
Teradata Audit Tools
Teradata powers large-scale analytics for enterprises across finance, telecom, and retail. With such data volumes, maintaining accountability is essential. Teradata audit tools enable administrators to track every query, transaction, and access attempt across distributed systems.
Modern compliance frameworks like GDPR, HIPAA, and SOX require verifiable evidence of user actions and data access. This article explains how native Teradata tools achieve that and how DataSunrise can further enhance the process with autonomous audit orchestration and centralized monitoring.
What is Audit Tools?
Audit tools are software utilities or database-integrated mechanisms that capture, record, and analyze user activities, system events, and data changes. They are fundamental components of data auditing, ensuring accountability and transparency within information systems.
In databases like Teradata, audit tools serve multiple purposes:
- Monitoring user actions: Every query, login, or data modification can be tracked for security verification.
- Supporting compliance: They provide traceable logs that demonstrate adherence to data privacy laws and security standards.
- Facilitating investigations: When anomalies occur, audit logs help identify root causes and unauthorized behavior.
- Improving governance: Detailed logs allow organizations to enforce internal data access policies effectively.
Modern audit tools, including solutions like DataSunrise, extend beyond logging to provide intelligent analytics, automated compliance reporting, and real-time alerting—key for maintaining operational trust in data-centric environments.
Native Teradata Audit Tools Overview
Teradata provides built-in facilities to record activity within the system. Its DBQL (Database Query Log) and Access Logging mechanisms capture information about queries, user sessions, and object interactions in real time.
Enabling Teradata Access Logging
Access Logging focuses on user behavior—who accessed which tables and when. Administrators can define log rules at the database or object level:
BEGIN LOGGING WITH TEXT ON EACH TABLE;
BEGIN LOGGING ON ALL;
BEGIN LOGGING ON DATABASE sales_db;
Logs are stored in DBC.AccessLog and DBC.EventLog, making it easy to filter specific actions:
SELECT UserName, ObjectName, AccessType, LogDate
FROM DBC.AccessLogV
WHERE LogDate > CURRENT_DATE - 1;
These logs can be analyzed for unauthorized activity, privilege misuse, or audit-trail verification during compliance checks.
Query-Level Tracking with DBQL
The Database Query Log (DBQL) captures every executed SQL statement and associated performance metrics:
BEGIN QUERY LOGGING WITH OBJECTS ON ALL;
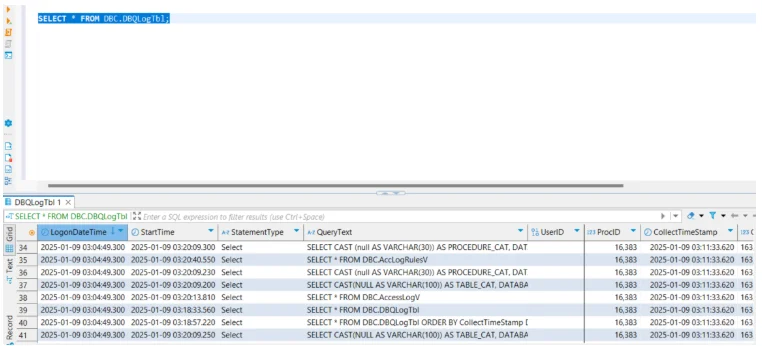
This statement activates detailed tracking for all users. Audit logs can be queried directly from system tables to monitor database activity. For example:
SELECT UserName, StartTime, StatementText
FROM DBC.DBQLogTbl
WHERE StartTime > CURRENT_DATE - 1;
DBQL’s modular architecture enables selective logging by user or application. Combined with Access Logging, it provides full accountability across Teradata workloads.
Enhancing Teradata Auditing with DataSunrise
DataSunrise extends Teradata’s audit ecosystem with autonomous compliance orchestration and real-time monitoring. It collects and correlates activity data across multiple clusters through proxy, sniffer, or native log integration modes—ensuring non-intrusive deployment with minimal overhead.
