Couchbase Audit Trail
In today's distributed NoSQL landscape, implementing comprehensive audit trails for Couchbase has become essential for enterprise security. According to Verizon's 2024 Data Breach Investigation Report, organizations with robust NoSQL audit trail systems detect insider threats 82% faster and reduce compliance-related costs by up to 68%.
Couchbase, a leading distributed NoSQL database platform, offers native auditing capabilities. However, with data breach costs averaging $4.88 million in 2024, organizations require more sophisticated solutions to protect sensitive data and demonstrate regulatory compliance.
This guide explores Couchbase's native audit trail features and demonstrates how DataSunrise's Zero-Touch Compliance Automation enhances NoSQL security monitoring with automated compliance reporting.
Understanding Couchbase Audit Trail
A Couchbase audit trail creates a chronological record of all database operations within your distributed NoSQL environment, capturing who accessed what documents, when, and from where—essential for maintaining database security oversight.
The audit trail captures:
- Document Operations: CREATE, READ, UPDATE, DELETE operations on JSON documents
- Query Executions: N1QL queries and index usage patterns
- Authentication Events: Login attempts across cluster nodes
- Administrative Actions: Cluster configuration and access control updates
- Cross-Cluster Activities: Operations spanning multiple data centers
Native Couchbase Audit Trail Capabilities
Couchbase includes built-in features for implementing audit trails through various monitoring mechanisms. For detailed configuration options, refer to the official Couchbase auditing documentation.
1. Couchbase Audit Configuration
Enable comprehensive auditing through the Admin Console or REST API:
# Enable auditing via REST API
curl -X POST http://localhost:8091/settings/audit \
-u Administrator:password \
-d auditdEnabled=true \
-d rotateInterval=86400 \
-d logPath=/opt/couchbase/var/lib/couchbase/logs
The audit subsystem tracks:
- Authentication Events (8192-8207): Login attempts, password changes
- Authorization Events (8208-8223): Permission grants, role modifications
- Data Service Events (8224-8239): Document operations, query executions
- Administrative Events (8240-8255): Cluster changes, bucket operations
2. Reviewing Audit Logs
Examine captured audit trail data:
# View recent audit entries
tail -f /opt/couchbase/var/lib/couchbase/logs/audit.log
# Filter for specific events
cat audit.log | jq 'select(.id == 8201)'
3. Couchbase Web UI
The Admin Console provides intuitive access to audit information:
- Security Tab: Configure audit settings and review security events
- Logs Tab: Access and filter audit logs
- Query Workbench: Analyze audit data using N1QL queries
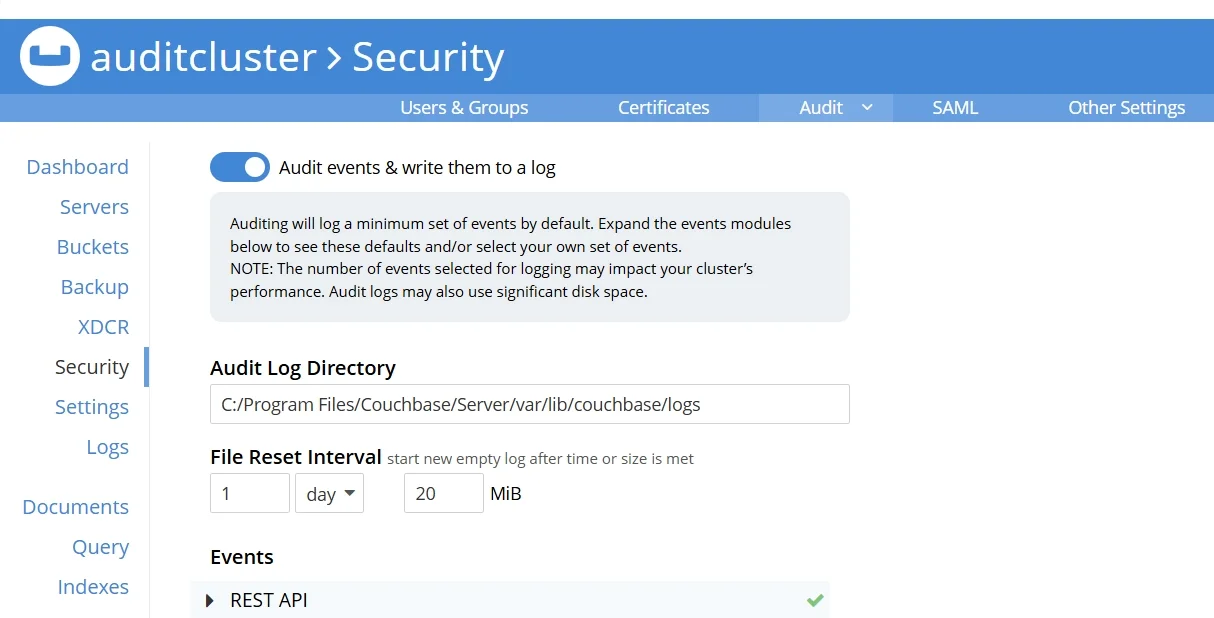
Limitations of Native Couchbase Audit Trail
| Native Feature | Key Limitation | Business Impact |
|---|---|---|
| Audit Logs | JSON format requires custom parsing | Complex analysis of security threats |
| Event Configuration | Manual selection of event types | Risk of missing critical events |
| Retention | Basic log rotation only | May not meet compliance requirements |
| Alerting | No real-time notifications | Delayed response to threats |
| Data Classification | No automatic discovery | Critical data may remain unidentified |
Enhanced Couchbase Audit Trail with DataSunrise
DataSunrise significantly enhances NoSQL data security monitoring through Autonomous Compliance Orchestration and sophisticated analytics. Unlike basic logging approaches, DataSunrise delivers enterprise-grade database activity monitoring with comprehensive audit logs analysis.
