DataSunrise Database Firewall for Greenplum
Greenplum firewall by DataSunrise ensures that corporate databases are protected against any type of external or internal threat. It detects and blocks unauthorized activity. Customizable rules allow flexible configuration. Advanced SQL analysis algorithms ensure a high level of security. Immediate notification about suspicious behavior allows you to take urgent measures to prevent intrusion.
Greenplum firewall by DataSunrise is an enterprise-class tool aimed at protecting big data. It is designed to secure databases and data warehouses on-premises and in the cloud. It protects sensitive data from external attacks, malicious insiders and the potential threat of user negligence. The firewall also enhances an organization’s ability to meet compliance requirements.
The firewall is deployed in the proxy mode. It scans and intercepts communication between client and database. Playing a role of an inspection point the firewall audits, logs and filters traffic, blocking queries violating security policies.
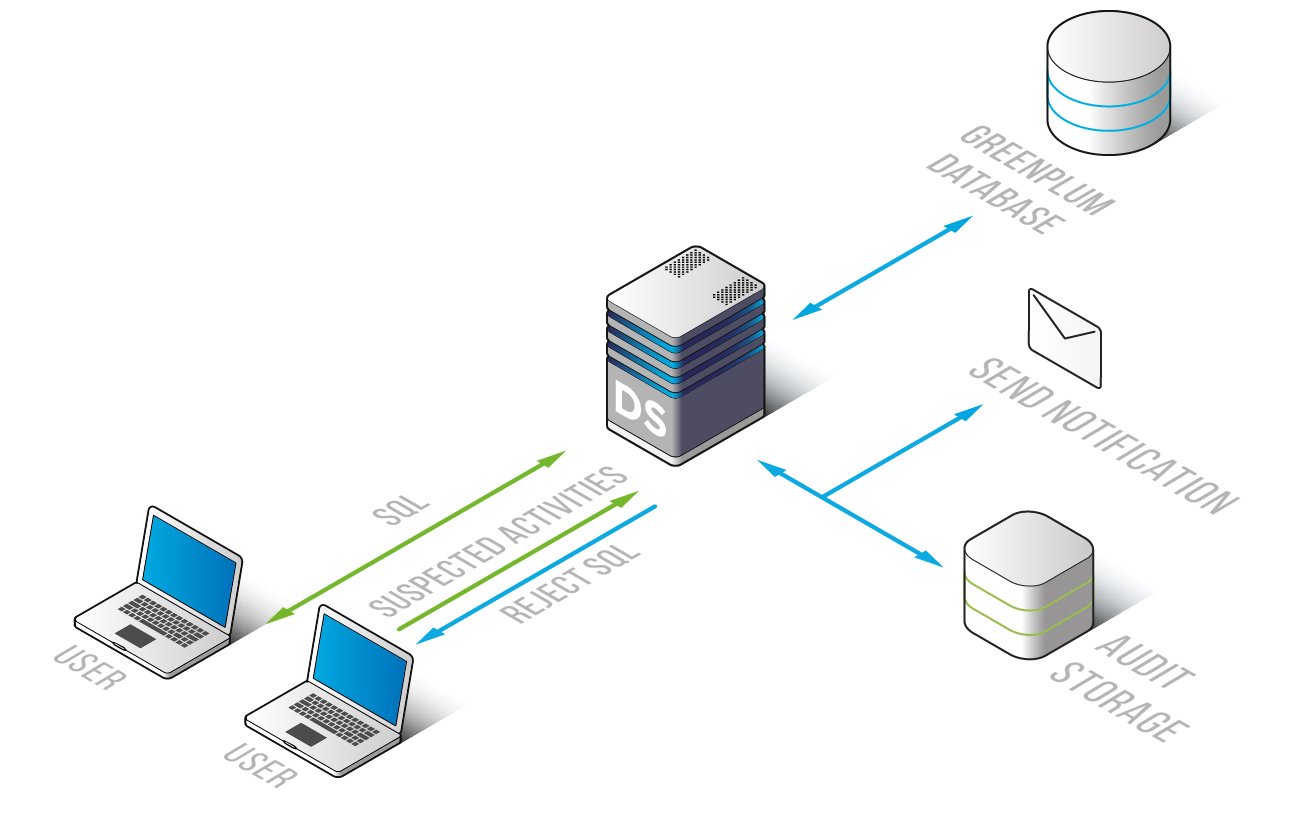
After deployment you can add learning rules so that DataSunrise will analyze incoming SQL queries and generate a list of common requests that further will be assumed safe and used to build a comprehensive security perimeter.
In the process of initial traffic processing the firewall inspects queries coming from users, output returned by the database, etc. Queries are subjected to a deep analysis and those violating security rules are blocked. When disassembling the packets the firewall differentiates objects of the target database, tables, schemas, and other relevant information.
DataSunrise firewall for Greenplum Database has the following advantages:
- Proccessing and tracking of a wide range of DDL and DML transaction.
- High-availability. Automatic failover in case one of the servers is down.
- Compatibility SIEM systems.
- Functioning as authentication proxy. There is a possibility to configure user mapping for Active Directory users with the support of Kerberos protocol.
- Remote storage of logs.
- Scalable security rules for filtering SQL transactions according to the application, database user, attack signatures, signs of SQL injection.
Greenplum firewall by DataSunrise protects from SQL injections, unauthorized access and helps to keep your data safe. It runs on Linux, Unix, and Windows and supports Greenplum version 4.2 и higher.