ClickHouse Audit Trail
ClickHouse, a high-performance analytical database from the official project at https://clickhouse.com/, is engineered for large-scale workloads using vectorized execution, columnar storage, distributed query processing, and real-time ingestion. While this architecture delivers exceptional speed, it complicates governance and compliance. Organizations operating under regulations such as SOX, HIPAA, PCI DSS, GDPR, and similar frameworks require complete visibility into all data access and administrative actions. This means maintaining a verifiable and immutable audit trail rather than relying on scattered logs distributed across cluster nodes.
Although ClickHouse provides valuable native telemetry through system tables and server logs, these mechanisms lack the consistency, centralization, and enrichment necessary for enterprise-grade auditing. DataSunrise solves this by unifying, enriching, and governing ClickHouse audit trails across the entire environment. For broader context, you can also review related topics such as Audit Logs, Database Activity Monitoring, and Audit Trail Fundamentals.
What Is an Audit Trail?
An audit trail is a chronological, tamper-resistant record capturing all meaningful actions inside a database system. It documents user activity, SQL statements, access to sensitive fields, schema modifications, authentication attempts, permission changes, data updates, and engine-level operations such as merges and mutations.
A complete audit trail answers four essential compliance questions: who accessed the data, what they did, when it occurred, and whether it was authorized.
For deeper reading, see Data Activity History and Database Activity History.
For ClickHouse, a proper audit trail must be immutable, exhaustive, centrally stored, searchable, and maintained according to retention policies. Native ClickHouse logs provide partial visibility but remain node-local and insufficient for regulated environments. DataSunrise provides the unified, enriched, and compliance-ready audit framework required for modern governance.
Native ClickHouse Audit Capabilities
ClickHouse surfaces internal activity through system tables and server logs. These components form the foundation of its native audit trail.
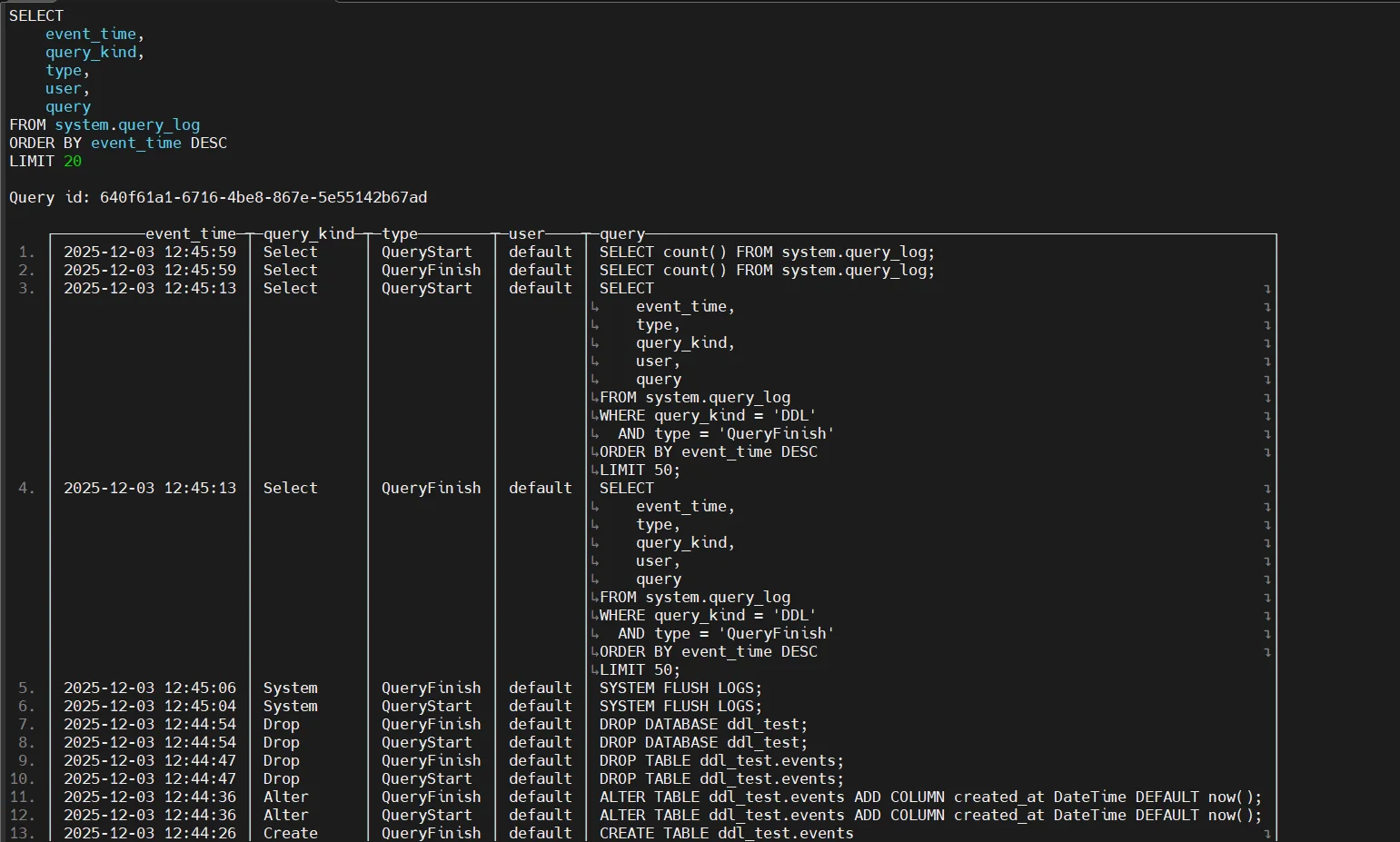
1. Query Log — Capturing Executed Queries
The system.query_log table records SQL statements, timestamps, user identity, exceptions, read/write metrics, and performance details. These events become important for Data Audit Goals
and downstream compliance reporting.
