Amazon OpenSearch Data Governance
Amazon OpenSearch is the kind of platform that quietly becomes mission-critical: teams use it for application search, log analytics, observability, and security investigations. And because it ingests “everything,” it also ends up storing sensitive data—often unintentionally—inside documents, event payloads, and log messages. That’s where data governance stops being a policy deck and starts being an engineering requirement.
This guide explains how to build a practical, audit-friendly governance program for Amazon OpenSearch: discovery and classification, access governance, auditability, protection controls, and compliance reporting. AWS provides strong service-level controls and managed features (see Amazon OpenSearch Service), but governance is still your responsibility: you must prove what data exists, who touched it, how it was protected, and how you enforce rules continuously.
Why OpenSearch Needs a Governance Program
OpenSearch differs from traditional databases in one key way: it’s optimized for search and analytics, not clean schema boundaries. Indices evolve quickly, documents are semi-structured, and teams often ship raw payloads because “we might need it later.” That creates governance risk:
- Data sprawl: sensitive values duplicated across indices, environments, and pipelines
- Shadow data: unknown fields in unstructured payloads (headers, params, free-text logs)
- Overbroad access: roles designed for convenience rather than least privilege
- Weak audit evidence: logs exist, but not always in an audit-ready, consistent format
Once OpenSearch contains regulated data, governance must align with requirements outlined in data compliance regulations including GDPR, HIPAA, PCI DSS, and financial controls such as SOX compliance.
Governance Pillar 1: Discovery and Classification
You can’t govern what you can’t see. The first pillar of OpenSearch data governance is building a defensible inventory of sensitive data across indices and fields. That means scanning for regulated elements like Personally Identifiable Information (PII), tokens, account identifiers, and other high-risk patterns—not guessing based on index names.
DataSunrise automates this via Data Discovery, helping you classify content and generate an evidence-backed scope for governance rules. This reduces the classic governance failure mode: “We didn’t realize that index contained customer data.”
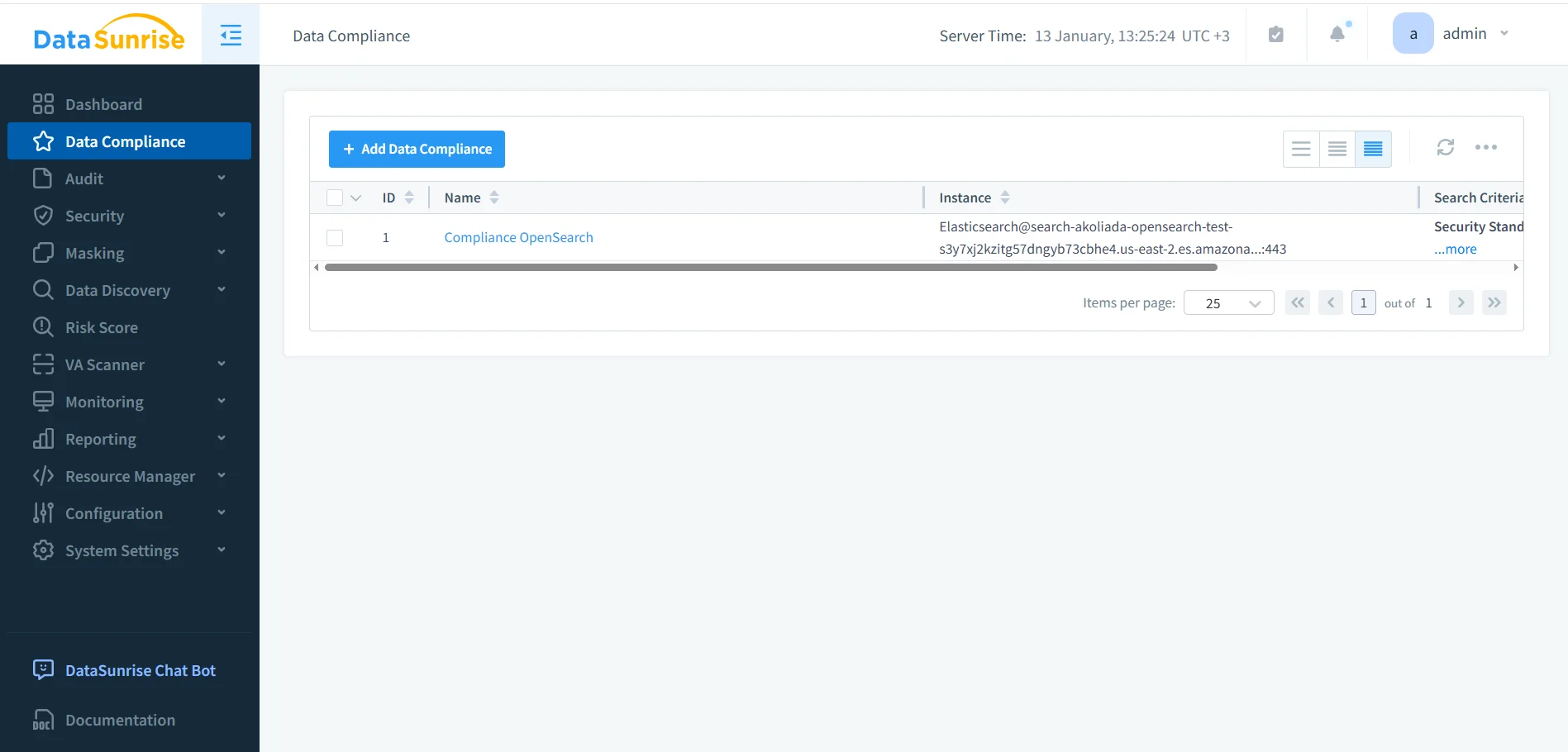
Governance Pillar 2: Access Governance and Least Privilege
Governance is meaningless if everyone can query everything. Strong access governance starts with least privilege and role clarity:
