DataSunrise Database Activity Monitoring for Percona Server for MySQL
DataSunrise activity monitoring tool captures, identifies and records activity traffic over multiple databases. Using real-time security technology it helps in detecting unauthorized or unusual internal and external activities without causing database slowdown. When a certain rule is triggered, administrators are alerted so that they don’t need to go through all traffic logs. Activity monitoring tool by DataSunrise helps to keep your Percona Server databases safe.
DataSunrise activity monitoring tool for Percona Server for MySQL databases is designed for real-time monitoring, keeping logs on database transactions and alerting in case of security policy violation or any suspicious activity. Self-learning mode’s main purpose is to identify what kinds of queries are executed in a certain environment in a normal state. Sophisticated algorithms helps to detect non-typical operations and minimize data security risk.
Unauthorized databases, misconfigurations, default passwords, outdated security patches, SQL injection vulnerabilities provide easy vectors of attack to hackers. By providing full transparency of database activities DAM tools reveal these vulnerabilities. In addition, they collect logs that can be used as evidence while investigating cybercrimes.
Logs contain codes of processed queries, user, host names, application names, responses of database, user session data, authorization data, security/audit rule updates, occurred errors, etc.
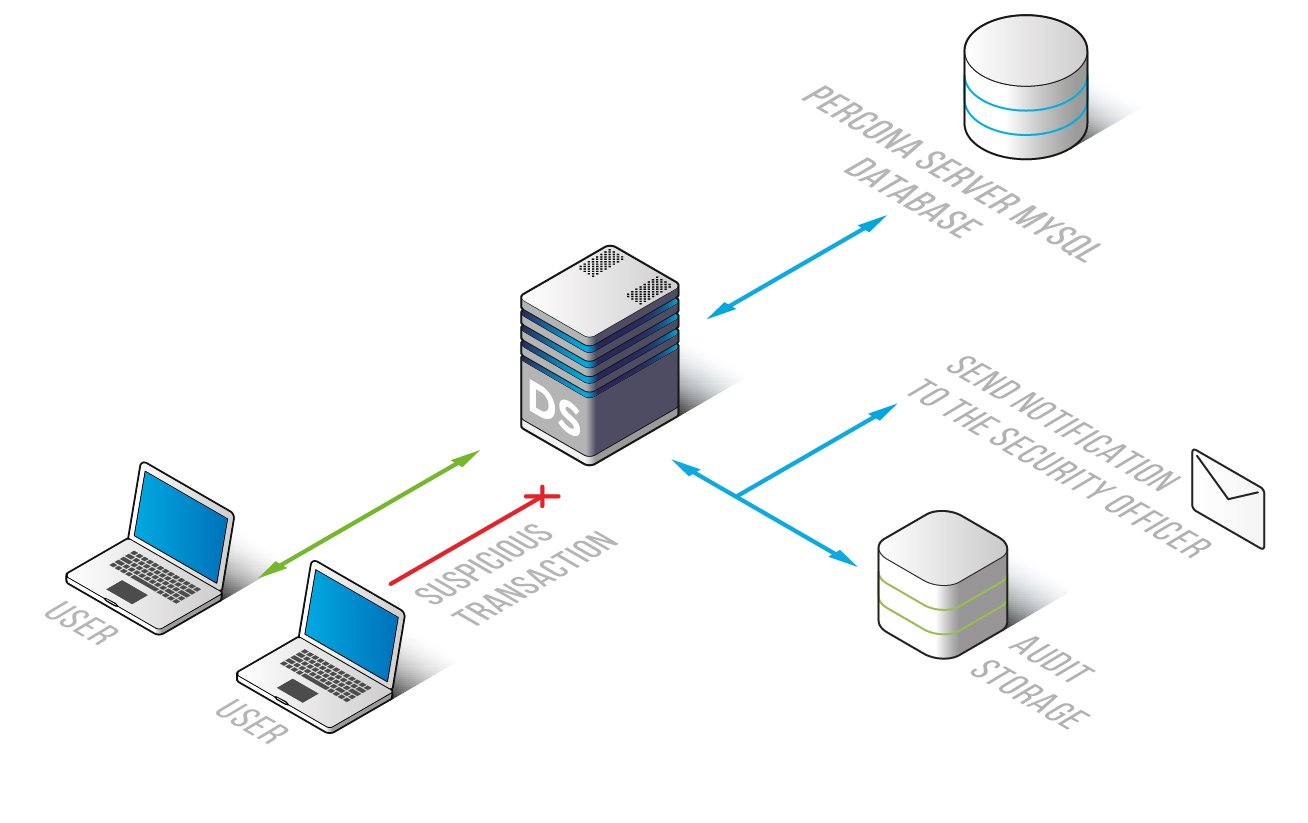
DataSunrise activity monitoring tool compatible with Percona Server for MySQL has the following benefits:
- Convenient interface with features to adjust different corporate needs;
- Detailed logs on database traffic;
- Compliance in addressing regulatory mandates: HIPAA – Health Insurance Portability and Accountability Act, SOX – Sarbanes Oxley Act, PCI DSS – Payment Card Industry Data Security Standard;
- Integration with a SIEM system (Splunk, IBM QRadar, MCAfee, HP ArcSight);
- Opportunity to add email addresses in order to receive notifications via SMTP, SNMP when certain security rule is triggered;
- Ability to manage multiple databases;
- Easy to deploy and to work with;
- Monitoring privileged users and database administrators operations.


