Amazon OpenSearch Regulatory Compliance
Amazon OpenSearch Service is widely adopted for log analytics, observability, security monitoring, and search-driven applications. In many organizations, OpenSearch indexes contain authentication events, customer activity, application telemetry, and operational logs that qualify as regulated data.
As OpenSearch deployments grow, so does regulatory exposure. Yes, AWS provides strong security capabilities, including layered access controls and encryption options, but compliance responsibility still belongs to the organization operating the data. Regulations don’t care whether regulated data lives in a database, a log index, or a search cluster — they care whether you can prove controls exist and are enforced consistently.
This article explains what regulatory compliance means for Amazon OpenSearch, what native controls can (and can’t) do, and how DataSunrise enables centralized compliance enforcement across OpenSearch environments — including discovery, audit evidence, masking, reporting, and policy automation.
Why Amazon OpenSearch Falls Under Regulatory Scope
OpenSearch is often treated as an analytics or logging backend. That assumption is dangerous. In real deployments, OpenSearch frequently stores:
- User identifiers and authentication events (usernames, emails, session IDs, tokens)
- Application payloads and request metadata (URLs, headers, query params)
- Operational logs containing personal or financial data (support tickets, purchase events, payment errors)
- Security events tied to individual users or systems (alerts, detections, access anomalies)
Once personal or regulated data is indexed, compliance requirements such as GDPR, HIPAA, PCI DSS, and SOX apply. OpenSearch becomes part of the regulated data estate whether teams planned for it or not — and that’s usually the problem.
What “Regulatory Compliance” Actually Means for OpenSearch
Compliance isn’t a checkbox that says “encryption enabled.” For OpenSearch environments, auditors and security teams typically expect evidence that you can:
- Identify regulated content across indices (data classification and inventory)
- Control access using least-privilege policies (who can query what)
- Reduce exposure of sensitive fields in query results (masking/redaction)
- Log and reconstruct activity for investigations and audits (who did what, when, from where)
- Prove enforcement using consistent reporting, not hand-built screenshots
That last one matters more than people like to admit. If you can’t produce repeatable evidence, you don’t have “compliance” — you have hope.
Core Compliance Challenges in Amazon OpenSearch
Unlike transactional databases, OpenSearch introduces unique compliance challenges:
- Audit depth isn’t automatically audit evidence
OpenSearch can produce logs, but compliance-grade audit evidence often requires richer context (identity, role, index scope, query intent, and response characteristics). Without external controls such as database activity monitoring, teams struggle to prove who accessed regulated data and what was exposed. - Sensitive data hides inside “harmless” logs
OpenSearch doesn’t magically label “this field is PII.” Logs and documents may contain emails, phone numbers, tokens, addresses, or embedded identifiers. Without automated data discovery, compliance scope becomes guesswork. - Access control doesn’t equal exposure control
Even with role restrictions, once a query is permitted, results can still contain sensitive values. Many organizations need runtime controls such as dynamic data masking to ensure users see only what they are allowed to see — not everything the index contains. - Evidence is fragmented across teams and tools
Compliance audits require consistent, repeatable proof aligned to frameworks. That means centralized audit data, clear policies, and standardized reporting aligned with data compliance regulations, not scattered exports and “ask the platform team for logs.”
Amazon OpenSearch Native Security: Useful, But Not the Whole Story
AWS provides meaningful security capabilities for OpenSearch — including layered access control and encryption options — and these features are foundational. If you’re not enabling them, you’re not doing compliance; you’re doing wishful thinking.
At a minimum, compliance-bound deployments should rely on:
- Network isolation and restricted connectivity (e.g., private access patterns)
- Access policies and identity controls for who can reach domain endpoints
- Encryption controls for data protection expectations
- Audit logging for traceability (when enabled and configured correctly)
One important compliance reality: audit logging is not always enabled by default, and enabling it requires deliberate configuration, including log publishing and dashboard configuration. If you don’t explicitly build an audit posture, you don’t have one.
Outbound reference (native audit logs documentation): Monitoring audit logs in Amazon OpenSearch Service
Compliance Control Matrix for Amazon OpenSearch
Below is a practical mapping of common regulatory expectations to the controls you need around OpenSearch. This is not legal advice — it’s the reality of what auditors ask for.