- Define user roles with role-based access control (RBAC)
- Enforce policy boundaries through centralized access controls
- Operationalize principles with the least privilege principle
When OpenSearch is used by many teams (security, SRE, product analytics, support), access should be scoped by purpose. Security analysts may need broad visibility; support teams often need partial visibility; developers usually need masked or synthetic data access. Treat OpenSearch like a shared regulated datastore, not a communal playground.
Governance Pillar 3: Auditability and Activity Evidence
Auditors don’t want “we have logs.” They want proof of traceability: who accessed what data, when, through which role, and whether controls were enforced. DataSunrise supports auditability by combining:
- Centralized data audit controls for governed environments
- Detailed audit logs suitable for investigations and reporting
- Immutable audit trails aligned with compliance evidence expectations
- Continuous database activity monitoring to detect abnormal access patterns
- Queryable database activity history and data activity history for forensics
If you’re implementing OpenSearch audit logging at the service level, AWS provides a baseline reference here: Amazon OpenSearch Service audit logs. Use it—but remember that governance requires consistent, audit-ready evidence across environments, not only platform-level events.
Governance Pillar 4: Data Protection Controls (Masking, Firewalling, and Encryption Discipline)
A mature governance program includes protection controls that reduce exposure even when access is legitimate. For OpenSearch, this often means:
- Dynamic data masking to reduce sensitive field exposure in real time
- Static data masking for safe data copies and lower environments
- Synthetic data generation when dev/test workloads should avoid real regulated data
- Database firewall controls to block abusive patterns and reduce exploitation paths
- Security baselines informed by the security guide and encryption expectations like database encryption
A practical mindset: governance is not only “who can access,” but also “what they can actually see.” Masking is especially effective in OpenSearch deployments used by mixed audiences (engineering + support + analytics) where raw sensitive values should be limited to a few roles.
Governance Pillar 5: Policy Automation and Compliance Workflows
Policies that aren’t enforced automatically are just documentation. With DataSunrise, governance policies can be formalized through Compliance Manager and scaled via automated compliance reporting. This helps standardize governance across OpenSearch domains, regions, and environments.
