DataSunrise Audit for Heroku Postgres
While using Heroku Postgres you can enjoy another very powerful tool from DataSunrise. The Heroku Data Audit feature makes it possible for you to keep track of every query made to your database at any time. Auditing your data with DataSunrise is a highly versatile and adjustable process. However, despite being easy to use, it provides you with a very powerful tool to audit your databases on Heroku.
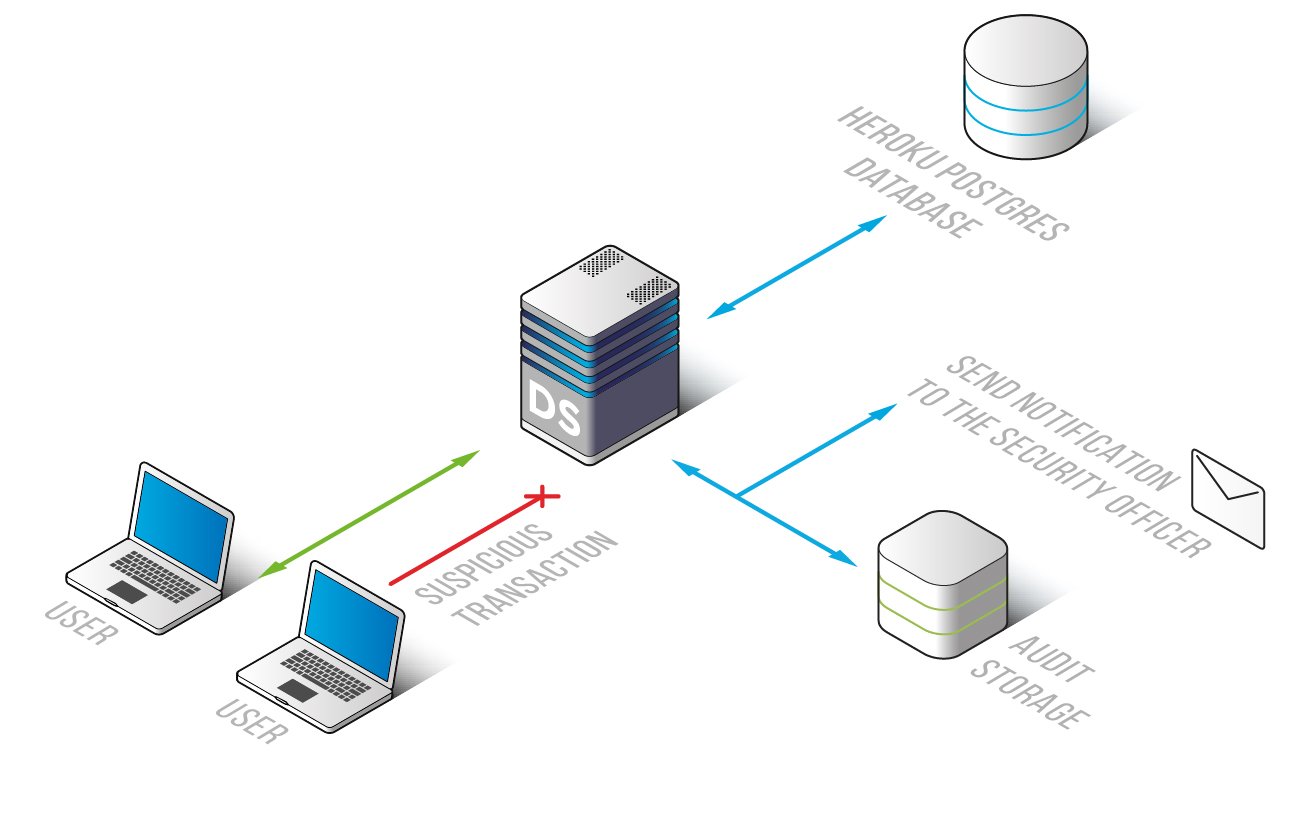
Heroku Postgres Database Audit from DataSunrise acts as a proxy between a database and its users. Protection of any database starts with understanding what is happening with a database at any given time. That is, who and how viewed, changed or updated certain information. That makes auditing a crucial element of database protection on Heroku Postgres. Heroku Postgres Database Audit tool from DataSunrise is effected using a set of Rules which are easily adjustable and triggered if a Rule is violated. In the result, any illegitimate queries, attempted SQL injections, fraudulent insider activity, suspicious operations are registered and can be blocked. All events are registered too. All user sessions on Heroku Postgres are monitored and registered. Adjustable Learning Rules do the whitelisting thus saving a lot of time for DB administrators as they don’t have to look through all operation logs. Also, they enable them to take measures against hacking attempts proactively.
Heroku Postgres Database Audit is a very important feature from DataSunrise for protection of your Postgres databases.
Experience the future of data management. Join us for an interactive online demo of DataSunrise Audit and our suite of tools. Book now!


