How to Automate Data Compliance for Amazon OpenSearch
How to automate data compliance for Amazon OpenSearch is a practical question for any team using OpenSearch for log analytics, observability, security monitoring, or application search. These workloads frequently ingest user identifiers, authentication events, request payload fragments, and operational telemetry that can become regulated data once indexed and searchable. When that happens, compliance can’t be handled as a one-time checklist—it must be continuously enforced and continuously provable.
AWS provides managed infrastructure and security features for Amazon OpenSearch Service, but compliance responsibility remains with the organization operating the data. The goal of automation is to replace manual governance with repeatable controls: discover sensitive data, scope it, enforce policy at the query layer, capture audit evidence, and generate reports on demand.
Why Automation Is Essential for OpenSearch Compliance
OpenSearch environments change quickly. Pipelines add fields, new indices appear, dashboards drive broad access, and “temporary” logs become permanent. Manual compliance breaks under that pace. Automation reduces risk by keeping controls aligned with reality, not with last quarter’s architecture diagram.
Compliance obligations generally require three things: visibility into what data exists, control over who can access it, and evidence that policies are enforced over time. That expectation shows up across data compliance regulations and industry frameworks.
Automation Targets: What to Automate in Amazon OpenSearch
A reliable automation program for OpenSearch typically includes five recurring workflows:
- Inventory automation: continuously identify sensitive fields (including values embedded in unstructured logs).
- Scope automation: define which indices and objects are governed and keep that scope current.
- Policy automation: apply consistent controls for auditing, masking, and enforcement.
- Evidence automation: produce audit-ready records and retention without manual stitching.
- Reporting automation: generate regulator- and auditor-ready reports on a schedule.
DataSunrise centralizes OpenSearch compliance tasks in a single control plane for consistent enforcement and reporting.
Reference Architecture for Automated Compliance
Automation works best when compliance controls sit close to the access path—where queries can be analyzed, governed, and logged consistently. DataSunrise acts as a unified layer for discovery, auditing, and enforcement, enabling automation without requiring changes to indexed documents.
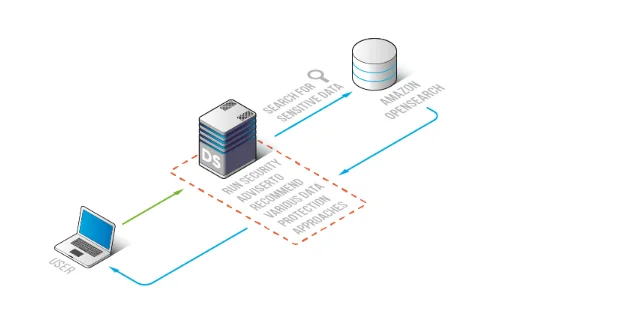
Automated discovery and enforcement architecture: DataSunrise inspects activity and searches for sensitive data in Amazon OpenSearch.
Step 1: Automate Sensitive Data Discovery in OpenSearch
Automation starts with visibility. If you can’t reliably identify what sensitive data exists in OpenSearch, every downstream control becomes guesswork. DataSunrise Data Discovery helps scan OpenSearch content to detect regulated elements such as PII, identifiers, and high-risk patterns embedded in structured fields or free-text payloads.
This discovery output becomes your living compliance inventory: what is in scope, where it appears, and what must be protected. The key automation principle is cadence: discovery should run repeatedly, not only during audits.
Step 2: Automate Scope Selection for Compliance Tasks
After discovery, you need scope boundaries that are precise enough to protect sensitive indices without disrupting low-risk operational analytics. DataSunrise supports scoped task configuration so policies apply only where they are required. This reduces friction and prevents “govern everything” rollouts that break dashboards.
