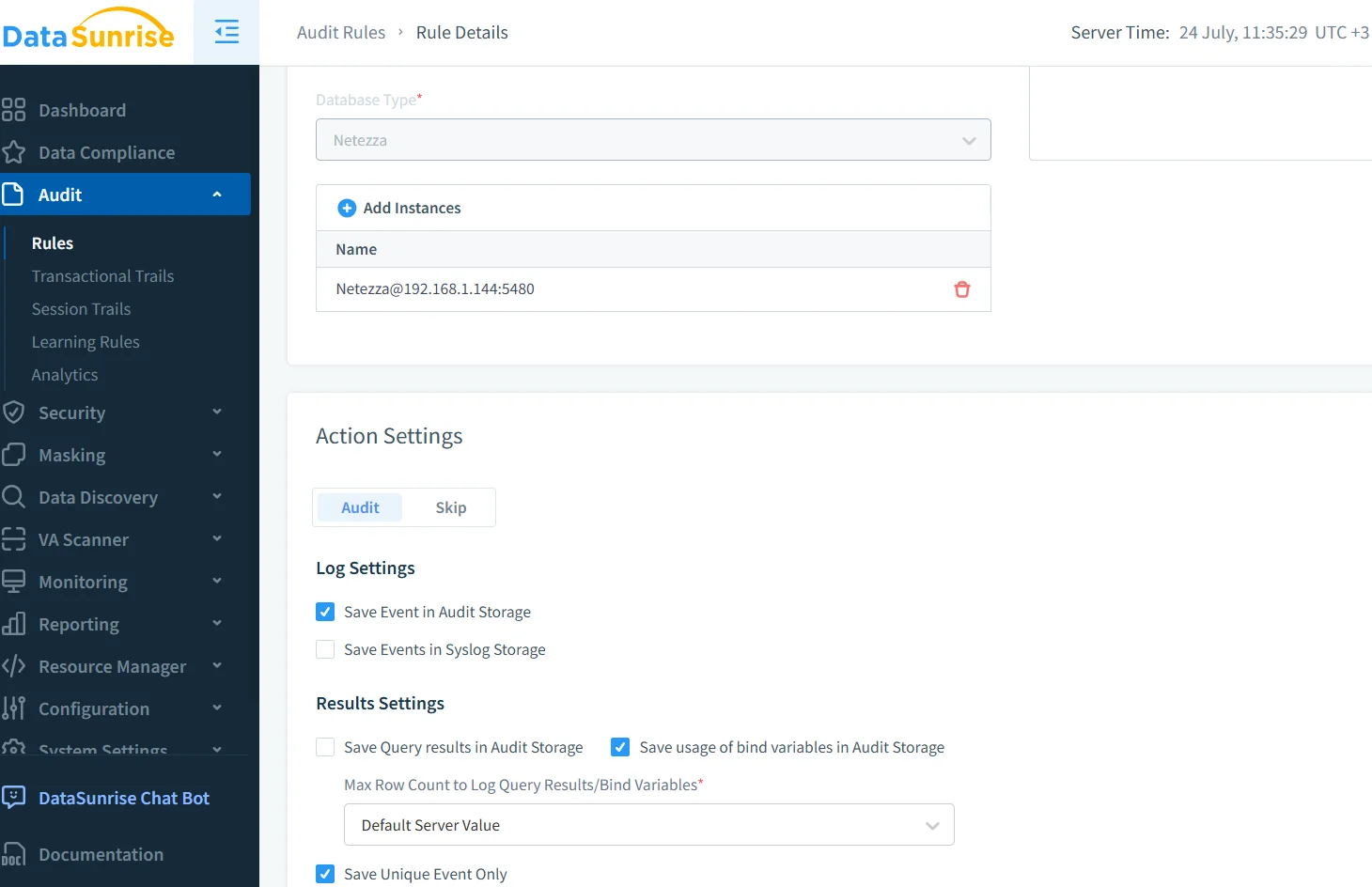
Set‑up is wizard‑driven. After pointing the tool to your Netezza host, choose Audit → New Rule and tick DDL, DML, Logon, Select. Behind the scenes DataSunrise generates a learning rule that auto‑tunes noise thresholds – see learning rules and audit.
GenAI: Turning Volumes of Audit Data into Actionable Insight
A raw log tells what happened; GenAI can propose why it happened and whether to trust it. Below is a simplified Python example that connects to DataSunrise’s REST API, streams fresh audit rows, and lets a local LLM summarise suspicious patterns:
import requests, json
from my_local_llm import chat # thin wrapper around Llama‑3‑instruct
rows = requests.get(
"https://datasunrise.local/api/audit" ,
headers={"Authorization": "Bearer $TOKEN"}
).json()
payload = """You are a security analyst. Classify each event as benign, risky or malicious.
Return JSON with id and verdict."""
decisions = chat(prompt=payload + json.dumps(rows[:100]))
for d in json.loads(decisions):
if d["verdict"] != "benign":
requests.post("https://pagerduty.com/api", json=d)
A similar flow can be built with SQL alone using model‑as‑a‑function support in Db2 Warehouse. The beauty is that GenAI reasons over the audit trail in near real time, catching iterative table‑scan prompts or brute‑force joins common to AI‑generated queries.
Compliance Landscape: Proving ‘Least‑Privilege’ at Scale
Auditors rarely read every row; they ask for narrative proof. With DataSunrise you can generate automated GDPR, HIPAA and PCI‑DSS sections (compliance manager). Each report cross‑references:
- user entitlements via access controls;
- masking policies against personally identifiable information;
- historical trends held in database activity monitoring.
Because the underlying IBM Netezza Audit Trail is immutable, GenAI summaries inherit the same chain of custody, satisfying regulators’ accuracy and integrity principles.
Putting It All Together – A Query‑Level Example
Suppose an AI assistant issues the following ad‑hoc request:
SELECT customer_id, card_number
FROM sales.payments
WHERE country = 'DE';
- Native trail records the SQL text and user.
- DataSunrise proxy masks
card_numberfor analysts while allowing an approved service account to see it in clear. - GenAI watch‑dog detects that the query returns more than 10 000 rows of PCI data outside business hours, assigns a risky verdict, and pushes a real‑time Slack alert.
At review time, an auditor can replay the entire decision tree, from originator through masking transform to AI verdict, proving both least‑privilege and continuous audit.
Final Thoughts
So, What Is IBM Netezza Audit Trail? It is the foundation for defensible analytics in a GenAI world. Configure the native engine for guaranteed capture, layer DataSunrise for real‑time intelligence, and invite GenAI to sift signals from noise. The result is an audit architecture that scales security, not bureaucracy.
For deeper dives explore the official IBM audit configuration guide and the DataSunrise overview to see deployment modes that match your network topology.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now