Effortless Data Compliance for SAP HANA
In today's regulatory landscape, achieving data compliance for SAP HANA has become a critical business imperative. According to IBM's 2024 Data Breach Report, organizations with comprehensive audit trail systems detect potential security threats significantly faster and substantially reduce breach-related costs. With SAP HANA managing sensitive business data across finance, HR, and customer operations, implementing robust compliance frameworks is essential.
SAP HANA's in-memory architecture powers mission-critical enterprise applications, making database security and regulatory adherence paramount for organizations worldwide.
This article explores SAP HANA's native compliance capabilities and demonstrates how DataSunrise transforms compliance from a resource-intensive burden into an automated process with Zero-Touch Compliance Automation.
Native SAP HANA Compliance Capabilities
SAP HANA includes built-in features for implementing compliance controls that track database activity and maintain audit logs. These native capabilities provide the foundation for regulatory adherence.
1. SAP HANA Audit Trail Configuration
SAP HANA provides native audit logging through SQL commands:
-- Enable audit logging for SAP HANA
ALTER SYSTEM ALTER CONFIGURATION ('global.ini', 'SYSTEM')
SET ('auditing configuration', 'global_auditing_state') = 'true'
WITH RECONFIGURE;
-- Configure audit policies for specific actions
CREATE AUDIT POLICY sensitive_data_access
AUDITING SUCCESSFUL SELECT, UPDATE, DELETE
ON SCHEMA financial_data
LEVEL CRITICAL;
-- Enable the audit policy
AUDIT POLICY sensitive_data_access;
2. Reviewing SAP HANA Audit Logs
Access audit logs through system views:
-- Query audit log entries
SELECT
TIMESTAMP, USER_NAME, CLIENT_IP, SCHEMA_NAME,
OBJECT_NAME, ACTION_NAME, AUDIT_LEVEL
FROM SYS.AUDIT_LOG
WHERE TIMESTAMP >= ADD_DAYS(CURRENT_TIMESTAMP, -1)
ORDER BY TIMESTAMP DESC;
For comprehensive configuration details, refer to the SAP HANA Security Guide.
Enhanced Data Compliance for SAP HANA with DataSunrise
