Amazon OpenSearch Data Compliance Automation
Amazon OpenSearch Data Compliance Automation is the practice of turning compliance from a manual, spreadsheet-driven scramble into a repeatable system: continuously discovering sensitive data in OpenSearch indices, enforcing access and masking policies, capturing audit-ready evidence, and generating reports automatically. If OpenSearch is used for log analytics, observability, SIEM workloads, or application search, it will eventually ingest identifiers, payload fragments, and operational records that fall under regulatory scope.
AWS provides the managed service and baseline security capabilities, but compliance responsibility still belongs to the organization operating the data. For service context, see Amazon OpenSearch Service. This article shows how to automate data compliance for OpenSearch using DataSunrise: discovery, policy enforcement, monitoring, masking, reporting, and alerting—at scale.
Why Amazon OpenSearch Data Compliance Automation Matters
OpenSearch compliance fails when it depends on people remembering to do things. Indices change, pipelines evolve, teams add new fields, and sensitive values appear in “temporary logs” that never get deleted. Manual compliance programs break in predictable ways:
- Unknown scope: you cannot prove where regulated data lives without continuous classification
- Overbroad access: roles get widened “just to fix a dashboard,” then never tightened
- Weak evidence: platform logs exist, but audit evidence is fragmented and inconsistent
- Slow audits: teams spend days stitching together what should be one report
Automation is how you keep governance aligned with data compliance regulations and enforce expectations tied to GDPR, HIPAA technical safeguards, PCI DSS, and financial accountability controls like SOX compliance.
Automation Blueprint: What to Automate in OpenSearch Compliance
A practical Amazon OpenSearch Data Compliance Automation program usually includes these five automated loops:
| Automation loop | What it does | DataSunrise capability |
|---|---|---|
| Discovery | Find sensitive data in indices and fields continuously | Data Discovery |
| Policy enforcement | Apply controls consistently to in-scope objects | Compliance Manager |
| Audit evidence | Record who did what, when, and under which policy | Audit Logs |
| Exposure reduction | Prevent raw sensitive values from being returned to non-privileged users | Dynamic Data Masking |
| Reporting + response | Generate reports and trigger alerts automatically | Report Generation |
Step 1: Automate Sensitive Data Discovery in Amazon OpenSearch
Automation starts with scope. If you can’t continuously identify sensitive data in OpenSearch, every other “control” becomes a guess. DataSunrise discovery scans OpenSearch content to identify regulated elements such as Personally Identifiable Information (PII) and other high-risk patterns embedded in structured fields or unstructured payloads.
Discovery output becomes your living compliance inventory: which indices are in scope, which fields are sensitive, and which teams own remediation. This is also the easiest way to prevent “new index drift,” where compliance scope quietly becomes outdated.
Step 2: Automate Scope Selection and Compliance Tasks
Once discovery identifies sensitive areas, automate enforcement by scoping compliance tasks to the right OpenSearch objects. Scoping prevents the classic mistake of applying strict controls everywhere and breaking operational dashboards. It also supports clean ownership: security defines baseline policies, data owners validate scope, and platform teams implement enforcement.
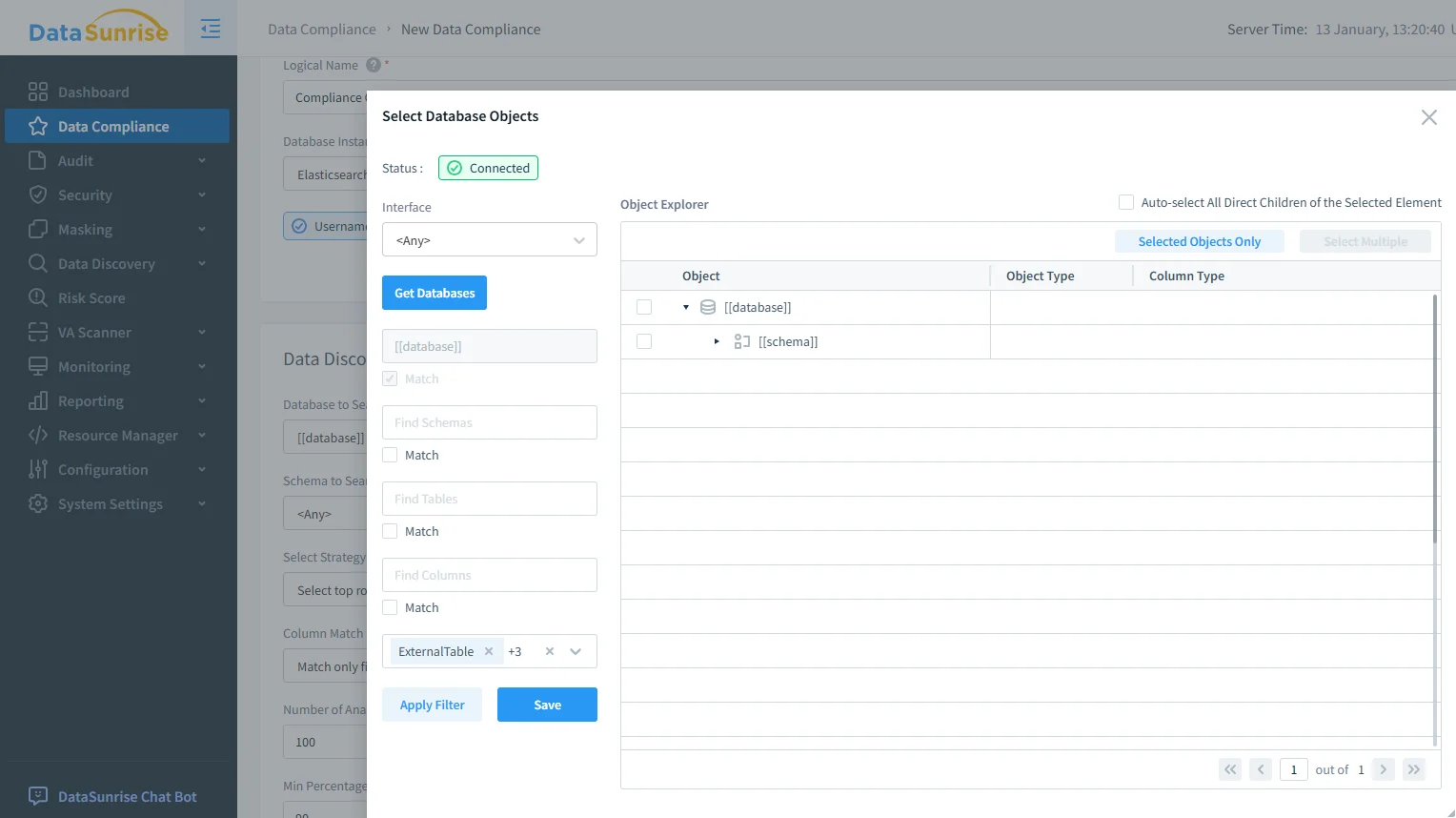
Defining compliance scope and discovery parameters for Amazon OpenSearch in DataSunrise (targets, objects, and report generation options).