Below is how DataSunrise augments traditional Teradata audit tools:
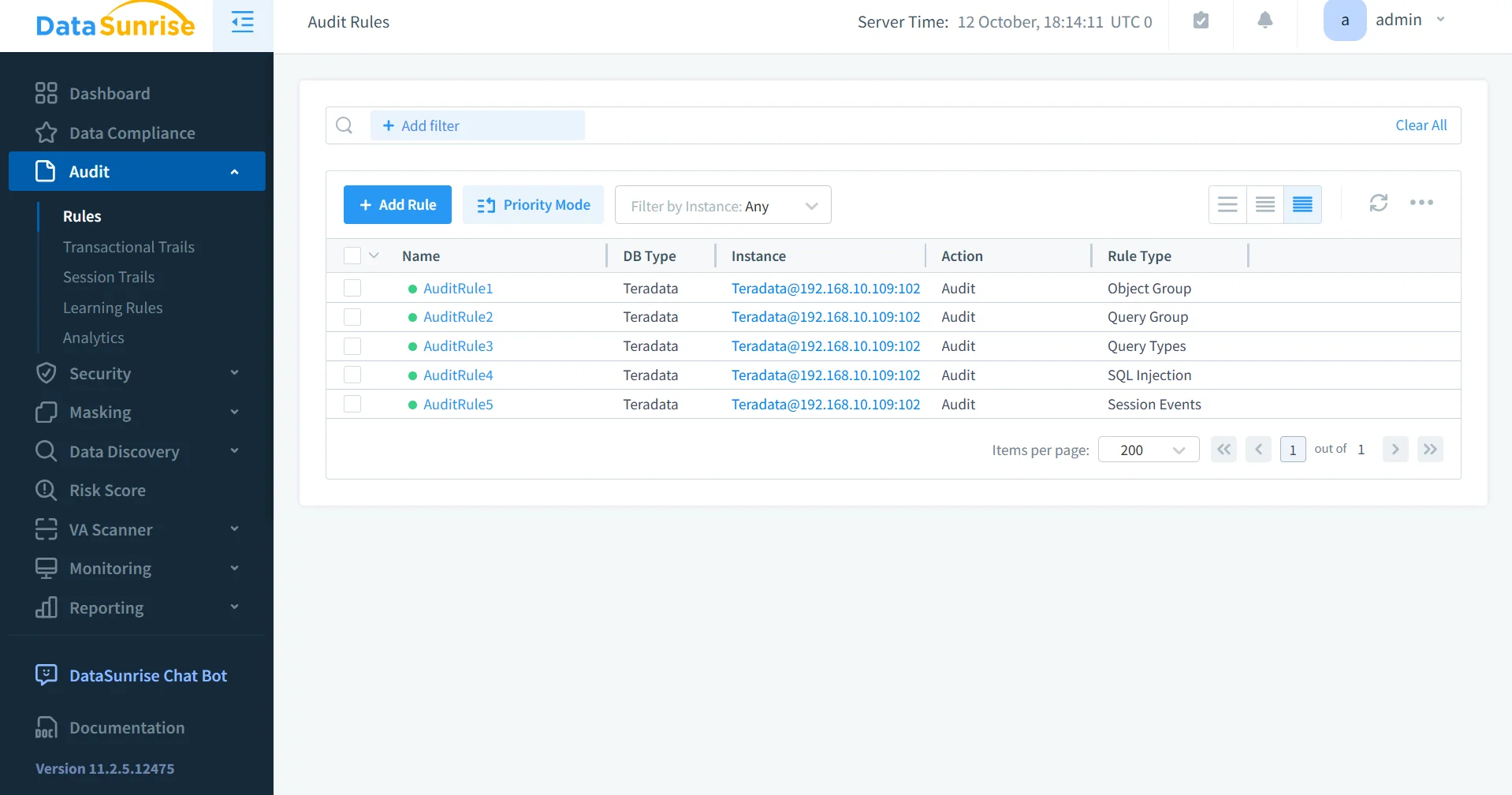
Granular Audit Rule Creation
Using Audit Rules, administrators can define precise filters by user, operation type, or object. This fine-grained control ensures compliance with policies like PCI DSS and SOX while minimizing unnecessary log noise.
- Targeted Monitoring: Apply audit rules to specific Teradata objects—such as tables or schemas—to capture only meaningful activity.
- User-Based Policies: Assign unique audit profiles for privileged users, developers, or data analysts.
- Time-Based Scheduling: Schedule audit rules to activate during critical hours or maintenance windows.
- Automated Triggers: Link audit actions with alerts to immediately flag unauthorized access or abnormal operations.
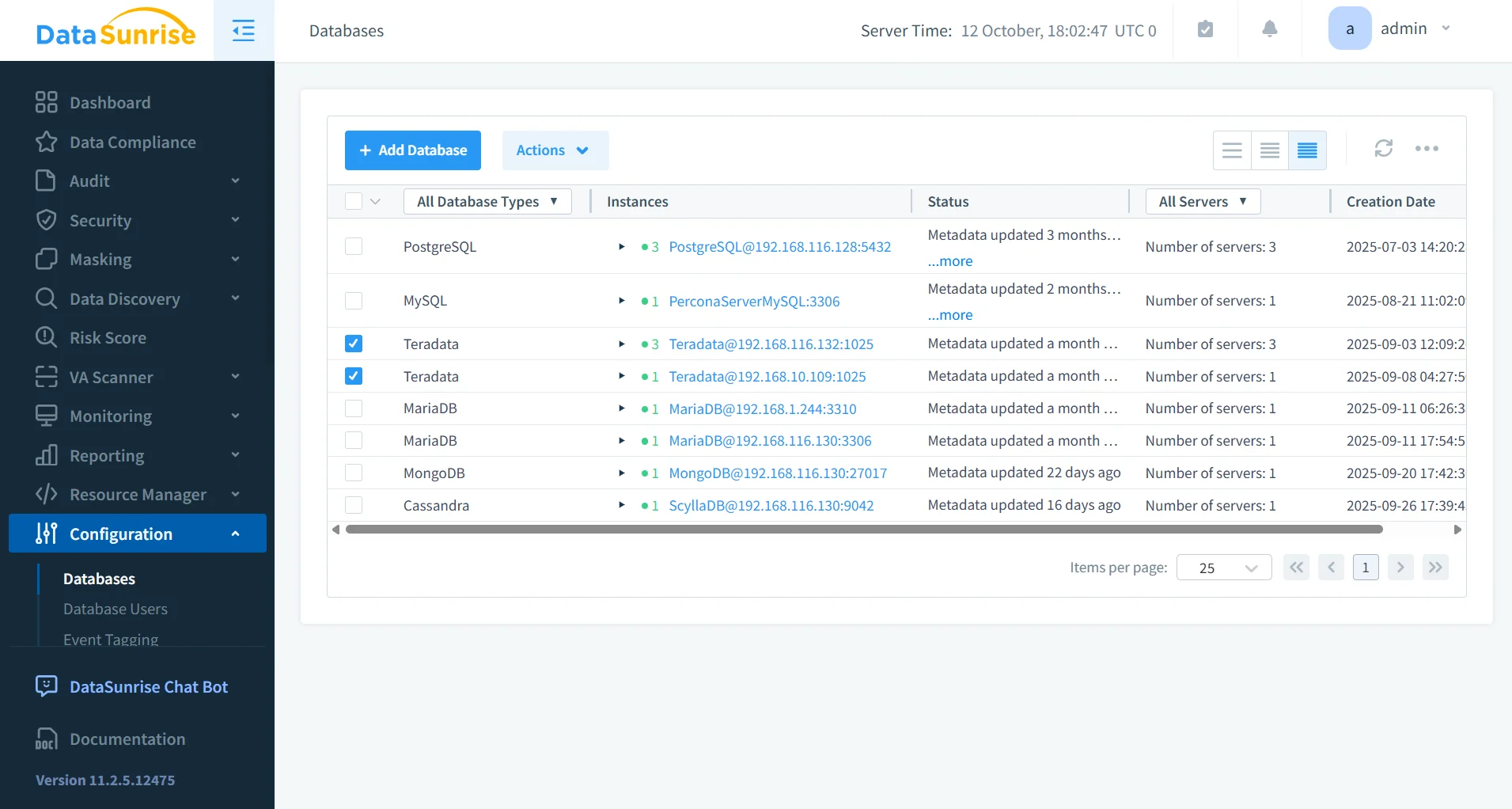
Centralized Monitoring and Reporting
With Database Activity Monitoring, DataSunrise unifies visibility across all Teradata environments. Administrators can review logs in real time, filter by session, and generate detailed compliance reports through automated compliance manager.
- Unified Interface: Consolidate logs from multiple Teradata systems and other databases into one dashboard.
- Dynamic Filters: Quickly filter events by query type, username, IP address, or affected object.
- Customizable Dashboards: Tailor visualization panels to display audit statistics and compliance metrics.
- Instant Reporting: Generate reports aligned with internal audit requirements and external regulators.
Real-Time Security Controls
DataSunrise integrates advanced security rules and behavioral analytics to detect anomalies instantly. Suspicious queries trigger alerts via Slack or SIEM connectors, strengthening proactive defense.
- Anomaly Detection: Identify deviations from normal behavior using statistical and rule-based models.
- SQL Injection Prevention: Automatically block or quarantine malicious statements detected in real time.
