How to Manage Data Compliance for Amazon OpenSearch
How to manage data compliance for Amazon OpenSearch is no longer a niche concern reserved for “regulated” industries. OpenSearch clusters commonly power log analytics, security monitoring, observability dashboards, and search-driven applications. In practice, that means indices end up storing customer identifiers, authentication events, request payloads, and operational telemetry that may qualify as regulated data.
AWS delivers the managed platform and baseline controls, but your organization remains responsible for compliant data handling and defensible audit evidence. For service context, see Amazon OpenSearch Service. This article breaks down a practical compliance workflow: discover sensitive data, enforce access policies, monitor activity, reduce exposure, and automate reporting with DataSunrise.
The Core Compliance Risks with Amazon OpenSearch
OpenSearch is often treated as “just logs.” That assumption is how regulated data sneaks in. Because OpenSearch indexes semi-structured documents and free-text fields, sensitive values can appear anywhere: nested JSON, message strings, or enrichment pipelines. Common high-risk content includes:
- Customer and employee identifiers (names, emails, phone numbers)
- Authentication artifacts (usernames, session IDs, tokens)
- Financial metadata (invoice IDs, payment references, refunds)
- Support tickets and security events containing personal details
Once that data is searchable, compliance obligations apply across your data estate. Governance programs should be aligned with data compliance regulations and supported by continuous discovery of Personally Identifiable Information (PII), rather than relying on index naming conventions or “tribal knowledge.”
Technical Solutions: A Practical Control Plane for OpenSearch Compliance
Managing compliance in OpenSearch works best when controls are applied consistently at the query and access layer. DataSunrise provides a unified approach that combines discovery, policy enforcement, auditing, and protection without requiring changes to indexed documents.
1) Discover and classify sensitive data continuously
Compliance starts with knowing what is stored and where it lives. DataSunrise Data Discovery scans OpenSearch content to identify sensitive fields and patterns, including values embedded in unstructured logs. This creates a defensible scope for controls and prevents “unknown sensitive index” surprises during audits.
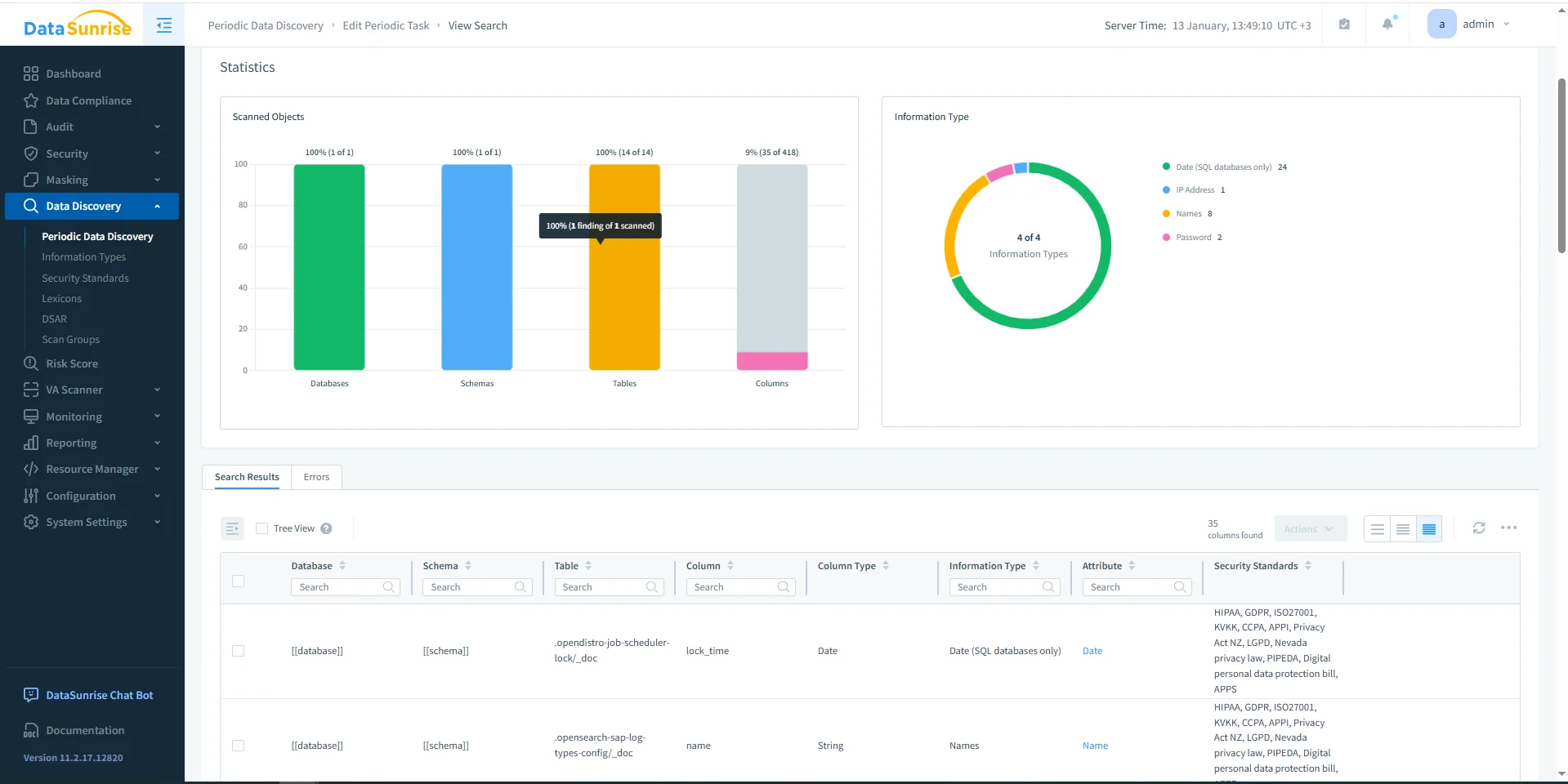
Discovery results establish which OpenSearch objects contain sensitive information and which standards they map to.
2) Define compliance scope and enforce policy boundaries
After discovery, translate findings into governance rules: which indices are in scope, who can access them, and what actions require logging or restrictions. DataSunrise Compliance Manager supports policy definition, while centralized access controls and role-based access control (RBAC) help enforce least-privilege access across teams.
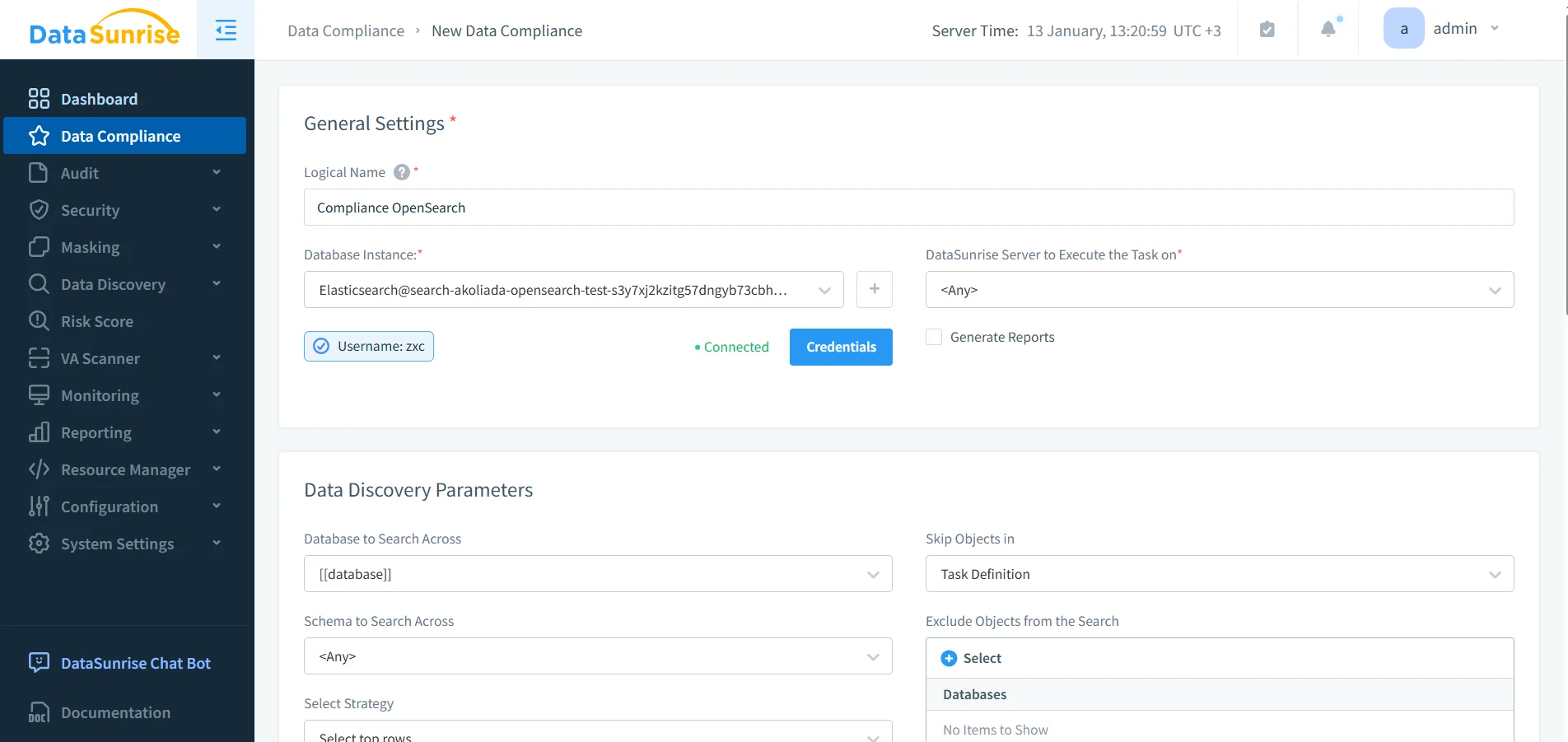
A policy-driven compliance rule in DataSunrise standardizes how OpenSearch access is governed and audited.
