DataSunrise Database Firewall for Amazon Redshift
Amazon Redshift firewall by DataSunrise is a must when you aim to protect databases against outside threat or inside vulnerabilities. The firewall prevents unauthorized access to a database and blocks intrusion attempts. It inspects sql queries for improper content and malicious commands and alerts about suspicious database activity in real time.
Amazon Redshift firewall by DataSunrise is an advanced data-centric solution designed for real-time database protection. Ultimately the firewall ensures the advanced level of data security in real time and helps organizations stay compliant with regulatory requirements. The firewall secures critical data on-premises and in the cloud, protecting it from advanced persistent threats, malicious insiders, and other attacks.
The firewall monitors traffic to and from Amazon Redshift databases and performs deep packet filtering on the application level. It blocks behavior that contradicts the administrator-defined security policies. Every incoming and outgoing packet is disassembled and compared against the customized rules set. In the case of a query meeting a forbidden security rule, the firewall disconnects a client from DB or closes the session. Another line of query filtration is performed according to the updated list of attack signatures. Security rule configurations enables blocking of specified types of DDL, DML operations, SELECT/UPDATE/DELETE/INSERT queries, queries made by certain database users, queries targeted to certain database elements, queries from specified applications and so on.
The DataSunrise firewall is deployed in a proxy mode and resides between client and Amazon Redshift database, preventing their direct communication. Acting as an intermediary, it audits and logs queries and filters traffic blocking activity violating security policies.
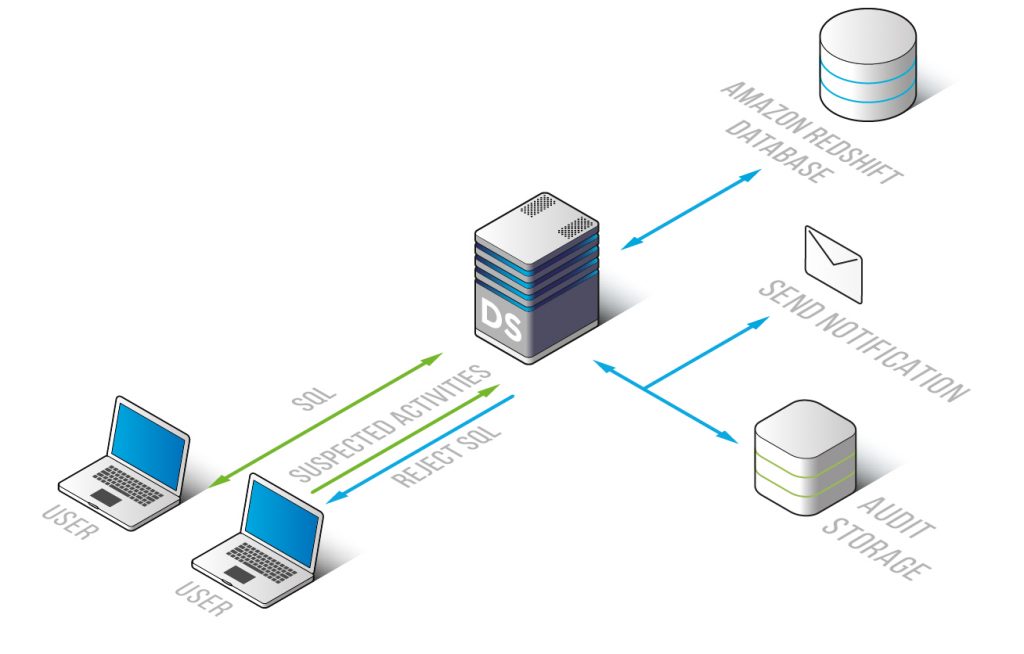
DataSunrise Security Suite can function as an authentication proxy providing Kerberos authentication of clients that are in the Active Active Directory domain. Connecting to the Amazon Redshift databases through DataSunrise proxy guarantees the secure connection and vastly reduces the risk of unauthorized access.
DataSunrise Database Firewall for Amazon Redshift databases is highly-available. You can install the firewall on multiple instances that will share firewall configuration settings. If one of the servers is down, a DataSunrise instance from another instance will be used as a proxy to filtrate the database transactions.
Among supported features there are:
- All user authentication methods
- Processing of SSL-encrypted traffic
- Data analysis and storage of all query types, including specific replication queries and multiple queries
- Detailed processing of prepared operations, cursors and portals
- Full analysis and data collection on COPY operation (transferring data from PostgreSQL table to external files and otherwise). Binary and text formats are supported
- Analysis of asynchronous queries (Pipelining)
- Converting all PostgreSQL data types, including composite, range and enum types, from binary format to text
- Processing of DML/DDL operations in compliance with transactions, search paths and administrator queries.