- User Behavior Analytics (UBA): Monitor typical access patterns and highlight abnormal actions.
- Alert Integration: Send notifications through popular communication and SIEM platforms for faster response.
Compliance Autopilot and Reporting
Through its Compliance Autopilot, DataSunrise continuously scans Teradata logs to identify sensitive data exposure and policy deviations. It generates audit-ready reports for GDPR, HIPAA, and PCI DSS—minimizing manual work and ensuring verifiable compliance evidence.
- Continuous Regulatory Alignment: Automatically updates compliance policies as standards evolve.
- Sensitive Data Discovery: Identifies PII, PHI, and financial data across Teradata schemas.
- Automated Compliance Workflows: Generates daily, weekly, or monthly reports based on your schedule.
- Audit Evidence Generation: Provides one-click PDF or CSV exports for audit committees and regulators.
Comparison Table
| Feature | Native Teradata Tools | Teradata with DataSunrise |
|---|---|---|
| Audit Scope | AccessLog, DBQL (manual setup) | Cross-cluster, multi-DB monitoring |
| Real-Time Alerts | None | Yes, via behavior analytics |
| Compliance Reporting | Manual export | Automated report generation |
| Retention & Storage | Local tables only | Centralized encrypted repository |
| Multi-System Visibility | Limited | Unified dashboard |
| Deployment | Native SQL setup | Proxy / Sniffer / Native log modes |
Conclusion
Teradata’s built-in audit tools form a solid foundation for accountability, but enterprises seeking advanced compliance management and automation benefit greatly from DataSunrise.
With autonomous rule orchestration, cross-platform monitoring, and audit-ready reporting, DataSunrise transforms Teradata auditing into a scalable, zero-touch compliance framework—ideal for organizations prioritizing security, transparency, and efficiency.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now