Setting Up DataSunrise for Couchbase
1. Connect to Couchbase Cluster
Establish a secure connection between DataSunrise and your Couchbase environment. DataSunrise supports both single-node and multi-node clusters for comprehensive coverage.
2. Create NoSQL-Specific Audit Rules
Configure granular audit rules using No-Code Policy Automation to monitor specific buckets, users, and document-level operations based on data sensitivity.
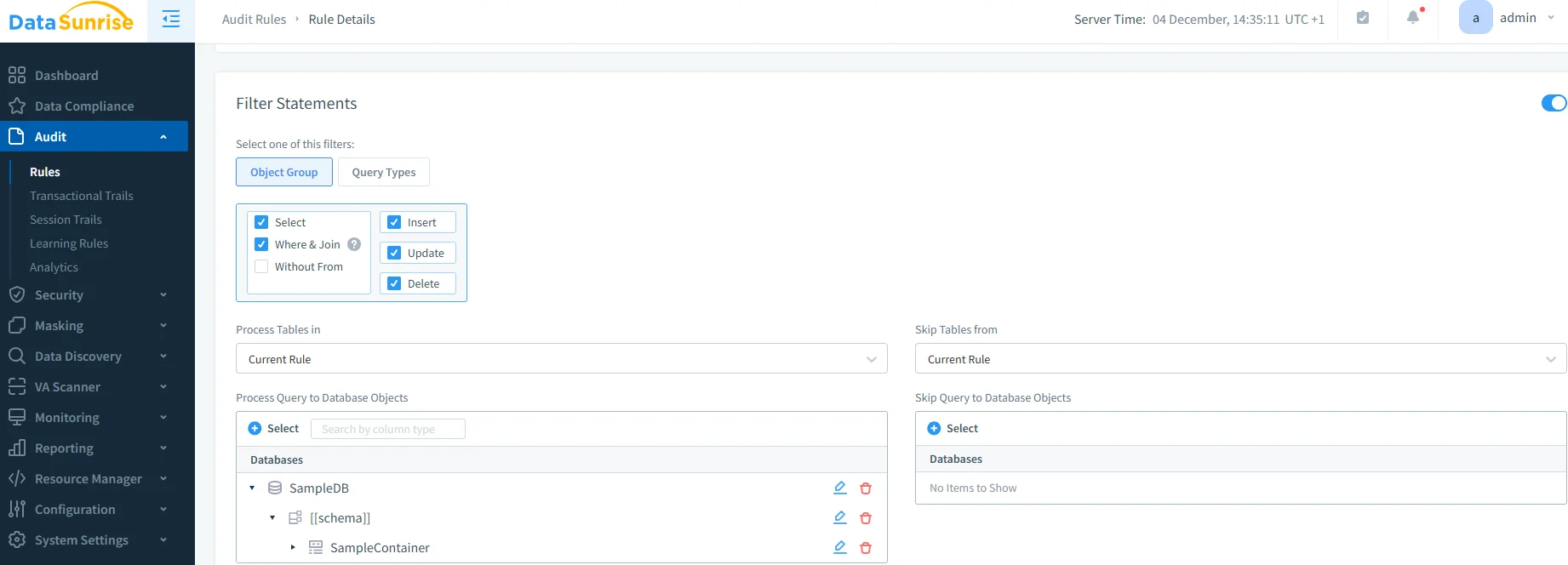
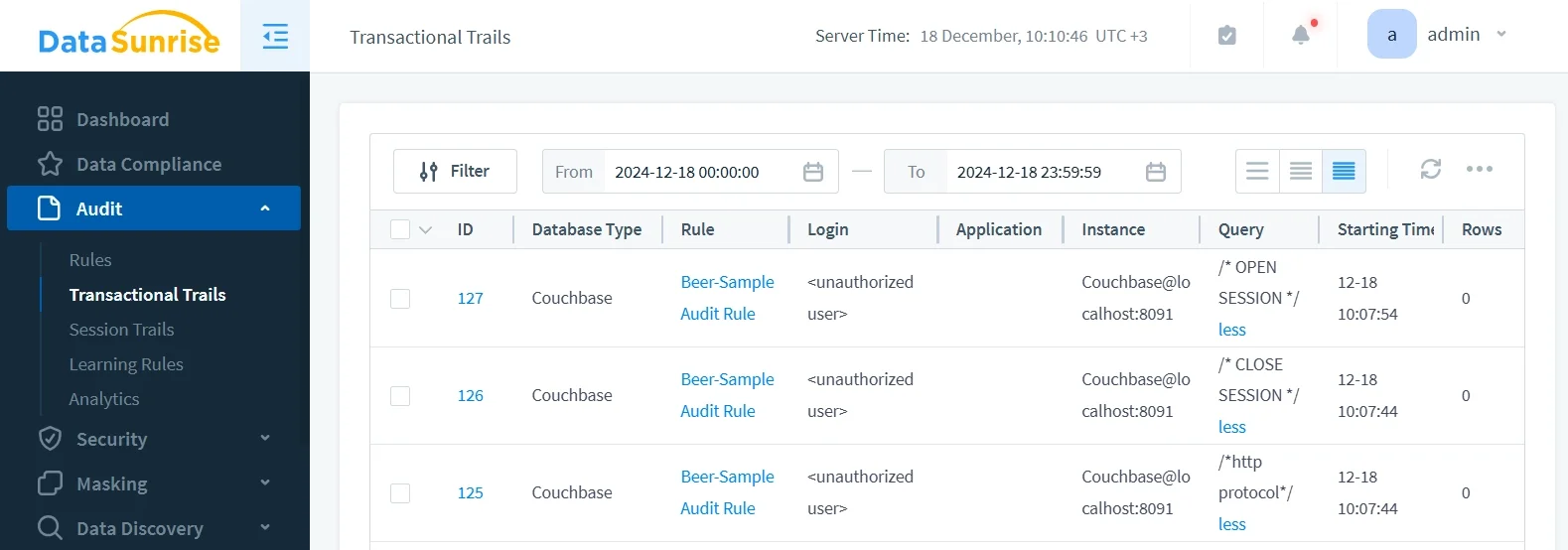
3. Review Comprehensive Audit Trails
Access detailed audit information through DataSunrise's unified dashboard with advanced filtering, real-time monitoring, and intelligent correlation.
Key Advantages of DataSunrise for Couchbase
Data Discovery: Automatically identify sensitive data in JSON documents using NLP and machine learning across dynamic schemas.
No-Code Policy Automation: Create sophisticated audit rules through an intuitive interface, reducing implementation time from weeks to hours.
Real-Time Notifications: Receive immediate alerts for suspicious activities with contextual information for rapid threat detection.
User Behavior Analysis: Establish baselines and detect anomalies using ML algorithms that adapt to changing patterns.
Automated Compliance Reporting: Generate pre-configured reports for GDPR, HIPAA, PCI DSS, and SOX.
Dynamic Data Masking: Protect sensitive JSON fields in real-time while maintaining application functionality.
Cross-Platform Visibility: Monitor SQL and NoSQL databases from a unified console with support for over 40 data storage platforms.
Best Practices for Couchbase Audit Trail Implementation
1. Performance-Optimized Strategy