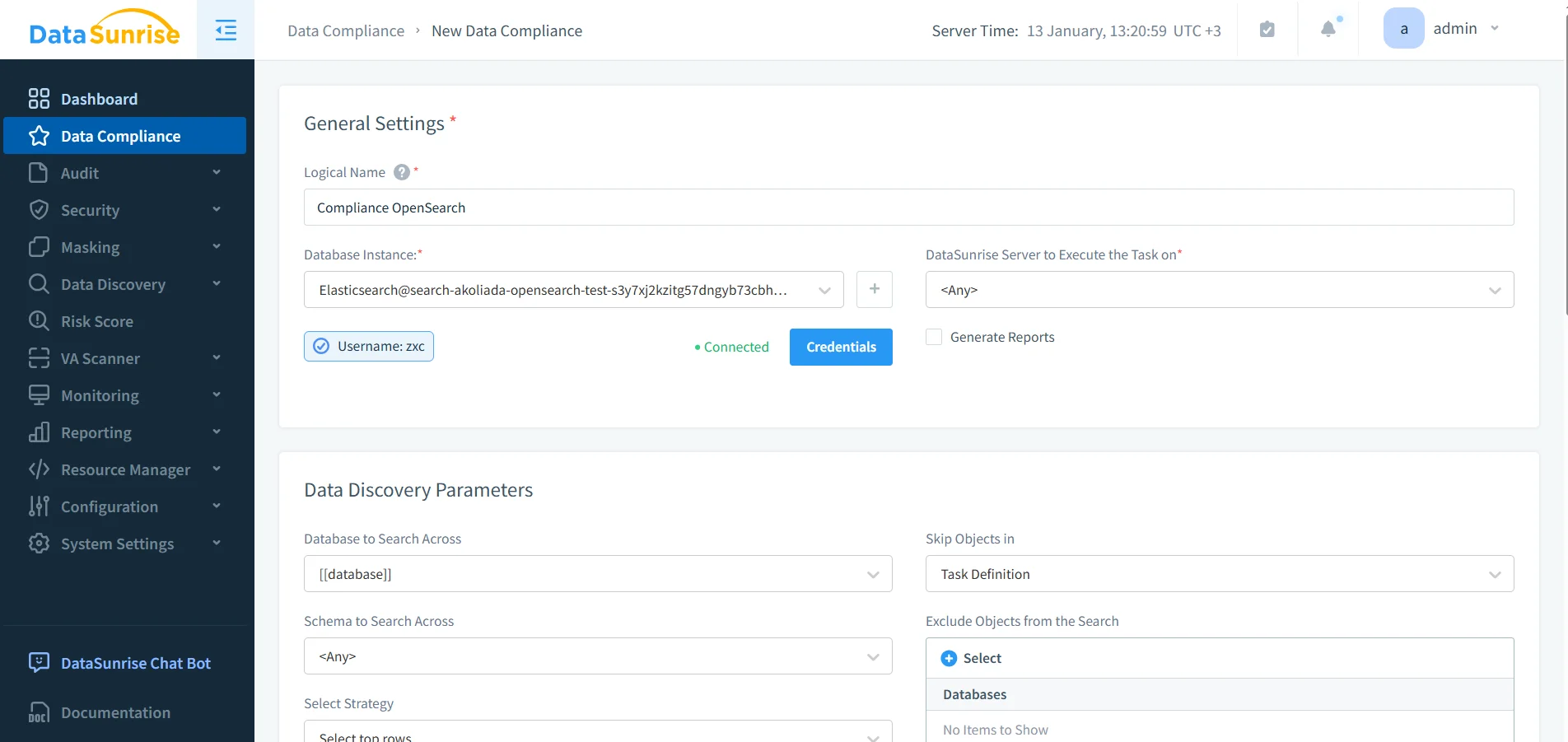
Governance policy creation: defining compliance rules for Amazon OpenSearch in DataSunrise.
Policies become operational when they produce repeatable outputs: alerts, audit evidence, and scheduled reports. That’s where governance becomes defensible under audit pressure.
Governance Control Matrix for Amazon OpenSearch
Use the table below as a practical governance blueprint: what to implement, what evidence you need, and which DataSunrise capabilities support the control.
| Governance Domain | What You Must Control in OpenSearch | Evidence You Need | DataSunrise Capability |
|---|---|---|---|
| Data Inventory | Identify sensitive fields across indices and payloads | Discovery scope, classification results, sensitivity mapping | Data Discovery |
| Access Governance | Restrict index/field visibility by role and business purpose | Role mapping, policy rules, access review artifacts | RBAC |
| Auditability | Record who queried what, when, and under which policy | Audit logs, trails, retention rules, investigation exports | Audit Logs |
| Exposure Reduction | Prevent raw sensitive values from appearing in results | Masking rules, test evidence, enforcement proof | Dynamic Masking |
| Operational Assurance | Detect misconfigurations and governance drift | Findings, remediation logs, risk trend documentation | Vulnerability Assessment |
Keeping Governance Current: Periodic Discovery and Scope Updates
OpenSearch environments change constantly: new pipelines, new index patterns, new fields. Governance must be continuous. Implement recurring discovery tasks and keep scope aligned with reality. This is especially important for “log” indices that suddenly include payload fragments, session IDs, or customer identifiers.