| Regulation | What Auditors Expect in OpenSearch Context | Typical Gaps Without a Compliance Layer | DataSunrise Controls That Close the Gap |
|---|---|---|---|
| GDPR | Data inventory, access traceability, controlled exposure of personal data | Unknown PII spread across indices; weak evidence for who accessed what | GDPR compliance, PII discovery, audit logs |
| HIPAA | Access controls, audit controls, and monitoring of PHI exposure | Hard to prove PHI wasn’t exposed through search queries and exports | HIPAA compliance, audit trails, activity history |
| PCI DSS | Limit visibility of cardholder data, monitor access, produce audit evidence | Log payloads can accidentally contain PAN or tokens; no runtime redaction | PCI DSS compliance, static masking, dynamic masking |
| SOX | Traceability, integrity of access records, and repeatable reporting | Manual log collection; inconsistent reporting; weak audit packaging | Compliance Manager, report generation, automated compliance reporting |
| Cross-regulation baseline | Least privilege, monitoring, secure storage of evidence | Overbroad roles, missing detection, and underpowered audit storage | least privilege principle, audit storage performance, behavior analytics |
DataSunrise Compliance Architecture for Amazon OpenSearch
DataSunrise acts as a unified compliance layer for OpenSearch, operating independently from cluster internals. This architecture enables consistent enforcement without modifying OpenSearch indices or applications — and it’s especially valuable when you have multiple environments (prod, staging, multiple domains, mixed cloud, hybrid).
Instead of relying on scattered native settings, you enforce consistent governance using:
- data activity history for traceability across environments
- audit guidance to structure evidence collection
- learning rules and audit automation to reduce manual policy tuning
1) Discover and Classify What’s in Your Indices
Before compliance controls can be applied, you need a defensible inventory of regulated data. DataSunrise scans OpenSearch content using data discovery and identifies regulated elements such as Personally Identifiable Information (PII).
This eliminates the “we think it’s only logs” excuse by producing real scope evidence.
2) Enforce Least-Privilege Access and Governance Policies
Compliance requires access controls that are consistent, reviewable, and enforceable. DataSunrise supports policy enforcement through:
- role-based access control to align access with job functions
- access controls for structured governance rules
- reverse proxy patterns to centralize control points
- rules priority to prevent policy collisions and blind spots
This is where governance stops being “tribal knowledge” and starts being enforceable.
3) Reduce Data Exposure with Masking and Safer Test Data
Even if users are authorized to query an index, they should not automatically see raw sensitive fields. DataSunrise supports exposure reduction using:
- data masking concepts applied in practice
- dynamic masking to redact sensitive fields at query time
- static masking for safe copies and lower environments
- synthetic data generation to reduce reliance on real regulated data in dev/test
Masking is not just about “hiding things.” It’s how you prove you’re enforcing minimum necessary access.
4) Centralize Auditing, Evidence, and Compliance Workflows
Audit evidence must be centralized, reviewable, and exportable. DataSunrise provides:
- audit logs for query-level traceability
- activity monitoring to spot misuse and abnormal behavior
- database activity history for investigations and audits
