DataSunrise Data Masking for Greenplum
Imagine that contractors you hired need access to your Greenplum database. The problem is that your database stores client addresses, credit card numbers and that sort of data. Static data masking is not an option because making a database “dummy” is a pricey and time-consuming process. The solution is dynamic data masking. When masking is employed, DataSunrise obfuscates the database output making it meaningless or unreadable.
Testing or development requires to Greenplum be completely available, troubleshooting issues – to have a direct connection to the database – as cases may be different, the solution maybe simple enough: to provide the database to third-parties obfuscating fields that must be kept private.
It ensures a consistent way to make fields with sensitive data contained in them indeterminate, puzzling or hidden from those with no rights to get it. DataSunrise functions in two directions – Dynamic and Static Greenplum Data Masking – that are dedicated to satisfy your specific needs. The masking algorithm of two options is the same: a sent query is intercepted by the Greenplum Data Masking component that is modified as per masking policies. They are configured beforehand to identify ones with the right to see sensitive data in specified fields and how all this works is illustrated below:
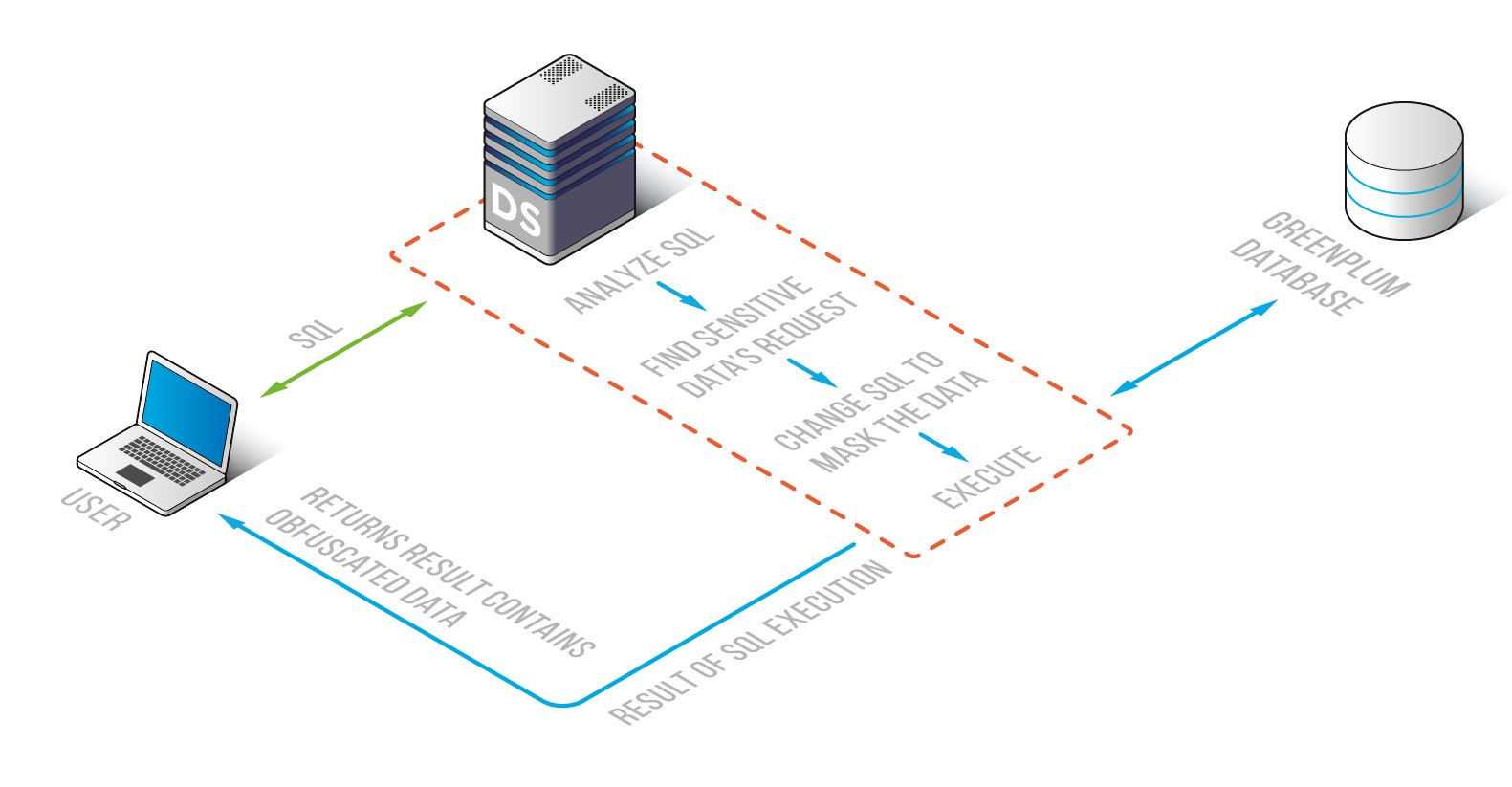
Greenplum Dynamic Data Masking defers from the static one by an ability to conceal confidential data from non-privileged users at the moment they send a query to the database. DataSunrise changes it making the database cloak information precious for the company in cryptic characters or replace it with fake data that resembles the real one though has no value.
Greenplum Static Data Masking makes a database copy and masks corporate data that is of utmost importance and leakage of which endangers company’s reputation before it is handed over to any outsourced specialists. With Static Data Masking a duplicated Greenplum database seems identical to the original one except confidential data becomes obscure and unintelligible for people with no business need to see it.
When it comes to Greenplum privacy and confidentiality, increase your sensitive data security within the database entrusting it to the Greenplum Data Masking functional component. Information shared with third-parties remains secure and available only at the level required to fulfill their job.