SELECT
event_time,
user,
query_id,
query_kind,
query,
exception,
read_rows,
written_rows
FROM system.query_log
ORDER BY event_time DESC
LIMIT 50;
2. Access Control & Authorization Logging
Authentication failures and RBAC permission issues appear as exceptions. These logs contribute to RBAC Governance
and provide early indicators of unauthorized access.
SELECT event_time, user, client_address, interface, os_user, http_user_agent
FROM system.query_log
WHERE exception LIKE '%AUTHENTICATION%'
OR type = 'Exception'
ORDER BY event_time DESC;
3. Server Logs — Operational & Administrative Events
Operational activity such as DDL execution, merges, replication steps, and configuration reloads is captured in clickhouse-server.log. These operations often fall under Data Security Requirements
and infrastructure governance policies.
SELECT event_time, query, user
FROM system.query_log
WHERE query_kind = 'DDL'
ORDER BY event_time DESC;
4. Part Log & Mutation Tracking
Internal storage operations and data mutations appear in system.part_log and system.mutations.
Understanding these changes is essential to maintaining Compliance Regulations
and validating schema integrity.
SELECT create_time, command, is_done, latest_failed_part
FROM system.mutations
ORDER BY create_time DESC;
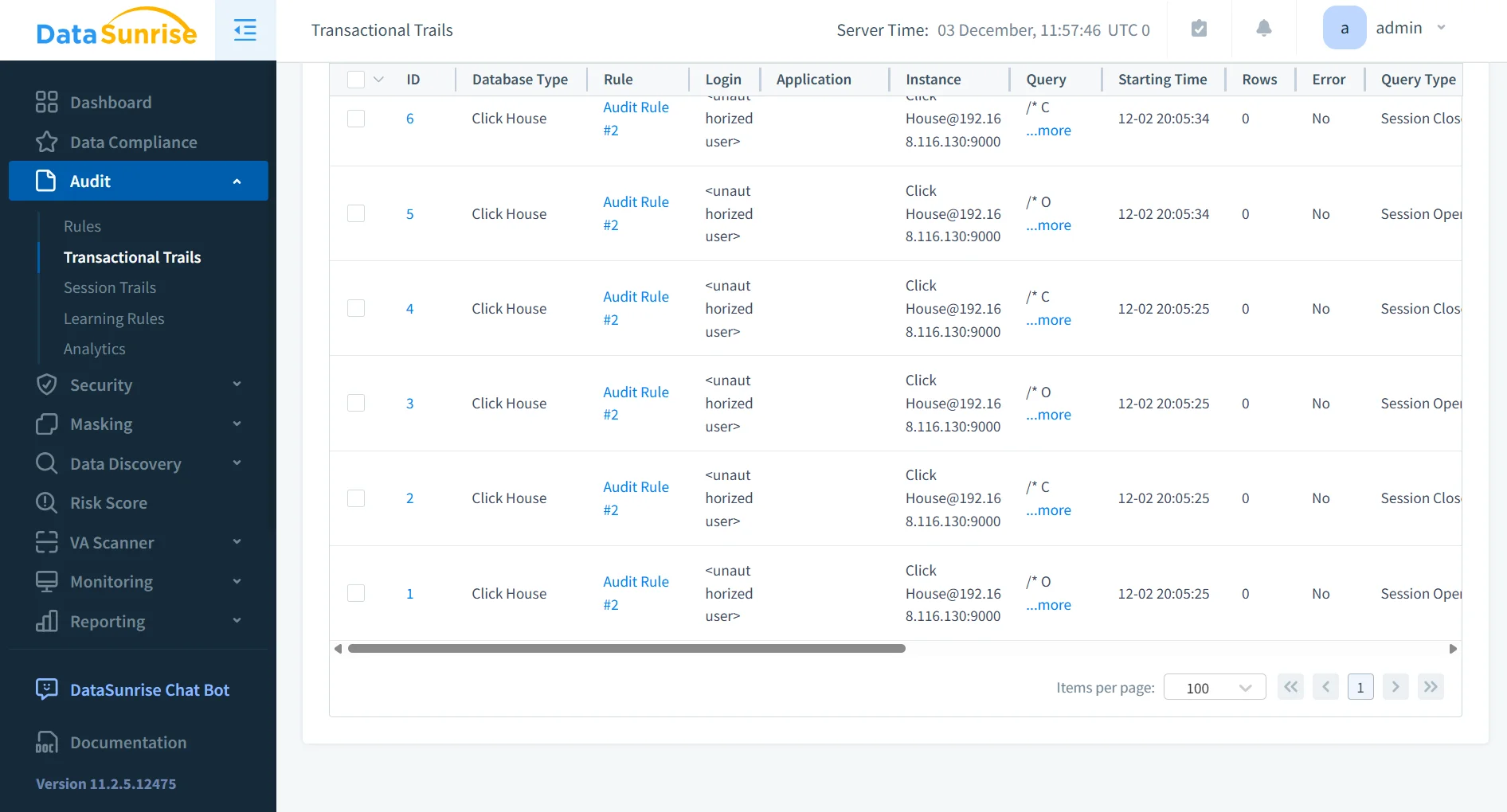
DataSunrise Audit Trail for ClickHouse
DataSunrise provides a centralized and compliance-ready audit layer that extends far beyond ClickHouse’s native logging. It captures SQL traffic through proxy or sniffer mode, enriches every request with contextual metadata, and stores it in an immutable audit repository that spans the entire cluster.
For more on how DataSunrise functions, refer to DataSunrise Overview
and DataSunrise Audit Guide.
Below are the four key pillars of DataSunrise’s ClickHouse auditing capabilities — expanded with additional information.
1. Centralized Cluster-Wide Audit Capture