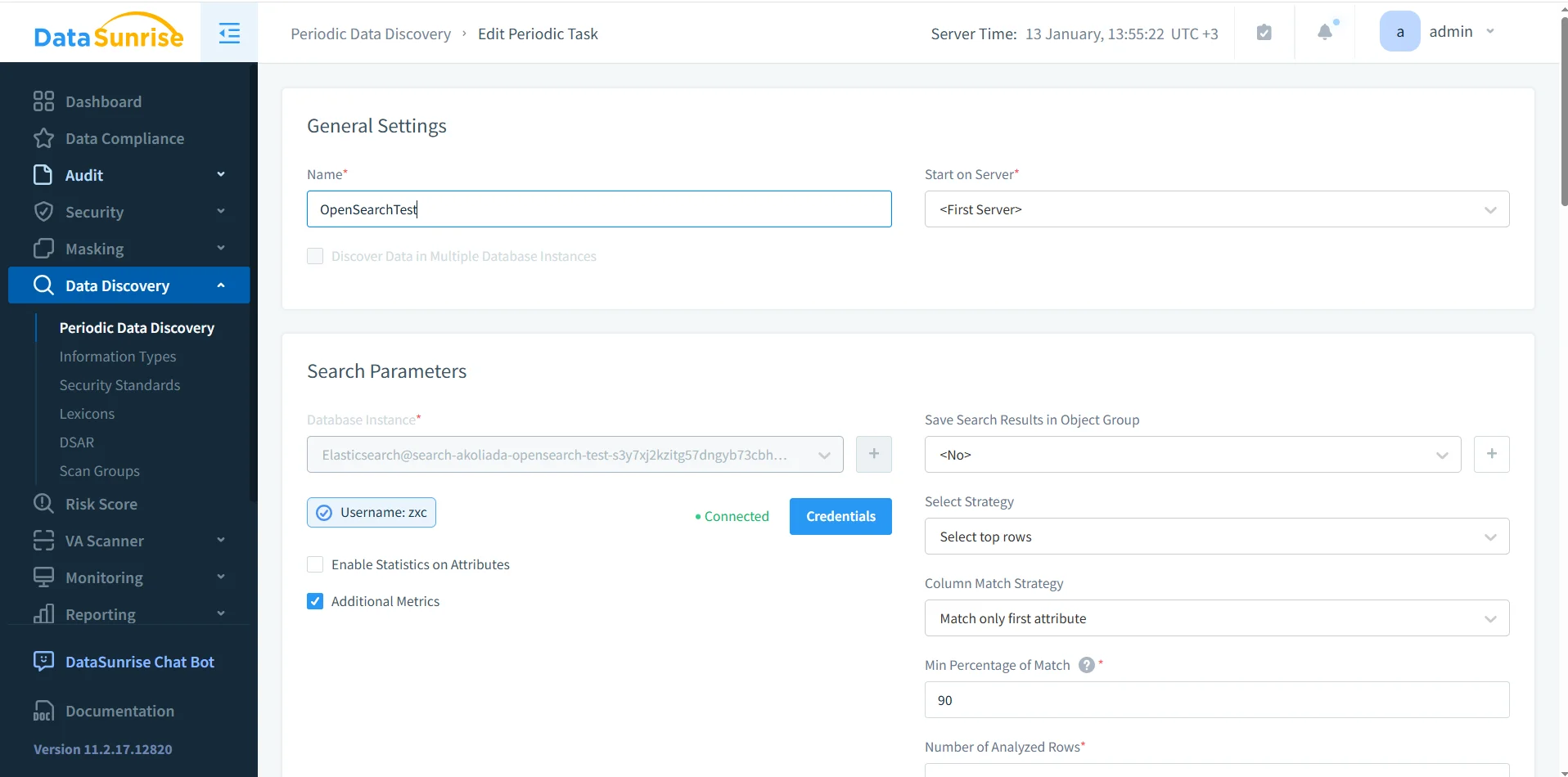
Periodic discovery tasks: continuous scanning prevents governance drift as OpenSearch indices evolve.
For durable governance operations, integrate discovery and monitoring with broader protection practices such as continuous data protection and standardized reports using report generation.
Governance in Practice: Scoping, Objects, and Operational Ownership
Governance also requires clean ownership boundaries: which indices are governed, which objects are excluded, and which teams own remediation. DataSunrise supports structured scoping so governance is precise rather than disruptive.