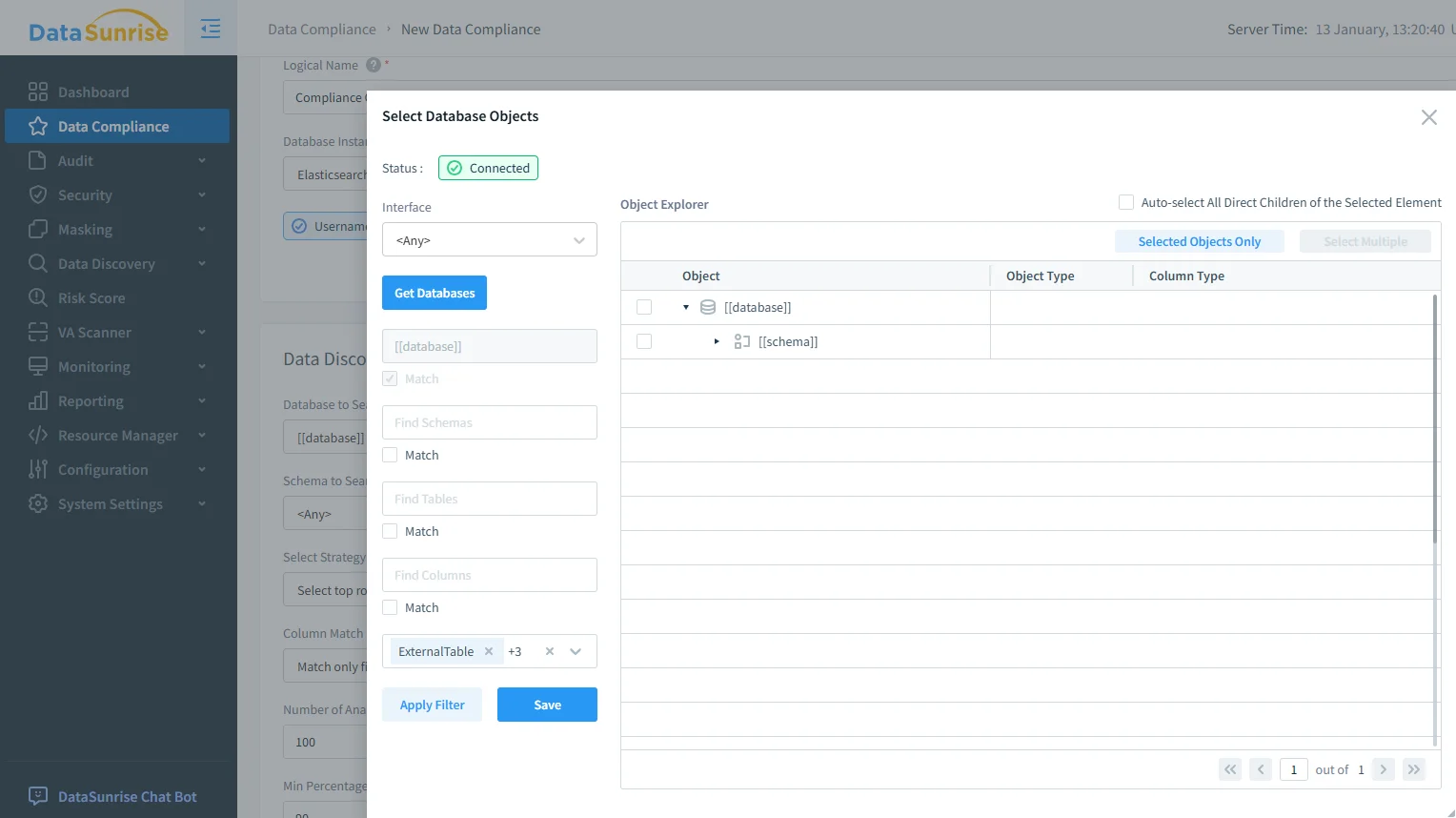
Scoping OpenSearch compliance: selecting database objects ensures policies apply to the right indices and fields.
Scope automation becomes more effective when aligned with governance roles. Use role-based access control and centralized access controls so object selection maps to real operational responsibility, not shared credentials.
