DataSunrise Database Activity Monitoring for IBM DB2
IBM DB2 activity monitoring software is designed to capture and record user actions and provide the complete visibility into database activity. Any violation of security policies is identified in real time, which guarantees that threats are detected and stopped immediately. DataSunrise monitors SQL-requests, unauthorized access to sensitive information, and more.
DataSunrise Activity Monitoring is a powerful DAM solution (Database Activity Monitoring) for IBM DB2 monitoring. Typically, DAM technology is used for:
- Monitoring user behavior, including privileged users, such as database administrators. Users with extended rights can pose a potential risk to data security. With DAM solution in place it becomes impossible for them to read or tamper with sensitive information.
- Identifying suspicious database activity to spot nosy and malicious employees or hackers looking for vulnerabilities in your system. Recognizing user behavior that deviates from normal access patterns allows administrators to prevent a data breach in advance.
- Detecting vulnerabilities in the system, such as dormant user accounts, which can be exploited by wrongdoers.
- Detecting and investigating data leaks and data security incidents. DataSunrise Database Activity Monitoring for DB2 can be used to reveal if the data has been stolen or tampered with and identify breaches that already occurred. This helps security teams to conduct proper investigation.
- Staying compliant with industry regulations, such as SOX, PCI DSS, HIPAA, and others. Many standards require companies to employs monitoring and auditing tools.
- Gathering statistics.
As you can see, DB2 monitoring is not only about statistics, but also actively helps to keep the database secure.
Database Activity Monitoring for IBM DB2
IBM DB2 Activity Monitoring enables to track in real time database user activity and document changes made to database contents. This allows administrators to be able to easily identify who, when and why accessed the database.
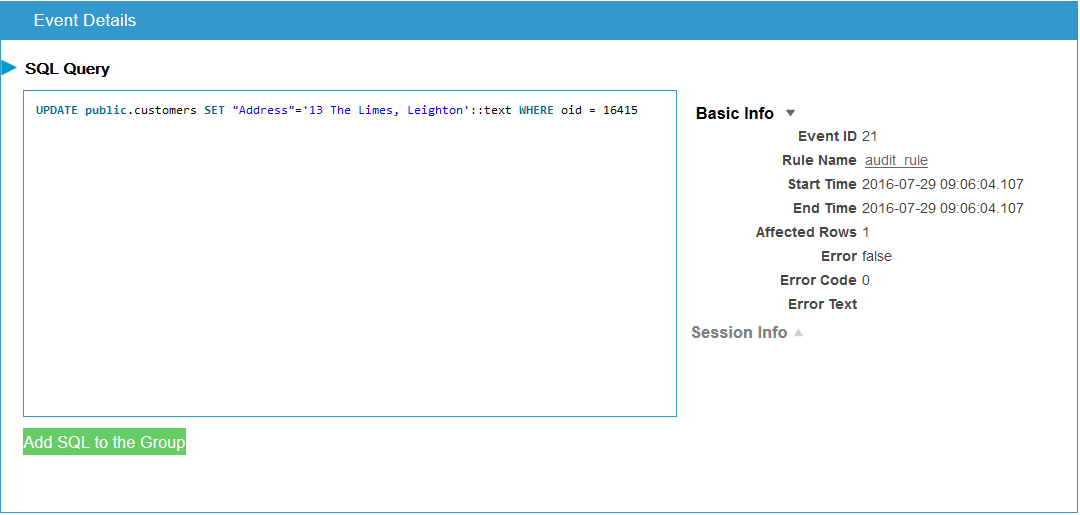
IBM DB2 activity monitoring solution by DataSunrise gathers and records the following data:
- SQL query code
- Session duration
- Number of rows affected by query, and query results
- Database error messages
- Database user information (user name, host name)
- Information on client application used to query database (application name, host name).
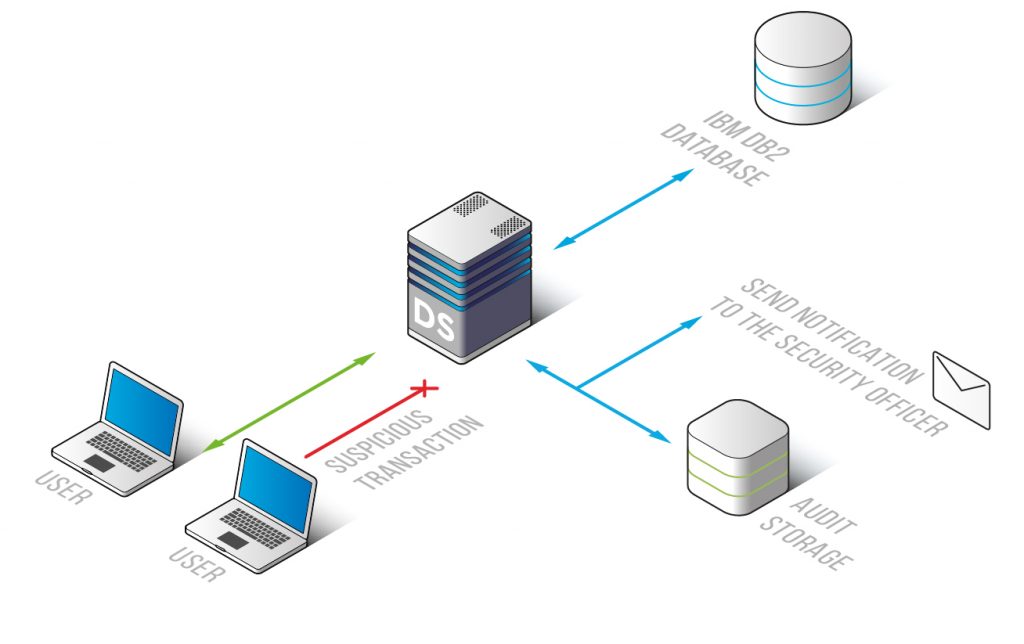
Audit records can be saved into DataSunrise-integrated SQLite database or to an external database. An important advantage is that the collected information can be exported to a third-party solution, e.g. a Security information and event management system (SIEM). Integrated with a SIEM, DataSunrise recreates the complete picture of database activity and enhances security analytics capabilities of the whole system.
Additionally, DataSunrise has Learning mode to speed up the initial deployment process. Self-learning algorithms capture typical safe user behavior and create a whitelist of permitted queries.