Strong scoping prevents operational friction. Instead of “govern everything,” you can apply stricter controls only to sensitive indices, while allowing low-risk observability data to remain broadly accessible.
3) Audit and monitor OpenSearch activity with full context
Auditors and incident responders need traceability: who queried what, when, from where, and under which policy. DataSunrise centralizes evidence with Data Audit, detailed audit logs, and immutable audit trails. For continuous oversight, database activity monitoring captures request patterns that often get lost in platform-only logging.
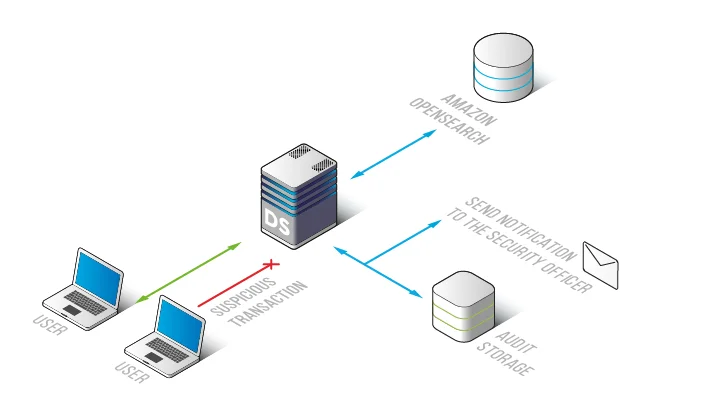
Monitoring OpenSearch queries at the access layer provides investigation-ready evidence and supports real-time alerts.
As a baseline reference for service-level logging, AWS documents configuration here: Amazon OpenSearch audit logs. Use it, but avoid splitting evidence across too many systems—centralized records simplify audits and incident response.
4) Reduce exposure with masking and preventive controls
Compliance is not only “who can access,” but also “what they can see.” DataSunrise supports exposure reduction with data masking, including dynamic data masking for query-time redaction and static data masking for safe downstream copies. This helps teams keep dashboards useful while limiting raw sensitive values.
To harden the access path, add a database firewall and validate security posture with vulnerability assessment. Where query interfaces are exposed, enforce proactive rules such as security rules against SQL injections and detection techniques like SQL injection detection to reduce the risk of data scraping, abuse, or account takeover amplification.
Operationalizing Compliance: Scheduling, Reporting, and Alerts
Compliance breaks when it becomes manual. OpenSearch evolves fast—new pipelines create new indices and fields—so compliance controls must run continuously. Periodic discovery keeps scope current and feeds reporting and remediation workflows.