- database agent options for flexible deployment patterns
And yes — you can wire compliance events into real workflows:
- Slack notifications for fast security response
- Microsoft Teams notifications for operational visibility
Configuring Compliance Rules in DataSunrise for OpenSearch
Compliance rules define how regulated data must be handled and how evidence is collected. In DataSunrise, you configure a compliance task, scope the discovery targets, and enforce reporting and monitoring workflows.
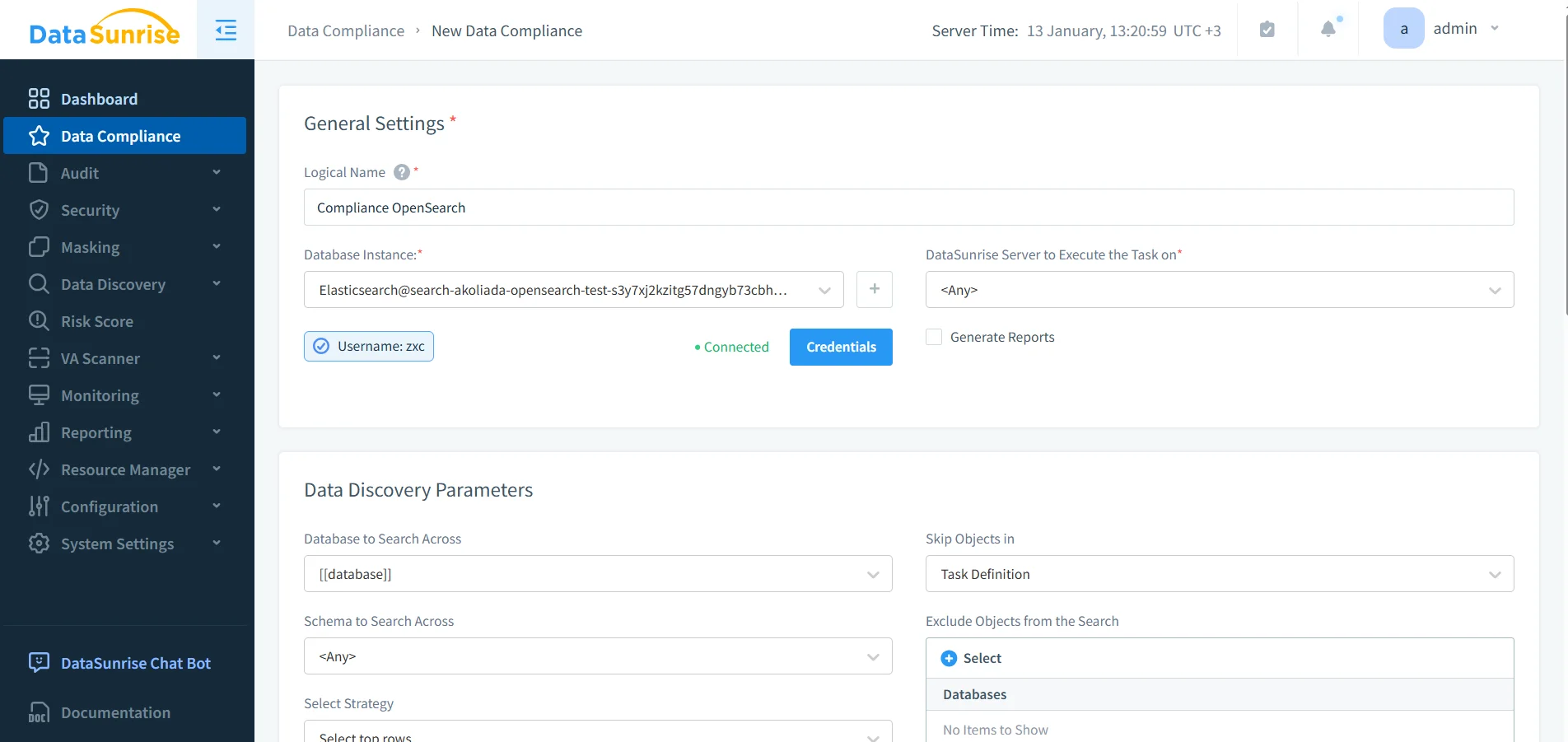
Defining regulatory compliance rules for Amazon OpenSearch in the DataSunrise Compliance Manager.
This can align directly with audit objectives such as:
- audit goals tied to regulatory evidence requirements
- database security controls that support compliance baselines
- database encryption posture expectations across the data estate
Security Controls That Keep Compliance From Collapsing
Compliance doesn’t survive contact with real attackers unless security controls reinforce it. DataSunrise strengthens compliance posture with:
- database firewall controls to reduce abusive access patterns
- security guide practices for building a defensible control model
- security rules that can be adapted to detect malicious query behavior
- threat detection foundations for query-layer abuse patterns
- vulnerability assessment to reduce compliance drift from misconfiguration
If you want a practical entry point specifically for OpenSearch audit workflows, see: Database Audit for Amazon OpenSearch.
Do not treat OpenSearch as “just logs.” If an index contains user identifiers or payload data, regulators will treat it as a regulated data store. Compliance must be enforced at the query level, not after an incident.
Operational Checklist: What Makes OpenSearch Compliance “Defensible”
If you need a sanity checklist that won’t betray you during an audit, start here:
- Know your scope: run discovery, identify PII/regulated fields, document where they exist
- Enforce least privilege: restrict who can query which indices and how broadly
- Reduce exposure: mask sensitive fields where full visibility isn’t required
- Log with context: retain query-level audit evidence with identity and target object details
- Report consistently: generate repeatable, framework-aligned compliance reports
- Alert on violations: integrate detection with security and ops workflows
Finally, if your organization runs multiple data platforms (which it does — don’t pretend), central governance matters. DataSunrise supports 40+ data platforms so OpenSearch doesn’t become the “one weird system” that breaks your compliance program.
Conclusion: Making Amazon OpenSearch Compliance Sustainable
Amazon OpenSearch is powerful infrastructure, but it was not designed to be a compliance system on its own. Native controls help — especially when configured correctly — but regulatory compliance requires more than encryption and basic access rules. It requires data visibility, exposure reduction, audit-grade evidence, and repeatable reporting.
By layering DataSunrise over OpenSearch, you gain centralized discovery, policy-driven compliance enforcement, robust auditing, and reporting workflows aligned to GDPR, HIPAA, PCI DSS, and SOX. Compliance becomes a continuous control system instead of a quarterly panic attack.
If you’re ready to operationalize compliance (instead of roleplaying it), you can explore deployment options and get hands-on quickly: Download or request a walkthrough via Demo.
Outbound reference (AWS security capabilities overview): Amazon OpenSearch Service Security
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now