DataSunrise Database Activity Monitoring for MariaDB
MariaDB activity monitoring solution by DataSunrise ensures full visibility of user actions and changes applied to the database. MariaDB monitoring is helpful for cybercrime investigation and detection of hazardous operations. The solution enables to manage a number of databases and alerts when suspicious activities take place. DAM tool is easy to deploy and has no impact on database performance rate. Monitor MariaDB activity monitoring and protect your databases from unauthorized access and attack attempts.
Activity monitoring is an important part of database security system. It is used for numerous purposes:
- For managing database user operations, being able to see the list of processed queries with detailed description.
- For monitoring transactions of privileged users and database administrators. In most cases of data leakage cause of the incident can be found among careless or malevolent actions of company members, that’s why it is important to keep track of their actions.
- During a cybercrime investigation culprit of a data breach can be found by records. Logged information about database operations is stored outside the corporate database, so it can be edited or deleted by evildoers.
- Regulatory agencies and government legislation in the sphere of information security demands companies storing sensitive data to implement tools for database monitoring and audit.
MariaDB Activity Monitoring
DataSunrise offers a MariaDB monitoring tool with sophisticated algorithms for query analysis that doesn’t affect database performance. Password brute-force, SQL injections and other types of attacks will be detected, as well as the cases of copying or viewing confidential information by privileged users.
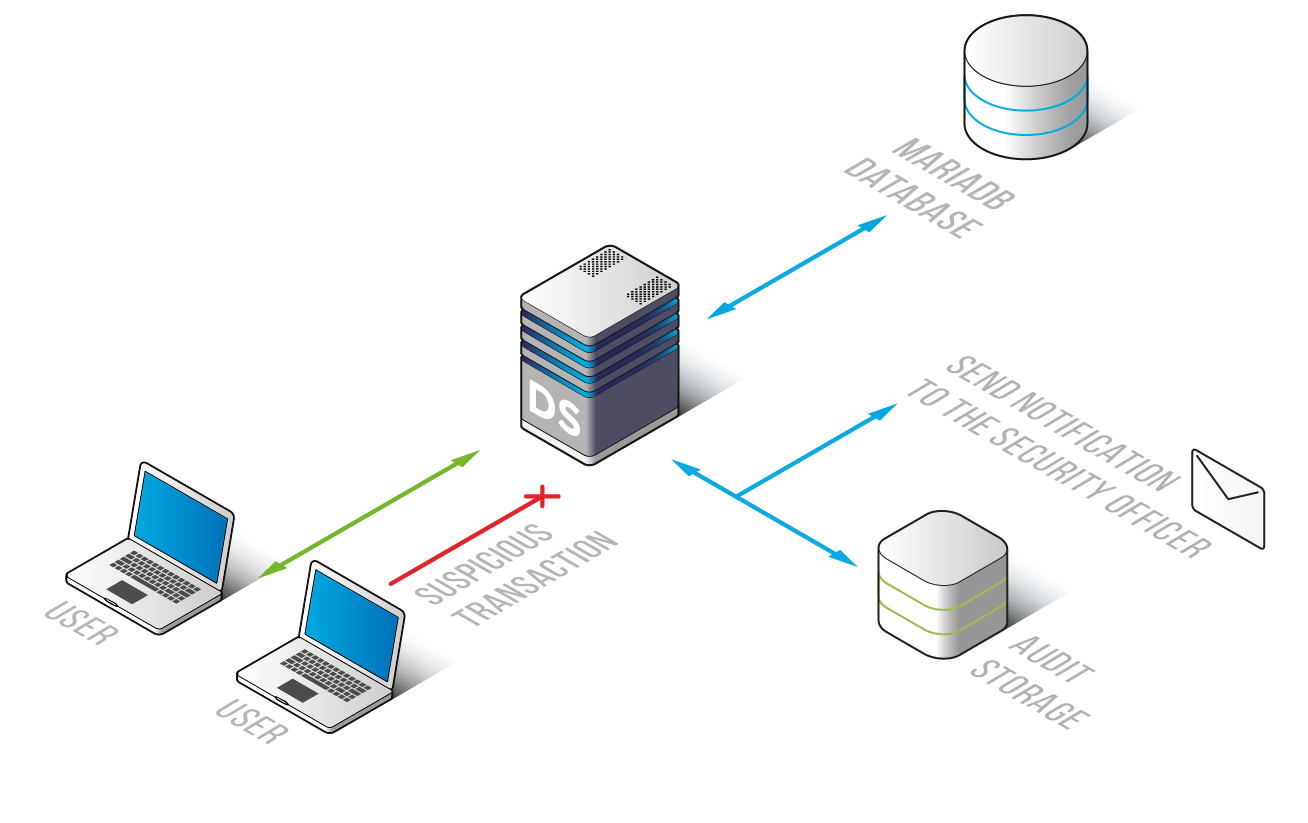
Monitoring result logs contain changes applied to security policy, firewall configurations, privilege assignment, user session data, including host names, IP addresses, used applications, codes, and results of query execution and many other parameters.
MariaDB activity monitoring solution by DataSunrise has a self-learning mode that identifies SQL queries typical for given environment. Recorded logs can be sent to SIEM products like Splunk, McAfee, IBM QRadar to get real-time analysis of security threats. Flexible options allow to skip transactions with certain parameters and notify of unusual queries.