DataSunrise intercepts SQL traffic before it reaches ClickHouse or observes it passively in sniffer mode. Every request is enriched with user identity, session metadata, sensitivity indicators, timestamps, object references, and optional before-and-after values, producing a unified audit trail across shards, replicas, and distributed environments.
- Ensures consistent audit coverage even when nodes scale dynamically
- Eliminates blind spots caused by node-local ClickHouse logs
- Normalizes all events into a consistent format
- Captures activity regardless of driver, protocol, or client application
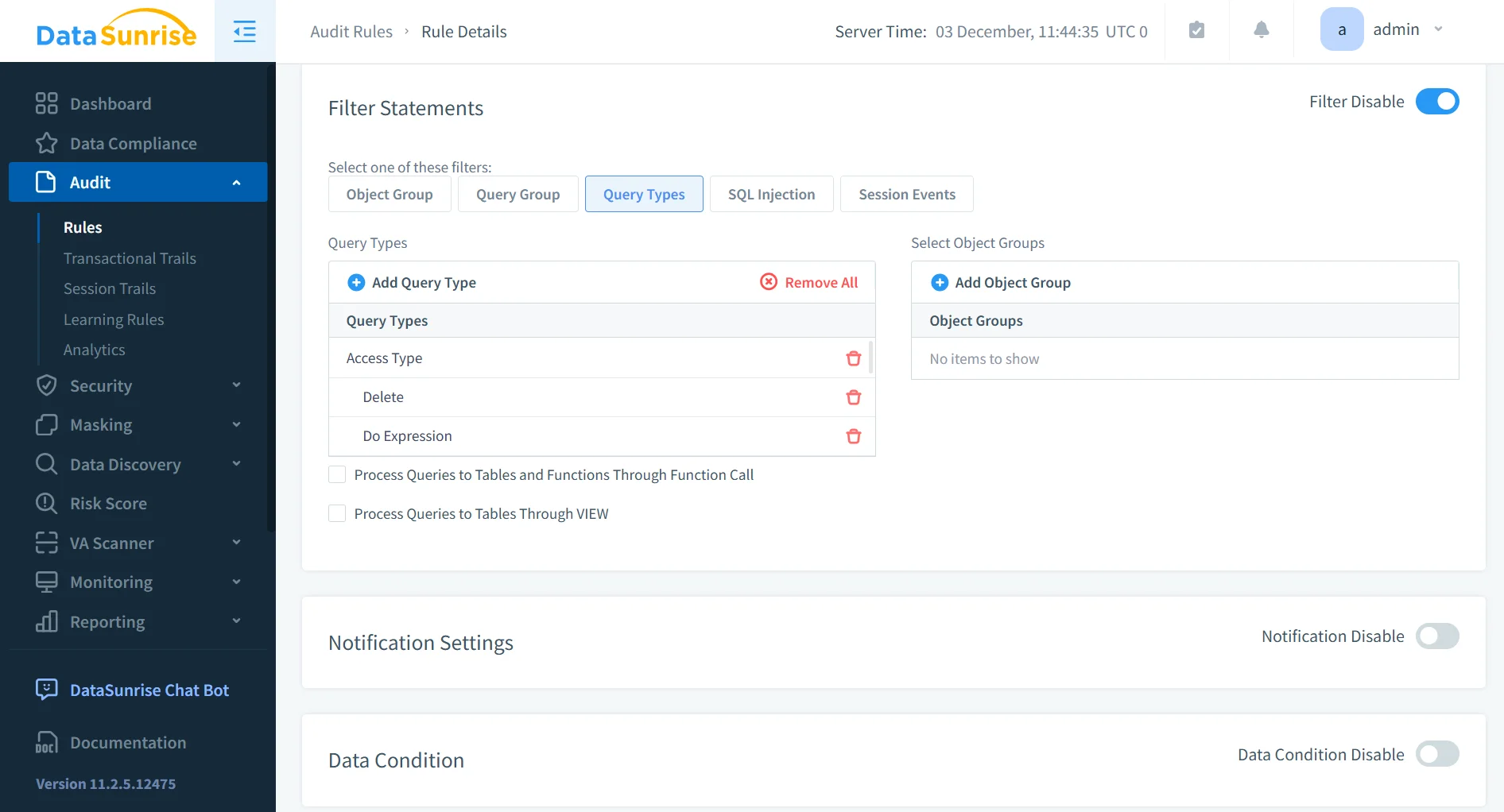
2. Granular Rule-Driven Monitoring and Enforcement
Administrators can define precise audit rules specifying which operations should be logged, monitored, masked, or restricted. DataSunrise identifies regulated datasets in real time, applies dynamic masking to sensitive fields, triggers alerts on unauthorized or suspicious queries, and blocks malicious actions through SQL firewall enforcement.
- Supports object-level, column-level, and user-level rules
- Enables context-aware policies responsive to user roles
- Enforces masking without modifying ClickHouse schemas
- Detects bypass attempts through deep SQL analysis
3. Forensic Analysis and Behavioral Visibility
DataSunrise provides powerful investigative tools for tracing user behavior, correlating events, reconstructing sessions, and identifying anomalies with ML-enhanced analytics. Security teams can create new rules directly from observed events.
- Supports chronological reconstruction of user activity
- Detects deviations from established behavioral baselines
- Offers multi-dimensional filtering across numerous attributes
- Enables long-term audit data retention for regulatory needs
Relevant topics: User Behavior Analytics
and Real-Time Notifications.
4. Compliance Automation and Cross-Platform Governance