DataSunrise significantly enhances regulatory adherence through Autonomous Compliance Orchestration and intelligent policy automation. Unlike manual approaches, DataSunrise delivers Comprehensive Sensitive Data Detection with Zero-Touch Data Protection.
Implementing DataSunrise for SAP HANA Compliance
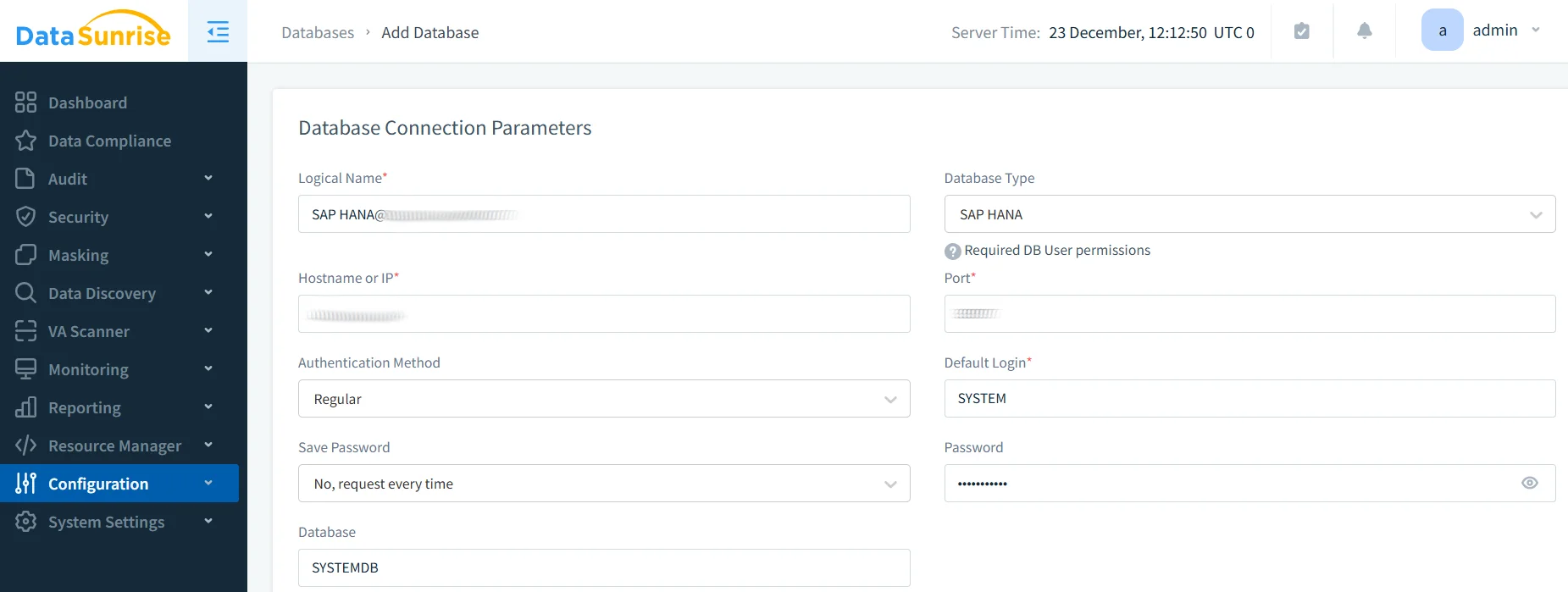
1. Connect to SAP HANA Instance: Establish a secure connection through the intuitive administrative interface, supporting both single-container and multi-tenant architectures.
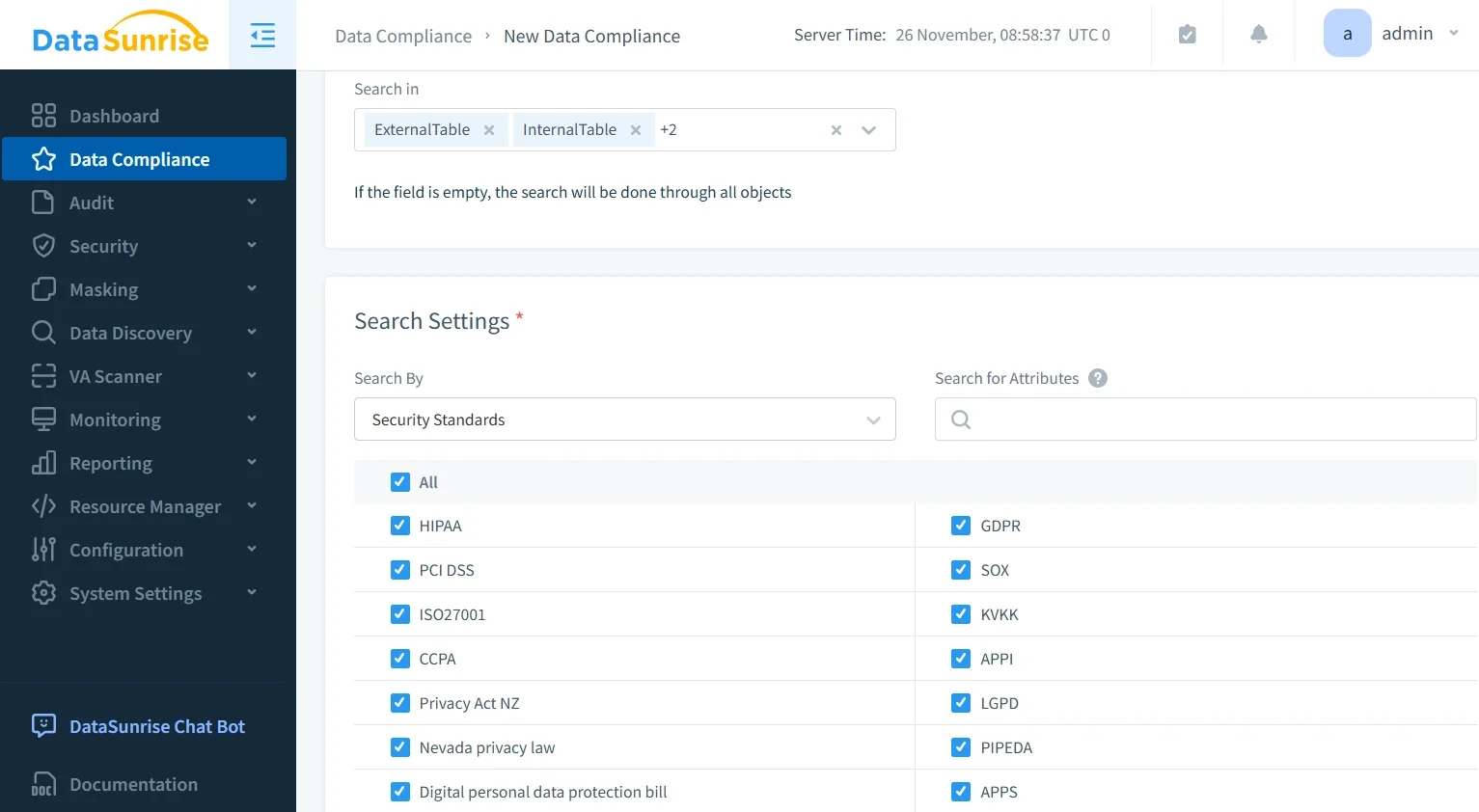
2. Create Compliance-Focused Audit Rules: Configure granular rules using No-Code Policy Automation, defining which schemas require monitoring and setting enforcement levels based on regulatory frameworks.
3. Review Comprehensive Compliance Trails: Access detailed documentation through the unified dashboard with advanced filtering, real-time monitoring, and automated compliance mapping.
Key Advantages of DataSunrise for SAP HANA Compliance
Auto-Discover & Classify: Automatically identify regulated information using NLP and machine learning without manual configuration.
No-Code Policy Automation: Create sophisticated policies through an intuitive interface, reducing implementation time from weeks to hours.
Automated Compliance Reporting: Generate pre-configured reports for GDPR, HIPAA, PCI DSS, and SOX, reducing audit preparation from days to minutes.
Real-Time Monitoring: Receive immediate alerts for violations with contextual information and recommended actions.
Dynamic Data Masking: Protect sensitive data in real-time while maintaining application functionality.
Behavioral Analytics: Establish baselines and detect anomalies using ML algorithms.
Cross-Platform Consistency: Monitor SAP HANA and other databases from a unified console with support for over 40 platforms.
Best Practices for SAP HANA Compliance Implementation
1. Risk-Based Compliance Strategy
