DataSunrise Database Activity Monitoring for Teradata
DataSunrise allows visualization of entire Teradata activity. Comprehensive analysis of data generated by the software product ensures the protection of your sensitive information, as you may be able to detect vulnerabilities in the system, take actions against insider threats and hacker attacks in a timely fashion, conduct data breach investigation using logged data as evidence. Use Teradata monitoring tools for cyberattack protection, privileged user and application activity monitoring.
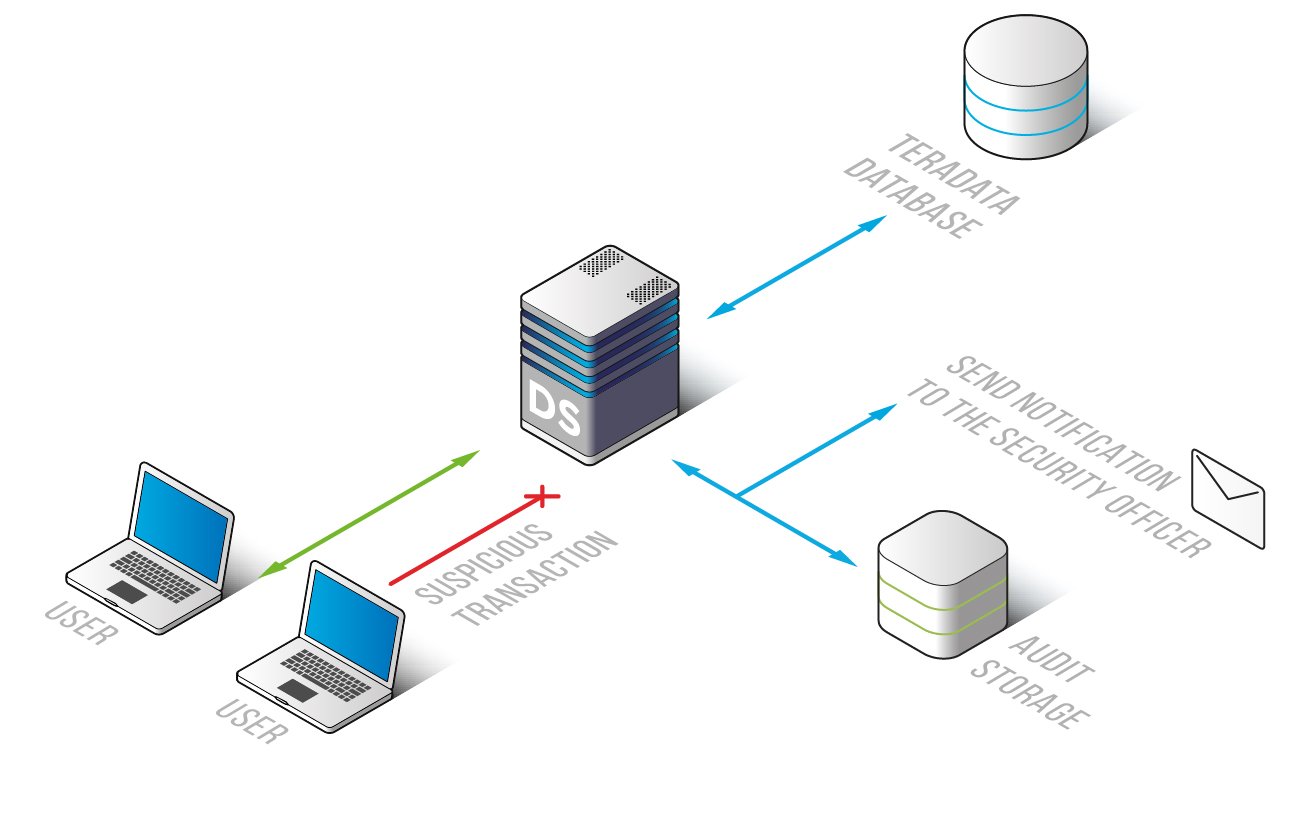
Monitor Teradata database and be aware of all queries that are sent to the database and make sure your sensitive information is protected from being compromised either by hackers or by inside attackers. DataSunrise provides a highly-scalable Teradata monitoring solution adjustable to various corporate needs.
Ensure your sensitive data protection against any possible hazards that your database may confront. Adapt DataSunrise to get accurate and comprehensive overview offered by the following logged data:
- SQL query codes;
- Information on Teradata users;
- Client applications;
- Session duration (start and end time);
- Affected or updated row number;
- Query results and database errors (if any).
Audit logs that can be used for analysis and investigation are stored either in the integrated SQLite database set by default or in any other external database at your option.
Teradata Database Activity Monitoring by DataSunrise is an effective mechanism that blocks suspicious queries and notifies an administrator of the fact thus allowing to immediately take all the required measures aimed at eliminating what provokes certain unexpected problems.
Ability to send Teradata monitoring results to SIEM systems makes it even more convenient. When it comes to large or geographically scattered enterprises, an enormous amount of generated data of various kind makes it impossible to be accurately tracked. To get a real-time analysis of security threats DataSunrise can be paired with a SIEM system.
Try Teradata monitoring solution for activity analysis, detection of any deviations from standards, i.e. nontypical user behavior, unknown applications, network traffic anomaly and so forth.