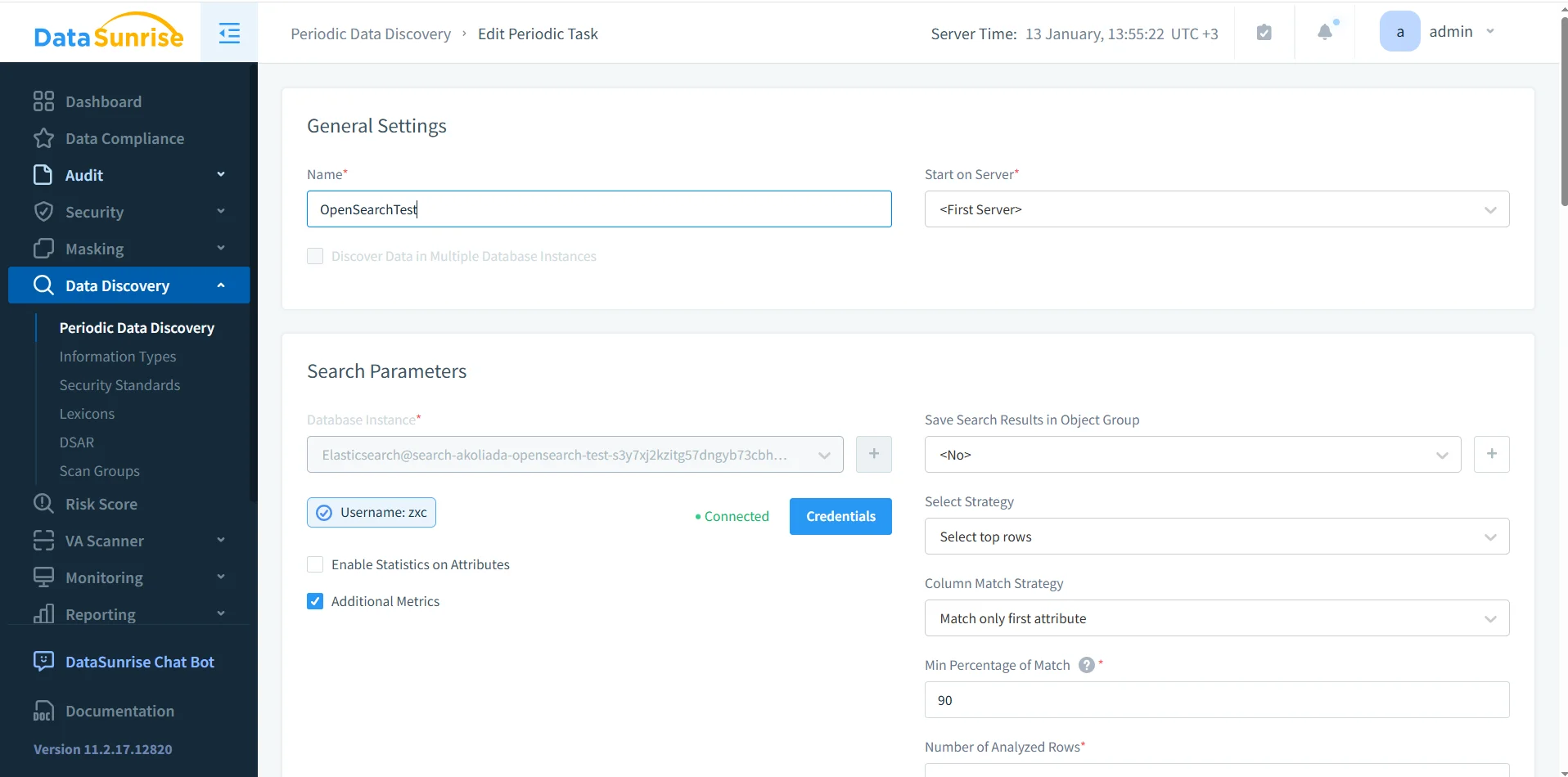
Scheduled discovery tasks help prevent governance drift as OpenSearch indices and schemas change over time.
For audit evidence, use report generation and automated compliance reporting to produce consistent outputs aligned with regulator expectations. For operational response, integrate Slack notifications, Microsoft Teams notifications, and behavior analytics to detect anomalies early and reduce time-to-investigation.
The Compliance Imperative
To keep OpenSearch compliance defensible, map regulatory expectations to controls you can prove in audits. The table below shows a simple control-to-evidence model.
| Regulation | OpenSearch requirement | Evidence you should produce |
|---|---|---|
| GDPR | Identify personal data and limit access/exposure | Discovery results, masking policies, access logs |
| HIPAA | Control and audit access to sensitive health-related data | Audit trails, monitoring events, reviewable reports |
| PCI DSS | Restrict payment data exposure and monitor access | Firewall events, audit logs, policy enforcement evidence |
| SOX | Maintain access accountability and change evidence | Centralized audit records and recurring compliance reports |
Treat OpenSearch as part of your regulated data estate. If an index includes identifiers or payload data, enforce compliance at the query layer using discovery, least privilege, masking, and centralized audit evidence.
Do not index secrets (API keys, session tokens, passwords) into OpenSearch and assume encryption alone makes it compliant. Searchable secrets shorten the path to exfiltration and can trigger reportable incidents.
Conclusion: Make Data Compliance for Amazon OpenSearch Continuous
Managing data compliance for Amazon OpenSearch is sustainable when you standardize four layers: discover sensitive data, govern access, protect outputs, and prove enforcement with audit-ready evidence. DataSunrise consolidates these workflows into a single control plane, reducing compliance drift across environments and speeding up audits and investigations.
To explore the platform capabilities, review the DataSunrise overview, compare deployment modes, and start with Download or a guided Demo.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now