At this stage, align access boundaries with structured access controls and RBAC so your automation doesn’t rely on “who has the password.” If multiple policies might match the same activity, define deterministic outcomes with rules priority to avoid enforcement gaps.
Step 3: Automate Policy Enforcement and Evidence Collection
Policy automation is where compliance stops being aspirational and becomes enforceable. DataSunrise centralizes governance with Compliance Manager automation, enabling repeatable controls across environments without manual reconfiguration for every new OpenSearch domain.
Automating compliance rules for OpenSearch: policy definition that drives auditing, enforcement, and reporting.
Evidence collection should be built in by default. DataSunrise supports centralized auditing with Data Audit, continuous oversight using Database Activity Monitoring, and defensible traceability via audit trails. This combination produces audit-ready proof rather than “we think access was limited.”
AWS also documents native service-level audit logging here: Amazon OpenSearch audit logs. Use that baseline, but don’t fragment evidence across systems if your goal is fast audits and clean investigations.
Step 4: Automate Exposure Reduction With Masking and Preventive Controls
Compliance is not only about whether a query is allowed—it’s about what the query returns. Many OpenSearch users need search and aggregations, not raw identifiers. Automate exposure reduction by applying static data masking for safer downstream copies and dynamic masking at query time. This directly lowers breach impact and reduces accidental disclosure risk.
For proactive defense, enforce risk controls such as a database firewall and verify configurations continuously using vulnerability assessment. Combine this with user behavior analysis to detect anomalous querying patterns that often indicate scraping or credential misuse.
Step 5: Automate Reporting, Alerts, and Continuous Protection
Compliance automation must produce outputs that auditors and security teams can use immediately. DataSunrise automates evidence packaging through standardized reporting, making it easier to demonstrate ongoing compliance without rebuilding the audit story every quarter.
Operational response matters too. Automate notifications with Slack notifications and Microsoft Teams notifications so policy violations are treated as incidents, not future surprises.
Finally, keep controls resilient by aligning compliance automation with continuous data protection practices. Automation is only valuable if it keeps running when your environment changes.
Automate compliance like you automate deployments: discovery on a schedule, policies applied by scope, auditing always-on, and reports generated routinely. If compliance depends on memory, it will fail.
Do not assume OpenSearch is “safe” because it’s not a transactional database. If tokens, secrets, or identifiers are indexed into searchable documents, you’ve created a high-speed exfiltration engine. Prevent this with discovery, masking, and strict access boundaries.
Conclusion: Make Amazon OpenSearch Data Compliance Automation the Default
Amazon OpenSearch Data Compliance Automation is about replacing ad hoc controls with repeatable enforcement: discover sensitive data, scope governance precisely, enforce policies, collect audit-ready evidence, reduce exposure, and generate reports automatically. DataSunrise provides a unified platform for this workflow so OpenSearch can remain fast and useful for analytics while staying defensible under audit pressure.
To explore implementation options, review DataSunrise overview and deployment modes, or start with Download and a guided Demo.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now