DataSunrise Data Masking for Amazon Aurora
DataSunrise is an Advanced Amazon APN Technology Partner in data and database security.
On AWS Database Blog: Monitor Amazon Aurora database activities using DataSunrise Database Security.
Amazon Aurora data masking tool by DataSunrise is an effective way to hide sensitive data from any unwanted users. As soon as any query from the specified prohibited list is detected, the tool immediately replaces sensitive data values with signs or values predetermined by an administrator. This enables to protect Amazon Aurora database against any data leakage.
Limit access to sensitive data stored in Amazon Aurora and at the same time remain the database available for nonproduction purposes to developers, testers or any third-parties. DataSunrise Amazon Aurora Data Masking is going to be the right solution to take care of sensitive data privacy and protection.
The Amazon Aurora Data Masking security feature allows production data to be safely used in various nonproduction situations. The operation algorithm consists in rewriting a query before it gets the database. DataSunrise Amazon Aurora Data Masking intercepts the query sent to the database, modifies it and directs to the database making it replace or change information in certain fields so that it becomes indeterminate or completely concealed in the query result as in the following example:
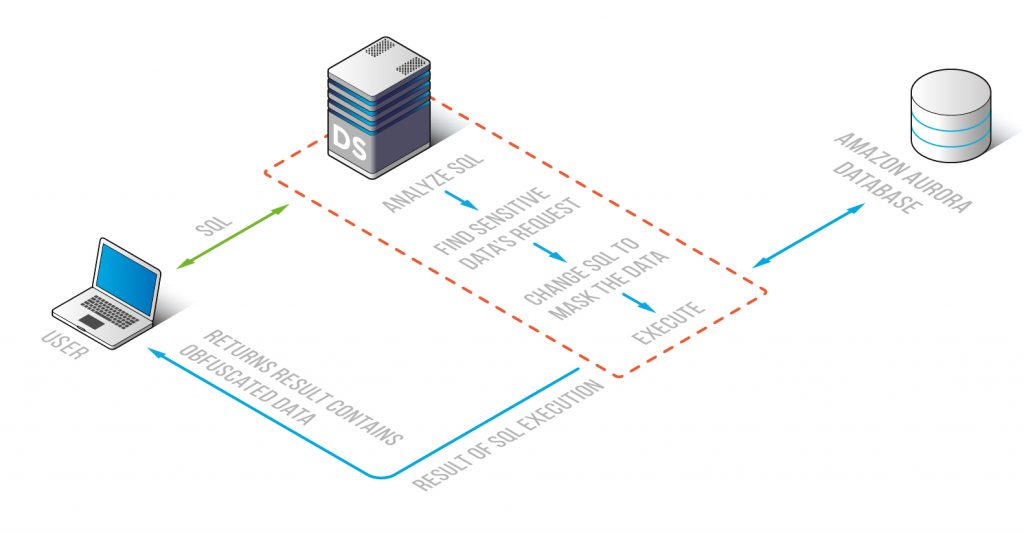
With the Amazon Aurora Data Masking module sensitive data maybe masked dynamically, i.e. all the fields that must be unclear and dubious for non-privileged users are obfuscated on-the-fly. Sensitive data in the database can be safeguarded for use in various nonproduction cases with static masking as well. The DataSunrise Amazon Aurora Static Data Masking feature enables to get a fully-functioning copy of Amazon Aurora, though with confidential information concealed according to preset masking rules. Masking rules may be configured for any column containing sensitive data. To control masking, the software may send notifications via SMTP or SNMP each time the rule is triggered.
As Amazon Aurora operations are unaltered and data in your database actually remains intact, privileged users can still easily see unmasked information. The masking rules are flexibly customized to define what must remain obscure and who has a business need to see real values and information.
DataSunrise Amazon Aurora Data Masking allows not only to ensure confidentiality of precious data, but meet privacy standards as well.