Focus comprehensive controls on schemas containing financial records and personal information. Apply detailed tracking to high-risk operations while using sampling for routine activities.
2. Performance-Optimized Configuration
Design policies aligned with SAP HANA's columnar architecture. Apply real-time blocking for critical violations while using audit-only mode for informational monitoring to maintain optimal database performance.
3. Compliance Documentation and Validation
Maintain tamper-evident documentation with encryption. Schedule regular compliance checks and implement automated report generation that maps activities to specific regulatory requirements.
4. Enhanced Implementation with DataSunrise
Deploy DataSunrise's platform for intelligent policy orchestration. Leverage behavioral analytics and cross-system correlation for comprehensive compliance monitoring. Implement role-based access controls to ensure proper data governance across your SAP landscape.
Business Benefits of Effortless SAP HANA Compliance
| Benefit | Description |
|---|---|
| Risk Mitigation | Identify compliance gaps before regulatory fines occur |
| Streamlined Audits | Dramatically reduce audit preparation time with automation |
| Operational Efficiency | Eliminate manual tasks, freeing teams for strategic work |
| Regulatory Confidence | Demonstrate continuous compliance with real-time monitoring |
| Cost Optimization | Reduce compliance costs through automation |
Conclusion
As SAP HANA serves as the foundation for critical business operations, implementing effortless data compliance has become essential. While SAP HANA provides foundational tools, organizations with complex requirements benefit significantly from enhanced solutions like DataSunrise.
DataSunrise provides comprehensive compliance automation for enterprise databases, offering Zero-Touch Data Protection with advanced monitoring and Continuous Regulatory Calibration. With flexible deployment modes, DataSunrise transforms SAP HANA compliance from a burden into a streamlined, automated process.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now