Align audit strategies with bucket design to minimize performance impact. Apply detailed trails to sensitive data buckets while using sampling for high-volume operations. Balance comprehensive auditing with sub-millisecond latency requirements.
2. Document-Centric Configuration
Focus auditing on collections with PII or regulated data. Monitor complex N1QL queries and cross-document operations. Implement field-specific rules for sensitive JSON attributes.
3. Cluster-Wide Correlation
Establish unified correlation across cluster nodes. Implement XDCR-aware auditing for geographically distributed centers. Configure consistent security policies across all environments.
4. Compliance Integration
Map audit collection to specific compliance requirements. Implement tamper-evident storage with database encryption. Schedule regular compliance validation checks.
5. Enhanced Security Implementation
Deploy DataSunrise for Intelligent Policy Orchestration and continuous data protection. Leverage ML for pattern analysis. Utilize unified monitoring with database firewall capabilities for comprehensive correlation.
Conclusion
As organizations rely on Couchbase for business-critical applications, implementing robust audit trails has become essential for security and compliance. While Couchbase offers foundational native capabilities, organizations with complex requirements benefit significantly from enhanced solutions like DataSunrise.
DataSunrise provides comprehensive security for NoSQL environments with Zero-Touch Data Protection, advanced audit trails, real-time monitoring, and automated reporting. With flexible deployment modes, DataSunrise transforms Couchbase audit trails into strategic security assets.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now