DataSunrise Audit for Apache Hive
DataSunrise’s hive audit tools monitor and track all database changes. Audit results of activity and performance monitoring provide an extra security measure and forensic evidence in case of cybersecurity incidents. Use DataSunrise to audit Hive databases and comply with regulatory demands (GBLA, SOX, HIPAA, PCI DSS).
Hive audit solution by DataSunrise allows monitoring and capturing of database events from different nodes on your network. It doesn’t require hardware appliances or even software-based agents.
Audit logs contain detailed information on database changes, such as client IP address, host, and application used. They also include SQL query code, affected database and table, number of rows changed, date, and time.
After the deployment, you can configure self-learning mode with help of learning rules. DataSunrise tracks every transaction and generates a list of SQL queries typical for the given environment.
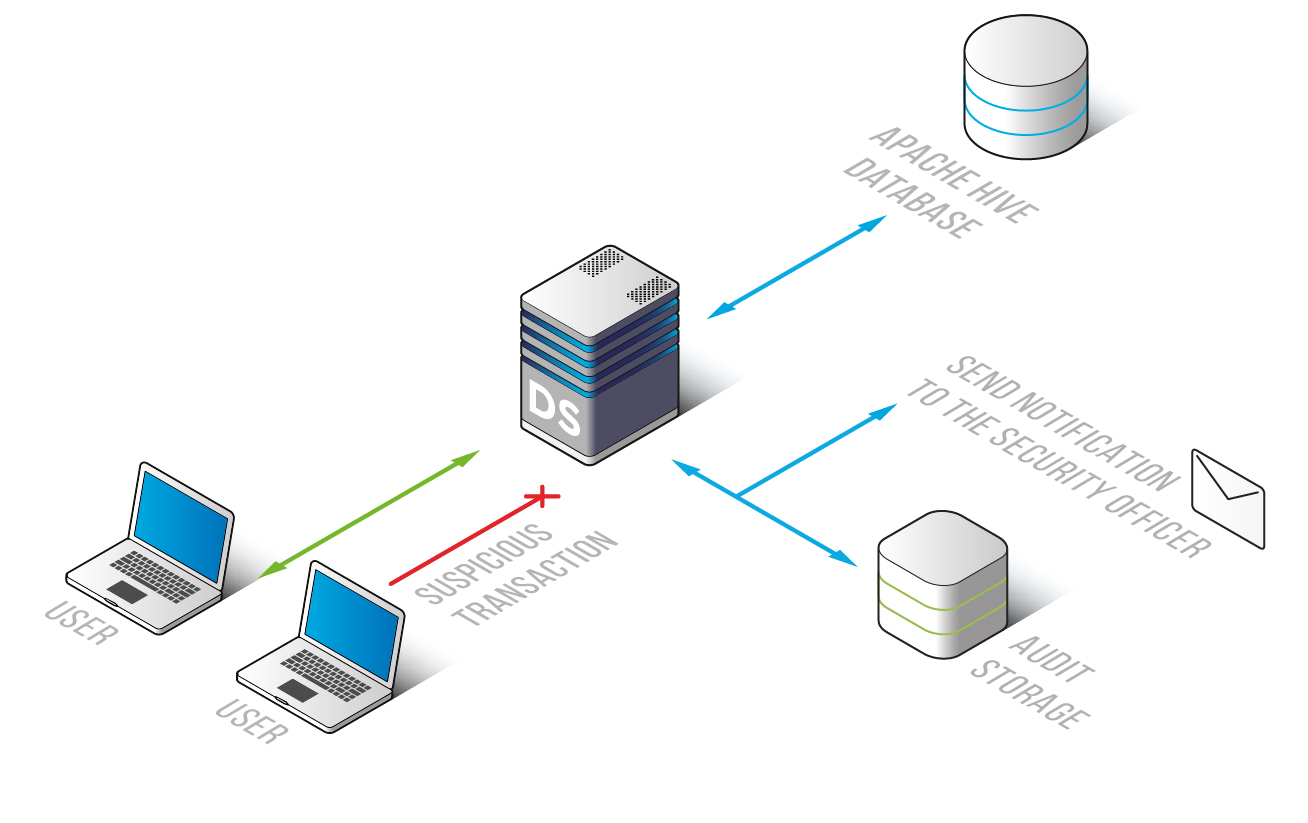
Hive audit software is easy to deploy. We designed scalable rule settings and a user-friendly GUI to automate essential security procedures.
Set up rules to catch any unauthorized access attempts, SQL injections, or requests for sensitive data. Receive notifications whenever a rule triggers. Properly configured security and audit policies save database administrators a lot of time.
DataSunrise performs monitoring and logging of transactions with minimal impact on database and application performance. Hive audit reports also contain different configuration changes. With DataSunrise you know who has changed certain security or audit policy and detailed session information of each user.
External databases store audit results, preventing evildoers from eliminating traces of malicious activity. Integration with SIEM systems provides real-time analyzing of security threats.
Reduce risks by using DataSunrise’s Hive audit tools. These tools help prevent excessive privilege and misuse of legitimate privileges. They also help manage sensitive data and protect against SQL injection attacks. Regular monitoring of logs helps to detect potential vulnerabilities and signs of preparation for a targeted attack.