Step 3: Automate Policy Enforcement with Compliance Rules
Once scope is defined, compliance automation depends on consistent, policy-driven enforcement. DataSunrise Compliance Manager enables rules that align with organizational requirements and standard frameworks. This is also where you operationalize the principle of least privilege by ensuring access is limited by role and purpose, not convenience.
When multiple controls can apply to the same activity, deterministic outcomes matter. Use rules priority to ensure enforcement remains predictable and audit evidence remains consistent.
Step 4: Automate Audit Evidence Collection and Retention
Automated compliance must produce evidence continuously. DataSunrise supports centralized Data Audit with detailed audit logs and immutable audit trails that reconstruct activity for audits and investigations. For ongoing oversight, database activity monitoring helps detect risky behavior patterns early instead of after an incident.
Retention must also be designed. Evidence that can’t be stored efficiently becomes evidence that gets turned off. Use guidance on audit storage performance to keep auditing sustainable as OpenSearch volume grows.
AWS also provides native service-level logging as a baseline reference: Amazon OpenSearch audit logs. In practice, automation is strongest when evidence is centralized and standardized, rather than spread across multiple partial sources.
Step 5: Automate Exposure Reduction with Masking and Preventive Controls
Compliance is not only about whether a query is allowed—it is also about what the query returns. Many OpenSearch users need aggregation, search relevance, and troubleshooting context, not raw personal identifiers. Automate exposure controls using data masking, including dynamic data masking for query-time redaction and static data masking for safer downstream copies and lower environments. Where realistic datasets are required without real identifiers, synthetic data generation reduces exposure while maintaining analytical utility.
To prevent abuse, enforce preventive controls such as a database firewall and validate configuration posture with vulnerability assessment. For anomaly-driven automation, behavior analytics can surface suspicious access patterns that warrant investigation.
Step 6: Automate Reporting and Notifications
Auditors and regulators do not want screenshots—they want repeatable evidence packages. Automate reporting with report generation and automated compliance reporting so compliance outputs are produced on schedule and remain consistent across environments.
Automation should also include operational response. Route policy violations and high-risk events into incident workflows using Slack notifications and Microsoft Teams notifications. Finally, align the entire workflow with continuous data protection so compliance stays resilient through platform change.
Compliance Automation Output: What You Should Be Able to Prove
A useful way to validate automation is to map each compliance obligation to the evidence it produces. If an auditor asks for proof, the output should already exist.
| Compliance obligation | Automated control | Audit-ready output | Mapped compliance program |
|---|---|---|---|
| Identify regulated data in OpenSearch | Scheduled discovery scans | Discovery inventory and scope definition | GDPR compliance |
| Limit access to sensitive indices | Least-privilege roles and policy scope | Role mappings and policy enforcement evidence | HIPAA compliance |
| Record who accessed what and when | Centralized auditing and monitoring | Audit logs and immutable trails | PCI DSS compliance |
| Maintain accountability for review cycles | Automated reporting and retention | Recurring compliance reports for audits | SOX compliance |
Automate compliance like you automate deployments: continuous discovery, scoped policies, always-on auditing, and scheduled reporting. If compliance depends on memory or manual reviews, it will drift.
Do not index secrets (API keys, session tokens, passwords) into OpenSearch and assume encryption alone is “compliance.” Searchable secrets create a fast exfiltration path and can trigger reportable incidents. Prevent this with discovery, strict access controls, masking, and proactive monitoring.
Conclusion: Make Compliance Automation the Default for OpenSearch
To automate data compliance for Amazon OpenSearch effectively, treat compliance as an operational system: continuously discover sensitive data, scope governance precisely, enforce policies consistently, capture audit evidence by default, reduce exposure in query results, and generate reports automatically. DataSunrise provides a unified control plane to run these workflows across environments without slowing down OpenSearch analytics.
For implementation planning, review the DataSunrise overview and available deployment modes, then start with Download or request a guided Demo.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now