DataSunrise supports GDPR, HIPAA, SOX, PCI DSS, and other frameworks through automated reporting templates and continuous monitoring. Real-time notifications integrate with Slack, Teams, and SIEM systems. LLM/ML-powered analytics enhance insider-threat detection. With support for more than 40 databases and cloud platforms, DataSunrise ensures consistent governance across heterogeneous environments.
- Generates auditor-ready evidence automatically
- Maintains data retention and integrity requirements
- Unifies governance across SQL, NoSQL, and cloud environments
- Detects compliance drift and policy violations
See also: Data Compliance Overview
and Compliance Manager.
Business Impact
| Business Area | Impact of DataSunrise for ClickHouse |
|---|---|
| Visibility | Provides unified, cluster-wide audit trails with enriched context for every SQL operation. |
| Accountability | Delivers immutable and complete event history, ensuring precise attribution of user actions. |
| Compliance Readiness | Aligns ClickHouse environments with GDPR, HIPAA, SOX, PCI DSS, and other standards. |
| Investigation Speed | Accelerates forensic analysis through correlation tools and behavioral analytics. |
| Security Strength | Enhances protection against insider threats using masking, SQL firewalling, anomaly detection, and alerts. |
Conclusion
While ClickHouse provides useful native diagnostic and operational logs, these mechanisms alone do not meet enterprise compliance requirements. DataSunrise unifies ClickHouse activity into an enriched, centralized audit repository with masking, firewalling, analytics, and automated compliance reporting.
For organizations running ClickHouse in regulated or mission-critical environments, DataSunrise delivers the governance, oversight, and security required to maintain trust and operational integrity.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now