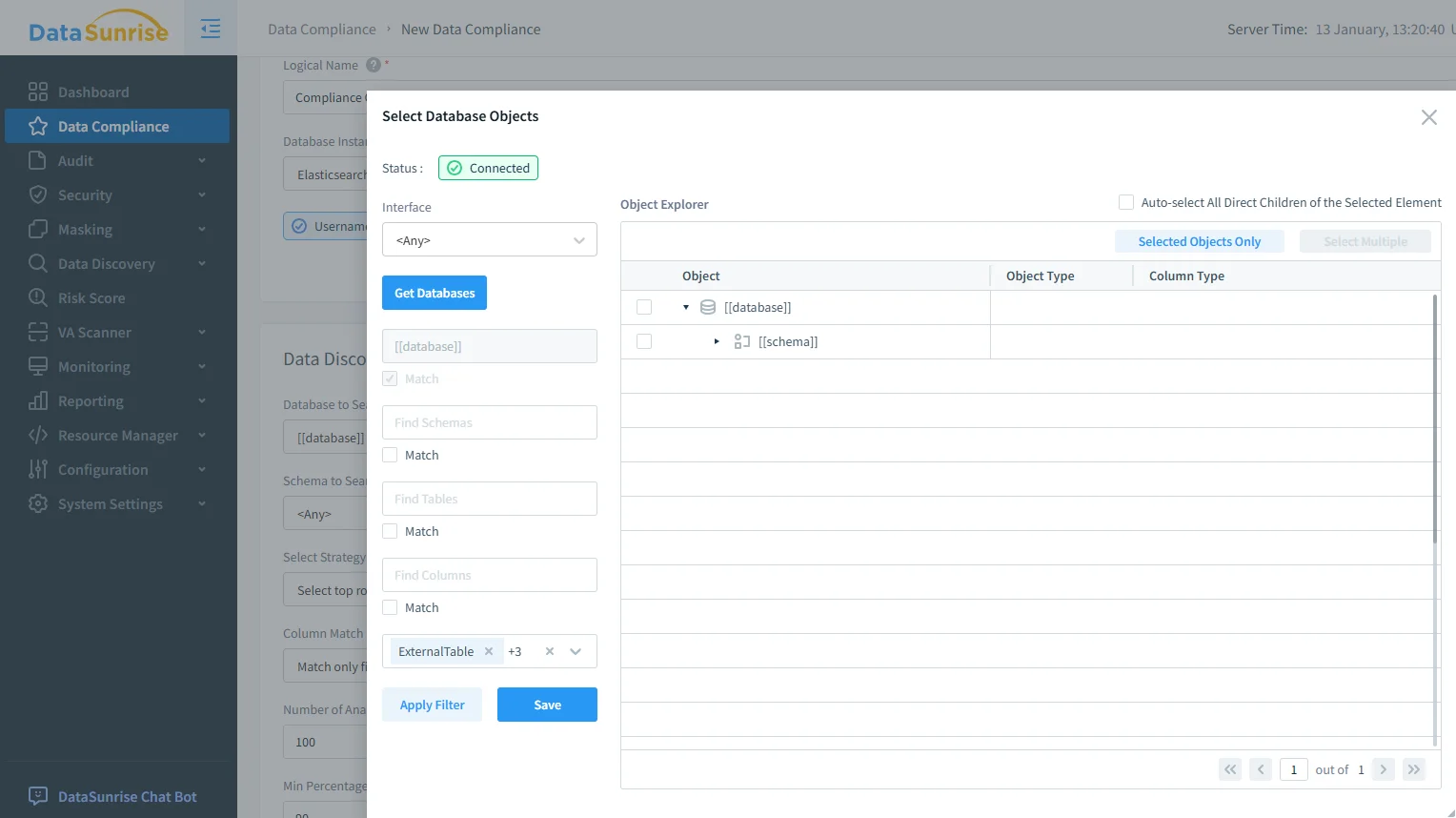
Scoping governance: selecting OpenSearch objects ensures policies apply to the right indices and fields.
From an operating model perspective, governance works best when:
- Security defines policy baselines and escalation paths
- Data owners validate scope and sensitivity categories
- Platform teams operationalize enforcement across environments
Do not treat OpenSearch as “just logs.” If an index contains user identifiers or payload data, regulators will treat it as a regulated data store. Compliance must be enforced at the query level, not after an incident.
Conclusion: Making Amazon OpenSearch Governance Defensible
Amazon OpenSearch data governance succeeds when it is continuous, measurable, and enforceable. The core pattern is consistent: discover and classify sensitive data, apply least-privilege access governance, reduce exposure with masking, collect audit-ready evidence, and automate reporting. Do that, and OpenSearch becomes a governed asset rather than an uncontrolled liability.
DataSunrise supports this program end-to-end, with flexible deployment options (see deployment modes) and a unified overview of capabilities in the DataSunrise overview. For hands-on evaluation, you can start from Download or request a walkthrough via Demo.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now