DataSunrise Masking for MS SQL Server
DataSunrise Masking for MS SQL Server guarantees business data protection against unauthorized access and data leaks. The tool obfuscates actual data in production databases to hide sensitive and regulated information but keeps it looking realistic. MS SQL Server Data Masking prevents critical data exposure to non-privileged users.
With MS SQL Server Data Masking sensitive and confidential information contained in databases is replaced with random or predefined values, so that the original data becomes inaccessible for non-authorized users. Masking of data is appropriate for the situations when a database is transferred to a third party for the purpose of application development, testing, analysis, etc. Also masking can be useful to limit data exposure to the employees within the company’s to avoid intentional and unintentional data leaks. After masking is applied data looks realistic, but it becomes useless for any potential wrongdoer.
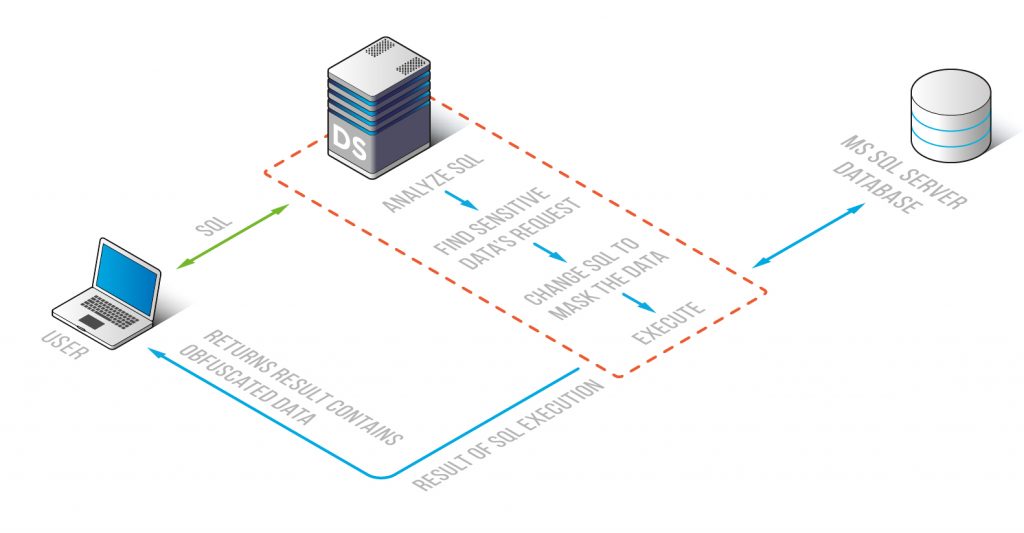
DataSunrise provides static and dynamic MsSQL Server data masking. With the Static MS SQL Server Data Masking component a stand-alone copy of the real database is created. The copy contains some neutral or randomized data instead of real sensitive data. Dynamic MS SQL Server Data Masking is performed at the moment of a query, on-the-fly. The actual database contents remain intact and only database output is obfuscated.
The SQL Server Data Masking tool obfuscates or randomizes database records according to the masking rules. DataSunrise MS SQL Server Data Masking provides general purpose masking methods and obfuscation algorithms for emails, credit card numbers, dates, time, etc. Users are also enabled to create their own masking algorithms.
This is how masking looks like: